New Trojan with a valid digital signature LLC Mail.Ru disguises as an update of popular programs
On a quiet Saturday evening, my mother peacefully Youtube Youtube to care for the cyclamens and suddenly a banner formed to the left of the video (unfortunately, there will be no screenshot because the banner could not be reproduced) calling for Skype to be updated. After clicking on it, there was a redirect to _http: //easyupdate.ru/skype/, which looks something like this ...
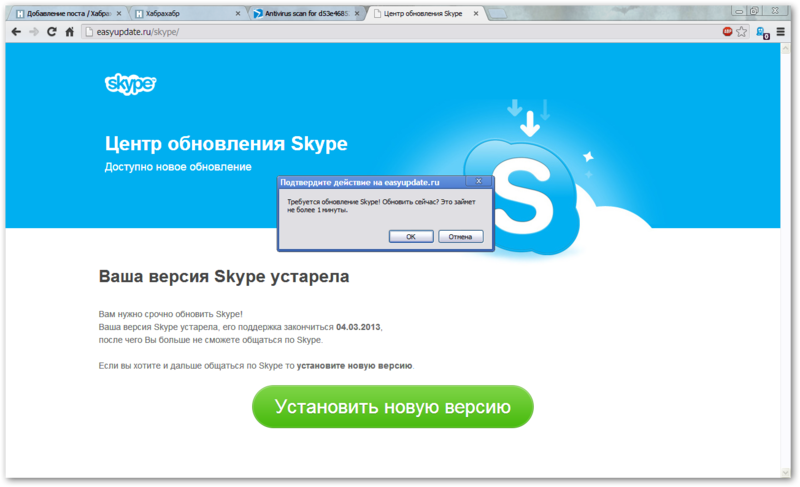
My mother is not a very experienced user and the phrases in the spirit of “Your version of Skype is outdated, its support will end on 03/04/2013, after which you will no longer be able to communicate via Skype” they are very frightened, so she pressed “Cancel” and called me. At first, I decided that it would be about a banal Skype update and with a sigh I connected with Teamviewer, just going to poke a couple of buttons and disconnect. To my shame, with all my many years of experience, I even managed to launch an “update” downloaded from easyupdate.ru, but after seeing that the file was signed for some reason by the publisher “LLC Mail.Ru” and not Skype, at the last moment forbade performance and realized that the evening will be interesting and long. Having praised my mother for vigilance, I began to study the fresh scheme of filling the botnet.
So, first of all, let's look at the file properties:

')
Strange, only 74 KB, somehow not enough even for a web installer. We look at the digital signature, what kind of “LLC Mail.Ru” is, can someone again drag a similar legal entity name through Thawte?

Strangely, a digital signature certificate is very similar to a real one from Mail.Ru:
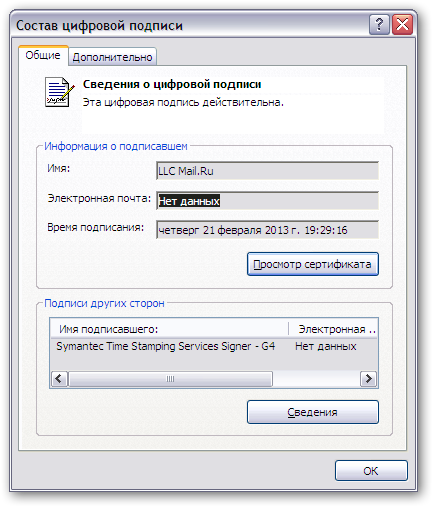
They have the same validity period, from 09/12/2011 to 07/02/2014, however, the Mail.ru Agent’s digital signature has signatures of other parties: Symantec Time Stamping Services Signer. All exe files are subscribed on the fly before returning to download to the browser, this is indicated by the dynamically changing time of file signing.
Total, we have three options:
1. This is the real digital signature of Mail.ru, the private key of which was somehow stolen and is now used to sign Malvari
2. This is a real digital signature Mail.ru, which Mail.ru itself for some reason uses to sign Malvari
3. This is a fake digital signature of Mail.ru, which was somehow compromised (which is unlikely, for RSA 2048 bits)
Googling easyupdate.ru, and finding nothing sensible in the output, I looked at all the links for site: easyupdate.ru and found that, besides Skype, there are landing pages for all popular browsers:
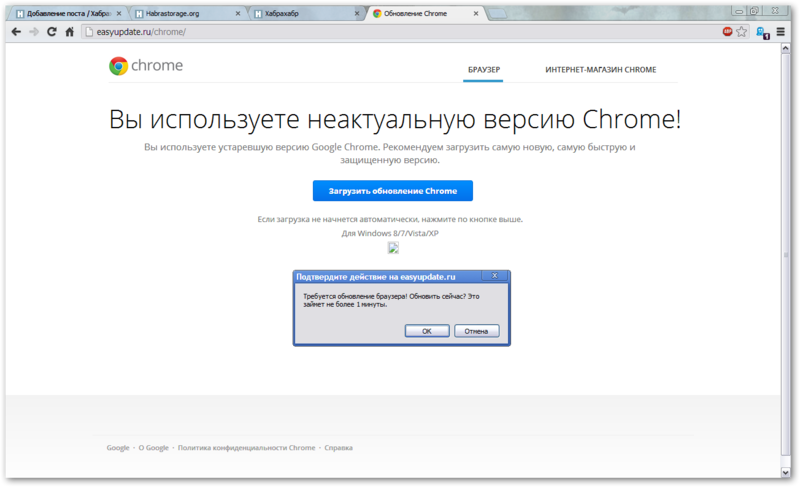



They are very much related to the nice pop-up javascript confirmation that the exe file starts downloading without even having to bother to check which button the user pressed, OK or Cancel.
Thus, we obtained 5 samples (links lead to the results of scanning the Virustotal files):
chromesetup.exe , firefox-setup.exe , ie-setup-full.exe , opera_int_setup.exe and skypesetup.exe
opera_int_setup.exe and ie-setup-full.exe have not yet been scanned before me, that is, the spread of the infection was started quite recently, but 8-9 antiviruses out of 46 reacted to the other files. Kaspersky is for some reason the only one who has classified exe as "Not a virus": "not-a-virus: HEUR: Downloader.Win32.LMN.a". Perhaps this decision was positively influenced by a digital signature, but this is better than the solution of Microsoft’s built-in antivirus program from Microsoft, which did not see any threat in the samples at all.
For chromesetup.exe, information is available on the behavior, apparently provided by some of the anti-virus companies, in particular network activity:

So, we have two strange domains and a link to the Mail.ru subdomain, let's take a closer look at them:
easyupdate.ru was registered on January 30, 2013 with the hiding of information about the owner (Private person), this service is available and free of charge with most Russian domain registrars. At the root of the site we are greeted by 404:
The second link apparently used a URL redirect vulnerability on one of the Mail.ru subdomains, however, it appears that the vulnerability has already been fixed. Perhaps the attackers decided that such a link is easier to pass through the firewall.
The dwnfile.ru domain is registered on February 1, 2013 with hiding information about the owner.
The text of the landing page also contains links to the following domains:
uprgadotesbest.com - was registered on December 26, 2012 through PrivacyProtect.org and currently has the status of "Locked"
uploadeasy.ru - the domain is not registered at all, apparently forgotten in the bustle of rolling out “in production”, cybersquatters, fly in!
All domains were registered through Reg.ru.
In addition, the Trojan disables the use of a proxy in the registry, which obviously affects the operation of IE and Chrome, Firefox and Opera have their own proxy settings.
Further, the link _http: //dwnfile.ru/get_xml? File_id = 18499626 returns us the following XML:
, , «», guid — , partner — , , , , . profitraf1, : profitraf.ru
, :

, , , . « » :
, , . , , 215 , :
, , , Mail.ru , . , , , . , Windows.
, Mail.ru, . , , «» , , , , , «» . , , Mail.ru, . , , , .
. , , «easyupdate.ru».
Mairon .

My mother is not a very experienced user and the phrases in the spirit of “Your version of Skype is outdated, its support will end on 03/04/2013, after which you will no longer be able to communicate via Skype” they are very frightened, so she pressed “Cancel” and called me. At first, I decided that it would be about a banal Skype update and with a sigh I connected with Teamviewer, just going to poke a couple of buttons and disconnect. To my shame, with all my many years of experience, I even managed to launch an “update” downloaded from easyupdate.ru, but after seeing that the file was signed for some reason by the publisher “LLC Mail.Ru” and not Skype, at the last moment forbade performance and realized that the evening will be interesting and long. Having praised my mother for vigilance, I began to study the fresh scheme of filling the botnet.
Digital signature puzzle
So, first of all, let's look at the file properties:

')
Strange, only 74 KB, somehow not enough even for a web installer. We look at the digital signature, what kind of “LLC Mail.Ru” is, can someone again drag a similar legal entity name through Thawte?

Strangely, a digital signature certificate is very similar to a real one from Mail.Ru:

They have the same validity period, from 09/12/2011 to 07/02/2014, however, the Mail.ru Agent’s digital signature has signatures of other parties: Symantec Time Stamping Services Signer. All exe files are subscribed on the fly before returning to download to the browser, this is indicated by the dynamically changing time of file signing.
Total, we have three options:
1. This is the real digital signature of Mail.ru, the private key of which was somehow stolen and is now used to sign Malvari
2. This is a real digital signature Mail.ru, which Mail.ru itself for some reason uses to sign Malvari
3. This is a fake digital signature of Mail.ru, which was somehow compromised (which is unlikely, for RSA 2048 bits)
Googling easyupdate.ru, and finding nothing sensible in the output, I looked at all the links for site: easyupdate.ru and found that, besides Skype, there are landing pages for all popular browsers:




They are very much related to the nice pop-up javascript confirmation that the exe file starts downloading without even having to bother to check which button the user pressed, OK or Cancel.
Virustotal
Thus, we obtained 5 samples (links lead to the results of scanning the Virustotal files):
chromesetup.exe , firefox-setup.exe , ie-setup-full.exe , opera_int_setup.exe and skypesetup.exe
opera_int_setup.exe and ie-setup-full.exe have not yet been scanned before me, that is, the spread of the infection was started quite recently, but 8-9 antiviruses out of 46 reacted to the other files. Kaspersky is for some reason the only one who has classified exe as "Not a virus": "not-a-virus: HEUR: Downloader.Win32.LMN.a". Perhaps this decision was positively influenced by a digital signature, but this is better than the solution of Microsoft’s built-in antivirus program from Microsoft, which did not see any threat in the samples at all.
For chromesetup.exe, information is available on the behavior, apparently provided by some of the anti-virus companies, in particular network activity:

So, we have two strange domains and a link to the Mail.ru subdomain, let's take a closer look at them:
easyupdate.ru was registered on January 30, 2013 with the hiding of information about the owner (Private person), this service is available and free of charge with most Russian domain registrars. At the root of the site we are greeted by 404:
404 Not Found
Found this server!
Powered By LiteSpeed Web Server
LiteSpeed Technologies is not responsible for this web site!
The second link apparently used a URL redirect vulnerability on one of the Mail.ru subdomains, however, it appears that the vulnerability has already been fixed. Perhaps the attackers decided that such a link is easier to pass through the firewall.
The dwnfile.ru domain is registered on February 1, 2013 with hiding information about the owner.
The text of the landing page also contains links to the following domains:
uprgadotesbest.com - was registered on December 26, 2012 through PrivacyProtect.org and currently has the status of "Locked"
uploadeasy.ru - the domain is not registered at all, apparently forgotten in the bustle of rolling out “in production”, cybersquatters, fly in!
All domains were registered through Reg.ru.
In addition, the Trojan disables the use of a proxy in the registry, which obviously affects the operation of IE and Chrome, Firefox and Opera have their own proxy settings.
Affiliate program
Further, the link _http: //dwnfile.ru/get_xml? File_id = 18499626 returns us the following XML:
<?xml version="1.0" encoding="utf-8"?>
<file>
<dltype>simple</dltype>
<name><![CDATA[chromesetup.exe]]></name>
<url><![CDATA[http://easyupdate.ru/chrome/ChromeSetup.exe]]></url>
<partner_new_url><![CDATA[http://dwnfile.ru/software_install?guid=$__GUID&sig=$__SIG&file_id=18499626]]></partner_new_url>
<partner_online_url><![CDATA[http://dwnfile.ru/online_activity?guid=$__GUID&sig=$__SIG&sid=1469&pid=775]]></partner_online_url>
<referer>profitraf1</referer>
<internet></internet>
<referer_inet>profitraf4</referer_inet>
<internet_silent></internet_silent>
<file_size><![CDATA[0]]></file_size>
<partner_new_url_inet><![CDATA[http://dwnfile.ru/software_install?guid=$__GUID&sig=$__SIG&ovr=$__OVR&file_id=18499626&browser=1]]></partner_new_url_inet>
<mpcln><![CDATA[9516]]></mpcln>
</file>, , «», guid — , partner — , , , , . profitraf1, : profitraf.ru
, :

, , , . « » :
(mp3, , — ), . , , profidownload.ru. ( ). , . . .
, , . , , 215 , :
, «» — SMS-, «» . ( ) — Mail.Ru. .
, , , Mail.ru , . , , , . , Windows.
, Mail.ru, . , , «» , , , , , «» . , , Mail.ru, . , , , .
12
. , , «easyupdate.ru».
Mairon .
Source: https://habr.com/ru/post/172393/
All Articles