Comprehensive protection of mobile phone information. Results of 2012
What will remember the outgoing year for the largest manufacturers of mobile communications: Samsung, Apple, Google, Nokia, Sony, Rim, Motorola, smaller corporations? First of all, a huge problem related to vulnerabilities in mobile phone information systems. At present, 6 billion phones have already been sold in the world (of which 1 billion are smartphones), and reliable information protection has not yet been created for them. The rapid demand for fashionable gadgets, obviously overtook the pace of their information protection, fierce rivalry for dividing the giant market and cheapening products was achieved primarily due to the level of security. Now this boomerang is back ...
The danger of hacker attacks threatening mobile users was noticeable even by such an example. In 2012, Ankort exhibited its products at four major international exhibitions of electronic technologies, in Las Vegas (USA), World Mobile Congress in Barcelona (Spain), CEBIT - in Hannover (Germany) and DSA in Kuala Lumpur (Malaysia) and everywhere the same picture was observed, the main slogan of the past events was information security of mobile phones.
Traditionally, the attention of clients who present specific requirements and represent a special layer among users is riveted to our developments: heads of state, major political figures, army representatives, bankers, businessmen, lawyers, famous artists, lawyers, in a word, all those for whom information security seems to be especially important condition.
')

This year, we could not help noticing the huge interest from the side of specialists representing the leaders of the modern IT industry. Along with high-ranking government officials from different countries, for example, only in Malaysia nine (!) Defense ministers from different countries visited our booth, and “Ankort” was also visited by ... heads of corporations engaged in mobile phone production. Even this fact alone, you see, leads to certain reflections.
I remember the outgoing year and another unexpected event: the appearance on the market of a large number of new companies that presented products related to the protection of information.
Various “Start-ups” obviously having felt “the trends of the time” were quick to show their developments in the field of security at the largest international exhibitions. They could be divided into two categories. One was made up of traditional software protection tools, and the other, more advanced ones, were hardware, in the military style.
It would seem that here it is evidence that the situation is changing and developers around the world have finally “woken up” by starting to offer mobile protection against hackers.
However, a more detailed analysis revealed an unexpected fact. After examining the websites and brochures of newcomers to the information protection market, it became clear that they contain mostly beautiful marketing reports, without any cryptographic specifics, at least about how the keys are generated and stored. But this is one of the most important factors.
Another fashionable trend to attract customers has been the numerous references in the phrase “Army Standard”. Individual firms cited the fact that their products are certified by military standards not only of the countries they represent, but of all NATO countries combined.
True, with a more detailed study, it turned out that in reality only one of the elements was certified, for example, the power supply, and not the entire product as a whole, but it was not possible to understand from advertising. In fact, for the sake of profit, the producer of information pseudo protection went to the deliberate deception of customers.
It is clear that in these cases, the calculation was solely on an inexperienced user who faced the problem of theft of personal or financial information, but who still did not have experience with cryptographic systems.
Those who already had this experience, and above all, users of software, this year tried to find something more serious, in the form of hardware. True, even with an unexpectedly large number of proposals from different countries, they had no choice, oddly enough - either our hardware stealthphone encoder or the product of the German company Rohde Schwartz. But more on that later…
First, it is necessary to clarify why the most sophisticated users no longer trust the software to protect information and completely lost interest in them. This year there was even a certain revaluation of values. And, apparently, a permanent gradation has been fixed forever, when only the information security hardware can claim the title of a professional-level system.
Why, you ask? After all, programs are very convenient and easy to use, they can be easily downloaded, they are relatively cheap, etc. All this is actually so, if you do not take into account that lately hackers have become so powerful computers and programs that they can hit any software protection installed on one or even several computers on the spot.
We give a fresh example. At the last Password 12 security conference, researcher Jeremy Gosney demonstrated the kind of standard device that hackers use today to crack your passwords. In total, it consists of 5 server cabinets equipped with 25 AMD Radeon graphic adapters that can transmit up to 10 gigabits per second. A password hacking program has been launched on the device, capable of performing 348 billion hashes of NTLM passwords per second. This speed indicates that the encrypted LM Windows XP password will be cracked in 6 minutes. From which the conference participants drew a logical conclusion: “a password that could have been broken for a million years yesterday could be cracked for lunch today ...”
You will ask how to act unhappy users after they face a similar or even more sophisticated and powerful adversary?
That's right! Applying cryptographic hardware protection is the only way to successfully resist any, even the most powerful hacker programs.
But even on this path, as it turned out, the owners of mobile equipment, seeking peace and security in the turbulent, violent and very dangerous electronic world, are waiting for unpleasant surprises.
A large number of protection hardware presented at the largest international exhibitions, except, as we have said, our company and the German Rode Schwartz offer “protection on CD”.
Our specialists have tested several samples of similar products and found out that the basic encryption in them is carried out using ordinary software, while the external one performs only the role of a keystore ...
In fact, this is the same marketing ploy used by unscrupulous manufacturers to mislead users and hinting to them that they are allegedly dealing with hardware protection.
Talk about the seriousness of such systems is not worth it. They do not protect against viruses, do not protect against unauthorized turning on of the microphone, and most importantly, they do not protect against dangerous information leaks through side channels. This happens because the phone's microphone is located next to the transmitting antenna. And the harmonics of the voice of a person talking through a microphone are superimposed on the signal going on the air through the antenna of a mobile phone along with the supposedly encrypted signal.
In other words, a low frequency voice signal recorded by the microphone is superimposed on the high frequency signal transmitted by the antenna. And, as a result, using a non-complex digital signal processing, a low-frequency voice signal can be extracted from it. Therefore, in reality, the so-called “encrypted” conversation can be quietly listened to with a conventional scanner costing only a few hundred dollars, up to five kilometers from the nearest GSM base station. Unfortunately, this time too, the calculation is made on the unpreparedness of users who do not know all the nuances.
As already noted, taking into account all these circumstances, according to the unanimous opinion of experts who analyzed the trends of the year at World Mobile Congress 2012 and CEBIT, only two companies presented real hardware protection to users that meets the highest standards: Ankort and Rode Schwartz.
At another international exhibition, in Malaysia, the competitor Ankort was the large cryptographic firm Crypto AG, which presented its secure phone as its latest development. Interestingly, even this company could not resist the buzzwords in advertising its phone, reckoning it to be a full-fledged hardware protection tool. Although in reality I used only the “SD” card, and the phone itself works only with the outdated operating system “Symbian”.
It should be recalled that several years ago, Ankort became the first company in the world to present a cryptosmartphone to the market — a special device with guaranteed cryptographic protection of voice information, subscriber authentication, and encryption of SMS and e-mail.

And it makes no sense to compare our developments, as they relate to different levels of protection of mobile phone information. Each of them has its own advantages, and in general it adequately copes with its task - individual protection of the voice data of a specific user.
Today we are talking about modern, mass protection of information in mobile phones, reducing the costs of users, including through the use of IP-telephony. Making it impossible for hackers to decipher and intercept not only mobile phone conversations, but also all kinds of data: voice communication via the Internet, SMS, MMS, email, social network databases, etc.
And it is very pleasant that in this dispute between two market leaders, international experts have given a palm to our products. However, from the comparative table below of the technical capabilities of the two hardware products, readers will be able to independently conclude why, in 2012, the Russian company Ankort is keeping the leadership in the development and production of tools for providing comprehensive information protection.
Both devices consist of a separate encoder from the mobile phone and special software that is installed on the mobile phone. However, the external similarity of the encoders in question is deceptive, since their technical and cryptographic characteristics are different, and the range of opportunities provided by them is unequal. The table below shows the technical and cryptographic characteristics of the hardware encoders "TopSec Mobile" and "Stealthphone Touch":
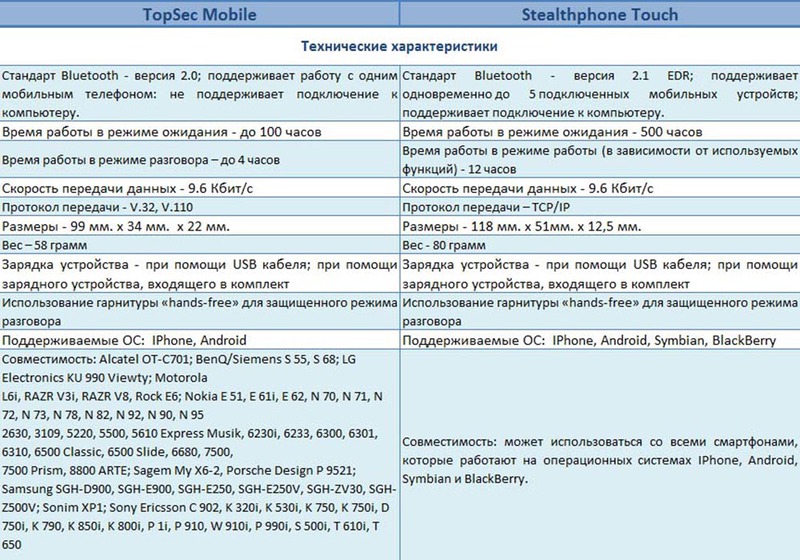
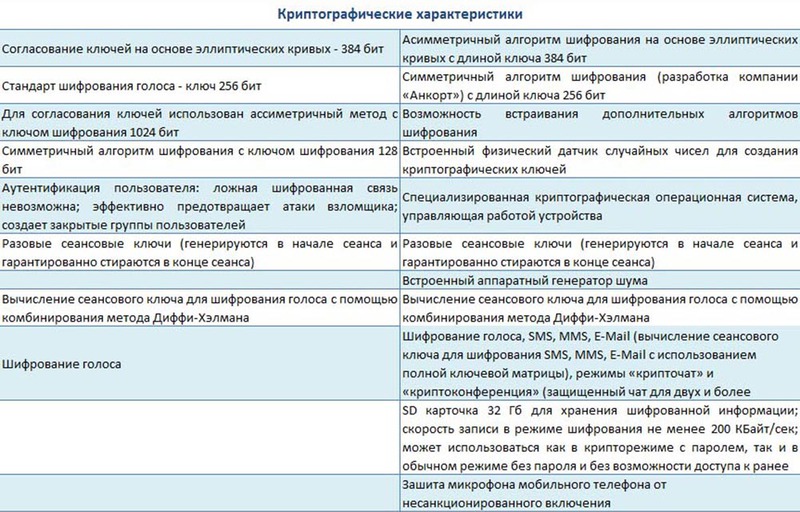
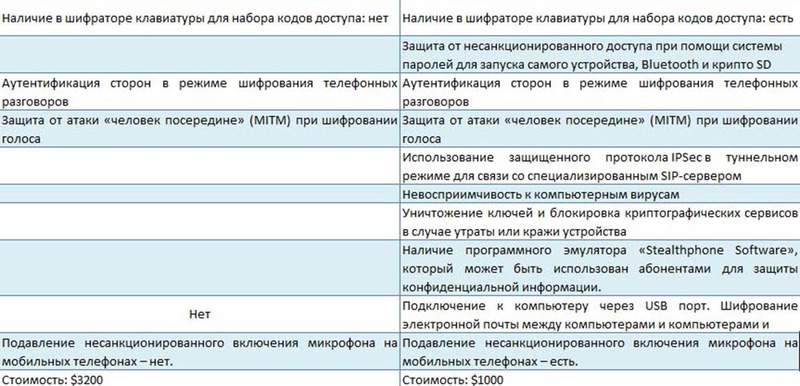
Based on the above data, reflecting the technical and cryptographic characteristics of hardware encoders, we can draw the following conclusions in favor of the “Stealthphone Touch”.
The functionality offered by the “Stealthphone Touch” to ensure the confidentiality of information on a mobile phone is very great. Each person, using his mobile phone, with the help of “Stealthphone Touch” can:
1. Encrypt voice, SMS, MMS, E-Mail;
2. Use the crypto chat and crypto conference chat modes;
3. Protect the microphone of your mobile phone from secretly removing information when the phone is in both call mode and standby mode;
4. Work with low-speed mobile Internet connections and transmit information in a protected form via 3G, 3.5G, EDGE, Wi-Fi and WiMAX communication channels;
5. Guaranteed to protect your data by transmitting encrypted information over a closed network and using the design features of the encoder (this is the “Stealthphone Touch” keyboard, on which various PIN access codes are entered);
6. Ensure the security of the operating system of your phone (Android, IPhone, Symbian, BlackBerry);
7. Use the encoder in conjunction with any modern mobile phone, as well as a tablet or personal computer to send e-mail;
8. Connect via Bluetooth at the same time up to 5 mobile devices;
9. Appreciate the high quality of voice transmission, user interface convenience, the duration of the no-charge operation period and the elegant concise design of the encoder, developed using nano technology.
In modern conditions, the governments of many countries follow the path of creating integrated information security systems at the state level, combining the efforts of government agencies, representatives of business communities and public organizations. The reason for this is the high level of network activity of hackers: in 2012, 556 million people suffered from their actions, that is, a hacker attack was carried out every 18 seconds (2). Popular high-tech mobile devices used to access the Internet and work with various applications are also in the “risk group”. Therefore, today it is very important not to make a mistake and choose the most cryptographically resistant solution that is suitable in all respects to protect user information.
More about Stealthphone
Sources:
1. Manufacturer data www2.rohde-schwarz.com/file_18186/TopSec-Mobile-VoIP_bro_en.pdf
2. According to the Internet resource www.memoid.ru/node/Gromkie_prestupleniya_russkih_hakerov
The danger of hacker attacks threatening mobile users was noticeable even by such an example. In 2012, Ankort exhibited its products at four major international exhibitions of electronic technologies, in Las Vegas (USA), World Mobile Congress in Barcelona (Spain), CEBIT - in Hannover (Germany) and DSA in Kuala Lumpur (Malaysia) and everywhere the same picture was observed, the main slogan of the past events was information security of mobile phones.
Traditionally, the attention of clients who present specific requirements and represent a special layer among users is riveted to our developments: heads of state, major political figures, army representatives, bankers, businessmen, lawyers, famous artists, lawyers, in a word, all those for whom information security seems to be especially important condition.
')

This year, we could not help noticing the huge interest from the side of specialists representing the leaders of the modern IT industry. Along with high-ranking government officials from different countries, for example, only in Malaysia nine (!) Defense ministers from different countries visited our booth, and “Ankort” was also visited by ... heads of corporations engaged in mobile phone production. Even this fact alone, you see, leads to certain reflections.
I remember the outgoing year and another unexpected event: the appearance on the market of a large number of new companies that presented products related to the protection of information.
Various “Start-ups” obviously having felt “the trends of the time” were quick to show their developments in the field of security at the largest international exhibitions. They could be divided into two categories. One was made up of traditional software protection tools, and the other, more advanced ones, were hardware, in the military style.
It would seem that here it is evidence that the situation is changing and developers around the world have finally “woken up” by starting to offer mobile protection against hackers.
However, a more detailed analysis revealed an unexpected fact. After examining the websites and brochures of newcomers to the information protection market, it became clear that they contain mostly beautiful marketing reports, without any cryptographic specifics, at least about how the keys are generated and stored. But this is one of the most important factors.
Another fashionable trend to attract customers has been the numerous references in the phrase “Army Standard”. Individual firms cited the fact that their products are certified by military standards not only of the countries they represent, but of all NATO countries combined.
True, with a more detailed study, it turned out that in reality only one of the elements was certified, for example, the power supply, and not the entire product as a whole, but it was not possible to understand from advertising. In fact, for the sake of profit, the producer of information pseudo protection went to the deliberate deception of customers.
It is clear that in these cases, the calculation was solely on an inexperienced user who faced the problem of theft of personal or financial information, but who still did not have experience with cryptographic systems.
Those who already had this experience, and above all, users of software, this year tried to find something more serious, in the form of hardware. True, even with an unexpectedly large number of proposals from different countries, they had no choice, oddly enough - either our hardware stealthphone encoder or the product of the German company Rohde Schwartz. But more on that later…
First, it is necessary to clarify why the most sophisticated users no longer trust the software to protect information and completely lost interest in them. This year there was even a certain revaluation of values. And, apparently, a permanent gradation has been fixed forever, when only the information security hardware can claim the title of a professional-level system.
Why, you ask? After all, programs are very convenient and easy to use, they can be easily downloaded, they are relatively cheap, etc. All this is actually so, if you do not take into account that lately hackers have become so powerful computers and programs that they can hit any software protection installed on one or even several computers on the spot.
We give a fresh example. At the last Password 12 security conference, researcher Jeremy Gosney demonstrated the kind of standard device that hackers use today to crack your passwords. In total, it consists of 5 server cabinets equipped with 25 AMD Radeon graphic adapters that can transmit up to 10 gigabits per second. A password hacking program has been launched on the device, capable of performing 348 billion hashes of NTLM passwords per second. This speed indicates that the encrypted LM Windows XP password will be cracked in 6 minutes. From which the conference participants drew a logical conclusion: “a password that could have been broken for a million years yesterday could be cracked for lunch today ...”
You will ask how to act unhappy users after they face a similar or even more sophisticated and powerful adversary?
That's right! Applying cryptographic hardware protection is the only way to successfully resist any, even the most powerful hacker programs.
But even on this path, as it turned out, the owners of mobile equipment, seeking peace and security in the turbulent, violent and very dangerous electronic world, are waiting for unpleasant surprises.
A large number of protection hardware presented at the largest international exhibitions, except, as we have said, our company and the German Rode Schwartz offer “protection on CD”.
Our specialists have tested several samples of similar products and found out that the basic encryption in them is carried out using ordinary software, while the external one performs only the role of a keystore ...
In fact, this is the same marketing ploy used by unscrupulous manufacturers to mislead users and hinting to them that they are allegedly dealing with hardware protection.
Talk about the seriousness of such systems is not worth it. They do not protect against viruses, do not protect against unauthorized turning on of the microphone, and most importantly, they do not protect against dangerous information leaks through side channels. This happens because the phone's microphone is located next to the transmitting antenna. And the harmonics of the voice of a person talking through a microphone are superimposed on the signal going on the air through the antenna of a mobile phone along with the supposedly encrypted signal.
In other words, a low frequency voice signal recorded by the microphone is superimposed on the high frequency signal transmitted by the antenna. And, as a result, using a non-complex digital signal processing, a low-frequency voice signal can be extracted from it. Therefore, in reality, the so-called “encrypted” conversation can be quietly listened to with a conventional scanner costing only a few hundred dollars, up to five kilometers from the nearest GSM base station. Unfortunately, this time too, the calculation is made on the unpreparedness of users who do not know all the nuances.
As already noted, taking into account all these circumstances, according to the unanimous opinion of experts who analyzed the trends of the year at World Mobile Congress 2012 and CEBIT, only two companies presented real hardware protection to users that meets the highest standards: Ankort and Rode Schwartz.
At another international exhibition, in Malaysia, the competitor Ankort was the large cryptographic firm Crypto AG, which presented its secure phone as its latest development. Interestingly, even this company could not resist the buzzwords in advertising its phone, reckoning it to be a full-fledged hardware protection tool. Although in reality I used only the “SD” card, and the phone itself works only with the outdated operating system “Symbian”.
It should be recalled that several years ago, Ankort became the first company in the world to present a cryptosmartphone to the market — a special device with guaranteed cryptographic protection of voice information, subscriber authentication, and encryption of SMS and e-mail.

And it makes no sense to compare our developments, as they relate to different levels of protection of mobile phone information. Each of them has its own advantages, and in general it adequately copes with its task - individual protection of the voice data of a specific user.
Today we are talking about modern, mass protection of information in mobile phones, reducing the costs of users, including through the use of IP-telephony. Making it impossible for hackers to decipher and intercept not only mobile phone conversations, but also all kinds of data: voice communication via the Internet, SMS, MMS, email, social network databases, etc.
And it is very pleasant that in this dispute between two market leaders, international experts have given a palm to our products. However, from the comparative table below of the technical capabilities of the two hardware products, readers will be able to independently conclude why, in 2012, the Russian company Ankort is keeping the leadership in the development and production of tools for providing comprehensive information protection.
Both devices consist of a separate encoder from the mobile phone and special software that is installed on the mobile phone. However, the external similarity of the encoders in question is deceptive, since their technical and cryptographic characteristics are different, and the range of opportunities provided by them is unequal. The table below shows the technical and cryptographic characteristics of the hardware encoders "TopSec Mobile" and "Stealthphone Touch":



Based on the above data, reflecting the technical and cryptographic characteristics of hardware encoders, we can draw the following conclusions in favor of the “Stealthphone Touch”.
The functionality offered by the “Stealthphone Touch” to ensure the confidentiality of information on a mobile phone is very great. Each person, using his mobile phone, with the help of “Stealthphone Touch” can:
1. Encrypt voice, SMS, MMS, E-Mail;
2. Use the crypto chat and crypto conference chat modes;
3. Protect the microphone of your mobile phone from secretly removing information when the phone is in both call mode and standby mode;
4. Work with low-speed mobile Internet connections and transmit information in a protected form via 3G, 3.5G, EDGE, Wi-Fi and WiMAX communication channels;
5. Guaranteed to protect your data by transmitting encrypted information over a closed network and using the design features of the encoder (this is the “Stealthphone Touch” keyboard, on which various PIN access codes are entered);
6. Ensure the security of the operating system of your phone (Android, IPhone, Symbian, BlackBerry);
7. Use the encoder in conjunction with any modern mobile phone, as well as a tablet or personal computer to send e-mail;
8. Connect via Bluetooth at the same time up to 5 mobile devices;
9. Appreciate the high quality of voice transmission, user interface convenience, the duration of the no-charge operation period and the elegant concise design of the encoder, developed using nano technology.
In modern conditions, the governments of many countries follow the path of creating integrated information security systems at the state level, combining the efforts of government agencies, representatives of business communities and public organizations. The reason for this is the high level of network activity of hackers: in 2012, 556 million people suffered from their actions, that is, a hacker attack was carried out every 18 seconds (2). Popular high-tech mobile devices used to access the Internet and work with various applications are also in the “risk group”. Therefore, today it is very important not to make a mistake and choose the most cryptographically resistant solution that is suitable in all respects to protect user information.
More about Stealthphone
Sources:
1. Manufacturer data www2.rohde-schwarz.com/file_18186/TopSec-Mobile-VoIP_bro_en.pdf
2. According to the Internet resource www.memoid.ru/node/Gromkie_prestupleniya_russkih_hakerov
Source: https://habr.com/ru/post/162577/
All Articles