One of the biggest DDoS attacks in history.
Over the past week, many Internet users in Europe have experienced delays and short-term unavailability of multiple sites. Their reason - the DDoS attack that raged all this time, reaching 300 gigabits per second - is one of the largest, perhaps even the largest in the history of the Internet. The scale of the attack was such that it was even felt by the “whales” on whom the Internet stands - Tier-1 operators and the largest traffic exchange points of European capitals.
The cause of the attack was a conflict between the Spamhaus organization, which composes the lists of spammers, and the Dutch provider Cyberbunker . The conflict erupted after Spamhaus included Cyberbunker in the spam lists. Cyberbunker is one of the most radical “bulletproof” providers. Its services enjoyed Pirate Bay. Cyberbunker’s headquarters and servers are located in the five-story building of a former NATO military bunker - hence the name. According to Spamhaus, in response to the inclusion in the blacklist, Cyberbunker launched an attack.
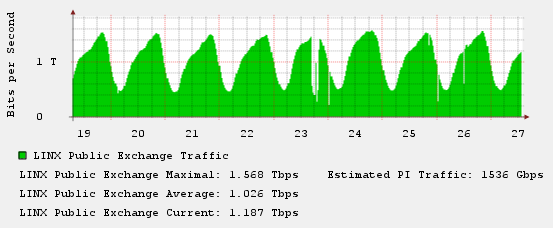
The blow took over CDN CloudFlare, providing, among other things, DDoS protection. The attack began on March 18 and the next day rose to 90 Gb / s. March 21, the attack was interrupted, but 22 continued with a new force, increasing to 120 Gb / s. Since it was not possible to overwhelm CloudFlare itself, the attackers soon switched to providers with which CloudFlare works and increased the attack power to a record 300 Gb / s. The attack affected the networks of the largest providers, which at certain moments turned out to be overloaded. On March 23, significant problems were at the London traffic exchange point. At rush hour, when traffic is usually about one and a half terabits, it did not cope with the load. The failure is clearly visible on the chart:
')
The attack was carried out by the method of DNS amplification - the servers of the attackers sent out a number of recursive queries to the DNS servers all over the Internet with fake return addresses. The answer to such a request with a length of several tens of bytes can weigh several kilobytes, and it is sent to the address of the victim, “reinforcing” the attack in this way. With the help of DNS amplification, you can achieve much more traffic than a regular botnet, since the role of "zombies" are not user computers with a weak channel, but servers. To conduct such an attack, you must have lists of addresses of vulnerable DNS servers. Apparently, the lists of the attackers were very long and of high quality. This DNS vulnerability has been known for a long time , but so far millions of servers around the world have not closed it.
The cause of the attack was a conflict between the Spamhaus organization, which composes the lists of spammers, and the Dutch provider Cyberbunker . The conflict erupted after Spamhaus included Cyberbunker in the spam lists. Cyberbunker is one of the most radical “bulletproof” providers. Its services enjoyed Pirate Bay. Cyberbunker’s headquarters and servers are located in the five-story building of a former NATO military bunker - hence the name. According to Spamhaus, in response to the inclusion in the blacklist, Cyberbunker launched an attack.
The blow took over CDN CloudFlare, providing, among other things, DDoS protection. The attack began on March 18 and the next day rose to 90 Gb / s. March 21, the attack was interrupted, but 22 continued with a new force, increasing to 120 Gb / s. Since it was not possible to overwhelm CloudFlare itself, the attackers soon switched to providers with which CloudFlare works and increased the attack power to a record 300 Gb / s. The attack affected the networks of the largest providers, which at certain moments turned out to be overloaded. On March 23, significant problems were at the London traffic exchange point. At rush hour, when traffic is usually about one and a half terabits, it did not cope with the load. The failure is clearly visible on the chart:

')
The attack was carried out by the method of DNS amplification - the servers of the attackers sent out a number of recursive queries to the DNS servers all over the Internet with fake return addresses. The answer to such a request with a length of several tens of bytes can weigh several kilobytes, and it is sent to the address of the victim, “reinforcing” the attack in this way. With the help of DNS amplification, you can achieve much more traffic than a regular botnet, since the role of "zombies" are not user computers with a weak channel, but servers. To conduct such an attack, you must have lists of addresses of vulnerable DNS servers. Apparently, the lists of the attackers were very long and of high quality. This DNS vulnerability has been known for a long time , but so far millions of servers around the world have not closed it.
Source: https://habr.com/ru/post/174483/
All Articles