AppFuscator - .NET cloud protection
Hi Habr! We worked hard on our product, and today I want to share the news. For those who have not read the previous topics ( 1 and 2 ), I remind you that we are developing an online service to protect .NET applications. The process of obfuscation occurs directly in the cloud on the SaaS model.
I'll tell you a little about innovations.
For those who obfusts their programs all the time, we have significantly simplified this process - now you can use a special client program to work with our service. The created configuration can be saved to the project, and then obfuscated your programs in one click.
')
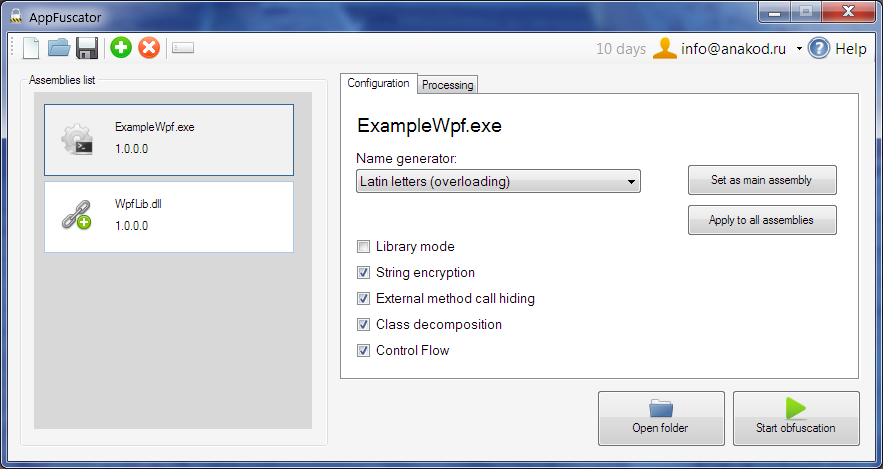
The program is distributed as OpenSource (MIT license), everyone can get acquainted with the source code . In the future, we plan to bring the API into a separate module, for easy integration with other programs.
The program is still beta, we apologize in advance for possible bugs.
A new control flow obfuscation protection algorithm has been added to AppFuscator. The essence of this method consists in dividing the program algorithm into separate components and building from them a complexly-connected transition graph. As a result, the logic of the code is not quite understandable.
A small example:

The full code of the obfuscated method can be viewed here (for clarity, all types of protection are turned off except for the control flow obfuscation)
Of the features:
Summary: it is possible to write a reverse decoder, but it will be quite difficult, expensive and difficult. We'll have to sharpen it personally for our algorithm, and we will try to update it more often so that the life of a potential hacker is fun and eventful.
Significantly refined WPF obfuscation algorithms. Our obfuscator can rename objects used in XAML markup, and at the same time correctly handles Bingings, Attached Properties, Attached Events and other clever constructions from the WPF world. As a rule, the process of obfuscation does not require manual configuration; intelligent code analysis and XAML markup (or, more precisely, BAML) will take care of everything.

Now each user has access to a personal account . You can see the history of obfuscations in it and download previous obfuscated versions for studying MAP files.

We will be glad to hear your questions and suggestions, as well as to discuss your ideas.
UPD1. Placed 10 promotional codes for registration:
wdk6tuffkc
2ppcpfgtpj
9p82pm8xnt
fg73hqfakd
wpkt6k8rqc
7ztv4jck8r
ku8dqn4u38
jc6gxxbdgw
eyjw7b9zd8
2nf68m6r2t
UPD2. Invites run out. Who was not enough, another one that was not activated was on our tweeter.
I'll tell you a little about innovations.
Client program
For those who obfusts their programs all the time, we have significantly simplified this process - now you can use a special client program to work with our service. The created configuration can be saved to the project, and then obfuscated your programs in one click.
')

The program is distributed as OpenSource (MIT license), everyone can get acquainted with the source code . In the future, we plan to bring the API into a separate module, for easy integration with other programs.
The program is still beta, we apologize in advance for possible bugs.
Control flow obfuscation
A new control flow obfuscation protection algorithm has been added to AppFuscator. The essence of this method consists in dividing the program algorithm into separate components and building from them a complexly-connected transition graph. As a result, the logic of the code is not quite understandable.
A small example:

The full code of the obfuscated method can be viewed here (for clarity, all types of protection are turned off except for the control flow obfuscation)
Of the features:
- Several different ways to transition between blocks
- Switch support instructions
- Dynamic counters that transmit state between blocks
Summary: it is possible to write a reverse decoder, but it will be quite difficult, expensive and difficult. We'll have to sharpen it personally for our algorithm, and we will try to update it more often so that the life of a potential hacker is fun and eventful.
Improved WPF Obfuscator
Significantly refined WPF obfuscation algorithms. Our obfuscator can rename objects used in XAML markup, and at the same time correctly handles Bingings, Attached Properties, Attached Events and other clever constructions from the WPF world. As a rule, the process of obfuscation does not require manual configuration; intelligent code analysis and XAML markup (or, more precisely, BAML) will take care of everything.

User account
Now each user has access to a personal account . You can see the history of obfuscations in it and download previous obfuscated versions for studying MAP files.

We will be glad to hear your questions and suggestions, as well as to discuss your ideas.
UPD1. Placed 10 promotional codes for registration:
UPD2. Invites run out. Who was not enough, another one that was not activated was on our tweeter.
Source: https://habr.com/ru/post/169195/
All Articles