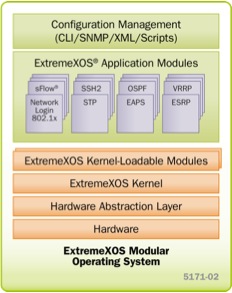
How does the inside look like and what are the advantages of modular OS network devices, using the example of Extreme Networks XOS
In recent years, active network equipment manufacturers have been promoting their products that run on modular operating systems, while the CLI, if different, is insignificant.
The main differences are usually hidden from administrators and users for quite logical reasons (protection of technology, copyright, as well as the possible irreversible consequences that may result from inquiring minds). About how such logical structures are implemented almost slightly lower.
')

As a rule, modular OSs work on top of:
• MontaVista Linux (Cisco NX-OS, Extreme XOS)
• FreeBSD (JunOS)
• OpenBSD (Dell-Force10 OS)
• and others ...
But working directly with the file system itself is blocked and requires additional privileges.
This mode of operation in Extreme XOS is called “debug-mode”.
To enter the “debug-mode” you must manually enter the command completely, since the prompt does not work in this case. After that, the console will issue an invitation to enter a password, which you need to get from TAC engineers (if this is required by the service case and there is a valid service contract). The password will be valid for 59 minutes, and is generated based on the issued by the “challenge” system.

After logging in to “debug-mode”, the user is prompted using a <TAB> pair of additional hidden branches of the settings commands.
And if the branch for the most part is available for viewing and in normal operation,
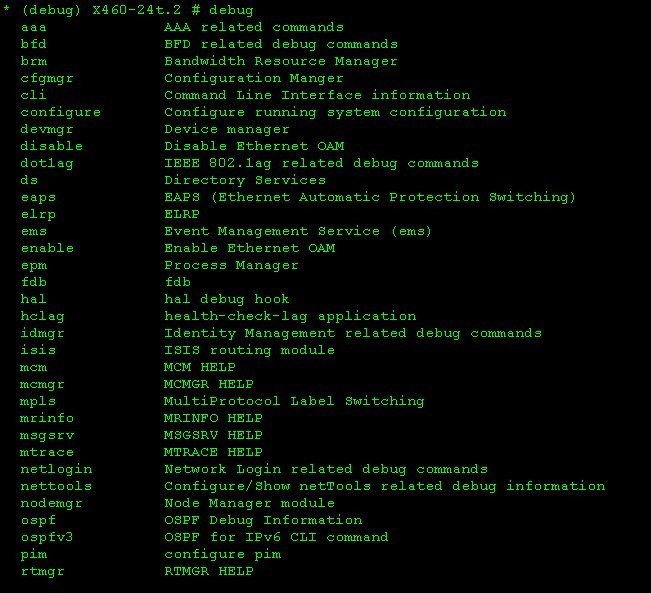
then here's a branch (for some reason, the cartoon is immediately remembered :) is completely hidden and intended for debugging by XOS developers.
It is also worth noting that if you know the hidden commands of a branch, then you can apply them completely in the CLI, but they will not work with the commands.
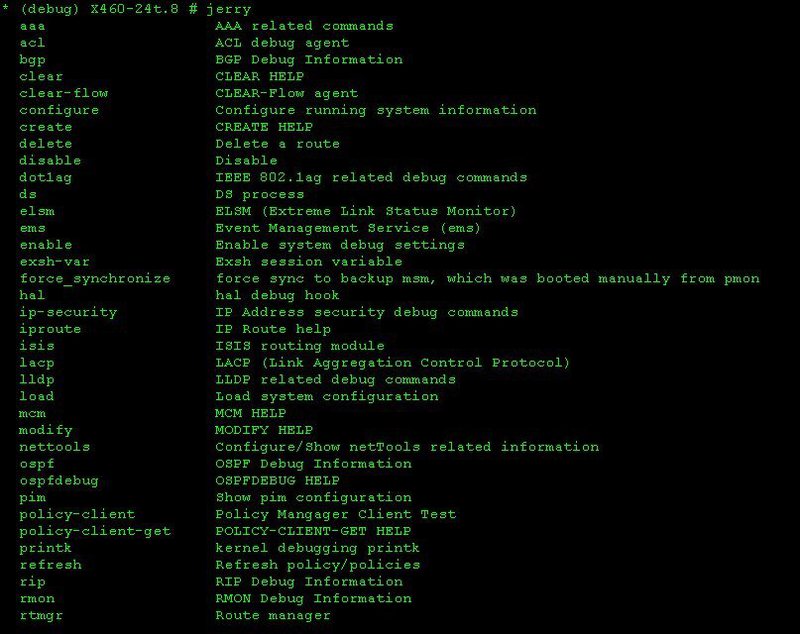
But the most important thing is that only from this mode it is possible to get into the shell.
A set of commands built BusyBox presented in the picture
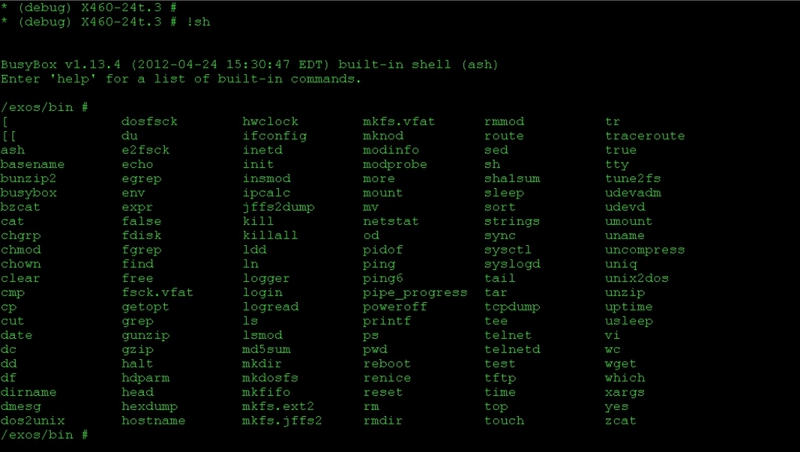
And the root directory structure is quite familiar to all Linux systems.
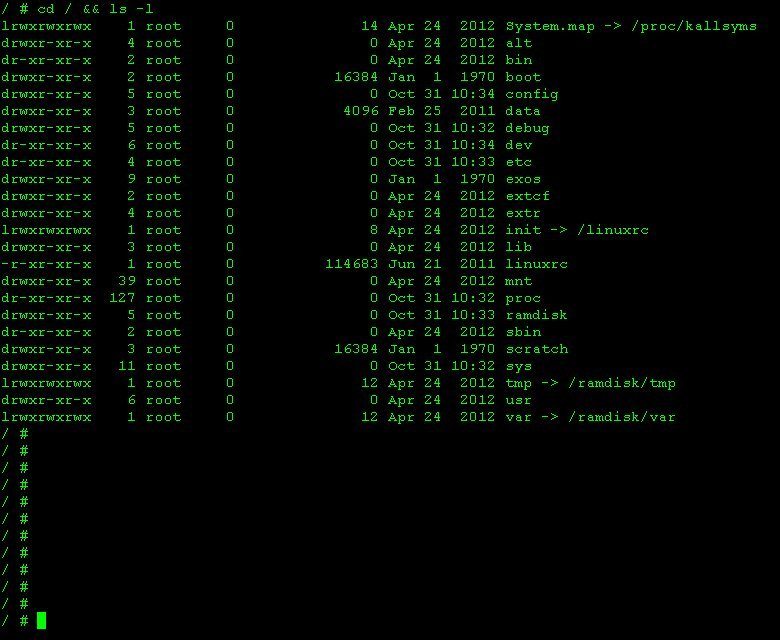
Everything is mounted on the CF pre-installed on the switch.
When installing XOS from BootRom, you can see how the formatting of these eight logical partitions goes. The ninth position is an external USB flash drive connected to the port on the front panel.

Below is the answer to the question - “What is the difference when installing the OS in the“ primary ”and“ secondary ”sections?”, And why one XOS file is suitable for installation on all switches of one line independently
from the model and functionality.
Prior to the release of the Summit X460 switch family, Broadcom CPUs with an MIPS 64 architecture were installed on the switches; now they are more powerful processors from RMI with a similar architecture. That is why the operating system file includes two cores, each of which is compiled under its own processor. The kernel version 2.6.98.6 is selected.
Alphadiags files help diagnose hardware, ranging from the performance of ports, internal buses and ending with LEDs. Diagnostics can be simple and extended and run from the CLI with the command <run diagnostic {normal | extended}> (the launch causes a traffic interruption on the ports !!!).
It is possible that the name alphadiags is somehow related to the fact that all Extreme Networks equipment is assembled on the conveyors of the Alpha plants.

The processor that is installed in the Summit X460-24t switch

Below, in fact, those processes and kernel modules due to which the operating system is called modular.
Each process is allocated its own section of memory, which allows for the rest of one process to work, as well as to make a manual restart of some non-critical ones for the whole
module systems.
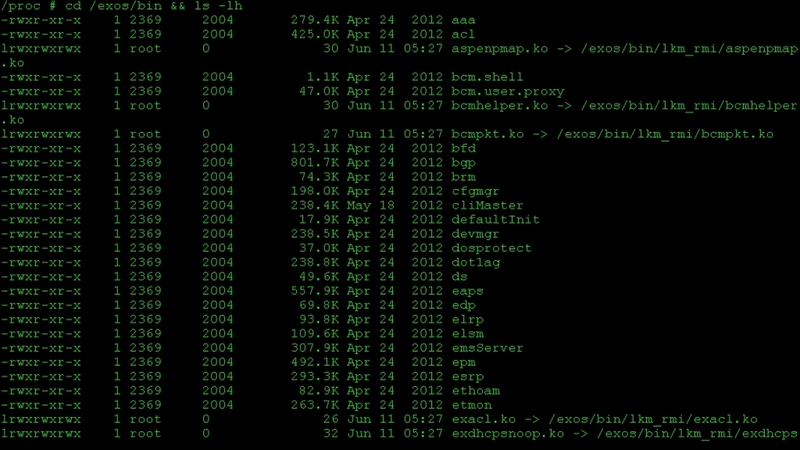
Authorship of some kernel modules. Since Extreme Networks uses Broadcom's ASICs in their hardware, they require kernel modules from the original source to work with them.

Each switch has an identifier of its platform which is stored in the EEPROM, so after installation a check is made for compliance with the platform and license level. Information about what functionality you need to run is contained in the corresponding files. The convenience of this approach is that after entering the license key, a command is simply given to launch the corresponding modules, without the need to completely reinstall the OS image.
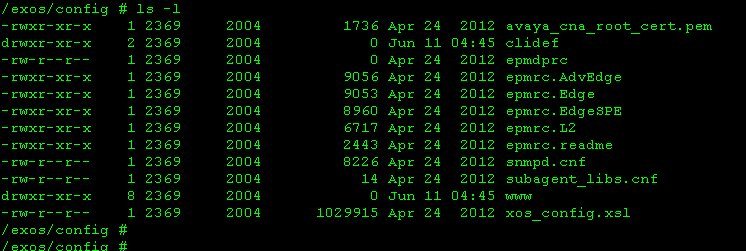
The last file is a script that loads the default configuration.
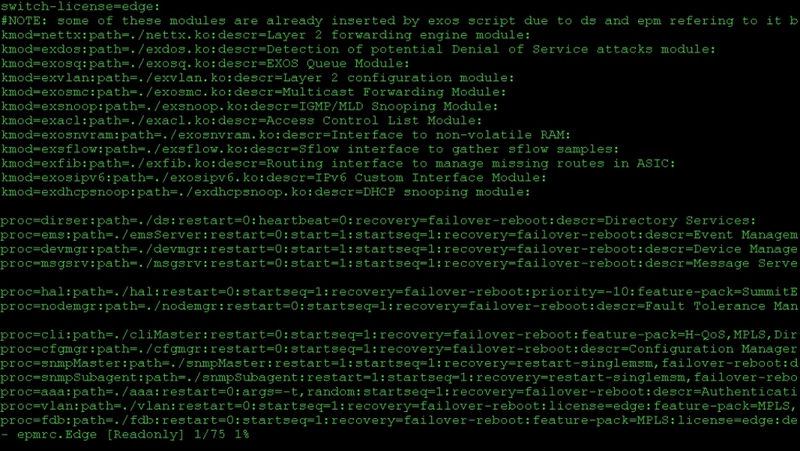
Using the built-in editor "vi" you can see the structure of such files. Everything is quite simple there: a description of the process / module, the launch path, the ability to manually restart, the ability to self-recover the process after a failure, as well as some other parameters.
Conclusion:
1. Modular operating systems are more intelligent than their predecessors - monolithic operating systems, with all the ensuing marketing implications. However, their installation requires appropriate hardware support, which in turn increases the final cost of the products. This is especially noticeable on access switches, which in this case cannot compete in price with analogs on monolithic operating systems, and some manufacturers do not even make offers in this segment.
2. Difficulty if you want to install an image of the system on a virtual machine: firstly, the installation scripts built into the OS are not available to the user, secondly, not all manufacturers use an x86 processor in their solutions. And therefore, this issue with emulators is solved only by manufacturers who make the necessary corrections and compile the source code for x86.
In general, the situation is somewhat (according to the personal opinion of the author) resembles the mobile phone market, where with the advent of modular OSs like IOS and Android, there was a de facto rejection of old platforms,
which now occupy a niche in the lower price segment. The market for network devices will certainly not be so dynamic, but the trends and benefits from such a transition are obvious.
So let's follow together the announcements from Extreme Networks, Cisco Systems, Juniper Networks and other market leaders who are actively developing and using the functionality we reviewed.
Extreme Networks Authorized Training Courses
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
The main differences are usually hidden from administrators and users for quite logical reasons (protection of technology, copyright, as well as the possible irreversible consequences that may result from inquiring minds). About how such logical structures are implemented almost slightly lower.

')

As a rule, modular OSs work on top of:
• MontaVista Linux (Cisco NX-OS, Extreme XOS)
• FreeBSD (JunOS)
• OpenBSD (Dell-Force10 OS)
• and others ...
But working directly with the file system itself is blocked and requires additional privileges.
This mode of operation in Extreme XOS is called “debug-mode”.
To enter the “debug-mode” you must manually enter the command completely, since the prompt does not work in this case. After that, the console will issue an invitation to enter a password, which you need to get from TAC engineers (if this is required by the service case and there is a valid service contract). The password will be valid for 59 minutes, and is generated based on the issued by the “challenge” system.

After logging in to “debug-mode”, the user is prompted using a <TAB> pair of additional hidden branches of the settings commands.
And if the branch for the most part is available for viewing and in normal operation,

then here's a branch (for some reason, the cartoon is immediately remembered :) is completely hidden and intended for debugging by XOS developers.
It is also worth noting that if you know the hidden commands of a branch, then you can apply them completely in the CLI, but they will not work with the commands.

But the most important thing is that only from this mode it is possible to get into the shell.
A set of commands built BusyBox presented in the picture

And the root directory structure is quite familiar to all Linux systems.

Everything is mounted on the CF pre-installed on the switch.
When installing XOS from BootRom, you can see how the formatting of these eight logical partitions goes. The ninth position is an external USB flash drive connected to the port on the front panel.

Below is the answer to the question - “What is the difference when installing the OS in the“ primary ”and“ secondary ”sections?”, And why one XOS file is suitable for installation on all switches of one line independently
from the model and functionality.
Prior to the release of the Summit X460 switch family, Broadcom CPUs with an MIPS 64 architecture were installed on the switches; now they are more powerful processors from RMI with a similar architecture. That is why the operating system file includes two cores, each of which is compiled under its own processor. The kernel version 2.6.98.6 is selected.
Alphadiags files help diagnose hardware, ranging from the performance of ports, internal buses and ending with LEDs. Diagnostics can be simple and extended and run from the CLI with the command <run diagnostic {normal | extended}> (the launch causes a traffic interruption on the ports !!!).
It is possible that the name alphadiags is somehow related to the fact that all Extreme Networks equipment is assembled on the conveyors of the Alpha plants.

The processor that is installed in the Summit X460-24t switch

Below, in fact, those processes and kernel modules due to which the operating system is called modular.
Each process is allocated its own section of memory, which allows for the rest of one process to work, as well as to make a manual restart of some non-critical ones for the whole
module systems.

Authorship of some kernel modules. Since Extreme Networks uses Broadcom's ASICs in their hardware, they require kernel modules from the original source to work with them.

Each switch has an identifier of its platform which is stored in the EEPROM, so after installation a check is made for compliance with the platform and license level. Information about what functionality you need to run is contained in the corresponding files. The convenience of this approach is that after entering the license key, a command is simply given to launch the corresponding modules, without the need to completely reinstall the OS image.
The last file is a script that loads the default configuration.

Using the built-in editor "vi" you can see the structure of such files. Everything is quite simple there: a description of the process / module, the launch path, the ability to manually restart, the ability to self-recover the process after a failure, as well as some other parameters.

Conclusion:
1. Modular operating systems are more intelligent than their predecessors - monolithic operating systems, with all the ensuing marketing implications. However, their installation requires appropriate hardware support, which in turn increases the final cost of the products. This is especially noticeable on access switches, which in this case cannot compete in price with analogs on monolithic operating systems, and some manufacturers do not even make offers in this segment.
2. Difficulty if you want to install an image of the system on a virtual machine: firstly, the installation scripts built into the OS are not available to the user, secondly, not all manufacturers use an x86 processor in their solutions. And therefore, this issue with emulators is solved only by manufacturers who make the necessary corrections and compile the source code for x86.
In general, the situation is somewhat (according to the personal opinion of the author) resembles the mobile phone market, where with the advent of modular OSs like IOS and Android, there was a de facto rejection of old platforms,
which now occupy a niche in the lower price segment. The market for network devices will certainly not be so dynamic, but the trends and benefits from such a transition are obvious.
So let's follow together the announcements from Extreme Networks, Cisco Systems, Juniper Networks and other market leaders who are actively developing and using the functionality we reviewed.
Extreme Networks Authorized Training Courses
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/159485/
All Articles