PowerShell Web Access: Configuring

We continue to get acquainted with Powershell Web Access (PSWA).
In the previous article, we explained how to remotely install PowerShell Web Acess on a new web server from a Windows 8 client running RSAT. In this article, we will configure the gateway and configure authorization rules. The original article on petri.co.il can be found here . We invite interested persons under cat.
PSWA and Gateway Configuration
The commands needed to configure the gateway can be run directly on the server, but I prefer to do everything remotely. Run the remote PowerShell session on the server (I work on a Windows 8 machine).
')
PS C:\> enter-pssession CHI-WEB01 (In our case, instead of CHI-WEB01, we specify the name of our server - Approx. Translator ).
Now I will configure the gateway using a self-signed test certificate. Then we will make the site use a valid certificate.
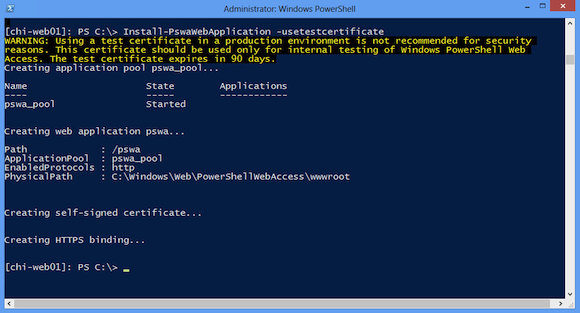
[chi-web01]: PS C:\> Install-PswaWebApplication –usetestcertificate The above command assumes that I did not change the default site name (“Default Web Site”), nor did the application name (“pswa”). Figure 1 shows the result.
Configuring Authorization Rules with PSWA
By default, no one has access to PowerShell Web Access. Authorization rules must be specified using the Add-PswaAuthorizationRule cmdlet . It should also be running on a web server, and I will use the current session. We specify the name of the user or his group to whom you would like to provide access. It is also necessary to clarify the names of computers to which remote access is possible (you can use the name of a group that contains computer accounts) and assign a configuration name.
The configuration is the remote endpoint name (remoting endpoint). Gateway PSWA establish a remote connection with it. Use Get-PSSessionConfiguration to number these sessions.
PS C:\> invoke-command {get-pssessionconfiguration} -ComputerName chi-dc03 Figure 2 shows the available endpoints for the CHI-DC03 server.

Session configuration must be present on all computers included in the rule. I'm going to create a test authorization rule using the Microsoft.PowerShell configuration. In fact, this is the end point to which you get remote access. You can also give the name of the rule, which I will do now.
[chi-web01]: PS C:\> Add-PswaAuthorizationRule -rulename "Test Rule 1" -computername chi-dc03 -username globomantics\jeff -configuration microsoft.powershell “Test Rule 1” was chosen as the rule name, of course you can do any other.
Pay attention to the format of the name of the user who is granted rights. In this case, we use globomantics \ jeff.
If you try to do this on a new system, you will most likely get the following error:
Add-PswaAuthorizationRule : This command must be run by a user account with permissions to perform Active Directory queries. If you run this command in an interactive session on the server (and not remote), then everything should work fine. The problem is the second retransmission (hop). The Add-PSwaAuthorizationRule cmdlet needs to communicate with a domain controller for which security design is not allowed to be in the PowerShell Remoting state. This second relay limitation can be overcome by activating CredSSP authentication. Caution : This should not be done “on the fly”, as there are security implications, prior research is required.
But in my case, since I want to use remote access, I will exit the remote session and activate CredSSP on my machine for the CHI-WEB01 server.
PS C:\> Enable-WSManCredSSP -DelegateComputer chi-web01 -Role Client Activated, now switch to server capabilities.
PS C:\> invoke-command {enable-wsmancredssp -Role Server -Force} -ComputerName chi-web01 Having done this, we restart the remote connection, specifying the CredSSP and my access settings.
PS C:\> enter-pssession chi-web01 -Authentication Credssp -Credential globomantics\jeff When I run the authorization command, it works as shown in Figure 3.

I can also check the rule:
[chi-web01]: PS C:\> Get-PswaAuthorizationRule Id RuleName User Destination ConfigurationName -- -------- ---- ----------- ----------------- 0 Test Rule 1 globomantics\jeff globomantics\chi... microsoft.powers... You can add as many authorization rules as you want. You can access the machine with PowerShell v2 if remote access is enabled on it. For example, add a rule for a domain controller with PowerShell v2.
[chi-web01]: PS C:\> Add-PswaAuthorizationRule -rulename "Test Rule 2" -computername chi-dc02 -username globomantics\jeff -configuration microsoft.powershell –force To remove a rule, use Remove-PwaAuthorizationRule . Refine the rule by id or rule object.
[chi-web01]: PS C:\> Remove-PswaAuthorizationRule -id 1 -whatif What if: Performing operation "Remove-PswaAuthorizationRule" on Target "Rule 'Test Rule 2' (ID: 1)". [chi-web01]: PS C:\> Get-PswaAuthorizationRule "test rule 2" | Remove-PswaAuthorizationRule –force –whatif What if: Performing operation "Remove-PswaAuthorizationRule" on Target "Rule 'Test Rule 2' (ID: 1)". What we have described above can be done through the IIS manager. But I assume that if you decide to configure PowerShell Web Access, you are more comfortable working in PowerShell. The configuration cmdlets must be run on the web server where the PSWA application is located. The next article will cover testing and using PowerShell Web Access.
The end of the translation.
Deploying Windows PowerShell Web Access - Technet article
Source: https://habr.com/ru/post/165227/
All Articles