Aruba Networks now in Russia. Part 1 - First acquaintance
Greetings to all!
I wanted to tell the public about a relatively recent player in the Russian market in the field of corporate wireless network equipment - Aruba Networks, in which much attention is paid to wireless network security. This post is primarily a descriptive, designed to give a first idea about Aruba, so some things can be intentionally simplified.
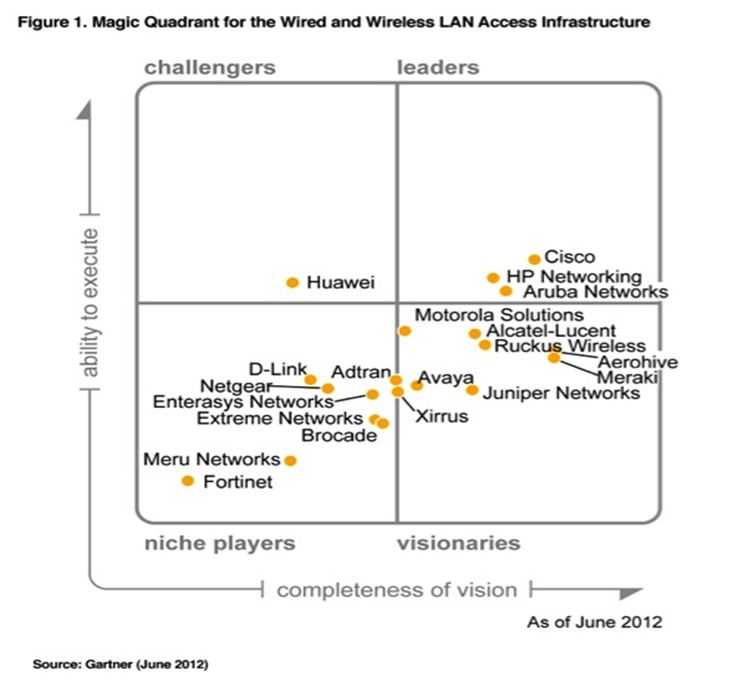
Yes, “behind the hill” Aruba Networks is very well known, and even in the lead, in the June version of Gartner, along with Cisco and HP Networking:
What is Aruba Networks? These are, first of all, solutions designed to build a secure wireless local area network in offices / geographically distributed corporations using public networks / relatively small open areas (stadiums, etc.). For building class MAN wireless networks, the solution described below does not fit; you need to use either Aruba Networks Mesh or Motorola solutions.
The main difference from Cisco products is the lower price of the final solution (about 1.5 times) and the smaller amount of equipment (for example, in most cases no additional network management software is required - the software built into the controller completely covers the needs of the enterprise, although, of course, there are exceptions, which will be discussed later).
In addition, the manufacturer offers some features that are not available from other manufacturers for such money.
What can Aruba do besides the actual construction of a centrally controlled Wi-Fi network? The list of features is quite large. Below we will try to mention them all.
Solutions are offered from controllers for small offices (branch offices - in the terminology of Aruba Networks), which support 8 access points connected directly to them via LAN or up to 64 remote access points (I don’t remember right now - there is no specification at hand) and to modular ones chassis - each module can support up to 2048 connected LAN points.
')
A small digression - why am I writing “LAN-connected-points” and “remote access points”? These are different connections from the point of view of the controller:
By LAN : access points are within the organization's network, the controller has a specific internal static address. Communication with points occurs via the GRE protocol.
"Remote" access points . In the terminology of Aruba Networks, this is called a “remote access point” (while there is some confusion - about it below). This means that the access point (TD) is connected to the controller through public networks (the Internet) using VPN (IPSec protocol, but you can choose another one). This is good for organizing wireless networks in small remote branches, where, on the one hand, installing a controller is expensive, and it makes no sense, and access to the network with corporate security policies must be provided. In this case, the controller, of course, must have an IP visible from the outside, i.e. either be located in the DMZ, or the ability to forward packets from the DMZ to the controller must be configured.
A small retreat. I plan to describe the specific features of the implementation for each option in further articles, but now I’ll just say that in the case of “remote TDs”, it is possible to set up routing in such a way that the user's Internet requests will go straight to the Internet, through a local provider, time service requests TD to the controller and all user requests going to the head office (access to the internal local network, for example) will go through VPN
A nice feature when organizing networks is that no direct (physical) connection of the AP to the LAN is required - service information to them can be “over the air” using Mesh technology. In this case, you need to physically connect only 1 TD, since the controller does not have a built-in Wi-FI module.
Low-end controllers (600 series) also have USB ports to which you can connect either an external USB 3 / 4G modem (Yota, for example, works) or organize a NAS / shared network printer / simply plug in a USB flash drive, making them available to network users ( in accordance with access policies, if any)
In addition, all controllers support the creation of a guest portal with the ability to create individual guest accounts with a limited expiration date, various authentication schemes (LDAP, RADIUS, internal database, certificates, etc.), have a built-in firewall that can work with 2- Go to level 7 of the OSI model, wireless intrusion prevention functions (WIPS - Wireless Intrusion Prevention), the possibility of suppressing "foreign" access points (in fact, suppression of the connection of client devices to foreign networks in the area of "their "TD), the ability to encrypt traffic on Suite B. Standards
Yes, there is a protocol for searching equipment in the local network - the Aruba Discovery Protocol. Those. sticking an access point somewhere in the steel mill of a giant plant, without any particular hassle, we will get all the necessary settings and policies for it. If, of course, you can make a route to the controller. The ARM technology is also built in - adaptive frequency control, which allows you to monitor the range and hang the client on the least loaded channel, increase the transmitter power somewhere, lower it somewhere ... Moreover, TDs are grouped together, for each group their settings and security policies, so without problems, different policies are implemented in different branches. QoS on guaranteed channel width is also present; In addition, VoIP (with bandwidth reservation for this type of traffic) and wireless video surveillance system (also with redundancy) are easily configured.
Well, a few words about the aesthetic look. The middle-level controllers (3000 series), in general, like ordinary switches, are probably familiar to everyone, can be put in a standard rack. Top - modular - triple chassis, supports up to 4 modules. The junior series - 600 - is designed to be installed on any horizontal surface, and even some attempt has been made to refine the design:

From above, the cactus pot is asked to calm the workers in order to neutralize harmful radiation.
All controllers have Ethernet ports 10/100 (Fast) and Ethernet 10/100/1000 (Gigabit). Yes, some controller ports have PoE. Some models also have SFPs. Also necessarily present is the console port RJ-45 (RS-232 protocol). You can connect to the controller either via HTTPS or using SSH / Telnet to work with the CLI. And, it should be noted, some operations are easier to perform in the CLI than in the web snout.
Controllers support almost all common traffic encryption algorithms and security protocols.
As well as the controllers can determine the location of the "enemy" TD, client devices and track their movement. It is necessary, at least, 3 TD - because positioning is implemented on the principles of triangulation. True, here, too, has its own characteristics, but you can talk about them later, if there is interest.
Aruba Networks offers a variety of access points - ranging from simple devices that do what they have to - provide a Wi-Fi network and ending up with monsters to work in difficult conditions: in dusty workshops, in the open air, etc.
All access points can operate in temperature ranges from 0 to 50 C (for a model intended for working outdoors, from -30 if memory does not change, to +55 C), at a relative humidity of 0-95% without condensation (excluding again, access points intended for outdoor use). Next, we will talk about access points designed to work indoors.
Most models, excluding the most budget, are able to work simultaneously in 2.4 and 5 GHz modes (802.11 a / b / g / n), using MIMO technology to increase the speed of data transmission. Some models allow you to work only in one selected mode (2.4 or 5 GHz), the transmitter power of the point is controlled by the controller. The maximum, usually, reaches 21-23 dBm (excluding supplies for the Chinese - there are 30 in each). Data transfer speeds - from 150 to 300 Mbps, again, depends on the model. Additional chips - like a spectrum analyzer - are already supported from mid-price models.
The general for all points: the same model, as a rule, is issued performed by with internal antennas or external. In turn, some models come with external antennas "on board", and some with connectors for external antennas. All points support either PoE or power adapters.
From the interfaces on the TD there is a Fast / Gigabit Ethernet and a console RJ 45 port. Of the additional features, it can be noted that TDs are able to function in 2 modes: either under the control of the controller or autonomously. In the latter case, the AP is able to perform the functions of a virtual controller for several other points connected to it. Or just be an expensive compact router. But there are limitations - “Home” (in case it works in the virtual controller mode) the AP should receive a DHCP address, otherwise Wi-Fi modules will not rise, despite the joyful indication. This is due to some idiocy of the TD architecture, which, I think, the manufacturer still deliberately introduced, because there are TDs of the RAP class (see below), which this restriction does not apply.
When you turn off the TD no information about the network, policies and so on. they do not remain, i.e. when enabled, the TD will request settings from the controller. This causes a relatively large start time TD - from 5 to 7 minutes.
I propose to admire the TD of the average, so to speak, class:


For a snack, all TDs support the creation of 8 to 16 virtual access points. Those. one TD generates several networks, each with its own BSSID, correlated with its own VLAN.
Here we are close to a mess of terminology. rap is a type of connection of “ordinary” TDs, and RAP is a special class of TDs that resemble ordinary household wireless routers in terms of functionality and appearance, but which have the ability to work under the control of a controller and receive policies from it, with a large number of Ethernet ports suitable for connection, say, a network printer, and the ability to connect a USB modem. The main difference from conventional TDs is that there is no spectrum analyzer, and these TDs can save information about networks, policies, etc. They can also work as a standalone router - and for work there is no need to receive an address at all, as for ordinary TDs. But this species is devoid of the following features characteristic of conventional TD:
It may look like the image below:

Roughly speaking, this is such an advanced router.
This is good for the organization of wireless networks in a very very distant mutarakani, where the Internet works with poltychka, and the network still need to provide, and preferably with security policies. In general, there is a giant plus in this decision: you can set up this box and hand it to the girl manager with the words “Masha, when you arrive, you plug the cable into this hole and plug it into the network. "Everything, the rest piece of iron will make itself.
And finally, let's see how the web interface is implemented. The screenshots below are taken from the administrator account, but there is an opportunity to play the role of an observer - only pages will be available to monitor customers or the system, without the ability to change the controller settings. When entering the main page, we get to the page where we can learn about the number of connected clients, network performance and other useful information:
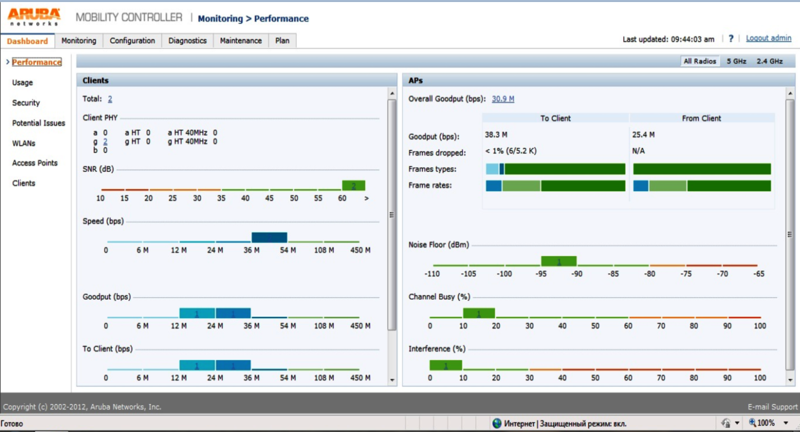
We can also receive and detailed information on the client:

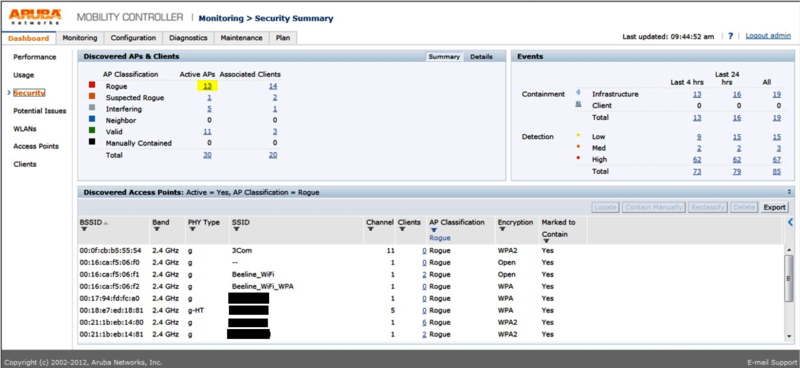
And also on this tab you can find a section on network security, where the number of suppressed (rogue) networks, neighbor (interference) and other networks, including service ones, is shown. Naturally, in each network, you can see the clients connected to it, get some information about bandwidth, etc., self-diagnostics, etc .:
And finally (I think everyone already understood what interface to work with Aruba), I will give a screenshot of the analysis of the radio-frequency environment:

Just a couple of words. Since the solution is self-sufficient, in most cases everything goes simply enough - you need to find a free port on the switch and plug the controller into it. To decide how the TD will work - using mesh technology (in this case, it is enough for them to provide only 220 V power) or via LAN, to set up the controller. Additional servers in most cases do not need to be installed; if necessary, the controller can be used as a router for some wired network segment. But it should be borne in mind that it is possible to detect the connection of devices to this network and mark them as illegal, as a result of which they will not work (yes, it is possible to detect unauthorized connections to the wired network segment).
Additional servers and software in most cases is not necessary; installation of additional servers is needed if you need to implement functionality like full-featured RTLS (location tracking system), centralized management of network equipment of various vendors (by the way, you can combine RTLS and management system), transparent BYOD, etc.
In the case of RTLS, Aruba Networks easily integrates with Ekahau or Aeroscout.
Here I tried to talk about Aruba Networks, but, unfortunately, the topic of security here is clearly not fully disclosed, although this is a key, in general, feature of the product. Therefore, I will write, as will be the time, a more “technical” post on the topic of security of Aruba Networks, and also try to uncover the remaining Aruba chips, such as BYOD, for which you don’t need to install any software on client devices, the AirWave multi-vendor control system access to VIA corporate LAN, implementation of one-time passwords, etc. - but the latter is in case of interest to the topic, probably.
It should be noted that, in contrast to the equipment of other vendors, there is already proposed functionality implemented in hardware, which requires only the acquisition of appropriate solutions.
And, if someone is interested - in Moscow there are now integrators who can build solutions based on Aruba Networks, but in order not to breed advertising - please clarify these questions through habrapost.
Thank you all for your attention!
I wanted to tell the public about a relatively recent player in the Russian market in the field of corporate wireless network equipment - Aruba Networks, in which much attention is paid to wireless network security. This post is primarily a descriptive, designed to give a first idea about Aruba, so some things can be intentionally simplified.
Yes, “behind the hill” Aruba Networks is very well known, and even in the lead, in the June version of Gartner, along with Cisco and HP Networking:

What is Aruba Networks? These are, first of all, solutions designed to build a secure wireless local area network in offices / geographically distributed corporations using public networks / relatively small open areas (stadiums, etc.). For building class MAN wireless networks, the solution described below does not fit; you need to use either Aruba Networks Mesh or Motorola solutions.
The main difference from Cisco products is the lower price of the final solution (about 1.5 times) and the smaller amount of equipment (for example, in most cases no additional network management software is required - the software built into the controller completely covers the needs of the enterprise, although, of course, there are exceptions, which will be discussed later).
In addition, the manufacturer offers some features that are not available from other manufacturers for such money.
What can Aruba do besides the actual construction of a centrally controlled Wi-Fi network? The list of features is quite large. Below we will try to mention them all.
Controllers
Solutions are offered from controllers for small offices (branch offices - in the terminology of Aruba Networks), which support 8 access points connected directly to them via LAN or up to 64 remote access points (I don’t remember right now - there is no specification at hand) and to modular ones chassis - each module can support up to 2048 connected LAN points.
')
A small digression - why am I writing “LAN-connected-points” and “remote access points”? These are different connections from the point of view of the controller:
By LAN : access points are within the organization's network, the controller has a specific internal static address. Communication with points occurs via the GRE protocol.
"Remote" access points . In the terminology of Aruba Networks, this is called a “remote access point” (while there is some confusion - about it below). This means that the access point (TD) is connected to the controller through public networks (the Internet) using VPN (IPSec protocol, but you can choose another one). This is good for organizing wireless networks in small remote branches, where, on the one hand, installing a controller is expensive, and it makes no sense, and access to the network with corporate security policies must be provided. In this case, the controller, of course, must have an IP visible from the outside, i.e. either be located in the DMZ, or the ability to forward packets from the DMZ to the controller must be configured.
A small retreat. I plan to describe the specific features of the implementation for each option in further articles, but now I’ll just say that in the case of “remote TDs”, it is possible to set up routing in such a way that the user's Internet requests will go straight to the Internet, through a local provider, time service requests TD to the controller and all user requests going to the head office (access to the internal local network, for example) will go through VPN
A nice feature when organizing networks is that no direct (physical) connection of the AP to the LAN is required - service information to them can be “over the air” using Mesh technology. In this case, you need to physically connect only 1 TD, since the controller does not have a built-in Wi-FI module.
Low-end controllers (600 series) also have USB ports to which you can connect either an external USB 3 / 4G modem (Yota, for example, works) or organize a NAS / shared network printer / simply plug in a USB flash drive, making them available to network users ( in accordance with access policies, if any)
In addition, all controllers support the creation of a guest portal with the ability to create individual guest accounts with a limited expiration date, various authentication schemes (LDAP, RADIUS, internal database, certificates, etc.), have a built-in firewall that can work with 2- Go to level 7 of the OSI model, wireless intrusion prevention functions (WIPS - Wireless Intrusion Prevention), the possibility of suppressing "foreign" access points (in fact, suppression of the connection of client devices to foreign networks in the area of "their "TD), the ability to encrypt traffic on Suite B. Standards
Yes, there is a protocol for searching equipment in the local network - the Aruba Discovery Protocol. Those. sticking an access point somewhere in the steel mill of a giant plant, without any particular hassle, we will get all the necessary settings and policies for it. If, of course, you can make a route to the controller. The ARM technology is also built in - adaptive frequency control, which allows you to monitor the range and hang the client on the least loaded channel, increase the transmitter power somewhere, lower it somewhere ... Moreover, TDs are grouped together, for each group their settings and security policies, so without problems, different policies are implemented in different branches. QoS on guaranteed channel width is also present; In addition, VoIP (with bandwidth reservation for this type of traffic) and wireless video surveillance system (also with redundancy) are easily configured.
Well, a few words about the aesthetic look. The middle-level controllers (3000 series), in general, like ordinary switches, are probably familiar to everyone, can be put in a standard rack. Top - modular - triple chassis, supports up to 4 modules. The junior series - 600 - is designed to be installed on any horizontal surface, and even some attempt has been made to refine the design:

From above, the cactus pot is asked to calm the workers in order to neutralize harmful radiation.
All controllers have Ethernet ports 10/100 (Fast) and Ethernet 10/100/1000 (Gigabit). Yes, some controller ports have PoE. Some models also have SFPs. Also necessarily present is the console port RJ-45 (RS-232 protocol). You can connect to the controller either via HTTPS or using SSH / Telnet to work with the CLI. And, it should be noted, some operations are easier to perform in the CLI than in the web snout.
Controllers support almost all common traffic encryption algorithms and security protocols.
As well as the controllers can determine the location of the "enemy" TD, client devices and track their movement. It is necessary, at least, 3 TD - because positioning is implemented on the principles of triangulation. True, here, too, has its own characteristics, but you can talk about them later, if there is interest.
Access points
Aruba Networks offers a variety of access points - ranging from simple devices that do what they have to - provide a Wi-Fi network and ending up with monsters to work in difficult conditions: in dusty workshops, in the open air, etc.
All access points can operate in temperature ranges from 0 to 50 C (for a model intended for working outdoors, from -30 if memory does not change, to +55 C), at a relative humidity of 0-95% without condensation (excluding again, access points intended for outdoor use). Next, we will talk about access points designed to work indoors.
Most models, excluding the most budget, are able to work simultaneously in 2.4 and 5 GHz modes (802.11 a / b / g / n), using MIMO technology to increase the speed of data transmission. Some models allow you to work only in one selected mode (2.4 or 5 GHz), the transmitter power of the point is controlled by the controller. The maximum, usually, reaches 21-23 dBm (excluding supplies for the Chinese - there are 30 in each). Data transfer speeds - from 150 to 300 Mbps, again, depends on the model. Additional chips - like a spectrum analyzer - are already supported from mid-price models.
The general for all points: the same model, as a rule, is issued performed by with internal antennas or external. In turn, some models come with external antennas "on board", and some with connectors for external antennas. All points support either PoE or power adapters.
From the interfaces on the TD there is a Fast / Gigabit Ethernet and a console RJ 45 port. Of the additional features, it can be noted that TDs are able to function in 2 modes: either under the control of the controller or autonomously. In the latter case, the AP is able to perform the functions of a virtual controller for several other points connected to it. Or just be an expensive compact router. But there are limitations - “Home” (in case it works in the virtual controller mode) the AP should receive a DHCP address, otherwise Wi-Fi modules will not rise, despite the joyful indication. This is due to some idiocy of the TD architecture, which, I think, the manufacturer still deliberately introduced, because there are TDs of the RAP class (see below), which this restriction does not apply.
When you turn off the TD no information about the network, policies and so on. they do not remain, i.e. when enabled, the TD will request settings from the controller. This causes a relatively large start time TD - from 5 to 7 minutes.
I propose to admire the TD of the average, so to speak, class:


For a snack, all TDs support the creation of 8 to 16 virtual access points. Those. one TD generates several networks, each with its own BSSID, correlated with its own VLAN.
Separate type TD - RAP
Here we are close to a mess of terminology. rap is a type of connection of “ordinary” TDs, and RAP is a special class of TDs that resemble ordinary household wireless routers in terms of functionality and appearance, but which have the ability to work under the control of a controller and receive policies from it, with a large number of Ethernet ports suitable for connection, say, a network printer, and the ability to connect a USB modem. The main difference from conventional TDs is that there is no spectrum analyzer, and these TDs can save information about networks, policies, etc. They can also work as a standalone router - and for work there is no need to receive an address at all, as for ordinary TDs. But this species is devoid of the following features characteristic of conventional TD:
- The inability to work inside the LAN over GRE - connection only via VPN. This is important because There is a license for the number of connected TDs, and this license also limits the number of points connected by each method.
- Cannot work in Mesh (although, in itself, it can be a Mesh portal for regular TDs) (depends on the model)
RAP points are several species; differ in size, number of ports and some other features. Most models have an integrated TPM chip (Trusted Platform Module).
It may look like the image below:

Roughly speaking, this is such an advanced router.
This is good for the organization of wireless networks in a very very distant mutarakani, where the Internet works with poltychka, and the network still need to provide, and preferably with security policies. In general, there is a giant plus in this decision: you can set up this box and hand it to the girl manager with the words “Masha, when you arrive, you plug the cable into this hole and plug it into the network. "Everything, the rest piece of iron will make itself.
WEB interface
And finally, let's see how the web interface is implemented. The screenshots below are taken from the administrator account, but there is an opportunity to play the role of an observer - only pages will be available to monitor customers or the system, without the ability to change the controller settings. When entering the main page, we get to the page where we can learn about the number of connected clients, network performance and other useful information:

We can also receive and detailed information on the client:

And also on this tab you can find a section on network security, where the number of suppressed (rogue) networks, neighbor (interference) and other networks, including service ones, is shown. Naturally, in each network, you can see the clients connected to it, get some information about bandwidth, etc., self-diagnostics, etc .:

And finally (I think everyone already understood what interface to work with Aruba), I will give a screenshot of the analysis of the radio-frequency environment:

A little bit about the introduction
Just a couple of words. Since the solution is self-sufficient, in most cases everything goes simply enough - you need to find a free port on the switch and plug the controller into it. To decide how the TD will work - using mesh technology (in this case, it is enough for them to provide only 220 V power) or via LAN, to set up the controller. Additional servers in most cases do not need to be installed; if necessary, the controller can be used as a router for some wired network segment. But it should be borne in mind that it is possible to detect the connection of devices to this network and mark them as illegal, as a result of which they will not work (yes, it is possible to detect unauthorized connections to the wired network segment).
Additional servers and software in most cases is not necessary; installation of additional servers is needed if you need to implement functionality like full-featured RTLS (location tracking system), centralized management of network equipment of various vendors (by the way, you can combine RTLS and management system), transparent BYOD, etc.
In the case of RTLS, Aruba Networks easily integrates with Ekahau or Aeroscout.
As a conclusion
Here I tried to talk about Aruba Networks, but, unfortunately, the topic of security here is clearly not fully disclosed, although this is a key, in general, feature of the product. Therefore, I will write, as will be the time, a more “technical” post on the topic of security of Aruba Networks, and also try to uncover the remaining Aruba chips, such as BYOD, for which you don’t need to install any software on client devices, the AirWave multi-vendor control system access to VIA corporate LAN, implementation of one-time passwords, etc. - but the latter is in case of interest to the topic, probably.
It should be noted that, in contrast to the equipment of other vendors, there is already proposed functionality implemented in hardware, which requires only the acquisition of appropriate solutions.
And, if someone is interested - in Moscow there are now integrators who can build solutions based on Aruba Networks, but in order not to breed advertising - please clarify these questions through habrapost.
Thank you all for your attention!
Source: https://habr.com/ru/post/160265/
All Articles