China is organizing a man-in-the-middle attack against github users
China actively blocks access to all kinds of scary opposition sites (Tiananmei, 事件, 1989, Ban Habr in China). DPI is used for this in all - deep packet analysis. Which allows not only to close access to the IP / domain name, but to cut out the “extra”, or to close specific pages. If a website (like google) starts using SSL, then SSL in this direction is simply closed, leaving users with http-only.
However ... There are sites in the world that China does not risk banning. One of them is github. If a gmail or facebook ban leaves someone without a favorite email or being able to see the status of friends, then a github ban will leave hundreds and thousands of IT companies without access to the repositories of open-source applications and libraries. And they are already over 5000000 on the githaba. This means idle time in work, or even termination of the company’s activities (we know that this is not a problem, but the Chinese take their firewall quite seriously, and the Russian scenario “we will ban everything, and then need to figure it out "do not consider).
However, github always uses SSL. http access is simply not there. Thus, direct DPI is not possible, and some comrades, having got wind of it, began to actively use github to exchange information on how to bypass the firewall, addresses of proxy servers, etc.
')
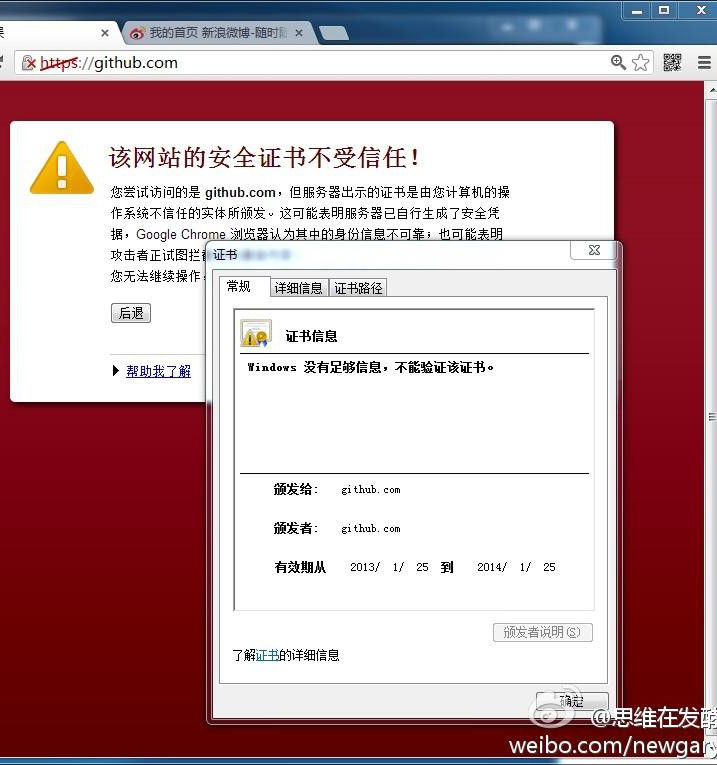
Not wanting to put up with this, China redirected github traffic to its servers. Of course, over https. And, of course, not having a githab certificate. Thus, Chinese users began receiving warnings about certificate errors, and the Chinese bloody gebnya was able to read and modify someone else's commits. Unless, of course, committing or reading, agrees that HTTPS with a fake certificate is normal. However, he has no options (legal), since There is no other way to access the githab.
This is all called man-in-the-middle. And this is the harsh Chinese reality.
The attack itself was short-lived, however, during this time, those who do not believe the terrible words of the browsers about the terrible consequences of a bad certificate could have:
1) Record information who was interested in political repositories (hmm, political repository, there is something in it).
2) Sniffing passwords and cookies
3) Fake repository information
4) Forgery or substitution of stored ssh-keys on the githab (which will give KKG the opportunity to have access to these repositories even after the end of the attack).
Next move.
This attack was simple and straightforward. The next move is to use CNNIC (Chinese root authentication server). If he issues a fake certificate to github.com, they will believe him. But CNNIC is trusted by most browsers.
Source: https://habr.com/ru/post/167727/
All Articles