McAfee Deep Defender: from plugging holes to protection "from the inside"
When Intel acquired anti-virus software developer McAfee in 2010, there was a lot of talk in the professional community about the feasibility of this transaction. Comments then were given at the highest level, some of them appeared in Habré . Meanwhile, now, after only two years, the logic of the association seems to be just iron: the possibilities of purely software protection against malicious code are almost exhausted, a transition to combined, hardware and software solutions is necessary. About them today and talk.
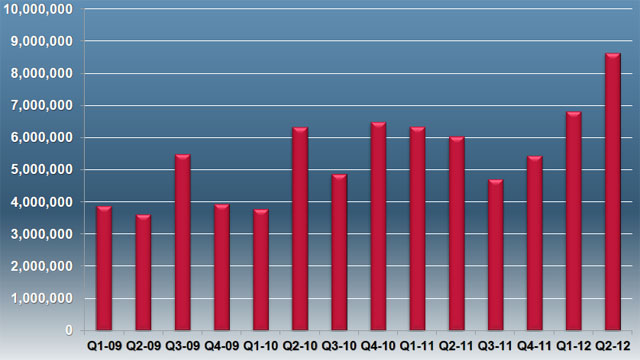
The number of new malware. McAfee data.
The history of the struggle of anti-virus programs with malicious code resembles a chronicle of the “trench warfare” of the First World War era: the same protracted positional battles and the same lack of hope for decisive success. Rather, the opposite is true: while the virus scum continues to complicate the algorithms of its behavior, the “asymmetric response” options of the fighters are getting smaller. Including the fact that an antivirus is a little more than just an OS program that can be counteracted with other programs, you can be misled, finally, simply destroyed. On the other hand, tracking of suspicious activity at the application level requires a large amount of resources, and they are not endless in the system, and antivirus software is always forced to take this into account. In general, the more intense the struggle, the more problems. The situation is somewhat similar to that shown in the title picture: the cube has a finite size, and you can make as many holes in it. Now imagine that someone has to stop them ...
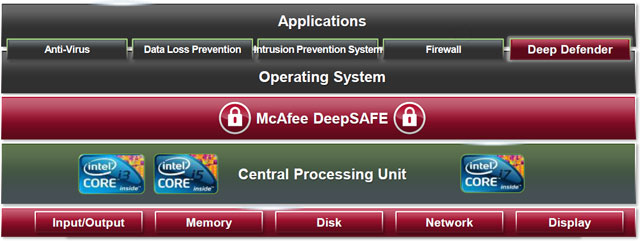
And then it's time to talk about the most innovative approaches. Having received the An Intel Company prefix, McAfee continued to develop a system that combines its own software solutions with the capabilities of Intel processors, and first of all (but not only) with hardware virtualization Intel VT-x (supported by Intel Core i3, i5 and i7). The general protection scheme looks like this:
')
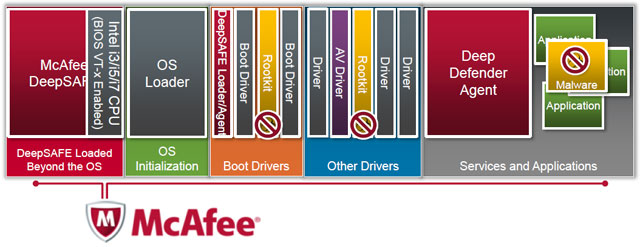
DeepSafe component is loaded to the operating system and separately from it. Located “below” the OS kernel (closer to the hardware), it monitors memory and the processor in all operating modes of the OS, starting with loading drivers and ending with launching any kind of software (unauthorized or with user). DeepSafe triggers work so fast that the malicious code doesn't even have time to execute properly. All cases of suspicious behavior of executable program modules and other “strange rustles” in the core of the DeepSafe system are reported “to the top” - to the Deep Defender agent, who decides on actions appropriate to the level of danger.
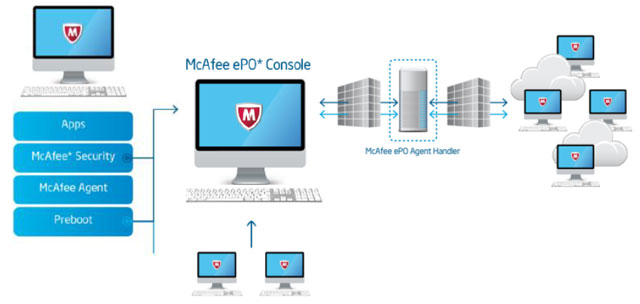
McAfee ePO Deep Command Infrastructure
In turn, the Deep Defender protection agents installed on user computers are under the central control panel of the McAfee ePolicy Orchestrator (ePO) system, which implements common corporate security policies by numerous tools developed by Intel and McAfee: besides those already mentioned, this is Intel vPro , Intel Anti-Theft and others. This is the macro level of protection at the level of the company's network infrastructure. Let us return, however, to the micro level - an individual PC processor.
 What antivirus can be called ideal? (For brevity, we will understand any malicious code as a virus.) One that does not affect other software components of the system, does not take resources from them and doesn’t manifest itself at all, silently doing its job. It is to this result that one should strive, and the only way to achieve it is to transfer the maximum number of protection components to the hardware level, in close proximity to the processor.
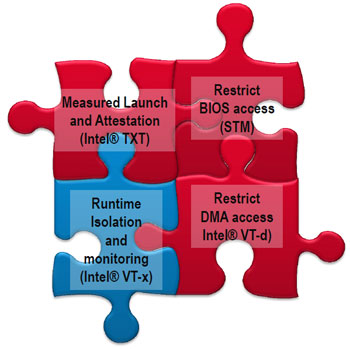
What antivirus can be called ideal? (For brevity, we will understand any malicious code as a virus.) One that does not affect other software components of the system, does not take resources from them and doesn’t manifest itself at all, silently doing its job. It is to this result that one should strive, and the only way to achieve it is to transfer the maximum number of protection components to the hardware level, in close proximity to the processor.On this path, Intel has achieved undoubted success: these are the technologies that control the execution of the code now:
- Boot Protection (Intel TXT - Trusted Execution Technology)
- Protection against software attacks (Intel VT-x - Virtualization Technology for IA-32, Intel 64 and Intel Architecture)
- Protection from DMA direct memory access (Intel VT-d - Virtualization Technology for Directed I / O)
- Protection against BIOS attacks
Let us consider briefly how the Intel VT-x technology serves as a guard of law and order.
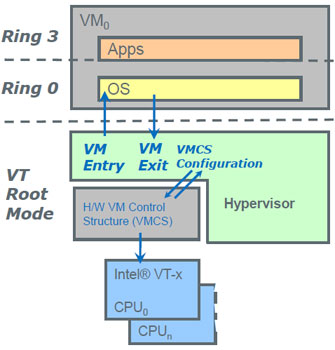
VM Control Structure (VMCS) allows the hypervisor to track the attributes of software code execution at the level of processor primitives. The hypervisor itself is isolated from the OS space, so it is able to monitor software at various privilege levels without any changes.
What is the prospect of combined protective solutions? Increasing monitoring parameters and increasing the nature of responses. For example, if we talk about the core of the system, we can single out a number of critical software interfaces that need to be monitored — first of all, those that are commonly used to inject malicious code into it. Special care will have to surround the drivers loaded into the system, which by their very nature often become sources of problems.
As for the application layer, it is important to achieve universal monitoring of critical APIs without slowing down the work of programs, but also without a chance to avoid control. New approaches do not reject the old proven methods, such as self-checking of antivirus software, placing suspicious objects in a protected execution environment (sandbox) - all this in one form or another will exist in the future, enriched with new functionality. But the development vector has already been set, and we expect the main achievements in this direction.
As we can see, the protection “from below” still has a difficult way to go. But there is no other option.
Source: https://habr.com/ru/post/160709/
All Articles