We return privacy or big brother watching me on the standard settings. Part 2. We block tracking scripts on sites and configure VPN
In the first part, we talked about general settings for all browsers, briefly walked through passwords, encryption and backup, and also somewhat complicated the life of Google.
Today we’ll see (and get rid of) how many statistics are collected on us even without using third-party “cookie” files and tell you about the benefits and configuration of VPN in simple language.
I want to say a big thank you to everyone who left comments in the last article (and will leave this one) - all your good advice will be included in this or the next manual.
')

It’s not enough to block third-party cookies while you are loading the site. Your "entry" can analyze dozens of different third-party scripts. For example, what works in the background, when you go in just to find out the weather at Gismeteo:
- AdFox;
- AdRiver;
- Gemius;
- Google Analytics;
- LiveInternet;
- Rambler;
- ScoreCard Research Beacon;
- SUP media;
- TNS;
- Yandex.Direct.
Some of this may be simple attendance counters, something to provide site owners with data for profiling (page load speed, resources, etc.), something that works for advertising modules. There may be useful things like Adobe Typekit, which loads third-party fonts, so that the site is displayed exactly as the designers intended it, rather than using the standard fonts of your system.
Third-party comment modules are controversial if the site does not have its own system. Someone uses disqus and similar, someone comments from "Contact", someone from "Facebook". Their controversy lies in the fact that, if you are logged in to one of these systems, then, formally, any of your moves to the site containing the Like or Comments button can be logged = “all moves are recorded”. Therefore, the question that arises before you is this: either blocking such modules on sites (believe me, you won't lose anything much + there will be less desire, something to write yourself — something that can be used against you in the future) or surf. not being logged in social. network.
The extremely simple way to disable the above (as advertising trackers, and various modules) is an extension for your browser Ghostery - configure it.
Agree, strangely speaking about privacy, to send any usage statistics, so here we disable it, but enable automatic updating of data on trackers.

Further, upon request, we will turn on a notification popup for 15 seconds that it was blocked on each specific page, however, as a mandatory, this information should be shown on a click (useful if you need to unblock something on the page for a while), as well as automatic blocking items that come with updates from the previous paragraph.
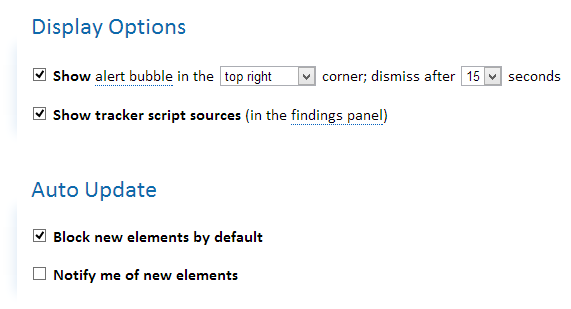
We block everything by default, except for Typekit by Adobe in the Widgets section (those additional fonts on the pages):

Now, when we go back to Gismeteo, the pop-up bubble will happily tell us about all the SEO-nastiness that he blocked on the page:

By clicking on the button ghosts in the panel with the number that shows the number of blocked, mini-settings ↓ appear. By the way, I will describe the icons on the chrome screenshot from left to right:
- similar to “pacman” with a cross - information that certain third-party cookies were blocked (we included this behavior in the previous article). It is necessary to click on it to allow the operation of a specific third-party cookie on the site (for example, on habrastorage to allow cookies from a habr to be able to upload a picture);
- the following two - add to favorites icon and pocket for saving pages for future reading;
- The third is the expansion of AdBlock , which allows you to block ads on websites;
- further described now by Ghostery;
- and, finally, the extension No History for Chrome. As we remember from the previous article, Google did not allow the automatic clearing of the history after a certain period of time, forcing us to compile a dossier from the visited pages - this extension disables the history altogether (Ctrl + Shift + T to open a tab of the accidentally closed will still work). It is important to understand that such extensions are not only for Chrome, but also for some other browsers (somewhere and not all of them are needed, for example, Safari under the poppy allows you to enable automatic deletion of the history older than a certain period).
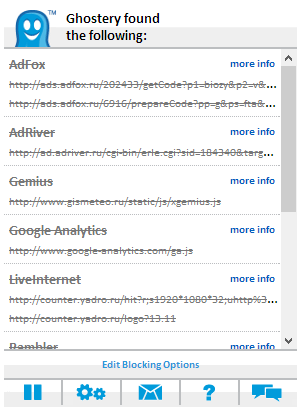
Here you can learn more about each of the blocked elements (more info), and if you need to unblock something for a specific site, click on the Edit Blocking Options button and remove the necessary checkboxes (for example, the “Contact” comment block, which, however, as already said, it is better not to turn it on if you are logged in with your account). Ideally, clean the browser’s cookies after that, because they can have a lot of different stuff in them (although you follow the advice from the previous article and set up the browser so that the cookies are deleted automatically every time you close the browser ).
It is also useful to disable plug-ins on all sites (you can in the settings of "Chrome" and the latest builds of "Fox"). More precisely, make them click-to-play, namely, click on each mouse (for example, on flash video) to activate it. Firstly, save a lot of traffic, and secondly, without any adblock get rid of flash advertising.
In the last article, the topic of VPN connections was mentioned only in passing, but this does not mean that this is not a very important thing. If you explain in simple language what it is and what it is eaten with, then this is a certain window that is protected from wiretapping and interception on the Internet. Imagine that you are sitting somewhere at the airport and saw an open Wi-Fi network with your laptop / ipad. You happily join her and you will not even suspect that in this way the attacker sitting in the next chair could intercept all your passwords used during the session. Now, many devices can raise their own Wi-Fi network, so an attacker could easily raise WiFi on his computer and fumble his 3G Internet, passing all your traffic through himself (and, accordingly, doing whatever you want with it). You can protect yourself from this if you use the https protocol to access the site (all traffic is encrypted). But, firstly, not all sites still use it, secondly, not everywhere it is enabled by default (for example, Facebook), thirdly, similar connections have recently been compromised and, therefore, are no longer a panacea .
Protection from all this is the VPN connection. All your traffic is encrypted and run through a third-party server, so even if this traffic is intercepted (you connect to an incomprehensible Wi-Fi, or your router starts to listen), it will be encrypted and useless to attackers (understandably, not 100% it is useless, but at least it will take a lot of work to get something out of it).
As a bonus, your location (in terms of IP address) on the Internet changes from physical to where the VPN server to which you are connected is located. Thus, for example, you can see content that is available only for certain countries and is not available from Russia. However, do not think that you can not be traced - for this you need to use other technologies.
Two types of VPN providers are common:
1. The first ones provide unlimited monthly traffic, but only for one device (i.e., you cannot use one account on both computers and phones at the same time, unless this is the home where you configured VPN on your router = all clients will be protected, connected to the router).
2. The second ones make it possible to use on any number of devices, but with a limited monthly quota for traffic sent through the server (accordingly, the more traffic, the more expensive per month).
The ideal scheme is a combination of the two: for a home computer where you download a lot of things, use the provider from the first category (for example, HideMyAss for $ 6.5 per month when you buy an annual plan) to exit "into people" (i.e. for phones, tablets and other devices where you do not download hundreds of gigabytes per month) - providers from the second category (for example, Cloak from $ 2 for 5 gigabytes per month).
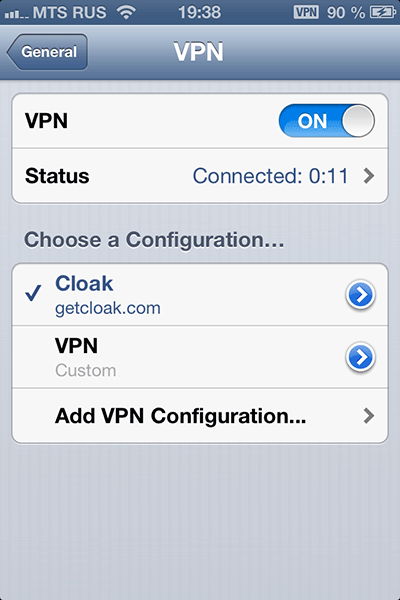
If you think that this is all difficult to set up, then you are mistaken. Here, for example, instructions for installing a VPN from Cloak on an iPhone / iPad:
1. Download their application, open it, log in with your login password and click on install profile.
2. A special page is opened in the browser and the connection settings file is downloaded to your device. Agree to install it.
3. Open the iOS settings, section “General - VPN”. Cloak profile will be installed in the list of profiles. We turn on the VPN connection by moving the VPN slider to the On ↓ position. Everything, you are protected.
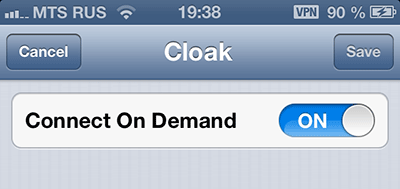
A small hack, which not everyone knows. VPN on iPhone / iPad falls off in case of blocking (it does not reconnect itself). However, all that is needed for the VPN to connect itself every time you go online is to click on the “arrow” in the profile name and tick the “Connect on demand” box (connect if necessary). In this case, every time an application needs to go online, it will first establish a VPN connection.
It is also worth saying that it is not always possible to establish a VPN connection with our quality of mobile communication. In this case, the “Internet” will simply not be until you disconnect the VPN connection (which the phone will unsuccessfully try to establish). However, remember that 3G encryption has already broken. Besides, as far as I know (correct me, please, if I'm wrong), the data is encrypted only to the nearest station. That is, it turns out that nothing prevents attackers from delivering a mini-cell of your operator in the next office (this is done absolutely legally to improve the quality of the signal in the office: you only need a more or less fast Internet channel to the office antenna), to which you’ll be happy join your phone and listen to all your traffic (including voice). VPN in this case will protect at least traffic (so, turning off, do not forget to turn it back on).
It is important to understand that in this case, for example, the operators will not have free traffic options for Yandex.Maps, since the traffic will be first to the VPN server, and from there to Yandex.Maps. However, it does not matter, because Yandex.Maps, that Yandex.Navigator can finally download a local copy of maps to a device (i.e., all traffic will only be available for traffic jams and route construction, which is not much).
In the next part we will talk about privacy on Facebook and Kontakt. Judging by similar comments in the current post, the article will be more than welcome.
Today we’ll see (and get rid of) how many statistics are collected on us even without using third-party “cookie” files and tell you about the benefits and configuration of VPN in simple language.
I want to say a big thank you to everyone who left comments in the last article (and will leave this one) - all your good advice will be included in this or the next manual.
')

Ghostery
It’s not enough to block third-party cookies while you are loading the site. Your "entry" can analyze dozens of different third-party scripts. For example, what works in the background, when you go in just to find out the weather at Gismeteo:
- AdFox;
- AdRiver;
- Gemius;
- Google Analytics;
- LiveInternet;
- Rambler;
- ScoreCard Research Beacon;
- SUP media;
- TNS;
- Yandex.Direct.
Some of this may be simple attendance counters, something to provide site owners with data for profiling (page load speed, resources, etc.), something that works for advertising modules. There may be useful things like Adobe Typekit, which loads third-party fonts, so that the site is displayed exactly as the designers intended it, rather than using the standard fonts of your system.
Third-party comment modules are controversial if the site does not have its own system. Someone uses disqus and similar, someone comments from "Contact", someone from "Facebook". Their controversy lies in the fact that, if you are logged in to one of these systems, then, formally, any of your moves to the site containing the Like or Comments button can be logged = “all moves are recorded”. Therefore, the question that arises before you is this: either blocking such modules on sites (believe me, you won't lose anything much + there will be less desire, something to write yourself — something that can be used against you in the future) or surf. not being logged in social. network.
The extremely simple way to disable the above (as advertising trackers, and various modules) is an extension for your browser Ghostery - configure it.
Agree, strangely speaking about privacy, to send any usage statistics, so here we disable it, but enable automatic updating of data on trackers.

Further, upon request, we will turn on a notification popup for 15 seconds that it was blocked on each specific page, however, as a mandatory, this information should be shown on a click (useful if you need to unblock something on the page for a while), as well as automatic blocking items that come with updates from the previous paragraph.

We block everything by default, except for Typekit by Adobe in the Widgets section (those additional fonts on the pages):

Now, when we go back to Gismeteo, the pop-up bubble will happily tell us about all the SEO-nastiness that he blocked on the page:

By clicking on the button ghosts in the panel with the number that shows the number of blocked, mini-settings ↓ appear. By the way, I will describe the icons on the chrome screenshot from left to right:
- similar to “pacman” with a cross - information that certain third-party cookies were blocked (we included this behavior in the previous article). It is necessary to click on it to allow the operation of a specific third-party cookie on the site (for example, on habrastorage to allow cookies from a habr to be able to upload a picture);
- the following two - add to favorites icon and pocket for saving pages for future reading;
- The third is the expansion of AdBlock , which allows you to block ads on websites;
- further described now by Ghostery;
- and, finally, the extension No History for Chrome. As we remember from the previous article, Google did not allow the automatic clearing of the history after a certain period of time, forcing us to compile a dossier from the visited pages - this extension disables the history altogether (Ctrl + Shift + T to open a tab of the accidentally closed will still work). It is important to understand that such extensions are not only for Chrome, but also for some other browsers (somewhere and not all of them are needed, for example, Safari under the poppy allows you to enable automatic deletion of the history older than a certain period).

Here you can learn more about each of the blocked elements (more info), and if you need to unblock something for a specific site, click on the Edit Blocking Options button and remove the necessary checkboxes (for example, the “Contact” comment block, which, however, as already said, it is better not to turn it on if you are logged in with your account). Ideally, clean the browser’s cookies after that, because they can have a lot of different stuff in them (although you follow the advice from the previous article and set up the browser so that the cookies are deleted automatically every time you close the browser ).
It is also useful to disable plug-ins on all sites (you can in the settings of "Chrome" and the latest builds of "Fox"). More precisely, make them click-to-play, namely, click on each mouse (for example, on flash video) to activate it. Firstly, save a lot of traffic, and secondly, without any adblock get rid of flash advertising.
VPN
In the last article, the topic of VPN connections was mentioned only in passing, but this does not mean that this is not a very important thing. If you explain in simple language what it is and what it is eaten with, then this is a certain window that is protected from wiretapping and interception on the Internet. Imagine that you are sitting somewhere at the airport and saw an open Wi-Fi network with your laptop / ipad. You happily join her and you will not even suspect that in this way the attacker sitting in the next chair could intercept all your passwords used during the session. Now, many devices can raise their own Wi-Fi network, so an attacker could easily raise WiFi on his computer and fumble his 3G Internet, passing all your traffic through himself (and, accordingly, doing whatever you want with it). You can protect yourself from this if you use the https protocol to access the site (all traffic is encrypted). But, firstly, not all sites still use it, secondly, not everywhere it is enabled by default (for example, Facebook), thirdly, similar connections have recently been compromised and, therefore, are no longer a panacea .
Protection from all this is the VPN connection. All your traffic is encrypted and run through a third-party server, so even if this traffic is intercepted (you connect to an incomprehensible Wi-Fi, or your router starts to listen), it will be encrypted and useless to attackers (understandably, not 100% it is useless, but at least it will take a lot of work to get something out of it).
As a bonus, your location (in terms of IP address) on the Internet changes from physical to where the VPN server to which you are connected is located. Thus, for example, you can see content that is available only for certain countries and is not available from Russia. However, do not think that you can not be traced - for this you need to use other technologies.
Two types of VPN providers are common:
1. The first ones provide unlimited monthly traffic, but only for one device (i.e., you cannot use one account on both computers and phones at the same time, unless this is the home where you configured VPN on your router = all clients will be protected, connected to the router).
2. The second ones make it possible to use on any number of devices, but with a limited monthly quota for traffic sent through the server (accordingly, the more traffic, the more expensive per month).
The ideal scheme is a combination of the two: for a home computer where you download a lot of things, use the provider from the first category (for example, HideMyAss for $ 6.5 per month when you buy an annual plan) to exit "into people" (i.e. for phones, tablets and other devices where you do not download hundreds of gigabytes per month) - providers from the second category (for example, Cloak from $ 2 for 5 gigabytes per month).
If you think that this is all difficult to set up, then you are mistaken. Here, for example, instructions for installing a VPN from Cloak on an iPhone / iPad:
1. Download their application, open it, log in with your login password and click on install profile.
2. A special page is opened in the browser and the connection settings file is downloaded to your device. Agree to install it.
3. Open the iOS settings, section “General - VPN”. Cloak profile will be installed in the list of profiles. We turn on the VPN connection by moving the VPN slider to the On ↓ position. Everything, you are protected.

A small hack, which not everyone knows. VPN on iPhone / iPad falls off in case of blocking (it does not reconnect itself). However, all that is needed for the VPN to connect itself every time you go online is to click on the “arrow” in the profile name and tick the “Connect on demand” box (connect if necessary). In this case, every time an application needs to go online, it will first establish a VPN connection.

It is also worth saying that it is not always possible to establish a VPN connection with our quality of mobile communication. In this case, the “Internet” will simply not be until you disconnect the VPN connection (which the phone will unsuccessfully try to establish). However, remember that 3G encryption has already broken. Besides, as far as I know (correct me, please, if I'm wrong), the data is encrypted only to the nearest station. That is, it turns out that nothing prevents attackers from delivering a mini-cell of your operator in the next office (this is done absolutely legally to improve the quality of the signal in the office: you only need a more or less fast Internet channel to the office antenna), to which you’ll be happy join your phone and listen to all your traffic (including voice). VPN in this case will protect at least traffic (so, turning off, do not forget to turn it back on).
It is important to understand that in this case, for example, the operators will not have free traffic options for Yandex.Maps, since the traffic will be first to the VPN server, and from there to Yandex.Maps. However, it does not matter, because Yandex.Maps, that Yandex.Navigator can finally download a local copy of maps to a device (i.e., all traffic will only be available for traffic jams and route construction, which is not much).
In the next part we will talk about privacy on Facebook and Kontakt. Judging by similar comments in the current post, the article will be more than welcome.
Source: https://habr.com/ru/post/174451/
All Articles