File hosting Mega began to pay rewards for found vulnerabilities
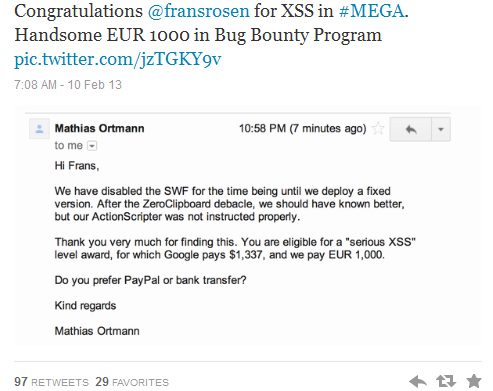
About a week ago on Habré there was news that the file sharing service Mega, or rather its creator, developed a reward system for the found vulnerabilities. The amount of remuneration can reach 10 thousand euros. The first awards have already found their owners.
In total, seven people have now received awards, whose personalities, which are reasonable, are not revealed. Of course, the file sharing service quickly closed the found holes / vulnerabilities, so the Mega operation became more reliable (I would like to hope so).
')
Total vulnerabilities in Mega are divided into six levels, including "fundamental problems" and "theoretical scenarios". Here is a list of found and fixed vulnerabilities, if anyone is interested:
List
List :
Class IV vulnerabilities
["Cryptographic design flaws that can be exploited only after compromising server infrastructure (live or post-mortem)"]
Invalid application of the CBC-MAC as a secure hash to integrity-check active content. Mitigating factors: No data content has been established at a time of 1024 bit SSL key on the static content servers. Fixed within hours.
Class III vulnerabilities
["Generally exploitable cross-site scripting)"]
XSS through file and folder names. Mitigating factors: None. Fixed within hours.
XSS on the file download page. Mitigating factors: Chrome is not vulnerable. Fixed within hours.
XSS in a third-party component (ZeroClipboard.swf). Mitigating factors: None. Fixed within hours.
Class II vulnerabilities
["For example, if you’re sending a certificate or DNS / BGP manipulation script, you’ll be able to do this?"
XSS through strings has been passed through. Mitigating factors — None. Fixed within hours.
Class I vulnerabilities
["All lower-impact or purely theoretical scenarios"]
HTTP Strict Transport Security header was missing. Fixed Also, mega.co.nz and * .api.mega.co.nz will be HSTS-preloaded in Chrome.
X-Frame-Options-Header - Redressing Risk. Fixed
Class IV vulnerabilities
["Cryptographic design flaws that can be exploited only after compromising server infrastructure (live or post-mortem)"]
Invalid application of the CBC-MAC as a secure hash to integrity-check active content. Mitigating factors: No data content has been established at a time of 1024 bit SSL key on the static content servers. Fixed within hours.
Class III vulnerabilities
["Generally exploitable cross-site scripting)"]
XSS through file and folder names. Mitigating factors: None. Fixed within hours.
XSS on the file download page. Mitigating factors: Chrome is not vulnerable. Fixed within hours.
XSS in a third-party component (ZeroClipboard.swf). Mitigating factors: None. Fixed within hours.
Class II vulnerabilities
["For example, if you’re sending a certificate or DNS / BGP manipulation script, you’ll be able to do this?"
XSS through strings has been passed through. Mitigating factors — None. Fixed within hours.
Class I vulnerabilities
["All lower-impact or purely theoretical scenarios"]
HTTP Strict Transport Security header was missing. Fixed Also, mega.co.nz and * .api.mega.co.nz will be HSTS-preloaded in Chrome.
X-Frame-Options-Header - Redressing Risk. Fixed
It is likely that in the near future, Mega will pay a number of awards, as reports of various kinds of errors / vulnerabilities in the service continue to appear.
Via thenextweb
Source: https://habr.com/ru/post/169083/
All Articles