Changes in AD Windows Server 2012. Part 2. Recycle AD, FGPP, gMSA, primary computers

WindowsITPro published an interesting article Windows Server 2012 Active Directory Security Changes , devoted to key changes in Active Directory in Windows Server 2012. Yesterday the first part was devoted to dynamic access control.
Today, we are considering the remaining issues regarding AD security innovations in Windows Server 2012, namely:
- New security management features in ADAC (AD Recycle Bin and Granular Password Policies),
- Group Managed Service Accounts
- Primary computers.
I want to note that the language of the article is quite complicated, so translation in some places may limp. I apologize in advance for this.
New security management features in ADAC
ADAC in Server 2012 has become the main AD administration interface. At the administrative level, ADAC has even supplanted its predecessor, the Active Directory Users and Computers snap-in in the Microsoft Management Console (MMC). Two new features in ADAC that most administrators will most certainly appreciate are the graphical interface of ADAC in terms of restoring deleted AD objects (see our post on innovations in the AD basket - translator's note ) and for configuring settings for granular password policies (fine-grained password policy - FGPP).
AD Recycle Bin in Windows Server 2012
The AD Recycle Bin was first introduced in Server 2008 R2 and allowed to recover deleted AD objects along with attributes. However, a big disadvantage of the AD basket was the lack of a graphical interface. Administrators were forced to use either ldp.exe or refer to PowerShell cmdlets, two tools that complicate the recovery of AD objects and slow down the recovery process. (For more recovery, see our post “ Recovering deleted AD objects: a collection of scripts ”)
')
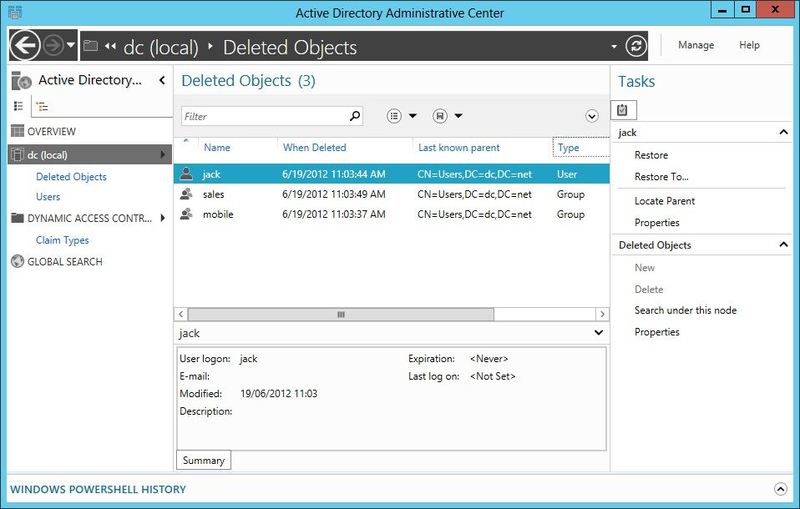
As shown in the figure above, Microsoft added the display of the Deleted Objects container to the ADAC Server 2012 interface. You can easily restore a deleted object using the Restore or Restore To links in the right ADAC panel. In Server 2012, the restrictions for the cart remained the same:
- Recycle bin is disabled by default (can be enabled via ADAC).
- Your AD forest must be at least at the Server 2008 R2 functional level.
- You can restore objects only during their lifetime (Deleted Object Lifetime - DOL), which by default is 180 days.
For more information on the AD cart, see the Microsoft " Active Directory Recycle Bin Step-by-Step Guide ."
Granular Password Policies
The second useful interface addition to ADAC is related to the configuration of granular password policies (FGPP). Microsoft introduced FGPP in Server 2008 so that you can set multiple Windows domain passwords and account lockout policies that are associated with various user or administrative AD groups. Prior to this, Windows Server supported only one domain password policy. To support granular password policies, Microsoft introduced a new type of AD object, called the Password Settings Object (PSO). See the PSO post in action .
As in the case of the AD basket in Server 2008, Microsoft decided to dispense with the graphical interface for the FGPPs configuration. Administrators needed to rely on tools like PowerShell cmdlets, ADSI Edit or LDIFDE to set PSO. In Server 2012, it became possible to use the ADAC GUI to create new FGPP and PSO from the new Password Settings container, which is located under the System container, as shown in Figure 6. As before, your domain must be at least at the Server 2008 functional level in order to use FGPP. Details can be found in this manual " AD DS Fine-Grained Password-Policy-Step-by-Step Guide ."

Group Managed Service Accounts
Managed Service Accounts (MSAs), a special type of domain account, appeared in AD Server 2008 R2. MSA allows you to resolve password management problems when setting up custom domain accounts for service authentication. Administrators prefer to define custom accounts that allow them to more accurately set application privileges than to use built-in highly privileged local accounts (for example, local system, local service, Local System network service, Local Service, Network Service) as service ones. But unlike these built-in local accounts, there is no automatic password management for custom accounts. Therefore, when you use custom service accounts, you need to manually manage their passwords.
MSA, in turn, is designed for automatic password management. Managed service accounts also simplify the installation of Service Principal Names (SPNs) for a service. Unfortunately, MSA that were introduced in Server 2008 R2 could not be used by clustered (clustered) or load-balanced services (for example, services in a web farm) that would like to share one service account and password. In these cases, administrators had to manually synchronize the passwords of service instances or implement a custom solution to automatically synchronize passwords.
Service groups managed accounts in Server 2012 (gMSAs) solve this problem with load-balanced services in web farms. Unfortunately, at the time of this writing, MSA has not yet worked with services that are part of a failover cluster.
In addition to the gMSA, a new service (namely, the Microsoft Key Distribution Service) is running on each Server 2012 domain controller. This service ensures that the password for the single service account that the web farm service instance uses is synchronized between instances. To use gMSA, your AD schema must be upgraded to Server 2012 and you need one or more Server 2012 domain controllers running the Microsoft Key Distribution Service. The service is automatically installed on each domain controller, but by default it is started manually. Only services running on Server 2012 can use gMSA. You can create and administer gMSA using PowerShell cmdlets. For more information about gMSA, see the " Getting Started with Group Managed Service Accounts ."
Primary computers for folder redirection and roaming profiles (Primary Computers for Folder Redirection and Roaming Profiles)
The last important function that I would like to discuss in this article is the ability to specify individual computers in AD as primary for certain domain users. You can use this feature to monitor computers that have roaming user profiles uploaded (users' roaming profiles) and to which users get access to their redirected folders (redirected folders). On computers that were not marked as primary computers, users will have their local profile and will not get access to their redirected folders.
In the era of IT consumerization trends and BYOD trends, this method is a powerful tool for establishing links between data and user account settings on the one hand, and specific computers or devices on the other; This is done to enhance corporate data security.
The function of the primary computer is based on a set of new settings for group policy objects and the extension of the AD schema. When a user logs in on a computer running Windows 8 or Server 2012, the status of two settings controlled by a GPO is checked: Download roaming profiles on primary computers only and Redirect folders on primary computers . It is checked whether the msDS-PrimaryComputer attribute bound to a user object in AD should affect the movement (roam) of the user profile or the use of Folder Redirection. New GPO settings are in the \ User Configuration \ Policies \ Administrative Templates \ System \ Folder Redirection and \ User Configuration \ Policies \ Administrative Templates \ System \ User Profiles GPO containers .
You can use together with ADAC and PowerShell cmdlets to populate (to populate) the msDS-PrimaryComputer attribute with data from the DistinguishedNames list of computer accounts that should be marked as the primary computers of users. Figure 7 shows how you can use ADAC and its built-in attribute editor to set the msDS-PrimaryComputer attribute for a user named Jack.

To support the Primary Computer feature, your AD schema needs to be updated on Server 2012. The feature can be used on domain computers running Server 2012 Windows 8. For more information, see the Storage Team Blog " Configuring Folder Redirection Roaming and Sharing Profiles" Windows Server 8 Beta . "
Summing up
Dynamic Access Control is a big step forward in the authorization and auditing model for files and folders in Windows since the introduction of AD, and maybe since the release of NTFS. Dynamic Access Control support is a significant change in the security of Server 2012 and AD, not only for the engineers at Microsoft who develop it, but also for everyone who uses it. If you are a Windows AD administrator or a system architect, I recommend that you thoroughly test Dynamic Access Control and get to know it well before using it.
ADAC and PowerShell are also high on security issues related to managing AD in Server 2012. Like Dynamic Access Control, ADAC and PowerShell are associated with greater flexibility in simplifying the daily administration and configuration of AD.
Source: https://habr.com/ru/post/169543/
All Articles