Critical vulnerability in many routers of various vendors
As previously reported , DefenseCode discovered a zero-day vulnerability in Cisco Linksys routers. Representatives of the company notified the vendor and took a timeout for a couple of weeks before revealing the details of the vulnerability. Time was up, some details were revealed and it turned out that not only Cisco Linksys is vulnerable.
We are talking about several vulnerabilities at once, which lie in a number of implementations of the UPnP protocol and SSDP (based on the Intel / Portable UPnP SDK and MiniUPnP SDK):
Vulnerabilities allow to cause a denial of service or to execute arbitrary code on a device without authorization. And since Many routers interact with UPnP through the WAN, this makes them vulnerable not only to attack from a local network, but also from remote networks. Those. from virtually any computer on the Internet. Not only routers, but generally any equipment that uses UPnP such as printers, media servers, IP cameras, NAS, smart TV, etc., can be vulnerable. Those. we are talking about millions of devices!
The company rapid7 has released a scanner to check their devices for vulnerabilities. Online version is available here .
')
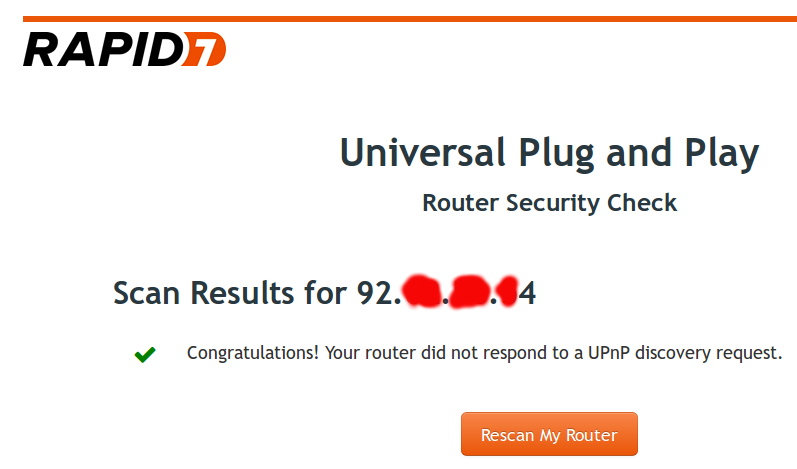
I was lucky. And you?
The IP address from which the user came is checked. Those. enter any address for verification will not work.
The offline version of the vulnerability scanner can be downloaded from this link . This scanner only supports Microsoft Windows. Mac OS X and Linux users can use Metasploit for this purpose. Metasploit usage example:
The answer will be something like this:
At the moment, it is known that TP-LINK has released a beta version of the firmware , which closes a vulnerability in the TD-W8960N hardware. By the end of February, they plan to release an official firmware.
As a temporary measure, it is recommended to turn off UPnP support on network equipment.
Related Links:
1. List of devices where the presence of vulnerabilities is confirmed
2. Rapid7 UPnP Vulnerability Report
3. DefenseCode UPnP Vulnerability Report
UPD: and today it became known about the regular zero-day vulnerabilities in various routers
Here are just some of the vendors where there is a vulnerability.
- Broadcom,
- Asus
- Cisco
- TP-Link
- Zyxel
- D-Link
- Netgear
- US Robotics
We are talking about several vulnerabilities at once, which lie in a number of implementations of the UPnP protocol and SSDP (based on the Intel / Portable UPnP SDK and MiniUPnP SDK):
CVE list
- CVE-2012-5958
- CVE-2012-5959
- CVE-2012-5960
- CVE-2012-5961
- CVE-2012-5962
- CVE-2012-5963
- CVE-2012-5964
- CVE-2012-5965
- CVE-2013-0229
- CVE-2013-0230
Vulnerabilities allow to cause a denial of service or to execute arbitrary code on a device without authorization. And since Many routers interact with UPnP through the WAN, this makes them vulnerable not only to attack from a local network, but also from remote networks. Those. from virtually any computer on the Internet. Not only routers, but generally any equipment that uses UPnP such as printers, media servers, IP cameras, NAS, smart TV, etc., can be vulnerable. Those. we are talking about millions of devices!
The company rapid7 has released a scanner to check their devices for vulnerabilities. Online version is available here .
')

I was lucky. And you?
The IP address from which the user came is checked. Those. enter any address for verification will not work.
The offline version of the vulnerability scanner can be downloaded from this link . This scanner only supports Microsoft Windows. Mac OS X and Linux users can use Metasploit for this purpose. Metasploit usage example:
$ msfconsole
msf>
msf> use auxiliary / scanner / upnp / ssdp_msearch
msf auxiliary (ssdp_msearch)> set RHOSTS 192.168.0.0/24
msf auxiliary (ssdp_msearch)> run
The answer will be something like this:
[*] 192.168.0.9:1900 SSDP Net-OS 5.xx UPnP/1.0 | 192.168.0.9:3278/etc/linuxigd/gatedesc.xml
[+] 192.168.0.254:1900 SSDP miniupnpd/1.0 UPnP/1.0 | vulns:2 (CVE-2013-0229, CVE-2013-0230)At the moment, it is known that TP-LINK has released a beta version of the firmware , which closes a vulnerability in the TD-W8960N hardware. By the end of February, they plan to release an official firmware.
As a temporary measure, it is recommended to turn off UPnP support on network equipment.
Related Links:
1. List of devices where the presence of vulnerabilities is confirmed
2. Rapid7 UPnP Vulnerability Report
3. DefenseCode UPnP Vulnerability Report
UPD: and today it became known about the regular zero-day vulnerabilities in various routers
Source: https://habr.com/ru/post/168613/
All Articles