Just about mail security.
This post has two goals. First: slightly lift the veil over the rules of the game, which are followed by a large postal service in matters of security. We want the measures we take to protect users to become more understandable to the community. The post is based on the experience of Mail.Ru Mail, but the recommendations are universal and applicable to any mail service.
The second goal is to talk about how to protect the box. We will go through the basic points and recall those points in the “security plan” that we rarely think about. Perhaps the information in this article will be useful to you, and perhaps to your careless friend, parents or colleague. We may even manage to make the calls “I think the box was hacked, you're a programmer, do something !!! 11” becomes a little less.
In any case, if after reading someone makes a couple of changes in the settings of their email inbox, this will be the best result that the authors can count on. And if you already know all this, then we can only be glad.
')
We will talk about how to break open the boxes, who needs it and why, and describe how to prevent hacking (as well as what to doand where to go if everything bad has already happened).
Why hack email
Why exactly your mailbox can be of value to someone? Very often, users neglect elementary precautions simply because they cannot answer this question. Of course, usually the ultimate goal of hacking is to get some financial profit. But from whom can a cracker get money? There are several scenarios.
Most often, spammers are engaged in buying large amounts of mailboxes. Hacked boxes are used for mass mailings like "Elite replica Swiss watches." Most hacks are done for this very purpose.
Even if the hacker’s main purpose is to resell the mailbox, immediately after gaining access, he still scans the information contained in the mailbox for something more or less valuable. This may be, for example, accounts of social networks, hosting, banks, electronic money, game accounts. If the box does not contain data about the passwords themselves, the attacker may request a password reset for the box. Also, an attacker will definitely check if your mail password is suitable for accounts on other resources.
You can become a victim of blackmail - you will be offered to buy access to the box or to your account on the social network. The subject of blackmail can also be personal information (correspondence, photos, scans of documents), which is contained in the box. Sometimes to collect money from owners of hacked accounts, paid sms receiving services are used. Unfortunately, not all sms-aggregators are sufficiently scrupulous in this matter.
Hacking can be customized. Access may be needed by your competitor or former partner, employee, jealous spouse. Immediately, we note that hacking on order is a very small fraction of the total.
From this you can make a simple conclusion - any mailbox has value for a cracker.
How to break mail
On the Internet, you can find ads on hacking mailboxes on request. Prices range from a dozen to several hundred dollars. In most cases, the victim becomes the customer himself, who is deceived in one way or another or blackmailed with a promise to tell the victim about the hacking attempt. If it still comes to hacking, then usually social engineering goes into battle and, rarely, the selection of a password and a secret question.
But usually hacks are done massively and using botnets. An attacker has no purpose to hack a specific box; He has the task to crack as many mailboxes as possible - for example, having a certain simple password. We have not yet encountered any situations of truly serious hacking, when, for example, 0-day-security vulnerabilities in any browser would be used against the victim.
The following are the main methods for gaining access to someone else's mailbox and how to protect against them.

Almost any Trojan among other information and takes away passwords from e-mail. According to various sources, up to 30% of computers are infected every year. Using Linux, MacOS X, any other operating systems, or various phone and tablet platforms does not guarantee the absence of malware.
At the same time, remember that the malware first appears, then it infects someone, and only after some time does it get into the anti-virus database. Thus, the antivirus does not guarantee 100% protection. However, this does not mean that anti-virus programs should not be used. It is enough not to interfere with the anti-virus regularly update the database, and most of the threats it will not miss.

It’s not just short passwords or single-digit passwords. On the Internet, you can find databases of popular passwords, which include almost all passwords consisting of the following on the keyboard (qwerty) or easily alternating characters (1q2w3e). The same can be said about passwords consisting of a date of birth in any format, even if it is supplemented with a symbol or initials. Of course, the most common vocabulary passwords are also known - they are picked up literally from the dictionary. A set of Russian vocabulary words in the Latin layout is also not a guarantee of invulnerability. Such passwords are also easily selected by the dictionary. Do not forget that if you are registered on social networks, almost anyone can know your date of birth or phone. The number of the car and the data of various documents are also quite easy to “make their way” when it comes to customized hacking.
The choice of a password must be taken seriously, it depends on the degree of security of your mailbox. Choose a long enough password consisting of large and small letters, numbers and symbols. The more the password looks like a random sequence, the better. But Russian words in the English layout is not what is needed.
Now it is fashionable to use a key phrase of several words instead of a password. This is a good practice, but avoid the famous catchwords. The key phrase should not be heard, it is better if it is unique, and even better - meaningless.
We recommend changing passwords regularly. This is effective, because if you have already used the “email” password on another site (which we strongly advise not to do), and the unprotected site has leaked the database, your email account is under threat.
In addition, it will complicate the selection (brute force) of a password if a targeted attack is on the box and helps protect against accidental password leaks - for example, when a password was used from someone else's infected computer.
It is logical to change passwords in connection with such life events as divorce, dismissal, loss of a phone or address book, capture and elimination of the Trojan.
However, frequent change of passwords can lead to their weakening: the user either starts to choose light passwords, either writes them in an easily accessible place, or makes the next password look like the previous one. Do not be tempted and do not be lazy when inventing a password - the password to the mail must remain difficult.
Mail.Ru Mail, for its part, implements password protection in the form of antibruteforce - a multi-factor system that eliminates attempts to automatically enter the box.

Using answers to a secret question is not a very good practice from a security point of view. But often this is the only way to restore access to the mailbox for a user who visits the mail very rarely and has not indicated any real information about himself. Therefore, we and other free mail services do not refuse it.
If your favorite dish is dumplings, your favorite book is Harry Potter, you can get the name of your grandmother from the list of relatives on the social network, and the name of your favorite cat is signed in the top post under his photo, you are literally half a step away from making a big mistake.
All that has been said about passwords applies to answers to secret questions.
The only difference between the secret question is that along with the answer, as a rule, CAPTCHA is requested (a verification code that must be recognized and entered), and there is a stricter limitation on the number of input attempts. This is somewhat difficult brute force (selection) machine methods. Otherwise, the answer to a secret question is equivalent to a password, and it is worthwhile to choose it just as carefully.
Social engineering is a method of unauthorized access to information or information storage systems without the use of technical means, exploiting the human factor. One type of social engineering is phishing. A typical example is to force a user to enter a password on another site disguised as an authorization page design, for example:
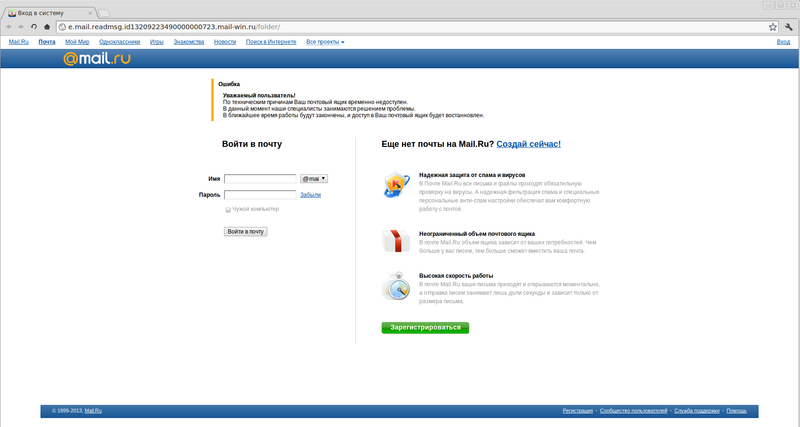
This is not the only option. Also, quite often we encounter social engineering aimed at “extracting” from the user the data necessary for password recovery or access to the box. For example, passport details are trying to request under the guise of receiving a prize in the lottery. The answer to the secret question can be elicited in a normal conversation on social networks (“Do you have a cat? What a cute one! And what is his name?”). Everything is explained by the classic joke from Bash :
Connect: Listen, are we relatives?
ALEXA: think ???
Connect: Well, maybe distant. What maiden name was your mother?
ALEXA: * EKO
Connect: Oh, you have 8 new letters)
ALEXA: in the sense ???
Phishing can be directed not only to gain access to your account. A phishing email can report about blocking an account and require sending an SMS to a short number, which, of course, will be paid.

According to the phishers themselves, about 80% of women and 60% of men bite at attacks with the help of social engineering.
Be very critical of the information that strangers tell you, and even more critical of the information that you give them. Especially if you are in a hurry.
If we become aware that your account has been hacked, it is unauthorizedly used, and we want to inform you about it, we will not ask the employee of any service to write you a letter. We will do something like this:

Do not follow the links from strangers, be attentive to who the link came from and where it brought you. Do not be lazy to look in the address bar of the browser before entering any data. Unexpected effects, such as requesting a login / password when opening a letter from an unknown sender, should also alert.
Attacks are carried out not only on the owner of the box: the support staff are also constantly under pressure. The attacker is trying to "restore" the allegedly lost access to someone else's box. Sometimes you can read very interesting and intricate stories worthy of Latin American TV shows, describing love polygons and detective situations, explaining why you need to give the author a password from someone else's box.
Support staff have strict instructions for recovering passwords, so if such a need arose, do not try to soften them; better provide as much objective information as possible that will confirm that you are the box owner.
This is one of the most serious problems. Often, when registering on any forum, torrent trackers or website, the user specifies an email address and password that is identical to the password to the mailbox or little different from it. The level of protection of forums and torrent trackers, as a rule, is low. In addition, many of them are built on the same popular engines. If any security vulnerabilities are detected in such an engine, thousands of sites can be hacked at the same time.
This is the first thing that the attacker will check. For example, a number of users who suffered from the same password on other sites suffered during the high-profile hacking of LinkedIn. Therefore, for different sites - different passwords. Is always. If inventing a unique password for each site seems to you an impossible mission, think up a separate at least for mail - because it is the “key” to many of your accounts on various services.
Often several people use the same box. Sometimes friends are asked to check their mail - for example, if the user himself does not have access to the Internet at this moment.
However, it is worth remembering that a person who has used the box for some time can almost always regain access to it afterwards. If the relationship deteriorates, a dispute may arise around the box.
For the same reason, avoid buying boxes with beautiful names from anyone. If a dispute arises about the ownership of the box, preference is given to the one who registered it. That is why postal services are asked to register the box on themselves or on the company, and not on relatives, not on employees and not on comic characters.
Sniffing is listening to network traffic. It is easy enough to “sniff” the traffic going over wireless networks - both via Wi-Fi and via satellite channel. When you connect to the Internet via Wi-Fi, an attacker can listen to all traffic through his device, since the physical data is transmitted via radio waves.
Many services now support the HTTPS protocol, use it. For example, authorization and work inside Mail.Ru Mail always takes place using this protocol.
In email programs, be sure to enable SSL / TLS when working with SMTP, POP and IMAP protocols. At the same time in Mail Mail.Ru work on the IMAP protocol is possible only via SSL / TLS. Be sure to respond to all warnings about the inconsistency of certificates, especially if you are using a wireless network or from an unfamiliar place - otherwise all the cryptography does not make sense.
What we do
The weakest link in the security of any mass service, as a rule, is the user. But, of course, there are problems with the service. The loud hacking of the last months, when the accounts of the largest services (recall LinkedIn) got into the network, remind us of this. No service is free from software bugs.
The measures taken by the postal service or social network is always a balance between functionality, comfort and security. You can disable any password recovery methods: it will be safer, but then the user will not be able to restore access to his own mailbox. By limiting you can require very strong passwords - but in this case, users will forget them. You can block an IP address when you first try to log in or recover a password; This will protect against the selection of passwords and secret answers, but subscribers of providers using dynamic addresses or NAT technology will not be able to enter the mail. You can disable all potentially dangerous HTML tags in emails when accessing via the web interface, but this means that some of the emails will not be displayed correctly.
Therefore, we use compromise solutions and complex algorithms that take into account a combination of factors. Of course, we will not disclose the details of the implementation, so we invented such a cunning phrase. All mechanisms are constantly being improved and these are not separate changes, but a planned process. For example, an article published on Habré comparing filtering systems for HTML tags of different mail services was already outdated at the time of its publication - we changed the filtering system just a day before the article was published and did this more than once after it was published. We also did a great job to make HTTPS in Mail work by default for all users.
We pay great attention to the fight against automatic password selection, implementing and constantly improving anti-grunt algorithms.
We have a special department in the support service that conducts targeted work to ensure the safety of users: looking for fraudulent and phishing sites, reports them to hosting providers and domain registrars, informs search engines about counterfeit resources in search results and contextual advertising, fights SMS - fraudsters, exchanges information with CERT-teams and anti-virus vendors.
Of course, we protect our information system not only from the outside, but also from the inside. , - «» , . « »: , . , , .
:
, , , - , , .
. , .
— . SMS — .
, , , .

— . . — , , . , , , , . , , .
, SMS ( , ), , . , , . , , . !
, , .
, , , . , .. . , Mail.Ru SMS.
, .
- , , . , . , , , . , , .
, , , . . , , , .
Mail.Ru, , mailru-suppr1@hogmail.com, support@corp.mail.ru. , , , . http://e.mail.ru/cgi-bin/passremind – .
, security@corp.mail.ru — . , – hr@corp.mail.ru.
, , antiphishing@corp.mail.ru, .
The second goal is to talk about how to protect the box. We will go through the basic points and recall those points in the “security plan” that we rarely think about. Perhaps the information in this article will be useful to you, and perhaps to your careless friend, parents or colleague. We may even manage to make the calls “I think the box was hacked, you're a programmer, do something !!! 11” becomes a little less.
In any case, if after reading someone makes a couple of changes in the settings of their email inbox, this will be the best result that the authors can count on. And if you already know all this, then we can only be glad.
')
We will talk about how to break open the boxes, who needs it and why, and describe how to prevent hacking (as well as what to do
Why hack email
Why exactly your mailbox can be of value to someone? Very often, users neglect elementary precautions simply because they cannot answer this question. Of course, usually the ultimate goal of hacking is to get some financial profit. But from whom can a cracker get money? There are several scenarios.
Accounts can be resold in bulk
Most often, spammers are engaged in buying large amounts of mailboxes. Hacked boxes are used for mass mailings like "Elite replica Swiss watches." Most hacks are done for this very purpose.
Money can be taken from the box itself ...
Even if the hacker’s main purpose is to resell the mailbox, immediately after gaining access, he still scans the information contained in the mailbox for something more or less valuable. This may be, for example, accounts of social networks, hosting, banks, electronic money, game accounts. If the box does not contain data about the passwords themselves, the attacker may request a password reset for the box. Also, an attacker will definitely check if your mail password is suitable for accounts on other resources.
... or get from the account owner
You can become a victim of blackmail - you will be offered to buy access to the box or to your account on the social network. The subject of blackmail can also be personal information (correspondence, photos, scans of documents), which is contained in the box. Sometimes to collect money from owners of hacked accounts, paid sms receiving services are used. Unfortunately, not all sms-aggregators are sufficiently scrupulous in this matter.
... or from another interested person
Hacking can be customized. Access may be needed by your competitor or former partner, employee, jealous spouse. Immediately, we note that hacking on order is a very small fraction of the total.
From this you can make a simple conclusion - any mailbox has value for a cracker.
How to break mail
On the Internet, you can find ads on hacking mailboxes on request. Prices range from a dozen to several hundred dollars. In most cases, the victim becomes the customer himself, who is deceived in one way or another or blackmailed with a promise to tell the victim about the hacking attempt. If it still comes to hacking, then usually social engineering goes into battle and, rarely, the selection of a password and a secret question.
But usually hacks are done massively and using botnets. An attacker has no purpose to hack a specific box; He has the task to crack as many mailboxes as possible - for example, having a certain simple password. We have not yet encountered any situations of truly serious hacking, when, for example, 0-day-security vulnerabilities in any browser would be used against the victim.
The following are the main methods for gaining access to someone else's mailbox and how to protect against them.
Problem # 1: Trojan on the computer

Almost any Trojan among other information and takes away passwords from e-mail. According to various sources, up to 30% of computers are infected every year. Using Linux, MacOS X, any other operating systems, or various phone and tablet platforms does not guarantee the absence of malware.
Solution: use antivirus software
At the same time, remember that the malware first appears, then it infects someone, and only after some time does it get into the anti-virus database. Thus, the antivirus does not guarantee 100% protection. However, this does not mean that anti-virus programs should not be used. It is enough not to interfere with the anti-virus regularly update the database, and most of the threats it will not miss.
Problem # 2: password guessing

It’s not just short passwords or single-digit passwords. On the Internet, you can find databases of popular passwords, which include almost all passwords consisting of the following on the keyboard (qwerty) or easily alternating characters (1q2w3e). The same can be said about passwords consisting of a date of birth in any format, even if it is supplemented with a symbol or initials. Of course, the most common vocabulary passwords are also known - they are picked up literally from the dictionary. A set of Russian vocabulary words in the Latin layout is also not a guarantee of invulnerability. Such passwords are also easily selected by the dictionary. Do not forget that if you are registered on social networks, almost anyone can know your date of birth or phone. The number of the car and the data of various documents are also quite easy to “make their way” when it comes to customized hacking.
Solution: avoid simple passwords
The choice of a password must be taken seriously, it depends on the degree of security of your mailbox. Choose a long enough password consisting of large and small letters, numbers and symbols. The more the password looks like a random sequence, the better. But Russian words in the English layout is not what is needed.
Now it is fashionable to use a key phrase of several words instead of a password. This is a good practice, but avoid the famous catchwords. The key phrase should not be heard, it is better if it is unique, and even better - meaningless.
We recommend changing passwords regularly. This is effective, because if you have already used the “email” password on another site (which we strongly advise not to do), and the unprotected site has leaked the database, your email account is under threat.
In addition, it will complicate the selection (brute force) of a password if a targeted attack is on the box and helps protect against accidental password leaks - for example, when a password was used from someone else's infected computer.
It is logical to change passwords in connection with such life events as divorce, dismissal, loss of a phone or address book, capture and elimination of the Trojan.
However, frequent change of passwords can lead to their weakening: the user either starts to choose light passwords, either writes them in an easily accessible place, or makes the next password look like the previous one. Do not be tempted and do not be lazy when inventing a password - the password to the mail must remain difficult.
Mail.Ru Mail, for its part, implements password protection in the form of antibruteforce - a multi-factor system that eliminates attempts to automatically enter the box.
Problem # 3: Secret Answer Selection

Using answers to a secret question is not a very good practice from a security point of view. But often this is the only way to restore access to the mailbox for a user who visits the mail very rarely and has not indicated any real information about himself. Therefore, we and other free mail services do not refuse it.
If your favorite dish is dumplings, your favorite book is Harry Potter, you can get the name of your grandmother from the list of relatives on the social network, and the name of your favorite cat is signed in the top post under his photo, you are literally half a step away from making a big mistake.
Solution: avoid simple answers
All that has been said about passwords applies to answers to secret questions.
The only difference between the secret question is that along with the answer, as a rule, CAPTCHA is requested (a verification code that must be recognized and entered), and there is a stricter limitation on the number of input attempts. This is somewhat difficult brute force (selection) machine methods. Otherwise, the answer to a secret question is equivalent to a password, and it is worthwhile to choose it just as carefully.
Problem # 4: social engineering, phishing
Social engineering is a method of unauthorized access to information or information storage systems without the use of technical means, exploiting the human factor. One type of social engineering is phishing. A typical example is to force a user to enter a password on another site disguised as an authorization page design, for example:

This is not the only option. Also, quite often we encounter social engineering aimed at “extracting” from the user the data necessary for password recovery or access to the box. For example, passport details are trying to request under the guise of receiving a prize in the lottery. The answer to the secret question can be elicited in a normal conversation on social networks (“Do you have a cat? What a cute one! And what is his name?”). Everything is explained by the classic joke from Bash :
Connect: Listen, are we relatives?
ALEXA: think ???
Connect: Well, maybe distant. What maiden name was your mother?
ALEXA: * EKO
Connect: Oh, you have 8 new letters)
ALEXA: in the sense ???
Phishing can be directed not only to gain access to your account. A phishing email can report about blocking an account and require sending an SMS to a short number, which, of course, will be paid.

According to the phishers themselves, about 80% of women and 60% of men bite at attacks with the help of social engineering.
Solution: don't talk to strangers
Be very critical of the information that strangers tell you, and even more critical of the information that you give them. Especially if you are in a hurry.
If we become aware that your account has been hacked, it is unauthorizedly used, and we want to inform you about it, we will not ask the employee of any service to write you a letter. We will do something like this:

Do not follow the links from strangers, be attentive to who the link came from and where it brought you. Do not be lazy to look in the address bar of the browser before entering any data. Unexpected effects, such as requesting a login / password when opening a letter from an unknown sender, should also alert.
Attacks are carried out not only on the owner of the box: the support staff are also constantly under pressure. The attacker is trying to "restore" the allegedly lost access to someone else's box. Sometimes you can read very interesting and intricate stories worthy of Latin American TV shows, describing love polygons and detective situations, explaining why you need to give the author a password from someone else's box.
Support staff have strict instructions for recovering passwords, so if such a need arose, do not try to soften them; better provide as much objective information as possible that will confirm that you are the box owner.
Problem # 5: Hacking Other Sites
This is one of the most serious problems. Often, when registering on any forum, torrent trackers or website, the user specifies an email address and password that is identical to the password to the mailbox or little different from it. The level of protection of forums and torrent trackers, as a rule, is low. In addition, many of them are built on the same popular engines. If any security vulnerabilities are detected in such an engine, thousands of sites can be hacked at the same time.
Solution: do not use one password for multiple accounts
This is the first thing that the attacker will check. For example, a number of users who suffered from the same password on other sites suffered during the high-profile hacking of LinkedIn. Therefore, for different sites - different passwords. Is always. If inventing a unique password for each site seems to you an impossible mission, think up a separate at least for mail - because it is the “key” to many of your accounts on various services.
Problem # 6: controversial situation around the account
Often several people use the same box. Sometimes friends are asked to check their mail - for example, if the user himself does not have access to the Internet at this moment.
However, it is worth remembering that a person who has used the box for some time can almost always regain access to it afterwards. If the relationship deteriorates, a dispute may arise around the box.
Solution: do not use someone else's box and do not let anyone in your!
For the same reason, avoid buying boxes with beautiful names from anyone. If a dispute arises about the ownership of the box, preference is given to the one who registered it. That is why postal services are asked to register the box on themselves or on the company, and not on relatives, not on employees and not on comic characters.
Problem # 7: Sniffing
Sniffing is listening to network traffic. It is easy enough to “sniff” the traffic going over wireless networks - both via Wi-Fi and via satellite channel. When you connect to the Internet via Wi-Fi, an attacker can listen to all traffic through his device, since the physical data is transmitted via radio waves.
Solution: use cryptography
Many services now support the HTTPS protocol, use it. For example, authorization and work inside Mail.Ru Mail always takes place using this protocol.
In email programs, be sure to enable SSL / TLS when working with SMTP, POP and IMAP protocols. At the same time in Mail Mail.Ru work on the IMAP protocol is possible only via SSL / TLS. Be sure to respond to all warnings about the inconsistency of certificates, especially if you are using a wireless network or from an unfamiliar place - otherwise all the cryptography does not make sense.
What we do
The weakest link in the security of any mass service, as a rule, is the user. But, of course, there are problems with the service. The loud hacking of the last months, when the accounts of the largest services (recall LinkedIn) got into the network, remind us of this. No service is free from software bugs.
The measures taken by the postal service or social network is always a balance between functionality, comfort and security. You can disable any password recovery methods: it will be safer, but then the user will not be able to restore access to his own mailbox. By limiting you can require very strong passwords - but in this case, users will forget them. You can block an IP address when you first try to log in or recover a password; This will protect against the selection of passwords and secret answers, but subscribers of providers using dynamic addresses or NAT technology will not be able to enter the mail. You can disable all potentially dangerous HTML tags in emails when accessing via the web interface, but this means that some of the emails will not be displayed correctly.
Therefore, we use compromise solutions and complex algorithms that take into account a combination of factors. Of course, we will not disclose the details of the implementation, so we invented such a cunning phrase. All mechanisms are constantly being improved and these are not separate changes, but a planned process. For example, an article published on Habré comparing filtering systems for HTML tags of different mail services was already outdated at the time of its publication - we changed the filtering system just a day before the article was published and did this more than once after it was published. We also did a great job to make HTTPS in Mail work by default for all users.
We pay great attention to the fight against automatic password selection, implementing and constantly improving anti-grunt algorithms.
We have a special department in the support service that conducts targeted work to ensure the safety of users: looking for fraudulent and phishing sites, reports them to hosting providers and domain registrars, informs search engines about counterfeit resources in search results and contextual advertising, fights SMS - fraudsters, exchanges information with CERT-teams and anti-virus vendors.
Of course, we protect our information system not only from the outside, but also from the inside. , - «» , . « »: , . , , .
:
, , , - , , .
. , .
— . SMS — .
, , , .

— . . — , , . , , , , . , , .
, SMS ( , ), , . , , . , , . !
, , .
, , , . , .. . , Mail.Ru SMS.
, .
- , , . , . , , , . , , .
, , , . . , , , .
Mail.Ru, , mailru-suppr1@hogmail.com, support@corp.mail.ru. , , , . http://e.mail.ru/cgi-bin/passremind – .
, security@corp.mail.ru — . , – hr@corp.mail.ru.
, , antiphishing@corp.mail.ru, .
Source: https://habr.com/ru/post/169801/
All Articles