Carberp: an endless story
The cybercrime group Carberp was one of the first groups that massively used a family of malicious programs aimed at compromising remote banking systems and conducting fraudulent operations against the largest banks in Russia. Many members of the core Carberp group have already been arrested , but this family of malicious programs is still actively and continues to evolve. Our colleague Alexander Matrosov made an analysis of the latest modification of the Carberp banking Trojan, which we want to present below.
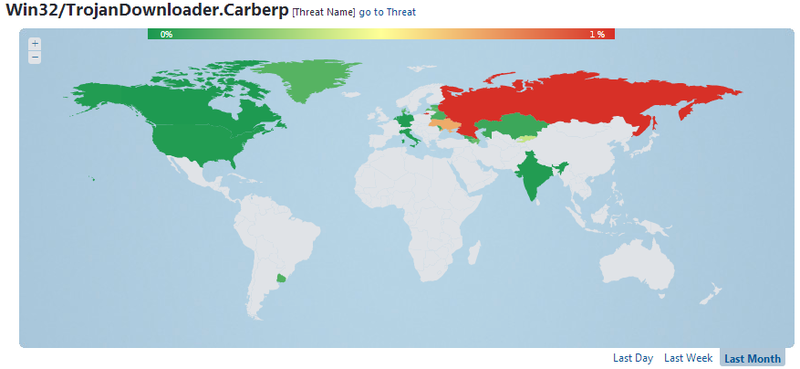
The screenshot shows the statistics of ESET Virus Radar, which shows the regions most affected by Carberp infection during the last month.
')
You can see that the region most affected by Carberp is still Russia . If we look at the history of detection of this malicious code, we will see that the Carberp group was the most active in the spring and summer of 2012 . After the mass arrests in the summer of 2012, the botnet was still active, although the number of detections began to decline.
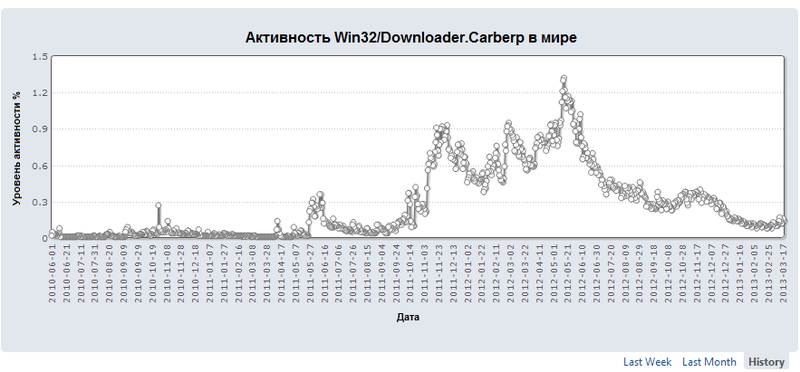
The Carberp Group still holds the first position among similar groups that are involved in banking fraudulent operations in Russia and Ukraine. Next we look at the latest, updated version of the bot code, as well as additional plugins that are used by it.
The method of introducing malicious code
When analyzing one of the latest Carberp droppers, we discovered a special technique for introducing malicious code into trusted processes based on Power Loader . At the start of its execution, the dropper tries to open one of the public (shared) sections and add the shellcode to the end of one of the sections, the list of which is presented below:

Next, the dropper uses similar methods that Gapz uses, with the exception of small changes in the code.

At the final stage, the introduction of malicious code into the trusted explorer.exe process is carried out in order to bypass the antivirus software and execute its further actions as a trusted process.
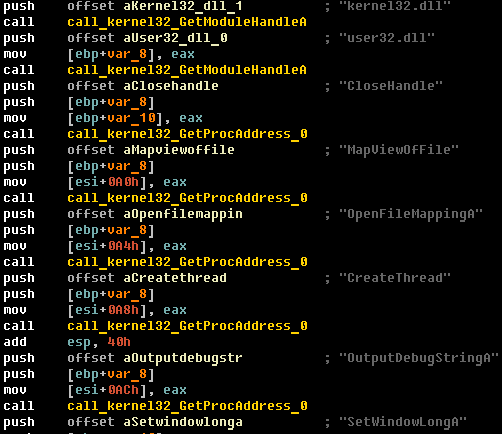
This technique is not new and uses the Shell_TrayWnd implementation method, which was already described in some underground Russian forums a few years ago.
On-the-fly modification of banking software written in Java
We have already described a method for modifying Java code for banking clients in another Trojan family, Win32 / Spy.Ranbyus . Ranbyus modifies the JVM (Java Virtual Machine) during its execution in order to track the execution of the banking software code. Carberp modifies Java banking software using the open source Javassist library. This library allows you to manage java bytecode on the fly (during execution). Malicious code Carberp uses a modification of this bytecode in one of the most popular online banking systems, BIFIT's iBank 2 .
In the process of analyzing the latest Carberp sample, the following lines were found that are present in the client software of the online banking system iBank2, with an interesting link to the correction of Java code.
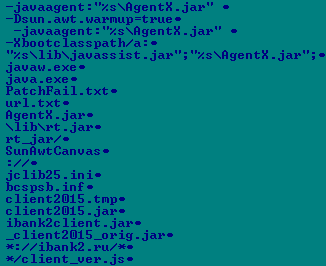
After using the iBank2 client on an infected computer, the malicious code loads the additional module AgentX.jar (detected by ESET as Java / Spy.Banker.AB ). When this module is successfully loaded, Carberp tries to load the Javassist library. Java / Spy.Banker is a special Carberp component designed to modify payment documents on the fly.
The decompiled Java class, which is used to modify the client's iBank2 code, looks like this:
After making changes to iBank2, attackers can control all payments made using this banking software. BIFIT's iBank2 system does not check the integrity of its code, and after modifying it, it continues to work as if nothing had happened, that is, it can perform cash transaction operations. But in this case, cash transactions go through the cybercrime group Carberp.
The Java / Spy.Banker module has the functionality to bypass the two-factor authentication system using one-time passwords. The decompiled java class to bypass this check is presented below.
The decompiled code to confirm the payment in this case is as follows:

The AgentX module is not an ordinary malware component, since it does not change the Java system itself, but uses a legitimate library to modify the code. It presents a certain difficulty in recognizing malicious activity in AgenX.jar without manual analysis of this module. At the time of this writing, the AgentX.jar module had a very low detection rate.
Using legitimate software as a component of malicious code
The malicious code described by us, which uses legitimate libraries to perform its functions, is not alone. Last week , information appeared about a targeted attack that some European countries underwent. The attack was carried out using a special malicious toolkit TeamSpy. TeamSpy used the modified components of the well-known TeamViewer software. ESET discovered this backdoor, which has been used by TeamViewer modules since 2010 ( Sheldor-Shocked ). The malicious Win32 / Sheldor code was used by the cybercriminal group Carberp to manually transfer money from infected systems, starting in 2010. The Carberp group uses other legitimate software for remote access to infected computers; In the table below we list the variations of such software used by the Carberp group.
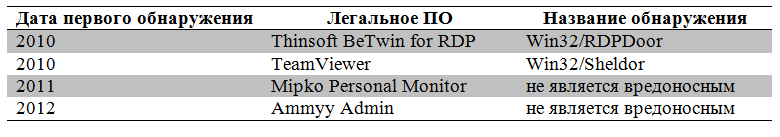
Using legitimate software tools by cybercrime groups is one of the ways to get remote access to infected systems. In this case, it greatly complicates the detection of malicious activity. Malicious code families such as Win32 / Sheldor and Win32 / RDPdoor make some changes to the original components. At the same time, software such as Mipko and Ammyy are used unchanged. In some cases, it would be inappropriate to detect legitimate software as malicious, from an antivirus point of view.
Conclusion
In this post, we summarized the latest changes that were recorded in the activity of the cybercrime group Carberp. The most interesting changes relate to the Java / Spy.Banker component (AgentX.jar) and the most popular banking software in Russia and Ukraine, which is attacked through a modification of the java-code. Another interesting observation is the increasing use of legal software as components of malicious code to gain remote access. In this case, the detection mechanism of such software that would lead to the absence of false positives (false positive) seems to be rather difficult, especially if attackers modify this software every few months.
The screenshot shows the statistics of ESET Virus Radar, which shows the regions most affected by Carberp infection during the last month.

')
You can see that the region most affected by Carberp is still Russia . If we look at the history of detection of this malicious code, we will see that the Carberp group was the most active in the spring and summer of 2012 . After the mass arrests in the summer of 2012, the botnet was still active, although the number of detections began to decline.

The Carberp Group still holds the first position among similar groups that are involved in banking fraudulent operations in Russia and Ukraine. Next we look at the latest, updated version of the bot code, as well as additional plugins that are used by it.
The method of introducing malicious code
When analyzing one of the latest Carberp droppers, we discovered a special technique for introducing malicious code into trusted processes based on Power Loader . At the start of its execution, the dropper tries to open one of the public (shared) sections and add the shellcode to the end of one of the sections, the list of which is presented below:

Next, the dropper uses similar methods that Gapz uses, with the exception of small changes in the code.

At the final stage, the introduction of malicious code into the trusted explorer.exe process is carried out in order to bypass the antivirus software and execute its further actions as a trusted process.

This technique is not new and uses the Shell_TrayWnd implementation method, which was already described in some underground Russian forums a few years ago.
On-the-fly modification of banking software written in Java
We have already described a method for modifying Java code for banking clients in another Trojan family, Win32 / Spy.Ranbyus . Ranbyus modifies the JVM (Java Virtual Machine) during its execution in order to track the execution of the banking software code. Carberp modifies Java banking software using the open source Javassist library. This library allows you to manage java bytecode on the fly (during execution). Malicious code Carberp uses a modification of this bytecode in one of the most popular online banking systems, BIFIT's iBank 2 .
In the process of analyzing the latest Carberp sample, the following lines were found that are present in the client software of the online banking system iBank2, with an interesting link to the correction of Java code.

After using the iBank2 client on an infected computer, the malicious code loads the additional module AgentX.jar (detected by ESET as Java / Spy.Banker.AB ). When this module is successfully loaded, Carberp tries to load the Javassist library. Java / Spy.Banker is a special Carberp component designed to modify payment documents on the fly.
The decompiled Java class, which is used to modify the client's iBank2 code, looks like this:

After making changes to iBank2, attackers can control all payments made using this banking software. BIFIT's iBank2 system does not check the integrity of its code, and after modifying it, it continues to work as if nothing had happened, that is, it can perform cash transaction operations. But in this case, cash transactions go through the cybercrime group Carberp.
The Java / Spy.Banker module has the functionality to bypass the two-factor authentication system using one-time passwords. The decompiled java class to bypass this check is presented below.

The decompiled code to confirm the payment in this case is as follows:

The AgentX module is not an ordinary malware component, since it does not change the Java system itself, but uses a legitimate library to modify the code. It presents a certain difficulty in recognizing malicious activity in AgenX.jar without manual analysis of this module. At the time of this writing, the AgentX.jar module had a very low detection rate.
Using legitimate software as a component of malicious code
The malicious code described by us, which uses legitimate libraries to perform its functions, is not alone. Last week , information appeared about a targeted attack that some European countries underwent. The attack was carried out using a special malicious toolkit TeamSpy. TeamSpy used the modified components of the well-known TeamViewer software. ESET discovered this backdoor, which has been used by TeamViewer modules since 2010 ( Sheldor-Shocked ). The malicious Win32 / Sheldor code was used by the cybercriminal group Carberp to manually transfer money from infected systems, starting in 2010. The Carberp group uses other legitimate software for remote access to infected computers; In the table below we list the variations of such software used by the Carberp group.

Using legitimate software tools by cybercrime groups is one of the ways to get remote access to infected systems. In this case, it greatly complicates the detection of malicious activity. Malicious code families such as Win32 / Sheldor and Win32 / RDPdoor make some changes to the original components. At the same time, software such as Mipko and Ammyy are used unchanged. In some cases, it would be inappropriate to detect legitimate software as malicious, from an antivirus point of view.
Conclusion
In this post, we summarized the latest changes that were recorded in the activity of the cybercrime group Carberp. The most interesting changes relate to the Java / Spy.Banker component (AgentX.jar) and the most popular banking software in Russia and Ukraine, which is attacked through a modification of the java-code. Another interesting observation is the increasing use of legal software as components of malicious code to gain remote access. In this case, the detection mechanism of such software that would lead to the absence of false positives (false positive) seems to be rather difficult, especially if attackers modify this software every few months.
Source: https://habr.com/ru/post/174281/
All Articles