Time back ...
 That died down the first of April. Someone on this day sniffing their devices in the new Google Nose service, someone was playing “Field of Miracles” , and someone, having forgotten the fatal date, simply sullenly brushed off the chalk from the chalk
That died down the first of April. Someone on this day sniffing their devices in the new Google Nose service, someone was playing “Field of Miracles” , and someone, having forgotten the fatal date, simply sullenly brushed off the chalk from the chalkI, inspired by the article about the hidden possibilities for customizing the explorer.exe process, also decided to do something funny.
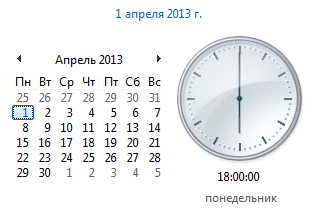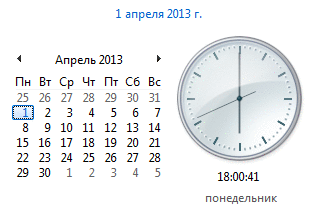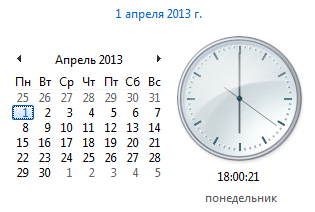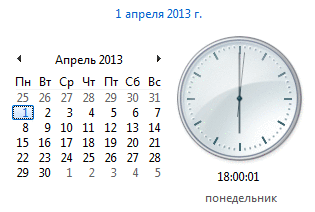
Let today my second hand of the clock in Windows goes in the opposite direction! Not the most, of course, useful in the fashion industry, but for academic and recreational purposes it will fit perfectly :)
I left the hour and minute hands in the right direction. Sometimes you still have to watch for hours on the tray - let them show the time with an accuracy of at least a minute ...
Training
The sequence of actions is approximately as follows:
- Explore explorer.exe and understand how it counts time.
- Something to change something in logic so that the clock goes back
There is no difficulty in changing the logic of a 32-bit usermode process: there is a long-time OllyDbg debugger, which has plenty of tutorials on which is even in Russian. Therefore, to give a zest, it was decided to implement the task on my 64-bit Windows 7 - I have long wanted to know what processes live there with doubled digit capacity ...
In the 64-bit world at the disassembler level, unfortunately, life is not very sweet: neither you are comfortable with Olly for debugging, nor you with the most comfortable Detours , for which they ask to pay as much as $ 9,999.95 (well, thank you for not $ 10k - marketers know how to make the price more attractive). Even old 32-bit injectors cannot be used to embed 64-bit dll. Apparently, my default search engine will have a hard time working ...
')
Forgive me, the fans of static analysis, I didn’t have a relationship with IDA Pro, so I had almost no choice - the old WinDbg waited in the wings.
In matters of working with WinDbg, the most valuable source of information is the windbg.info resource .
Explore explorer.exe
Connect to the process and look for something related to the word " clock ":
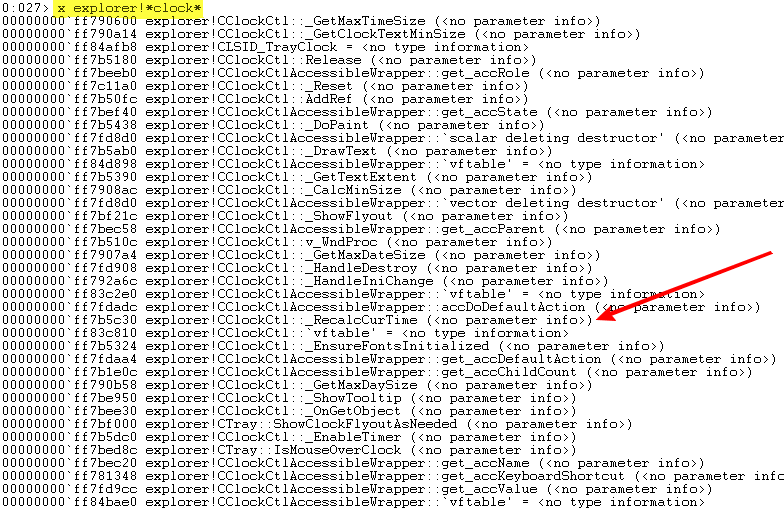
Looking closer at the list of functions, you can see the inconspicuous function
explorer!CClockCtl::_RecalcCurTime . Is the first shot at once in the goal? Let's see what's inside:
That's right, right after the function prologue we see a call to GetLocalTime , which, as you know, returns the local time and date. If we can influence the return result of this function, we can also change the direction of the second hand - all that remains is to put a hook on this function.
To realize our plans, we need to somehow get into the address space of the explorer.exe process. And with this, the CLI DLL-Injector command line utility will help us. Not only does it support 32 and 64 bits, it can also inject dll in two ways: via LoadLibrary injection, and using direct code writing via WriteProcessMemory followed by transfer of relocs.
Directly to install the hooks inside the explorer.exe process, we use the simple and reliable MinHook library.
It is worth noting that behind the seeming simplicity of the library, there is a very thoughtful logic inside, which works even in rather complicated cases. So, the Powerful x86 / x64 Mini Hook-Engine library, which I tried to use at first, caused Access Violation because the first instruction of the GetLocalTime function is a relative JMP transition. In this case, the task is complicated by the need to recalculate the offset.
Implementation
Determined with the tools. Now it remains to write the dll, which when DLL_PROCESS_ATTACH will put a hook on the GetLocalTime function:
#include <windows.h> #include "MinHook.h" // libMinHook.dll #pragma comment(lib, "libMinHook.x64.lib") // GetLocalTime static void (WINAPI *GetLocalTime_)(LPSYSTEMTIME lpSystemTime); void WINAPI MyGetLocalTime(LPSYSTEMTIME lpSystemTime) { // GetLocalTime GetLocalTime_(lpSystemTime); // : 59 -> 0, 0 -> 59 lpSystemTime->wSecond = 59 - lpSystemTime->wSecond; } BOOL APIENTRY DllMain(HMODULE hModule, DWORD dwReason, LPVOID lpReserved) { switch (dwReason) { case DLL_PROCESS_ATTACH: // ! // , DllMain() // libMinHook if (MH_Initialize() != MH_OK) { return FALSE; } // ( ) if (MH_CreateHook(&GetLocalTime, &MyGetLocalTime, reinterpret_cast<void**>(&GetLocalTime_)) != MH_OK) { return FALSE; } // if (MH_EnableHook(&GetLocalTime) != MH_OK) { return FALSE; } } return TRUE; } Use the resulting dll
Now you can embed dll. Run the injector in the console with the following command:
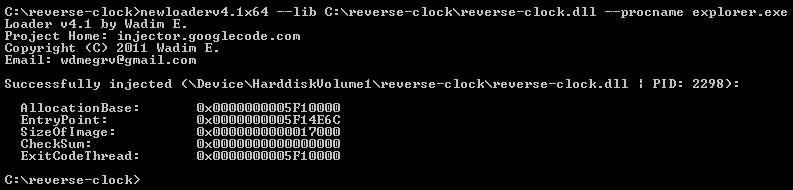
In the key --lib it is important to pass the full path to the dll, for more details why this is done, see the comment
Everything, you can enjoy the results! (gently hypnotizes)
Source codes (projects for VS2010) and binaries for self-tinkering can be found here .
Source: https://habr.com/ru/post/175025/
All Articles