SIEM: Frequently Asked Questions
Instead of the preface
I welcome everyone who reads this post!
Recently, I have often been asked questions related to the SIEM. Finally, the communication with a friend, with whom we gathered in the evening to drink a beer, finished off and somehow imperceptibly turned to the topic of security. He said that they are going to implement the SIEM - because "it helps protect the infrastructure." And they even found people who agree to do it “cheaply and quickly.” It was then that I became wary ... As it turned out, they thought that the introduction of SIEM would at once save them from troubles such as data leakage, and besides, it would be inexpensive and quick - they said they found a system that does not require tuning. Gee, thought Stirlitz, and decided to scribble his thoughts on this issue in order to send questioners to a printed source. I will try to be brief and cover the most frequently asked questions.
Some theory
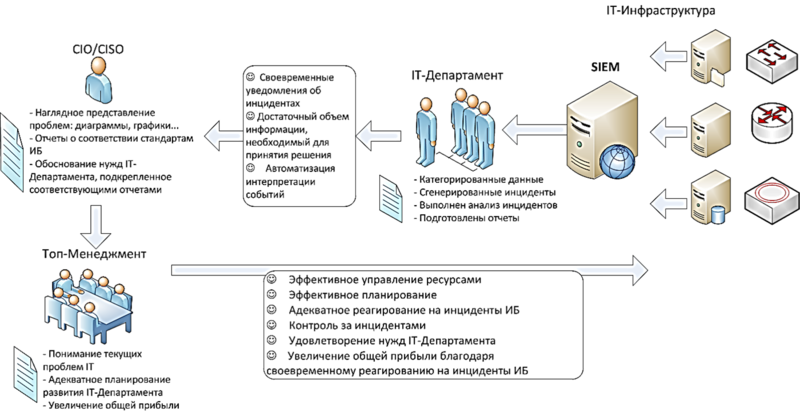
I do not want to describe in detail the theoretical aspects of the work of modern SIEM and their classification, because The topic is well described. In short, what is SIEM? SIEM is S ecurity Information and E vent M anagement. As the name implies, it is “by itself” not capable of preventing or protecting something. This system is designed to analyze information from various other systems, such as DLP, IDS, antiviruses, various hardware (Fortinet, routers, etc.) and further identify deviations from the standards by some criteria. As soon as we have identified a deviation - we generate an incident. At the heart of the work of the SIEM is, oddly enough, almost naked mathematics and statistics. The “bare” SIEM does not carry any protective functions.
On the technical aspects of the work of systems of this class, I recommend to read through articles on www.securitylab.ru or on Habré in the Positive Technologies blog. Also, some information can be found in my post: habrahabr.ru/post/159929 .
Actually questions
Here I will try to give answers to the most frequently asked questions.
')
You say - SIEM itself does not protect. Why is she then?
SIEM is needed precisely for collecting and analyzing information. Information comes from various sources - such as DLP systems, IDS, routers, firewalls, user workstations, servers ...
Agree - just a chore to manually view the logs from a large number of sources. In addition, there are situations when seemingly innocuous events received from various sources, in the aggregate, carry a threat. Suppose when a letter is sent with a company-sensitive data person who has the right to do so, but to an address outside his usual circle of addresses to which he sends. The DLP system may not catch this, but using the accumulated statistics, the SIEM will generate an incident based on this.
OK, the incident happened - but the employee who allowed the leak, in any way denies. How to prove? SIEM is able to provide all the necessary evidence base suitable for both internal investigations and the court. Strictly speaking, this is one of its main destinations. At the time of the incident, all interested parties will also be notified.
And complement the bar - from time to time you need to conduct audits for compliance with any standards. This is SIEM too. Of the additional features - the SIEM after the implementation can indirectly help you to get money for the additional purchase of some other information security tools: for example, you attach a report as a justification, which shows that most of the incidents received are closed by the means you request. Below is an illustration of when SIEM can be useful.
Suppose you do not have a SIEM. Then you have:

And now we have set the SIEM:
Pictures, of course, do not claim to the ultimate truth, but simply give an idea about why you might need a SIEM.
Let's summarize what the SIEM system can do:
- Analyze events and create alerts for any anomalies: network traffic, unexpected user actions, unidentified devices, etc.
- Check for compliance with standards (PCI DSS, COBIT, etc.). Not without pitfalls, really.
- Create a beautiful report. Including customized directly for your needs. For example, a daily report on incidents, a weekly report on the TOP-10 violators, a report on the health of devices, etc. Reports are configured flexibly, as are their recipients.
- Monitor events from devices / servers / critical systems, create appropriate alerts for interested parties.
- Collect evidence base on incidents.
- To help beat out funds for information security systems from adequate managers.
- If you have a vulnerability scanner, SIEM will partially save you from headaches in terms of risk.
Who is the main consumer of SIEM?
At the moment - the banking sector. Because
a) They need to regularly conduct compliance audits.
b) Banks work with sensitive information, so in the event of incidents, it is important to know who has ever leaked, was it a malicious act or accidental, and what were the attendant factors.
c) External auditors and the presence of a SIEM is sometimes put in +
The second category of consumers is large enterprises (or geographically distributed enterprises) that daily generate a ton of events of various properties and are simply physically impossible to track, and managers want to “keep abreast” in order to quickly respond to possible incidents.
The third category is large enterprises who have already known the charm of an unexpectedly discovered information security incident.
Accordingly, it is possible to roughly outline the circle of those to whom, perhaps, the introduction of SIEM is relevant:
- There must be a large / geographically extensive infrastructure. How big? Well, probably, this is not 100 cars :) At least 1000-1300.
- There should be information security systems - from antiviruses to DLP, IDS, IDM, etc. The more such systems, the better. In my opinion, in an organization that is going to implement SIEM, there should already be a DLP.
- Availability of devices that require monitoring. Many out-of-the-box SIEM systems support a sufficiently large number of vendors, including some specific messages, and therefore are able to predict in advance any critical situations. Say, the wireless network controller generates a message that the number of users is close to critical - based on this, the SIEM is able to generate an alert, the notification of which will be sent to the interested party.
- Must be money !!! And the understanding that SIEM does not pay off in six months.
How long will the implementation take? What works need to lay?
I will give an approximate list of works:
- Inspection of infrastructure and decision-making on the method of implementation. Those. - whether we will process all events in one place or need parallelization.
- Formation and approval of TK.
- Development of the administrator's manual and user manual.
- Installation and basic setup of SIEM. This means setting up the SIEM server / piece of hardware integration, writing it to the network, making some specific settings.
- Configure event sources. Setting up DLP itself, servers and workstations (possibly with the installation of agents), hardware in the network to send events to the SIEM collector.
- Writing additional rules of response. Out of the box, nothing will work properly; you need to add rules for a particular organization. Also at this stage, the first shoals come out in terms of crookedly configured sources / basic settings of the SIEM components.
- Test operation and the accumulation of statistics. An important stage. Lay from one to four months, depending on the size of the organization. Get ready for a flurry of incidents, 95% of which are so-called. False-Positive, i.e. false.
- Correction and addition of correlation rules. It is carried out in parallel with the previous stage, in fact, this is SIEM training, fine tuning for specific needs.
- Completion of test operation. Here it is better to put a few days on the final grinding system. It is no longer necessary to make any major changes here, otherwise goto on p.5 or p.6
- Conduct acceptance tests. Writing cases and running them. I think everything is clear.
On average, if you do everything “according to your mind,” then the minimum period you need to count on is half a year. You will feel some advantages from the introduction of SIEM in 5-6 months after the system is operating in a “combat” mode. The price of the work will be appropriate, add to it the cost of licenses, and, possibly, training security administrators to work with SIEM.
What so much work? What is so expensive? Here XXX promised to do everything for a week for a hundred thousand rubles!
There is a wonderful picture that gives an answer to this question:

SIEM refers to systems that do not provide all the declared functionality “out of the box” and without a prior thorough examination and further careful customization for a specific customer turn into garbage, the headache of the IT department and those responsible for security.
Will there be False-positive events after the start of operation?
Will stay. If you are told that they will not - spit in the face of the manager that assures you of this. In this case, either you will have omissions of incidents that really require attention (tuning curve), or you are not offered SIEM. The total number of false-positive events will be affected by the number of sources from which SIEM is rowing data and the accuracy of writing correlation rules, as well as the size of the accumulated statistics in the database. And anyway, when you connect a new computer or an unexpected (but coordinated) “inversion” of the user, an incident will be created. Here, the principle of “better to perebdet than to come short”. Still, the number of such false events will be small, and the accuracy of determining incidents is higher than if you analyzed manually.
It should also be understood that the SIEM is part of the technical measures to ensure the organization’s information security. And she will not save from the fact that an employee drunk something somewhere in the bar or if she forgets the prototype of your development in the same bar.
SIEM can prevent incidents ...
NOT! SIEM itself is not able to prevent anything. If an incident is recorded in it, then it has already occurred. Another conversation - what could not be the continuation of the incident, because DLP blocked the transfer, the antivirus killed the Trojan, the user changed his mind to merge information after the warning, etc.
But SIEM will provide you with evidence that can be used for internal disassembly, in court or to demonstrate to the offender and say “Vasya! do not do that! Big brother sees everything. ”
What vendor to choose?
You will not answer in advance, a normal integrator usually studies the client's infrastructure, his needs, finds out how much money he is willing to part with. Then offers a vendor, because on the one hand, they are similar, and on the other, McAfee, for example, scales worse than IBM QRadar, and both of them may not support any specific program for which there is already a ready-made connector for ArcSight.
How much hard disk is required to store data?
Too ambiguous question. This is calculated depending on the number of sources, the intensity of the generation of events (which is tied to the number of users) and the voracity of a particular vendor. Naturally, "the more the better." Usually each vendor has “iron” options, and “virtual”, iron options, as a rule, in terms of stuffed equipment, do not represent anything interesting and do not possess any special properties, except for design and size. But they are often unnecessarily expensive. But according to the size of the hard drives installed in them, you can roughly estimate how comfortable the system will feel on your configuration. The size of the hard disk, as well as the intensity of the flow of events for which the servers are calculated, are usually indicated in the datasheet.
Keep in mind that the speed and reliability of the disk subsystem is crucial, so RAID is vital here, you also need to pay attention to the performance of each HDD that is part of the array. SSD, although fast, is currently undesirable due to the high cost of storing information and a smaller resource compared to conventional HDDs.
UPD from comments A suggested article on this topic. Thank you lless .
Is it hard to work with her?
No, it is not difficult - in modern SIEM, the entire interface is intuitive, works in most cases, as a WEB-application (through a browser). If necessary, you can separate the different sections to which will be accessed by roles.
Can I write the correlation rule myself?
Yes, it is possible, there are no difficulties - the creation of rules in most SIEM is maximally visualized, only where there can be difficulties - the rules can use regular expressions "in the pure form". In most cases, the regular expression syntax is standard - if a person is familiar with perl, for example, he can write a syntactically correct regular expression. The main difficulty here is to present the logic of the work as a whole, since adding rules may entail a change in the logic of other rules for the formation of the incident.
UPD from the comments I would like to add that, as part of the SIEM, there are sometimes graphical utilities for testing the developed regular expressions. In particular, in ArcSight ESM, this utility is called - regex. Thank you eafanasov for the addition.
Is it possible to make support for the source of events YYY?
First, you need to see if the source (program or piece of hardware) can send events as a SYSLOG. If yes, then the problem is solved - all SIEM leading vendors with syslog work.
If the program is some kind of specific, then in most cases you can write an event handler or a connector, but this means additional labor and cash costs.
At the same time, modern out-of-the-box SIEM support a significant number of sources + manufacturers add them in their updates.
UPD from comments As correctly suggested, different sources may call the same event differently. For example, the firewall of one vendor will say “deny” in the log, another “discard”, the third “drop”, and SIEM should categorize all these events into a single format, for example “Firewall / Access / Failure”, i.e. may require additional handler. Thank you bondbig for the comment.
Do I need any support for SIEM?
Yes, it is necessary. Starting from the actual server maintenance (database optimization and other service tasks — most SIEM are able to do this on their own) and ending with the fact that large organizations tend to grow, information security products are updated and added — and then adjustment of the rules is required.
We summarize
Here I tried to highlight the general questions that arise among people; Unfortunately, the specificity of the SIEM is such that it is difficult to give concrete figures for an abstract organization - you need to know the specific specifics. For a preliminary understanding of the situation, you can use approximately a list of questions that are desirable to answer before making a decision about finding an integrator who will do everything for you (especially since he will also ask you about it):
- What do I expect in the end from introducing SIEM? (you can rephrase as: what everyday tasks are you planning to do with SIEM?)
- Total number of users?
- Are there any branches, geographically remote, events from which must also be taken into account?
- What IS systems do we already have?
- Is network flow analysis planned (sFlow, netFlow ...)?
- Do you plan to shoot events from servers, AWP users?
- Are there any specific devices in the infrastructure, the events from which must also be taken into account?
- How often do incidents requiring intervention / investigation occur? (<10 incidents / day, 10 ... 50 incidents / day, 50 ... 100 incidents / day,> 100 incidents / day)
- Need to check for compliance with any standards? If so, how?
- Who will be responsible for handling incidents?
- After what time do I expect to get some tangible results?
- How much are we willing to spend on the implementation and purchase of SIEM?
- Who will support SIEM and how much are we willing to pay for support?
A couple of comments ... If you can not answer the 1st question - then I advise you to read the literature and google - you should not hope that the integrator will tell you everything at once. Because the phone will tell you the marketing material. At the first meeting, you will learn that the integrator naturally has experience in this field. But! Why did you need SIEM - engineers will understand it with your words, because you should know the needs of a particular organization and the features of its operation better than them. Therefore, in the absence of a complete image - what do you want to get in the end - you will get what the integrator thought would suit you best. If there is an image - what you want to see in the end - some particulars will inevitably be corrected, but the end result, as a rule, will satisfy you. If you answer the 2nd question - the number of users - is less than 1000, then you probably do not need SIEM. If you only have an antivirus and firewall from your security tools, then all the more so. SIEM is quite a specific product, which is not really necessary for everyone.
On this, perhaps, finish; if you think that you haven't covered any general questions, please write in the letters.
Thank you all for your attention!
Source: https://habr.com/ru/post/172389/
All Articles