Full scan / 0
Internet Census 2012 website internetcensus2012.bitbucket.org has published the results of scanning all existing IPv4 addresses. A scan of this magnitude was made possible thanks to a botnet of 420,000 unprotected devices.
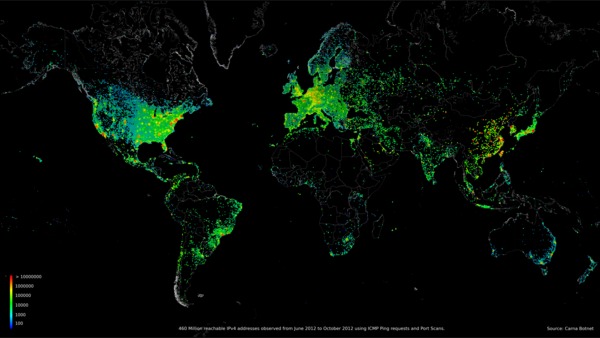
The idea of such a scan came to the author two years ago, when using the Nmap Scripting Engine he decided to try to log in to random IP addresses with standard login: password (root: root) via telnet, and a sufficient number of devices were found where authorization was successful. Then a worm was created that scanned a specific address range and, when an unprotected device was detected, copied itself there. A new copy began to scan its range and so exponentially. Thus, a fairly large distributed botnet named Carna was formed.
During the ten months of 2012, all IP addresses in the IPv4 address space were scanned, scanning was performed by the following methods: sending service packages to all popular port numbers, ping, reverse DNS request, and SYN request.
')
As a result of scanning, the base turned out to be 9 terabytes of volume, after archiving, with the help of ZPAQ, the volume became equal to 568 gigabytes and all this is available for downloading here internetcensus2012.bitbucket.org/download.html
In total, the database has:
-52 billion ICMP pings
-80 million TCP / IP prints
-10.5 billion responses to a reverse DNS query
-180 billion scans on service ports
-68 million traceroute records
-2.8 billion responses to a SYN request for 660 million IP addresses and 71 billion ports tested
The author hopes that researchers will be able to benefit from the collected data.

The idea of such a scan came to the author two years ago, when using the Nmap Scripting Engine he decided to try to log in to random IP addresses with standard login: password (root: root) via telnet, and a sufficient number of devices were found where authorization was successful. Then a worm was created that scanned a specific address range and, when an unprotected device was detected, copied itself there. A new copy began to scan its range and so exponentially. Thus, a fairly large distributed botnet named Carna was formed.
During the ten months of 2012, all IP addresses in the IPv4 address space were scanned, scanning was performed by the following methods: sending service packages to all popular port numbers, ping, reverse DNS request, and SYN request.
')
As a result of scanning, the base turned out to be 9 terabytes of volume, after archiving, with the help of ZPAQ, the volume became equal to 568 gigabytes and all this is available for downloading here internetcensus2012.bitbucket.org/download.html
In total, the database has:
-52 billion ICMP pings
-80 million TCP / IP prints
-10.5 billion responses to a reverse DNS query
-180 billion scans on service ports
-68 million traceroute records
-2.8 billion responses to a SYN request for 660 million IP addresses and 71 billion ports tested
The author hopes that researchers will be able to benefit from the collected data.
Source: https://habr.com/ru/post/173471/
All Articles