Caphaw Banking Trojan attacks European banks using web injects plugin
Banking malware Win32 / Caphaw (also known as Shylock ) was used by attackers in carrying out attacks on large European banks, which lasted more than a year. This threat began to spread in the fall of 2011. Our colleague, Alexander Matrosov, carried out a detailed analysis of this banking trojan, and we want to present the most interesting findings made during this analysis. Win32 / Caphaw differs from other similar threats by the fact that it is one of the few Trojans that can automatically steal money from a bank account when a user is actively working with this account.

The geography of distribution shows that Win32 / Caphaw prevails in England, Italy, Denmark and Turkey. According to our statistics ESET Virus Radar, the period of time that accounts for the greatest activity of this Trojan is December 2012. The following screenshot shows the geography of Win32 / Caphaw distribution for the last week (at the time of the study).
')

Fig. The geography of the prevalence of Caphaw.
Bot
Win32 / Caphaw has the capabilities of a typical banking malware, and also has the ability to check the environment in which it is trying to run. Such checks are obviously aimed at preventing the launch of the dropper in a system designed for automatic analysis of samples. We found that Caphaw injects its code into all running processes, and has a multi-threaded architecture for executing tasks sent from C & C. This code can use interprocess communication (IPC) using named pipes.

Fig. Creating a stream in which IPC interaction will take place.
Caphaw sets up multiple hooks for system functions. Especially interesting is the intercept function for advapi32! InitiateSystemShutdownEx . It can control the process of restarting and shutting down the system, as well as allowing the malicious code to perform its reinstallation in the system.

Fig. Intercept the advapi32! InitiateSystemShutdownEx function. The Trojan is reinstalled into the system.
All strings in Caphaw's body are encrypted using a simple algorithm.

Fig. String decode code.
Caphaw checks the OS environment to see if they are trying to run it in a virtual machine environment (VMware, VirtualBox and VirtualPC). Malicious code checks the names of running processes and drivers in the system. Name checking is done using a pre-calculated hash.

Fig. A function that calculates the hash of a string when checking names.
For example, checking for a VMware environment is as follows.

Fig. Validation code for a VMware environment; according to a pre-calculated hash, the names of running processes and drivers are checked
Every few hours dropper files are repacked using a special service that provides opportunities for using polymorphic cryptor for these purposes. This approach avoids the static signature detection by antivirus scanners of these droppers. URL links, from which these droppers are distributed, are as follows:

Fig. Links leading to the installation of Caphaw droppers.
The format of such URLs is:
hxxps: // [random subdomain]. [domain] / [DIR] / [DIR-random string] / [dropper file]? r = [random number]
To generate random numbers, Caphaw uses the following algorithm:

Fig. Algorithm for generating random numbers in Caphaw.
Caphaw uses C & C to load additional modules, web injects, configuration files, and instructions. At the same time URL links for working with C & C are:

Fig. The URL links that Caphaw uses to interact with C & C.
Such URLs, which are used to refer to C & C, are formed according to a special pattern.
hxxp: // [URL format] / [key] & id = [bot id] & inst = [master or slave] & net [botnet id] & cmd = cfg
The response from the C & C server is:

In this case, a special template is also used:
hxxp: // [random subdomain]. [domain] / [DIR] / [file_name.jpg]? r = [random number]
The bot's configuration file is encrypted using RC4 and Base64. The encryption scheme is: Base64 (RC4 (cfg_data)). After decryption, the configuration file has the form:

Fig. Configuration file after decryption.
Plugins
Win32 / Caphaw has the ability to download and execute additional plug-ins. The plugins that we watched while tracking the botnet are shown in the table.

The plugin used to distribute Caphaw via Skype was described by our colleagues from CSIS . Another interesting plugin is the MBR bootkit module (defined by ESET as Win32 / Wolcape.A ), which is downloaded to infected machines upon special request from C & C. The bootkit is based on the modification of the MBR and provides for downloading the unsigned driver. The intercept function to interrupt the int13 (interrupt is used to read sectors from the hard disk) for this bootkit looks like this:

Fig. Interception on int13.
Location of the malicious driver:

The driver is encrypted using RC4 with a key length of 256 bytes. The call graph of the function that loads the driver is:

Fig. The graph of the function that loads the driver into the system.
The driver intercepts typical system functions in the kernel to hide files and processes. The most interesting of them intercept the functions of the \ Driver \ nsiproxy and \ Device \ Tcp objects to gain control over the passing network traffic. The bootkit configuration file is encrypted according to a similar scheme, as is the case with the above. It also uses a similar XML structure:
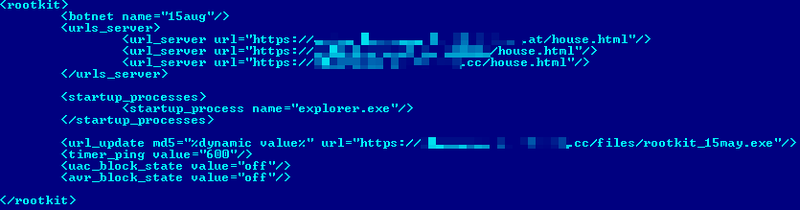
Fig. Bootkit configuration file
Web injections and theft of funds
Web injections use a similar form for configuration data, but the encryption algorithm for them is different. In decrypted form, web injections are as follows:

Below is a list of banks from the latest web injects configuration files:

One of the most interesting details in the code that is inserted into a web page when you visit an online bank is the substitution of all phone numbers for fake numbers belonging to the attackers ( Merchant of Malice: Trojan.Shylock Injects Phone Numbers into Online Banking Websites ). This substitution is based on a special configuration of web injects and has a unique structure for each individual bank.

Conclusion
Win32 / Caphaw is an interesting family of banking Trojans. This malicious code is one of the few who have the functionality to automatically steal money when the user is working with his bank account. In fact, it is very difficult for an infected user to recognize the fact of theft of funds, as he sees fake forms on the online banking page. Similar functionality was tracked by us earlier in such families of banking Trojans as Carberp ( Carberp Gang Evolution ), Gataka ( Win32 / Gataka banking Trojan - Detailed analysis ), Win32 / Spy.Ranbyus ( Win32 / Spy.Ranbyus aimed at modifying the Java code of remote systems Ukrainian banking ) and Tinba.

The geography of distribution shows that Win32 / Caphaw prevails in England, Italy, Denmark and Turkey. According to our statistics ESET Virus Radar, the period of time that accounts for the greatest activity of this Trojan is December 2012. The following screenshot shows the geography of Win32 / Caphaw distribution for the last week (at the time of the study).
')

Fig. The geography of the prevalence of Caphaw.
Bot
Win32 / Caphaw has the capabilities of a typical banking malware, and also has the ability to check the environment in which it is trying to run. Such checks are obviously aimed at preventing the launch of the dropper in a system designed for automatic analysis of samples. We found that Caphaw injects its code into all running processes, and has a multi-threaded architecture for executing tasks sent from C & C. This code can use interprocess communication (IPC) using named pipes.

Fig. Creating a stream in which IPC interaction will take place.
Caphaw sets up multiple hooks for system functions. Especially interesting is the intercept function for advapi32! InitiateSystemShutdownEx . It can control the process of restarting and shutting down the system, as well as allowing the malicious code to perform its reinstallation in the system.

Fig. Intercept the advapi32! InitiateSystemShutdownEx function. The Trojan is reinstalled into the system.
All strings in Caphaw's body are encrypted using a simple algorithm.

Fig. String decode code.
Caphaw checks the OS environment to see if they are trying to run it in a virtual machine environment (VMware, VirtualBox and VirtualPC). Malicious code checks the names of running processes and drivers in the system. Name checking is done using a pre-calculated hash.

Fig. A function that calculates the hash of a string when checking names.
For example, checking for a VMware environment is as follows.

Fig. Validation code for a VMware environment; according to a pre-calculated hash, the names of running processes and drivers are checked
Every few hours dropper files are repacked using a special service that provides opportunities for using polymorphic cryptor for these purposes. This approach avoids the static signature detection by antivirus scanners of these droppers. URL links, from which these droppers are distributed, are as follows:

Fig. Links leading to the installation of Caphaw droppers.
The format of such URLs is:
hxxps: // [random subdomain]. [domain] / [DIR] / [DIR-random string] / [dropper file]? r = [random number]
To generate random numbers, Caphaw uses the following algorithm:

Fig. Algorithm for generating random numbers in Caphaw.
Caphaw uses C & C to load additional modules, web injects, configuration files, and instructions. At the same time URL links for working with C & C are:

Fig. The URL links that Caphaw uses to interact with C & C.
Such URLs, which are used to refer to C & C, are formed according to a special pattern.
hxxp: // [URL format] / [key] & id = [bot id] & inst = [master or slave] & net [botnet id] & cmd = cfg
The response from the C & C server is:

In this case, a special template is also used:
hxxp: // [random subdomain]. [domain] / [DIR] / [file_name.jpg]? r = [random number]
The bot's configuration file is encrypted using RC4 and Base64. The encryption scheme is: Base64 (RC4 (cfg_data)). After decryption, the configuration file has the form:

Fig. Configuration file after decryption.
Plugins
Win32 / Caphaw has the ability to download and execute additional plug-ins. The plugins that we watched while tracking the botnet are shown in the table.

The plugin used to distribute Caphaw via Skype was described by our colleagues from CSIS . Another interesting plugin is the MBR bootkit module (defined by ESET as Win32 / Wolcape.A ), which is downloaded to infected machines upon special request from C & C. The bootkit is based on the modification of the MBR and provides for downloading the unsigned driver. The intercept function to interrupt the int13 (interrupt is used to read sectors from the hard disk) for this bootkit looks like this:

Fig. Interception on int13.
Location of the malicious driver:

The driver is encrypted using RC4 with a key length of 256 bytes. The call graph of the function that loads the driver is:

Fig. The graph of the function that loads the driver into the system.
The driver intercepts typical system functions in the kernel to hide files and processes. The most interesting of them intercept the functions of the \ Driver \ nsiproxy and \ Device \ Tcp objects to gain control over the passing network traffic. The bootkit configuration file is encrypted according to a similar scheme, as is the case with the above. It also uses a similar XML structure:

Fig. Bootkit configuration file
Web injections and theft of funds
Web injections use a similar form for configuration data, but the encryption algorithm for them is different. In decrypted form, web injections are as follows:

Below is a list of banks from the latest web injects configuration files:

One of the most interesting details in the code that is inserted into a web page when you visit an online bank is the substitution of all phone numbers for fake numbers belonging to the attackers ( Merchant of Malice: Trojan.Shylock Injects Phone Numbers into Online Banking Websites ). This substitution is based on a special configuration of web injects and has a unique structure for each individual bank.

Conclusion
Win32 / Caphaw is an interesting family of banking Trojans. This malicious code is one of the few who have the functionality to automatically steal money when the user is working with his bank account. In fact, it is very difficult for an infected user to recognize the fact of theft of funds, as he sees fake forms on the online banking page. Similar functionality was tracked by us earlier in such families of banking Trojans as Carberp ( Carberp Gang Evolution ), Gataka ( Win32 / Gataka banking Trojan - Detailed analysis ), Win32 / Spy.Ranbyus ( Win32 / Spy.Ranbyus aimed at modifying the Java code of remote systems Ukrainian banking ) and Tinba.
Source: https://habr.com/ru/post/171929/
All Articles