Frosty Encryption Attack for Android
Two researchers from the University of Erlangen, in Germany, have demonstrated a method of obtaining encrypted information of a smartphone running Android, using ... the freezer :)
In order to gain access to the encryption key stored in the phone’s memory, the researchers placed the device in the freezer for an hour, after which, preserving the contents of the phone’s memory — literally literally — freezing. Getting the encryption key from the device was carried out using the so-called cold boot attack .
')
By freezing the device to a temperature below -10 degrees, it is possible to ensure that data is stored in volatile memory for a short period of time without powering the device. Tilo Müller and Michael Spreitzenbarth used this vulnerability to detach the device’s battery for a subsequent reboot. Then, having started the bootloader, they resubmitted the device with their firmware under the saying name “Frost”. In order for this to work, the bootloader must already be unlocked, since any unlocking will result in the deletion of all smartphone user data. Frost then searches the encryption key in memory (among other information) to decrypt user data stored in the non-volatile memory of the device.
Starting from version 4.0, Android provides the ability to encrypt personal data (if the user activates the appropriate checkbox in the settings). In addition to the encryption key, Frost also managed to get other types of personal data from the frozen memory of the smartphone, in particular: text data access to Wi-Fi, history of correspondence from the WhatsApp application, a book of device contacts and photos taken from the phone.


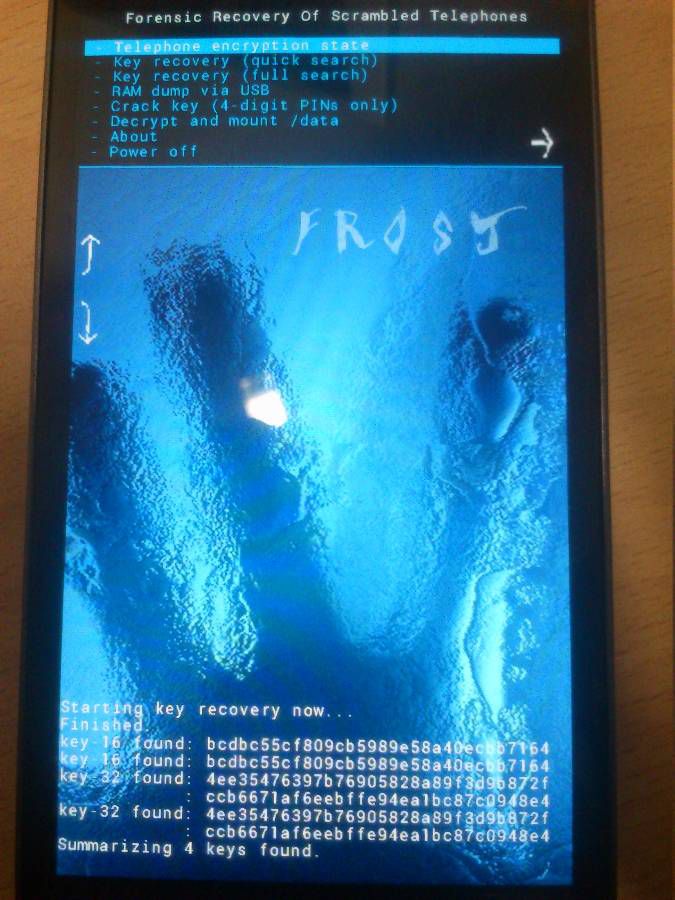
In order to gain access to the encryption key stored in the phone’s memory, the researchers placed the device in the freezer for an hour, after which, preserving the contents of the phone’s memory — literally literally — freezing. Getting the encryption key from the device was carried out using the so-called cold boot attack .
')
By freezing the device to a temperature below -10 degrees, it is possible to ensure that data is stored in volatile memory for a short period of time without powering the device. Tilo Müller and Michael Spreitzenbarth used this vulnerability to detach the device’s battery for a subsequent reboot. Then, having started the bootloader, they resubmitted the device with their firmware under the saying name “Frost”. In order for this to work, the bootloader must already be unlocked, since any unlocking will result in the deletion of all smartphone user data. Frost then searches the encryption key in memory (among other information) to decrypt user data stored in the non-volatile memory of the device.
Starting from version 4.0, Android provides the ability to encrypt personal data (if the user activates the appropriate checkbox in the settings). In addition to the encryption key, Frost also managed to get other types of personal data from the frozen memory of the smartphone, in particular: text data access to Wi-Fi, history of correspondence from the WhatsApp application, a book of device contacts and photos taken from the phone.

Source: https://habr.com/ru/post/169717/
All Articles