New default password in SAP
SAP's default passwords have long been news. The five well-known standard passwords have already been published in many books and security articles. It would seem that on this topic you can find a new one?
Conducting an SAP security audit with one of our clients, we stumbled upon an unknown TMSADM user password. This password was demonstrated to us by the system itself: the following results were obtained when analyzing standard accounts in the well-known RSUSR003 report.
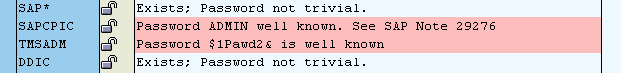
The standard password for TMSADM - PASSWORD - is really widely known, but about the password $ 1Pawd2 & I hear for the first time. Let's understand ...
The first thing that comes to mind is to search the Internet. Google provides only two links, on the SAP website - 6 links. None of these links clarifies our question: a mostly mysterious password is found in published ABAP code fragments.
Well, apparently we should look for answers in the code. Having opened the source code of the RSUSR003 report, we can easily find the text of the message that we saw earlier on the screen (the message number is 028).
')
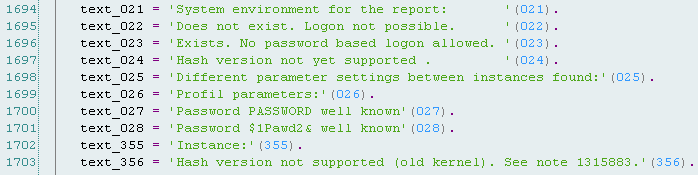
We also find hashes of all passwords by default, which are “wired” in the source code of the program. Interestingly, the TMSADM user has two groups of hashes: one for the password PASSWORD and the other for $ 1Pawd2 &. We give these hashes (I think they can be useful for someone to conduct audits, pentests, etc.).
* EARLYWATCH
lc_ewa TYPE xucode VALUE '13C810002A147DEE',
lc_ewb TYPE xucode VALUE 'BD5E494D3ECBF5E2',
lc_ewd type xucode val '573822832DF89B9C',
lc_ewe TYPE xucode VALUE 'B3ADDFE95DCD036F',
lc_ewf1 TYPE hash160x VALUE '924127D88EE3C1820A2C88495EC4825E819C9249',
lc_ewf2 TYPE hash160x VALUE '760293CCD7AC111298A7AC70D3304242E442320F',
* CPIC
lc_cpa TYPE xucode VALUE 'FC49DBF6F3FDCF36',
lc_cpb TYPE xucode VALUE '7D806C248F03813D',
lc_cpd TYPE xucode VALUE '35C7AB28316EA22F',
lc_cpe TYPE xucode VALUE '5A5F45726821A147',
lc_cpf1 TYPE hash160x VALUE '57CF364A7D83FA563025C7BCFFFB3B579DFB23F3',
lc_cpf2 TYPE hash160x VALUE '38AE55102813F3BBBC3B3BCA09285ED5A9E0423F',
* DDIC
lc_dda type xucode VALUE '5FA752863FB70BA9',
lc_ddb type xucode VALUE '61D26428640DBAB5',
lc_ddd type xucode value 'DCA44BB71C073A05',
lc_dde TYPE xucode VALUE '08FA7683A46D9AA9',
lc_ddf TYPE hash160x VALUE '905F5E6CE67B7C60D0F7BA9C4063AAF0D8602B45',
* SAP *
lc_saa TYPE xucode VALUE 'C75E6D9600AB5710',
lc_sab TYPE xucode VALUE 'D0BFF4276DA1E208',
lc_sad type xucode VALUE 'A83ECB9EC4D34C08',
lc_sae TYPE xucode VALUE '95984B6A25BA20E9',
lc_saf type hash160x VALUE '8948310AF768FA9061598E8F68FD144CE65B7480',
* TMSADM (PW1)
lc_tms1a TYPE xucode VALUE '7671D2F2729F27F0',
lc_tms1b TYPE xucode VALUE '942B9DC0F2394D85',
lc_tms1d TYPE xucode VALUE '7C6433CE69099272',
lc_tms1e TYPE xucode VALUE '940BAB0E12A36DC2',
lc_tms1 TYPE hash160x VALUE 'C9AA19DA354DC8397D7AC8EA8B4C04DF49CB58FF',
* TMSADM (PW2)
lc_tms2a TYPE xucode VALUE '05CB79BE189802A0',
lc_tms2b TYPE xucode VALUE 'B7E2F82C0A3E54C4',
lc_tms2d TYPE xucode VALUE '4DD4438D3C19138C',
lc_tms2e TYPE xucode VALUE 'D527A90BC0CAF484',
lc_tms2 TYPE hash160x VALUE 'A6BF38EE57F90B78C8D88A5212BBF1BA9A966ABB'
Note. For each account, there are 5 hashes: one for each hashing algorithm used in SAP (A, B, D, E, F). Some user accounts (CPIC, EARLYWATCH) each have two password hash values for the F algorithm — for upper and lower case passwords.
Now recall that in the old versions of the RSUSR003 report there was no information about the user of the TMSADM transport system at all. As you can see, such an account is completely absent when displaying analysis results.

This report was, obviously, relatively recently reworked, and in its new versions, information appeared on the default passwords and passwords for TMSADM. Recycled ... and immediately a new, unknown to the public password arose. We check: we turn to the beginning of the source code of the report, usually there is information about the modifications and changes made.

The latest update of the source code is dedicated to adding checks for the user. For more information, refer to the text of the note (released a month after the code change, April 27, 2011).

Everything is confirmed. In early 2011, SAP developers made changes to their RSUSR003 report, adding checks for the TMSADM user to it, taking into account two possible password options: PASSWORD and $ 1Pawd2 &.
What can we conclude:
1. When analyzing the security of SAP systems, you should consider that there is another default password for the TMSADM user. It is necessary to verify that the password used in the system is different from the two predefined options. (The password is $ 1Pawd2 & found on our two test benches, as well as on the stand of one of the customers, i.e. it can easily be in your system).
2. Professionals responsible for the security of their own SAP systems should use Note 1552894 to ensure that the standard passwords of system users, including the TMSADM user, are changed.
Author:
Dmitry Gutsko,
Positive Technologies,
Research Center Positive Research.
Conducting an SAP security audit with one of our clients, we stumbled upon an unknown TMSADM user password. This password was demonstrated to us by the system itself: the following results were obtained when analyzing standard accounts in the well-known RSUSR003 report.

The standard password for TMSADM - PASSWORD - is really widely known, but about the password $ 1Pawd2 & I hear for the first time. Let's understand ...
The first thing that comes to mind is to search the Internet. Google provides only two links, on the SAP website - 6 links. None of these links clarifies our question: a mostly mysterious password is found in published ABAP code fragments.
Well, apparently we should look for answers in the code. Having opened the source code of the RSUSR003 report, we can easily find the text of the message that we saw earlier on the screen (the message number is 028).
')

We also find hashes of all passwords by default, which are “wired” in the source code of the program. Interestingly, the TMSADM user has two groups of hashes: one for the password PASSWORD and the other for $ 1Pawd2 &. We give these hashes (I think they can be useful for someone to conduct audits, pentests, etc.).
* EARLYWATCH
lc_ewa TYPE xucode VALUE '13C810002A147DEE',
lc_ewb TYPE xucode VALUE 'BD5E494D3ECBF5E2',
lc_ewd type xucode val '573822832DF89B9C',
lc_ewe TYPE xucode VALUE 'B3ADDFE95DCD036F',
lc_ewf1 TYPE hash160x VALUE '924127D88EE3C1820A2C88495EC4825E819C9249',
lc_ewf2 TYPE hash160x VALUE '760293CCD7AC111298A7AC70D3304242E442320F',
* CPIC
lc_cpa TYPE xucode VALUE 'FC49DBF6F3FDCF36',
lc_cpb TYPE xucode VALUE '7D806C248F03813D',
lc_cpd TYPE xucode VALUE '35C7AB28316EA22F',
lc_cpe TYPE xucode VALUE '5A5F45726821A147',
lc_cpf1 TYPE hash160x VALUE '57CF364A7D83FA563025C7BCFFFB3B579DFB23F3',
lc_cpf2 TYPE hash160x VALUE '38AE55102813F3BBBC3B3BCA09285ED5A9E0423F',
* DDIC
lc_dda type xucode VALUE '5FA752863FB70BA9',
lc_ddb type xucode VALUE '61D26428640DBAB5',
lc_ddd type xucode value 'DCA44BB71C073A05',
lc_dde TYPE xucode VALUE '08FA7683A46D9AA9',
lc_ddf TYPE hash160x VALUE '905F5E6CE67B7C60D0F7BA9C4063AAF0D8602B45',
* SAP *
lc_saa TYPE xucode VALUE 'C75E6D9600AB5710',
lc_sab TYPE xucode VALUE 'D0BFF4276DA1E208',
lc_sad type xucode VALUE 'A83ECB9EC4D34C08',
lc_sae TYPE xucode VALUE '95984B6A25BA20E9',
lc_saf type hash160x VALUE '8948310AF768FA9061598E8F68FD144CE65B7480',
* TMSADM (PW1)
lc_tms1a TYPE xucode VALUE '7671D2F2729F27F0',
lc_tms1b TYPE xucode VALUE '942B9DC0F2394D85',
lc_tms1d TYPE xucode VALUE '7C6433CE69099272',
lc_tms1e TYPE xucode VALUE '940BAB0E12A36DC2',
lc_tms1 TYPE hash160x VALUE 'C9AA19DA354DC8397D7AC8EA8B4C04DF49CB58FF',
* TMSADM (PW2)
lc_tms2a TYPE xucode VALUE '05CB79BE189802A0',
lc_tms2b TYPE xucode VALUE 'B7E2F82C0A3E54C4',
lc_tms2d TYPE xucode VALUE '4DD4438D3C19138C',
lc_tms2e TYPE xucode VALUE 'D527A90BC0CAF484',
lc_tms2 TYPE hash160x VALUE 'A6BF38EE57F90B78C8D88A5212BBF1BA9A966ABB'
Note. For each account, there are 5 hashes: one for each hashing algorithm used in SAP (A, B, D, E, F). Some user accounts (CPIC, EARLYWATCH) each have two password hash values for the F algorithm — for upper and lower case passwords.
Now recall that in the old versions of the RSUSR003 report there was no information about the user of the TMSADM transport system at all. As you can see, such an account is completely absent when displaying analysis results.

This report was, obviously, relatively recently reworked, and in its new versions, information appeared on the default passwords and passwords for TMSADM. Recycled ... and immediately a new, unknown to the public password arose. We check: we turn to the beginning of the source code of the report, usually there is information about the modifications and changes made.

The latest update of the source code is dedicated to adding checks for the user. For more information, refer to the text of the note (released a month after the code change, April 27, 2011).

Everything is confirmed. In early 2011, SAP developers made changes to their RSUSR003 report, adding checks for the TMSADM user to it, taking into account two possible password options: PASSWORD and $ 1Pawd2 &.
What can we conclude:
1. When analyzing the security of SAP systems, you should consider that there is another default password for the TMSADM user. It is necessary to verify that the password used in the system is different from the two predefined options. (The password is $ 1Pawd2 & found on our two test benches, as well as on the stand of one of the customers, i.e. it can easily be in your system).
2. Professionals responsible for the security of their own SAP systems should use Note 1552894 to ensure that the standard passwords of system users, including the TMSADM user, are changed.
Author:
Dmitry Gutsko,
Positive Technologies,
Research Center Positive Research.
Source: https://habr.com/ru/post/170341/
All Articles