Hyper-V Extensible Switch in Windows Server 2012
Hyper-V Extensible Switch, a key component of Hyper-V in Windows Server 2012 , is an extensible, managed second-level switch. Extensibility means the ability of developers to create modules embedded in Hyper-V and modifying / expanding the regular functionality of analysis, filtering and forwarding packages. Manageability implies the presence of a whole set of settings available to the administrator through PowerShell or the Hyper-V Manager console, providing the required level of isolation, security, and monitoring of running virtual machines (VM). In one of the previous posts I described the implementation of the Private VLAN technology (PVLAN) in the Hyper-V Extensible Switch. Today we look at a number of additional features.
In terms of terminology, the concept of Hyper-V Switch (or Virtual Switch) has replaced the concept of a virtual network (Virtual Network) in Windows Server 2008/2008 R2. If earlier, to ensure the interaction of the VM with each other or with the outside world, you created a virtual network of one of three types - External, Internal, Private - then you are creating a Virtual Switch, which can be of the same three types and has all the features described below . Moreover, these capabilities are defined for a specific port of a virtual switch (see fig.), And the port, in turn, is identified by the name of the virtual machine that is connected to this port, more precisely, by the name of the virtual network adapter, since there may be several adapters in the VM.

')
Next, I considered the Hyper-V Extensible Switch settings into three categories: security and isolation, monitoring, and fault tolerance.
In the Hyper-V Manager console, a new subsection of Advanced Features has appeared in the properties of the virtual network adapter. The first three settings in this window are directly related to security and isolation.

MAC address spoofing
By default, Hyper-V does not allow MAC address spoofing. In other words, if the VM tries to replace the sender's MAC address in the outgoing packets, that is, its MAC address associated with the virtual network adapter of this machine with another MAC address, Hyper-V blocks such packets. Installing the top checkbox, respectively, allows spoofing. As always, everything that can be done in the Hyper-V Manager console and even more can be done in PowerShell. For the VM named SRV4 shown in the figure, enabling MAC spoofing is implemented by the following command:
DHCP security (DHCP Guard)
This setting must be used to block an unauthorized DHCP server running inside the VM. Technically, when installing this checkbox, Hyper-V blocks DHCP packets to acknowledge from this VM and prevents DHCP clients from getting IP settings from this VM.
Router Guard
By analogy with DHCP Guard, the installation of this checkbox blocks redirection and router advertisements (redirection and router advertisement) from this VM. Thus, the VM will not be able to affect the routing tables of other computers on the network.
Port Access Control List (Port ACL)
For each Hyper-V Extensible Switch port, you can configure one or more Access Control Lists (ACLs) to specify additional security rules and VM isolation level. All ACL settings are set only via PowerShell; in the Hyper-V Manager console, list management is not available. You can view the current status of the lists with the command:
Adding and deleting a list is done by the Add-VMNetworkAdapterAcl and Remove-VMNetworkAdapterAcl commands, respectively. The syntax of both commands is the same. For each ACL, you must specify:
By default, no ACLs are set, and thus all traffic is allowed. The example below prohibits for the VM with the name SRV4 any traffic from / to the IP address 192.168.1.143:
With regard to IP addresses, you can specify not only a specific address, but also a subnet:
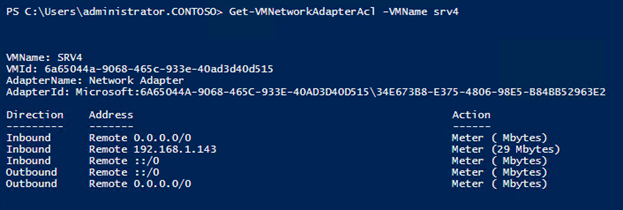
If ACLs are set for both the subnet and a specific address from that subnet, then the ACL for the address has higher priority, that is, the “more specific” rule has more power. For example, the following shows the result of the Get-VMNetworkAdapterAcl command :

As you can see, the ban on the subnet 192.168.1.0/24 is set, and traffic is allowed for the address 192.168.1.143. As a result, IP traffic is possible only on one 143rd address from the entire subnet.
The Meter allows you to measure the amount of incoming and / or outgoing traffic for a specified IP or MAC address since the creation of the corresponding ACL, for example, the following command enables the measurement of incoming traffic from 192.168.1.143:
The result can be seen using the same Get-VMNetworkAdapterAcl :
Traffic monitoring can be implemented through the port mirroring mechanism. To configure mirroring, you need to specify the source of information; in the Hyper-V Manager, this is done here:

And then in the settings of the necessary VM, which will monitor the traffic, select the value Destination in the same field. In PowerShell, this is done with the parameters of the Set-VMNetworkAdapter command :
After that, all traffic, incoming and outgoing, to the VM port of the SRV3 is copied and redirected to the VM port of the SRV4. You only need to install the necessary traffic analysis software in SRV4. An important condition is that both VMs must be connected to the same virtual switch.
The last option in the advanced properties of the virtual network adapter relates to fault tolerance, namely to the network adapter grouping technology (NIC Teaming).
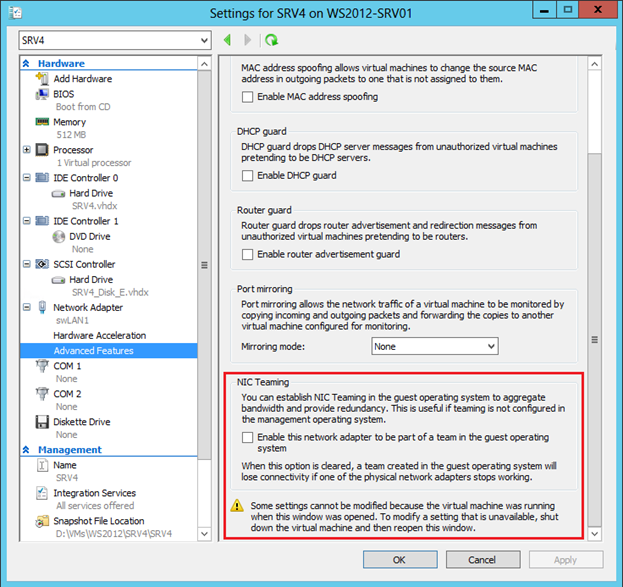
NIC Teaming is a full-featured Windows Server 2012 feature that deserves, generally speaking, a separate post. This feature allows you to combine several physical network adapters into a group and, on the one hand, to ensure the fault tolerance of network traffic when any network card fails, on the other hand, to aggregate the bandwidth of the adapters included in the group.
For various reasons, you may not want to enable timing on the host machine. However, if the host has more than one physical network adapter, you can use NIC Teaming inside the guest OS. Imagine that the host has two network cards. If in some VM there are two virtual network adapters, these adapters are connected via two virtual external switches to two physical cards, respectively, and Windows Server 2012 is installed inside the VM, then you can configure NIC Teaming inside the guest OS. And such a VM can take advantage of timing, and fault tolerance, and increased throughput. But in order for Hyper-V to understand that when a single physical adapter fails, the traffic for this VM needs to be transferred to another physical adapter, you just need to install the mentioned checkbox in the properties of each virtual NIC included in the timing. In PowerShell, a similar setting is made as follows:
All the settings discussed above can be set for running VMs and take effect immediately. Of course, this is not all the functionality of the Hyper-V Extensible Switch. After reviewing the list of cmdlets available in Hyper-V , you can find many more interesting things.
In conclusion, I would like to note that on November 26, a free IT Camp series on Windows Server 2012 and System Center 2012 will be held in Moscow. My colleagues, Georgy Hajiyev and Simon Perriman (Redmond) will conduct the seminar. You can look at the products alive and ask any questions.
Hope the material was helpful.
Thank!
In terms of terminology, the concept of Hyper-V Switch (or Virtual Switch) has replaced the concept of a virtual network (Virtual Network) in Windows Server 2008/2008 R2. If earlier, to ensure the interaction of the VM with each other or with the outside world, you created a virtual network of one of three types - External, Internal, Private - then you are creating a Virtual Switch, which can be of the same three types and has all the features described below . Moreover, these capabilities are defined for a specific port of a virtual switch (see fig.), And the port, in turn, is identified by the name of the virtual machine that is connected to this port, more precisely, by the name of the virtual network adapter, since there may be several adapters in the VM.

')
Next, I considered the Hyper-V Extensible Switch settings into three categories: security and isolation, monitoring, and fault tolerance.
Safety and isolation
In the Hyper-V Manager console, a new subsection of Advanced Features has appeared in the properties of the virtual network adapter. The first three settings in this window are directly related to security and isolation.

MAC address spoofing
By default, Hyper-V does not allow MAC address spoofing. In other words, if the VM tries to replace the sender's MAC address in the outgoing packets, that is, its MAC address associated with the virtual network adapter of this machine with another MAC address, Hyper-V blocks such packets. Installing the top checkbox, respectively, allows spoofing. As always, everything that can be done in the Hyper-V Manager console and even more can be done in PowerShell. For the VM named SRV4 shown in the figure, enabling MAC spoofing is implemented by the following command:
Set-VMNetworkAdapter -VMName srv4 -MacAddressSpoofing On DHCP security (DHCP Guard)
This setting must be used to block an unauthorized DHCP server running inside the VM. Technically, when installing this checkbox, Hyper-V blocks DHCP packets to acknowledge from this VM and prevents DHCP clients from getting IP settings from this VM.
Set-VMNetworkAdapter -VMName srv4 -DhcpGuard On Router Guard
By analogy with DHCP Guard, the installation of this checkbox blocks redirection and router advertisements (redirection and router advertisement) from this VM. Thus, the VM will not be able to affect the routing tables of other computers on the network.
Set-VMNetworkAdapter -VMName srv4 -RouterGuard On Port Access Control List (Port ACL)
For each Hyper-V Extensible Switch port, you can configure one or more Access Control Lists (ACLs) to specify additional security rules and VM isolation level. All ACL settings are set only via PowerShell; in the Hyper-V Manager console, list management is not available. You can view the current status of the lists with the command:
Get-VMNetworkAdapterAcl -VMName srv4 Adding and deleting a list is done by the Add-VMNetworkAdapterAcl and Remove-VMNetworkAdapterAcl commands, respectively. The syntax of both commands is the same. For each ACL, you must specify:
- Local or remote IP address or MAC address
- Direction: inbound traffic, outbound traffic, both directions (Inbound, Outbound, Both)
- Actually action: allow, prohibit, measure (Allow, Deny, Meter)
By default, no ACLs are set, and thus all traffic is allowed. The example below prohibits for the VM with the name SRV4 any traffic from / to the IP address 192.168.1.143:
Add-VMNetworkAdapterAcl -VMName srv4 -RemoteIPAddress 192.168.1.143 -Direction Both -Action Deny With regard to IP addresses, you can specify not only a specific address, but also a subnet:
Add-VMNetworkAdapterAcl -VMName srv4 -RemoteIPAddress 192.168.1.0/24 -Direction Both -Action Deny If ACLs are set for both the subnet and a specific address from that subnet, then the ACL for the address has higher priority, that is, the “more specific” rule has more power. For example, the following shows the result of the Get-VMNetworkAdapterAcl command :

As you can see, the ban on the subnet 192.168.1.0/24 is set, and traffic is allowed for the address 192.168.1.143. As a result, IP traffic is possible only on one 143rd address from the entire subnet.
The Meter allows you to measure the amount of incoming and / or outgoing traffic for a specified IP or MAC address since the creation of the corresponding ACL, for example, the following command enables the measurement of incoming traffic from 192.168.1.143:
Add-VMNetworkAdapterAcl -VMName srv4 -RemoteIPAddress 192.168.1.143 -Direction Inbound -Action Meter The result can be seen using the same Get-VMNetworkAdapterAcl :

Monitoring
Traffic monitoring can be implemented through the port mirroring mechanism. To configure mirroring, you need to specify the source of information; in the Hyper-V Manager, this is done here:

And then in the settings of the necessary VM, which will monitor the traffic, select the value Destination in the same field. In PowerShell, this is done with the parameters of the Set-VMNetworkAdapter command :
Set-VMNetworkAdapter -VMName srv4 -PortMirroring Destination After that, all traffic, incoming and outgoing, to the VM port of the SRV3 is copied and redirected to the VM port of the SRV4. You only need to install the necessary traffic analysis software in SRV4. An important condition is that both VMs must be connected to the same virtual switch.
fault tolerance
The last option in the advanced properties of the virtual network adapter relates to fault tolerance, namely to the network adapter grouping technology (NIC Teaming).

NIC Teaming is a full-featured Windows Server 2012 feature that deserves, generally speaking, a separate post. This feature allows you to combine several physical network adapters into a group and, on the one hand, to ensure the fault tolerance of network traffic when any network card fails, on the other hand, to aggregate the bandwidth of the adapters included in the group.
For various reasons, you may not want to enable timing on the host machine. However, if the host has more than one physical network adapter, you can use NIC Teaming inside the guest OS. Imagine that the host has two network cards. If in some VM there are two virtual network adapters, these adapters are connected via two virtual external switches to two physical cards, respectively, and Windows Server 2012 is installed inside the VM, then you can configure NIC Teaming inside the guest OS. And such a VM can take advantage of timing, and fault tolerance, and increased throughput. But in order for Hyper-V to understand that when a single physical adapter fails, the traffic for this VM needs to be transferred to another physical adapter, you just need to install the mentioned checkbox in the properties of each virtual NIC included in the timing. In PowerShell, a similar setting is made as follows:
Set-VMNetworkAdapter -VMName srv4 -AllowTeaming On All the settings discussed above can be set for running VMs and take effect immediately. Of course, this is not all the functionality of the Hyper-V Extensible Switch. After reviewing the list of cmdlets available in Hyper-V , you can find many more interesting things.
In conclusion, I would like to note that on November 26, a free IT Camp series on Windows Server 2012 and System Center 2012 will be held in Moscow. My colleagues, Georgy Hajiyev and Simon Perriman (Redmond) will conduct the seminar. You can look at the products alive and ask any questions.
Hope the material was helpful.
Thank!
Source: https://habr.com/ru/post/159391/
All Articles