Duqu - a malicious matryoshka
Introduction
On September 1, 2011, from Hungary, a file was sent to the VirusTotal website ~ DN1.tmp. At that time, the file was detected as malicious only by two anti-virus engines - BitDefender and AVIRA. So began the story of Duqu. Looking ahead, it must be said that the Duqu HV family was named after this file. However, this file is a completely independent spy module with keylogger functions installed, probably installed with the help of a malicious dropper downloader, and can only be viewed as a “payload” loaded by the Duqu malware during its work, but not part of the Duqu . One of the components of Duqu was sent to the Virustotal service only on September 9. Its distinguishing feature is the driver, digitally signed by C-Media. Some experts immediately began to draw analogies with another well-known sample of malware, Stuxnet, which also used signed drivers. The total number of computers infected by Duqu, detected by various antivirus companies around the world, amounts to dozens. Many companies claim that again the main goal is Iran, but judging by the geography of the distribution of infections, this cannot be stated for sure.
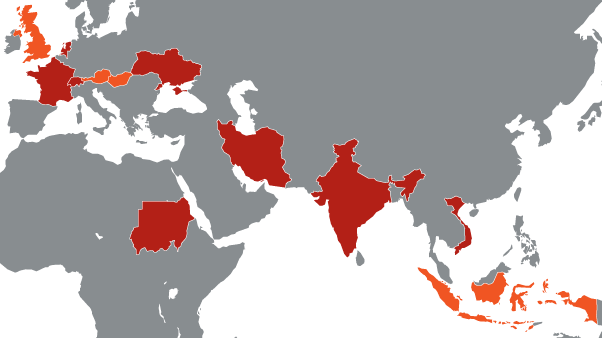
In this case, you should confidently speak only about the next company with the new-fashioned word APT (advanced persistent threat).
The procedure for introduction into the system
An investigation conducted by the specialists of the Hungarian organization CrySyS (Hungarian Laboratory of Cryptography and System Security of the Budapest University of Technology and Economics) led to the discovery of the installer (dropper) through which the system was infected. It was a Microsoft Word file format with an exploit of win32k.sys driver vulnerability (MS11-087, described by Microsoft on November 13, 2011), which is responsible for the rendering mechanism of TTF fonts. The exploit Silkcode uses a font embedded in the document called 'Dexter Regular', Showtime Inc. is listed as the font creator. As you can see, the creators of Duqu are not alien to a sense of humor: Dexter is a serial killer, the hero of a television series of the same name, filmed by Showtime. Dexter kills only (if possible) criminals, that is, transgress the law in the name of legality. Probably, in this way, the developers of Duqu are ironic that they are engaged in illegal activities with good purposes. Sending emails was carried out purposefully. Most likely, compromised (hacked) computers were used for dispatch as an intermediary to make tracking difficult.
The Word document thus contained the following components:
In case of successful triggering, the exploit shellcode performed the following operations (in kernel mode):
Due to the fact that win32k.sys is executed on behalf of the privileged user 'System', the Duqu developers have elegantly solved the problem of both unauthorized launching and elevation of rights (starting from under a user account with limited rights).
The installer, after receiving the control, decrypted in memory three data blocks in it, containing:
In the installer configuration data, a date range was set (in the form of two time stamps - the start and the end). The installer checked if the current date falls into it, if not - completed its execution. Also in the installer configuration data were the names under which the driver and the main module were saved. In this case, the main module was stored on the disk in encrypted form.
')
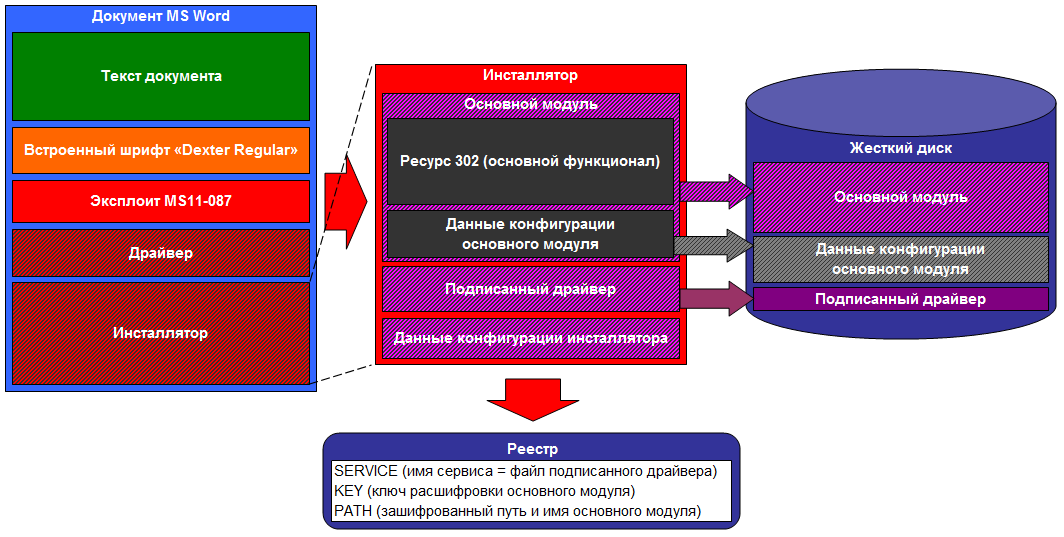
For Duqu autorun, a service was created that uses a driver file that decrypted the main module on the fly using the keys stored in the registry. The main module contains its own configuration data block. When it was first started, it was decrypted, the installation date was entered into it, after which it was again encrypted and saved by the main module. Thus, in the affected system, upon successful installation, three files were saved — the driver, the main module and its configuration data file, while the last two files were stored on disk in an encrypted form. All decryption procedures were carried out only in memory. Such a complex installation procedure was used to minimize the possibility of detection by antivirus software.
The main module
The main module (resource 302), according to Kaspersky Lab, was written using MSVC 2008 in pure C, but using an object-oriented approach. This approach is uncharacteristic when developing malicious code. As a rule, such code is written in C, in order to reduce the size and get rid of the implicit calls inherent in C ++. Here there is a certain symbiosis. Plus event-oriented architecture was used. Employees of Kaspersky Lab are inclined to the theory that the main module was written using a preprocessor add-in that allows you to write C code in an object style.
The main module is responsible for the procedure for receiving commands from operators. Duqu provides several ways to communicate: using the HTTP and HTTPS protocols, as well as using named pipes (pipe). For HTTP (S), the domain names of the command centers are specified, while the ability to work through a proxy server was provided for them to specify the user name and password. For a channel, an IP address and its name are specified. The specified data is stored in the data block of the configuration of the main module (in encrypted form).
To use named pipes, we launched our own implementation of the RPC server. She supported the following seven functions:
Named pipes could be used inside the local network to distribute updated modules and configuration data to infected Duqu-infected computers. In addition, Duqu could act as a proxy server for other infected computers (which did not have access to the Internet due to the firewall settings on the gateway). In some versions of Duqu, RPC functionality was missing.
Known "payloads"
Symantec discovered at least four types of “payload” loaded on command from the Duqu control center.
However, only one of them was resident and compiled as an executable file (exe), which was saved to disk. The remaining three were made in the form of a dll library. They loaded dynamically and ran in memory without saving to disk.
The resident "payload" was a spyware module ( infostealer ) with keylogger functions. It is from sending it to VirusTotal that the work on Duqu research began. The main spy functionality was in the resource, the first 8 kilobytes of which contained part of the photo of the galaxy NGC 6745 (for masking). It should be recalled that in April 2012 some media published information (http://www.mehrnews.com/en/newsdetail.aspx?NewsID=1297506) that Iran was exposed to some kind of malicious software "Stars", while details of the incident were not disclosed. Perhaps it was just such a sample of the “payload” Duqu that was discovered then in Iran, hence the name “Stars” (stars).
Spyware collected the following information:
Another spyware module ( infostealer ) was a variation of the already described, but compiled as a dll library, the functions of the keylogger, the creation of a list of files and the enumeration of computers included in the domain were removed from it.
The following module ( reconnaissance ) collected system information:
The last module ( lifespan extender ) implemented the function of increasing the value (stored in the data file of the configuration of the main module) of the number of days remaining until completion of the work. By default, this value was set to 30 or 36 days depending on the Duqu modification, and decreased by one every day.
Command centers
On October 20, 2011 (three days after the dissemination of information about the detection), Duqu operators conducted a procedure to destroy traces of the functioning of command centers. Command centers were located on hacked servers all over the world - in Vietnam, India, Germany, Singapore, Switzerland, Great Britain, Holland, South Korea. Interestingly, all the servers identified were running CentOS OS 5.2, 5.4 or 5.5. The operating systems were both 32-bit and 64-bit. Despite the fact that all the files related to the work of the command centers were deleted, the Kaspersky Lab specialists managed to recover part of the LOG information of the files from the slack space. The most interesting fact is that attackers on servers always replaced the default OpenSSH 4.3 package with version 5.8. This may indicate the use of an unknown vulnerability in OpenSSH 4.3 for hacking servers. Not all systems were used as command centers. Some, judging by the errors in the sshd logs when trying to redirect traffic to ports 80 and 443, were used as a proxy server to connect to the final command centers.
Dates and Modules
The Word document sent in April 2011, which was investigated at Kaspersky Lab, contained an installer download driver with a compilation date of August 31, 2007. A similar driver (size - 20608 bytes, MD5 - EEDCA45BD613E0D9A9E5C69122007F17) in the document that got into the CrySys laboratory, had a compilation date of February 21, 2008. In addition, Kaspersky Lab experts found the autorun driver rndismpc.sys (size - 19968 bytes, MD5 - 9AEC6E10C5EE9C05BED93221544C783E) with the date January 20, 2008. No component was found with a 2009 mark. Based on the time stamps of the compilation of individual parts of Duqu, its development could relate to the beginning of 2007. The earliest manifestation of it is associated with the detection of temporary files like ~ DO (probably created by one of the spyware modules), which was created on November 28, 2008 ( article "Duqu & Stuxnet: A Timeline of Interesting Events"). The most recent date for Duqu is February 23, 2012, it was contained in the installer’s download driver, discovered by Symantec employees in March 2012.
Information sources used:
a series of articles about Duqu from Kaspersky Lab;
Symantec research report “W32.Duqu The precursor to the next Stuxnet” , version 1.4, November 2011 (pdf).
On September 1, 2011, from Hungary, a file was sent to the VirusTotal website ~ DN1.tmp. At that time, the file was detected as malicious only by two anti-virus engines - BitDefender and AVIRA. So began the story of Duqu. Looking ahead, it must be said that the Duqu HV family was named after this file. However, this file is a completely independent spy module with keylogger functions installed, probably installed with the help of a malicious dropper downloader, and can only be viewed as a “payload” loaded by the Duqu malware during its work, but not part of the Duqu . One of the components of Duqu was sent to the Virustotal service only on September 9. Its distinguishing feature is the driver, digitally signed by C-Media. Some experts immediately began to draw analogies with another well-known sample of malware, Stuxnet, which also used signed drivers. The total number of computers infected by Duqu, detected by various antivirus companies around the world, amounts to dozens. Many companies claim that again the main goal is Iran, but judging by the geography of the distribution of infections, this cannot be stated for sure.

In this case, you should confidently speak only about the next company with the new-fashioned word APT (advanced persistent threat).
The procedure for introduction into the system
An investigation conducted by the specialists of the Hungarian organization CrySyS (Hungarian Laboratory of Cryptography and System Security of the Budapest University of Technology and Economics) led to the discovery of the installer (dropper) through which the system was infected. It was a Microsoft Word file format with an exploit of win32k.sys driver vulnerability (MS11-087, described by Microsoft on November 13, 2011), which is responsible for the rendering mechanism of TTF fonts. The exploit Silkcode uses a font embedded in the document called 'Dexter Regular', Showtime Inc. is listed as the font creator. As you can see, the creators of Duqu are not alien to a sense of humor: Dexter is a serial killer, the hero of a television series of the same name, filmed by Showtime. Dexter kills only (if possible) criminals, that is, transgress the law in the name of legality. Probably, in this way, the developers of Duqu are ironic that they are engaged in illegal activities with good purposes. Sending emails was carried out purposefully. Most likely, compromised (hacked) computers were used for dispatch as an intermediary to make tracking difficult.
The Word document thus contained the following components:
- text content;
- embedded font;
- explod shellcode;
- driver;
- installer (DLL).
In case of successful triggering, the exploit shellcode performed the following operations (in kernel mode):
- a check was made for reinfection; for this, the registry at 'HKEY_LOCAL_MACHINE \ SOFTWARE \ Microsoft \ Windows \ CurrentVersion \ Internet Settings \ Zones \ 4 \' checked if the key 'CF1D' was checked, if this was true, the shell code was completed;
- two files were decrypted - the driver (sys) and the installer (dll);
- the driver was injected into the services.exe process and executed the installer;
- at the end, the shellcode wiped itself with zeros in memory.
Due to the fact that win32k.sys is executed on behalf of the privileged user 'System', the Duqu developers have elegantly solved the problem of both unauthorized launching and elevation of rights (starting from under a user account with limited rights).
The installer, after receiving the control, decrypted in memory three data blocks in it, containing:
- signed driver (sys);
- main module (dll);
- installer configuration data (pnf).
In the installer configuration data, a date range was set (in the form of two time stamps - the start and the end). The installer checked if the current date falls into it, if not - completed its execution. Also in the installer configuration data were the names under which the driver and the main module were saved. In this case, the main module was stored on the disk in encrypted form.
')

For Duqu autorun, a service was created that uses a driver file that decrypted the main module on the fly using the keys stored in the registry. The main module contains its own configuration data block. When it was first started, it was decrypted, the installation date was entered into it, after which it was again encrypted and saved by the main module. Thus, in the affected system, upon successful installation, three files were saved — the driver, the main module and its configuration data file, while the last two files were stored on disk in an encrypted form. All decryption procedures were carried out only in memory. Such a complex installation procedure was used to minimize the possibility of detection by antivirus software.
The main module
The main module (resource 302), according to Kaspersky Lab, was written using MSVC 2008 in pure C, but using an object-oriented approach. This approach is uncharacteristic when developing malicious code. As a rule, such code is written in C, in order to reduce the size and get rid of the implicit calls inherent in C ++. Here there is a certain symbiosis. Plus event-oriented architecture was used. Employees of Kaspersky Lab are inclined to the theory that the main module was written using a preprocessor add-in that allows you to write C code in an object style.
The main module is responsible for the procedure for receiving commands from operators. Duqu provides several ways to communicate: using the HTTP and HTTPS protocols, as well as using named pipes (pipe). For HTTP (S), the domain names of the command centers are specified, while the ability to work through a proxy server was provided for them to specify the user name and password. For a channel, an IP address and its name are specified. The specified data is stored in the data block of the configuration of the main module (in encrypted form).
To use named pipes, we launched our own implementation of the RPC server. She supported the following seven functions:
- return the installed version;
- Inject dll into the specified process and call the specified function;
- load dll;
- start the process by calling CreateProcess ();
- read the contents of the specified file;
- write data to the specified file;
- delete the specified file.
Named pipes could be used inside the local network to distribute updated modules and configuration data to infected Duqu-infected computers. In addition, Duqu could act as a proxy server for other infected computers (which did not have access to the Internet due to the firewall settings on the gateway). In some versions of Duqu, RPC functionality was missing.
Known "payloads"
Symantec discovered at least four types of “payload” loaded on command from the Duqu control center.
However, only one of them was resident and compiled as an executable file (exe), which was saved to disk. The remaining three were made in the form of a dll library. They loaded dynamically and ran in memory without saving to disk.
The resident "payload" was a spyware module ( infostealer ) with keylogger functions. It is from sending it to VirusTotal that the work on Duqu research began. The main spy functionality was in the resource, the first 8 kilobytes of which contained part of the photo of the galaxy NGC 6745 (for masking). It should be recalled that in April 2012 some media published information (http://www.mehrnews.com/en/newsdetail.aspx?NewsID=1297506) that Iran was exposed to some kind of malicious software "Stars", while details of the incident were not disclosed. Perhaps it was just such a sample of the “payload” Duqu that was discovered then in Iran, hence the name “Stars” (stars).
Spyware collected the following information:
- list of running processes, information about the current user and domain;
- list of logical drives, including network drives;
- screen shots;
- network interface addresses, routing tables;
- Log file keystrokes keyboard;
- the names of open application windows;
- list of available network resources (sharing resources);
- full list of files on all drives, including removable ones;
- list of computers in the "network environment".
Another spyware module ( infostealer ) was a variation of the already described, but compiled as a dll library, the functions of the keylogger, the creation of a list of files and the enumeration of computers included in the domain were removed from it.
The following module ( reconnaissance ) collected system information:
- whether the computer is part of a domain;
- paths to Windows system directories;
- operating system version;
- current user name;
- list of network adapters;
- system and local time, as well as the time zone.
The last module ( lifespan extender ) implemented the function of increasing the value (stored in the data file of the configuration of the main module) of the number of days remaining until completion of the work. By default, this value was set to 30 or 36 days depending on the Duqu modification, and decreased by one every day.
Command centers
On October 20, 2011 (three days after the dissemination of information about the detection), Duqu operators conducted a procedure to destroy traces of the functioning of command centers. Command centers were located on hacked servers all over the world - in Vietnam, India, Germany, Singapore, Switzerland, Great Britain, Holland, South Korea. Interestingly, all the servers identified were running CentOS OS 5.2, 5.4 or 5.5. The operating systems were both 32-bit and 64-bit. Despite the fact that all the files related to the work of the command centers were deleted, the Kaspersky Lab specialists managed to recover part of the LOG information of the files from the slack space. The most interesting fact is that attackers on servers always replaced the default OpenSSH 4.3 package with version 5.8. This may indicate the use of an unknown vulnerability in OpenSSH 4.3 for hacking servers. Not all systems were used as command centers. Some, judging by the errors in the sshd logs when trying to redirect traffic to ports 80 and 443, were used as a proxy server to connect to the final command centers.
Dates and Modules
The Word document sent in April 2011, which was investigated at Kaspersky Lab, contained an installer download driver with a compilation date of August 31, 2007. A similar driver (size - 20608 bytes, MD5 - EEDCA45BD613E0D9A9E5C69122007F17) in the document that got into the CrySys laboratory, had a compilation date of February 21, 2008. In addition, Kaspersky Lab experts found the autorun driver rndismpc.sys (size - 19968 bytes, MD5 - 9AEC6E10C5EE9C05BED93221544C783E) with the date January 20, 2008. No component was found with a 2009 mark. Based on the time stamps of the compilation of individual parts of Duqu, its development could relate to the beginning of 2007. The earliest manifestation of it is associated with the detection of temporary files like ~ DO (probably created by one of the spyware modules), which was created on November 28, 2008 ( article "Duqu & Stuxnet: A Timeline of Interesting Events"). The most recent date for Duqu is February 23, 2012, it was contained in the installer’s download driver, discovered by Symantec employees in March 2012.
Information sources used:
a series of articles about Duqu from Kaspersky Lab;
Symantec research report “W32.Duqu The precursor to the next Stuxnet” , version 1.4, November 2011 (pdf).
Source: https://habr.com/ru/post/159669/
All Articles