Information security policy - development experience and recommendations
 In this topic, I will try to make a manual on the development of regulatory documents in the field of information security for the commercial structure, based on personal experience and materials from the network.
In this topic, I will try to make a manual on the development of regulatory documents in the field of information security for the commercial structure, based on personal experience and materials from the network.Here you can find answers to questions:
- What is the information security policy for?
- how to make it;
- how to use it.
The need for an information security policy
This section describes the need to implement the information security policy and related documents not in the beautiful language of textbooks and standards, but in examples from personal experience.
Understanding the goals and objectives of the information security division
 First of all, the policy is necessary in order to convey to the business the goals and objectives of the company's information security. A business should understand that security is not only a tool for investigating data leaks, but also an assistant in minimizing company risks and, therefore, in increasing company profitability.
First of all, the policy is necessary in order to convey to the business the goals and objectives of the company's information security. A business should understand that security is not only a tool for investigating data leaks, but also an assistant in minimizing company risks and, therefore, in increasing company profitability.Policy Requirements - Basis for Implementing Safeguards
IS policy is necessary to justify the introduction of protective measures in the company. The policy must be approved by the highest administrative body of the company (general director, board of directors, etc.)
')
 Any protective measure is a trade-off between risk reduction and user experience. When the safety officer says that the process should not occur in any way due to the appearance of some risks, he is always asked a reasonable question: “How should it occur?” The safety specialist needs to suggest a process model in which these risks are reduced to some extent satisfactory for business.
Any protective measure is a trade-off between risk reduction and user experience. When the safety officer says that the process should not occur in any way due to the appearance of some risks, he is always asked a reasonable question: “How should it occur?” The safety specialist needs to suggest a process model in which these risks are reduced to some extent satisfactory for business.At the same time, any application of any protective measures concerning the interaction of the user with the company's information system always causes a negative reaction from the user. They do not want to relearn, read the instructions developed for them, etc. Very often, users ask reasonable questions:
- Why should I work according to your invented scheme, and not in the simple way that I have always used
- who thought it all up
Practice has shown that the user doesn’t care about the risks, you can talk to him about hackers, the criminal code and so on for a long time, nothing will come out of this, except for the waste of nerve cells.
If the company has an information security policy, you can give a concise and succinct answer:
This measure was introduced to fulfill the requirements of the company's information security policy, which was approved by the highest administrative body of the company.
As a rule, after the energy of most users comes to naught. The rest can be invited to write a memo to this very highest administrative body of the company. Here the others are eliminated. Because even if the note goes there, then we can always prove the necessity of the measures taken before the leadership. We do not eat our bread for nothing, right?
Recommendations for developing an information security policy
There are two points to keep in mind when developing a policy.
- The target audience of the information security policy is the end users and the top management of the company who do not understand complex technical expressions, but must be familiar with the provisions of the policy.
- No need to try to
shove nevpihuemoeinclude in this document all that is possible! There should be only the goals of information security, methods to achieve them and responsibility! No technical details if they require specific knowledge. These are all materials for instructions and regulations.

The final document must meet the following requirements:
- conciseness - a large volume of the document will scare away any user, no one will ever read your document (and you will often use the phrase: “this is a violation of the information security policy that you were introduced to”)
- availability to the average man - the end user must understand WHAT is written in the policy (he will never read and remember the words and phrases “journaling”, “model of the offender”, “information security incident”, “information infrastructure”, “man-made”, “anthropogenic "," Risk factor ", etc.)
How to achieve this?
In fact, everything is very simple: the IS policy should be a first-level document, it should be expanded and supplemented by other documents (regulations and instructions) that will already describe something specific.
It is possible to draw an analogy with the state: the first level document is the constitution, and the doctrines, concepts, laws and other normative acts existing in the state only supplement and regulate the implementation of its provisions. The approximate scheme is shown in the figure.
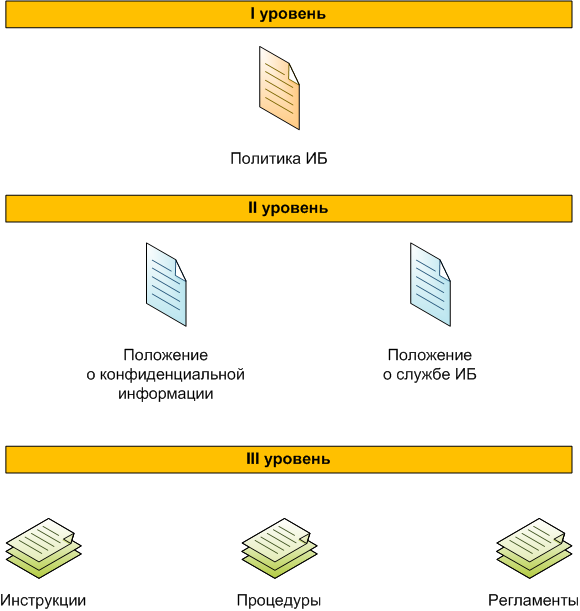
In order not to spread porridge on a plate, let's just look at examples of information security policies that can be found on the Internet.
Analysis of IS policies of existing companies
OAO Gazprombank - www.gazprombank.ru/upload/iblock/ee7/infibez.pdf
Damu Enterprise Development Fund JSC - www.damu.kz/content/files/PolitikaInformatsionnoyBezopasnosti.pdf
JSC NC "KazMunayGas" - www.kmg.kz/upload/company/Politika_informacionnoi_bezopasnosti.pdf
JSC “Radio Engineering Institute named after Academician A. L. Mints” - www.rti-mints.ru/uploads/files/static/8/politika_informacionnoy_bezopasnosti_rti.pdf
| Useful number of pages * | Term load | Overall rating | |
|---|---|---|---|
| OAO Gazprombank | eleven | Very high | Difficult document for thoughtful reading, the average person will not read, and if he does, he will not understand and will not remember |
| JSC "Entrepreneurship Development Fund" Damu " | 14 | High | Difficult document for thoughtful reading, the average person will not read, and if he does, he will not understand and will not remember |
| JSC NC "KazMunayGas" | 3 | Low | A simple to understand document, not overloaded with technical terms. |
| JSC "Radio Engineering Institute named after academician A. L. Mints" | 42 | Very high | Difficult document for thoughtful reading, the average person will not read - too many pages |
* Useful I call the number of pages without a table of contents, title page and other pages that do not carry specific information
Summary
The information security policy should fit into several pages, be easy for the average person to understand, describe in general the goals of the information security, methods of their achievement and the responsibility of employees.
Implementation and use of information security policy
After the approval of the information security policy it is necessary:
- to introduce the policies of all employees already working;
- to familiarize with the policy of all new employees (how best to do this is a topic for a separate conversation, we have an introductory course for beginners, in which I speak with explanations);
- analyze existing business processes in order to identify and minimize risks;
- to take part in the creation of new business processes in order not to run after the train;
- develop regulations, procedures, instructions and other documents that complement the policy (instructions for providing access to the Internet, instructions for providing access to restricted premises, instructions for working with company information systems, etc.);
- at least once a quarter, review the information security policy and other documents on information security with a view to updating them.
For questions and suggestions welcome to the comments and PM.
UPD001: after the publication of the topic an interesting dialogue with the habrauser took place (I publish it with the user's consent).
Question% username%
As for politics, the authorities do not like what I want in simple words. They say to me: “We have here, apart from me and you, and another 10 IT employees who themselves know and understand everything, there are 2 hundreds of people who do not understand this, half of them are retired at all.”
I took the path of medium descriptive descriptions, for example, anti-virus protection rules, and below I write the type of anti-virus protection policy, etc. But I do not understand if the user signs for the policy, but again he needs to read a bunch of other documents, sort of shortened the policy, but it seems not.
Reply bugaga0112358
I would follow the path of process analysis here.
Suppose anti-virus protection. Logically it must be so.
What risks do viruses carry us? Violation of the integrity (damage) of information, violation of the availability (downtime of servers or PC) of information. With proper network organization, the user should not have local administrator rights in the system, that is, he should not have the rights to install software (and therefore viruses) into the system. Thus, retirees fall off, because they do not do things here.
Who can reduce the risks associated with viruses? Users with admin rights domain. Admin domain - the role of scrupulous, issued to employees of IT departments, etc. Accordingly, they should install antiviruses. It turns out that they are also responsible for the activities of the anti-virus system. Accordingly, they should sign the instruction on the organization of anti-virus protection. Actually, this responsibility must be prescribed in the instructions. For example, Bezopasnik steers, admins perform.
Question% username%
Then the question is, what should not the responsibility for the creation and use of viruses be included in the instructions of the Antivirus ZI (or is there an article and can be not mentioned)? Or that they are required to report a virus or strange PC behavior to the Help Desk or IT staff?
Reply bugaga0112358
Again, I would look at risk management. It smacks, so to speak, GOST 18044-2007.
In your case, “strange behavior” is not necessarily a virus. This may be a brake system or gposhek etc. Accordingly, this is not an incident, but an information security event. Again, according to GOST, any person can declare an event, but it is possible to understand whether an incident is or not only after analysis.
Thus, this question of yours no longer translates into information security policy, but into incident management. Here in the policy you should be spelled out that the company must have an incident handling system .
Go ahead. Handle incidents will be already safe, admins, etc. Again, we leave in the responsibility of admins and security guards.
That is, as you can see, the administrative execution of the policy rests mainly on admins and security officers. Users remain custom.
Consequently, you need to create a certain “Procedure for using IT in a company”, where you must indicate the responsibilities of users. This document should correlate with the information security policy and be, so to speak, an explanation for the user.
In this document, you can specify that the user is obliged to notify the relevant authority about the abnormal activity of the computer. Well, everything else is custom, you can add there.
So you need to familiarize the user with two documents:
- IS policy (so that he understands what is being done and why, not rip, swear at the introduction of new control systems, etc.)
- this “Procedure for using SVT in a company” (so that he understands what specifically to do in specific situations)
Accordingly, when introducing a new system, you simply add something to the “Order” and notify employees about it by sending an order via email (or via the EDS, if one exists).
Source: https://habr.com/ru/post/174489/
All Articles