Linux in Active Directory Domain
Administrators sometimes face the challenge of integrating Linux servers and workstations into an Active Directory domain environment. Usually required:
1. Provide access to services on a Linux server for domain users.
2. Launch administrators' server on Linux using your domain credentials.
3. Configure the login to a Linux workstation for domain users, and it is desirable that they could at the same time taste all the delights of SSO (I, for example, do not really like to enter my long, long password often).
Usually, to provide a Linux system for users and groups from an Active Directory domain, they use winbind or configure nss libraries to work with an Active Directory domain controller using an LDAP protocol. But today we will go the other way: we will use PowerBroker Identity Services (The product is also known as Likewise).
There are two versions of the product: Enterprise and Open. For the implementation of my tasks, the Open version was enough for me, so everything written further will concern her.
You can get the Open version on the manufacturer's website , but you will be provided with a link in exchange for your name, company name and e-mail.
There are 32 and 64 packages in rpm and deb formats. (As well as packages for OS X, AIX, FreeBSD, SOlaris, HP-UX)
Open edition sources are available in git repositories: git: //source.pbis.beyondtrust.com/pbis.git
I installed PBIS on Debian Wheezy amd64:
')
Package contents are set to / opt / pbis. A new runscript lwsmd also appears in the system, which actually runs the PBIS agent.
The PAM module pap_lsass.so is added to the system.
Utilities (mostly console), necessary for the functioning of PBIS, as well as facilitating the life of the administrator are placed in / opt / pbis / bin
Before entering the domain, you should make sure that the domain controllers have access and domain names are correctly deployed in ip. (Otherwise, you should configure resolv.conf)
There are two commands for entering the domain: / opt / pbis / bin / domainjoin-cli and / opt / pbis / bin / domainjoin-gui. One of them works on the command line, the second uses libgtk to display the graphical interface.
To enter the domain, you will need to specify: the domain name, login and password of the domain user with the rights to enter the PC into the domain, the container for placing the computer object in the domain is all the same as entering the PC into the windows domain.
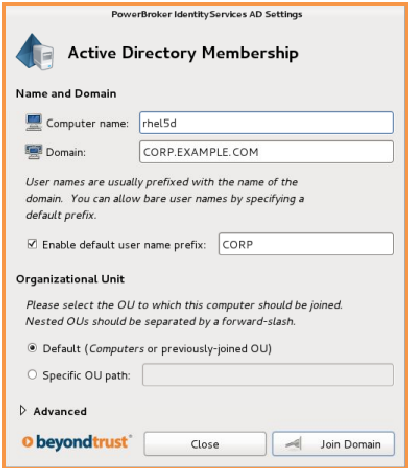
After entering the domain will require a reboot.
Please note - PBIS can work with Active Directory sites. The PBIS client will work with the controllers of the site in which it is located!
After rebooting, both id and getent will give you users and domain groups (national characters are processed correctly. Spaces are replaced with a “^”).
A record with the name of your PC will appear in the DNS domain zone.
Do not rush to log on as a domain user. First, it makes sense (but not necessarily) to configure PBIS.
One of the differences Enterprise version - the ability to manage these settings through the GPO.
It is worth paying attention to the HomeDirPrefix, HomeDirTemplate.
I also immediately set “RequireMembershipOf” - only users, members of groups or SIDs from this list can log in to computers.
Description of each parameter can be obtained, for example:
The parameter value is set like this:
Please note - PBIS does not use SFU attributes or other Acrive Directory attributes to retrieve the user's loginShell, as well as its uid and gid.
loginShell for domain users is set in the PBIS settings, and installation of different loginShell to different users is possible only in the Enterprise version.
The uid is generated as the user’s SID hash.
gid is like the SID hash of the user's primaryGroup.
Thus, on two PCs, the user will always receive the same uid and gid.
Now you can log in as a domain user. After the domain user has logged in, pay attention to the klist output - PBIS will receive the necessary kerberos tickets for the user. After that, you can easily access resources on windows PCs (The main thing is that the software used supports GSSAPI). For example: now I without any additional password requests (and my password is not saved anywhere!) Open any smb domain resources in Dolphin. Also, Firefox (when setting up network.negotiate-auth.trusted-uris) allows you to use SSO when accessing web-portals with domain authorization (of course, if SSO is configured on the server)
Could be so! PBIS fills in /etc/krb5.keytab and keeps it current. Therefore, the server software with GSSAPI support can be configured for SSO.
For example, to access the server via ssh, in the configuration file / etc / ssh / sshd_config (the path on your system may differ)
UsePAM yes
(PBIS provides a module for PAM as well)
It would also be logical to add the “AllowGroups” directive and, using a space, indicate the domain groups whose users you intend to give access to the ssh server.
On a Linux client PC, it is enough to include in the ssh client configuration:
Naturally, the kerberos should be configured on the client Linux computer. The simplest way to fulfill this condition is to also enter the client computer into the domain and work on behalf of the domain user.
On a client Windows PC (domain member), when using Putty, the “Attempt GSSAPI authentification (SSH-2 only)” flag should be set in the properties of the SSH connection (In different versions this item is called differently).
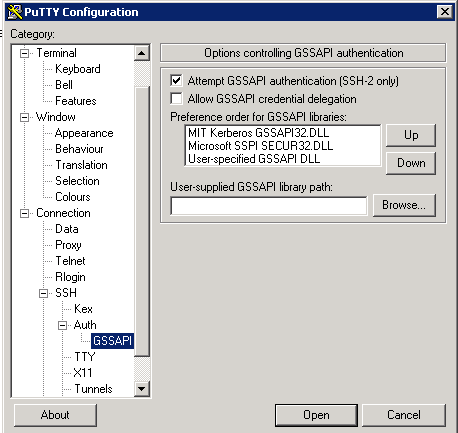
Also in the section Connection -> Data you can put the switch in the position “Use system username”
If you intend to organize ssh administrators access to linux servers in this way, it is a good idea to disable root ssh login and add linux administrators (or even better their domain group) to the sudoers file.
These are not the only scenarios for PBIS. if the article seems interesting to you, next I will write how to organize a samba file server in a domain for domain users without winbind.
Further information on the topic can be obtained at the PowerBroker Identity Services community forum: forum.beyondtrust.com
UPD . The advantages of PowerBroker Identity Services I can include:
UPD 2 Received feedback from the user sdemon72 . Perhaps someone will be useful.
UPD 3: Why the free version of PBIS will not work in a large company
In the free version, only one UNIX iD generation algorithm (uid and gid) by the domain user SID works. So he does not provide uniqueness
these ids. When you have a very old domain or just a lot of users there is a very high risk that two or more users will get the same ID in the system with OpenPBIS. In the paid version, there is a choice between id generation algorithms, but it costs much more than a similar product from Quest Software ; (.
1. Provide access to services on a Linux server for domain users.
2. Launch administrators' server on Linux using your domain credentials.
3. Configure the login to a Linux workstation for domain users, and it is desirable that they could at the same time taste all the delights of SSO (I, for example, do not really like to enter my long, long password often).
Usually, to provide a Linux system for users and groups from an Active Directory domain, they use winbind or configure nss libraries to work with an Active Directory domain controller using an LDAP protocol. But today we will go the other way: we will use PowerBroker Identity Services (The product is also known as Likewise).
Installation
There are two versions of the product: Enterprise and Open. For the implementation of my tasks, the Open version was enough for me, so everything written further will concern her.
You can get the Open version on the manufacturer's website , but you will be provided with a link in exchange for your name, company name and e-mail.
There are 32 and 64 packages in rpm and deb formats. (As well as packages for OS X, AIX, FreeBSD, SOlaris, HP-UX)
Open edition sources are available in git repositories: git: //source.pbis.beyondtrust.com/pbis.git
I installed PBIS on Debian Wheezy amd64:
wget http://download.beyondtrust.com/PBISO/7.1.0/1203/pbis-open-7.1.0.1203.linux.x86_64.deb.sh ./pbis-open-7.1.0.1203.linux.x86_64.deb.sh ')
Package contents are set to / opt / pbis. A new runscript lwsmd also appears in the system, which actually runs the PBIS agent.
The PAM module pap_lsass.so is added to the system.
Utilities (mostly console), necessary for the functioning of PBIS, as well as facilitating the life of the administrator are placed in / opt / pbis / bin
Enter into the domain.
Before entering the domain, you should make sure that the domain controllers have access and domain names are correctly deployed in ip. (Otherwise, you should configure resolv.conf)
There are two commands for entering the domain: / opt / pbis / bin / domainjoin-cli and / opt / pbis / bin / domainjoin-gui. One of them works on the command line, the second uses libgtk to display the graphical interface.
To enter the domain, you will need to specify: the domain name, login and password of the domain user with the rights to enter the PC into the domain, the container for placing the computer object in the domain is all the same as entering the PC into the windows domain.

After entering the domain will require a reboot.
Please note - PBIS can work with Active Directory sites. The PBIS client will work with the controllers of the site in which it is located!
After reboot.
After rebooting, both id and getent will give you users and domain groups (national characters are processed correctly. Spaces are replaced with a “^”).
A record with the name of your PC will appear in the DNS domain zone.
Do not rush to log on as a domain user. First, it makes sense (but not necessarily) to configure PBIS.
/opt/pbis/bin/config --list will display a list of available options.
[Eventlog]
AllowDeleteTo
AllowReadTo
AllowWriteTo
MaxDiskUsage
MaxEventLifespan
MaxNumEvents
[Lsass]
DomainSeparator
SpaceReplacement
EnableEventlog
LogInvalidPasswords
Providers
[Lsass - PAM]
Displaymotd
PAMLogLevel
UserNotAllowedError
[Lsass - Active Directory provider]
AssumeDefaultDomain
CreateHomeDir
CreateK5Login
SyncSystemTime
TrimUserMembership
LdapSignAndSeal
LogADNetworkConnectionEvents
NssEnumerationEnabled
NssGroupMembersQueryCacheOnly
NssUserMembershipQueryCacheOnly
RefreshUserCredentials
CacheEntryExpiry
DomainManagerCheckDomainOnlineInterval
DomainManagerUnknownDomainCacheTimeout
MachinePasswordLifespan
MemoryCacheSizeCap
HomeDirPrefix
HomeDirTemplate
RemoteHomeDirTemplate
HomeDirUmask
LoginShellTemplate
Skeletondirs
UserDomainPrefix
DomainManagerIgnoreAllTrusts
DomainManagerIncludeTrustsList
DomainManagerExcludeTrustsList
RequireMembershipOf
SmartcardEnabled
SmartcardRequiredForLogin
[Lsass - Local provider]
Local_AcceptNTLMv1
Local_HomeDirTemplate
Local_HomeDirUmask
Local_LoginShellTemplate
Local_SkeletonDirs
[User Monitor]
UserMonitorCheckInterval
[System Initialization]
LsassAutostart
EventlogAutostart
GpagentAutostart One of the differences Enterprise version - the ability to manage these settings through the GPO.
It is worth paying attention to the HomeDirPrefix, HomeDirTemplate.
I also immediately set “RequireMembershipOf” - only users, members of groups or SIDs from this list can log in to computers.
Description of each parameter can be obtained, for example:
/opt/pbis/bin/config --detail RequireMembershipOf The parameter value is set like this:
/opt/pbis/bin/config RequireMembershipOf "^Linux" Please note - PBIS does not use SFU attributes or other Acrive Directory attributes to retrieve the user's loginShell, as well as its uid and gid.
loginShell for domain users is set in the PBIS settings, and installation of different loginShell to different users is possible only in the Enterprise version.
The uid is generated as the user’s SID hash.
gid is like the SID hash of the user's primaryGroup.
Thus, on two PCs, the user will always receive the same uid and gid.
Now you can log in as a domain user. After the domain user has logged in, pay attention to the klist output - PBIS will receive the necessary kerberos tickets for the user. After that, you can easily access resources on windows PCs (The main thing is that the software used supports GSSAPI). For example: now I without any additional password requests (and my password is not saved anywhere!) Open any smb domain resources in Dolphin. Also, Firefox (when setting up network.negotiate-auth.trusted-uris) allows you to use SSO when accessing web-portals with domain authorization (of course, if SSO is configured on the server)
But what about SSO when accessing resources on a Linux PC?
Could be so! PBIS fills in /etc/krb5.keytab and keeps it current. Therefore, the server software with GSSAPI support can be configured for SSO.
For example, to access the server via ssh, in the configuration file / etc / ssh / sshd_config (the path on your system may differ)
GSSAPIAuthentication yes And when connecting, specify the domain name of the computer (present in its SPN - otherwise the kerberos ticket will not be able to be issued)UsePAM yes
(PBIS provides a module for PAM as well)
It would also be logical to add the “AllowGroups” directive and, using a space, indicate the domain groups whose users you intend to give access to the ssh server.
On a Linux client PC, it is enough to include in the ssh client configuration:
GSSAPIAuthentication yes Naturally, the kerberos should be configured on the client Linux computer. The simplest way to fulfill this condition is to also enter the client computer into the domain and work on behalf of the domain user.
On a client Windows PC (domain member), when using Putty, the “Attempt GSSAPI authentification (SSH-2 only)” flag should be set in the properties of the SSH connection (In different versions this item is called differently).

Also in the section Connection -> Data you can put the switch in the position “Use system username”
If you intend to organize ssh administrators access to linux servers in this way, it is a good idea to disable root ssh login and add linux administrators (or even better their domain group) to the sudoers file.
These are not the only scenarios for PBIS. if the article seems interesting to you, next I will write how to organize a samba file server in a domain for domain users without winbind.
Further information on the topic can be obtained at the PowerBroker Identity Services community forum: forum.beyondtrust.com
UPD . The advantages of PowerBroker Identity Services I can include:
- Good repeatability (compare the steps in this article with instructions for setting up winbind)
- Caching data from a directory (a domain user can log on to a PC when a domain is not available if his credentials are in the cache)
- PBIS does not require the formation of additional user attributes in the AD directory
- PBIS understands AD sites and works with its site controllers.
- Greater security (samba creates a computer account with a non-expiring password)
- In the paid version (if the need arises), the PBIS agent is managed through a GPO (although this can be deleted as well. If you do not intend to buy it)
UPD 2 Received feedback from the user sdemon72 . Perhaps someone will be useful.
Hello! I tried your recipe on fresh linuxmint-18-mate-64bit, everything turned out with some reservations:
1. With the receipt of the program through the site, I had difficulties (I didn’t want to write a real phone number, but didn’t give a sham one - I received a letter with doubts about it), but found a repository with the latest versions: repo.pbis.beyondtrust.com/apt. html
2. When starting the program, it gives errors, to avoid them, you need to do the following before starting:
2.1. Install ssh:
sudo apt-get install ssh
2.2. To fix /etc/nsswitch.conf:
hosts: files dns mdns4_minimal [NOTFOUND = return]
(i.e. we transfer dns from the end of the line to the second position)
2.3. Amend /etc/NetworkManager/NetworkManager.conf:
# dns = dnsmasq
(I comment on this line)
2.4. Restart network-manager:
sudo service network-manager restart
After that, everything worked out with a bang! I would be very grateful if you make these additions to the article, because In the search for sabzh it falls in the first lines. I cannot leave comments (forbids the site), so I am writing to you personally.
If interested - the story of my research here: linuxforum.ru/topic/40209
Best regards, Dmitry
UPD 3: Why the free version of PBIS will not work in a large company
In the free version, only one UNIX iD generation algorithm (uid and gid) by the domain user SID works. So he does not provide uniqueness
these ids. When you have a very old domain or just a lot of users there is a very high risk that two or more users will get the same ID in the system with OpenPBIS. In the paid version, there is a choice between id generation algorithms, but it costs much more than a similar product from Quest Software ; (.
Source: https://habr.com/ru/post/174407/
All Articles