Vulnerability in skype, allowing to hijack any account

About three months ago I wrote about this critical vulnerability in skype support, but it has not yet been fixed ( already fixed ).
I’ll say right away that I
')
To implement the attack, you only need to know the
Proof-of-Concept (copyright forum.xeksec.com/f13/t68922/#post98725 )
1. We register a new Skype account on the victim's soap (there will be written on this type of soap someone already registered). Do not pay attention - fill out further.
2. Login to Skype client
3. Delete all cookies, go to login.skype.com/account/password-reset-request we drive in the soap of the victim.
4. Skype notification comes
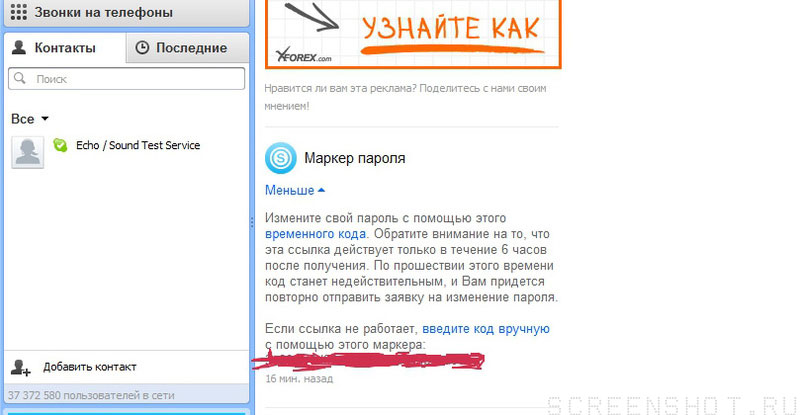
6. Click on the link and see the soap of the victim and the lists of logins registered on this soap. Your login is also visible.
7. Choose the victim's login and change the password
8. PROFIT
At the mail, the victims of the letter appear approximately in this sequence (partners and acquaintances sent screenshots of their mailboxes after hacking):
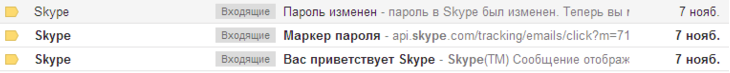
And other examples:
http://screenshot.ru/html/11.14.12_01:53:00_d0de803b.html
http://screenshot.ru/html/11.14.12_01:52:44_ecfe3230.html
http://screenshot.ru/html/11.13.12_23:00:43_210be0fe.html
http://screenshot.ru/html/11.13.12_23:06:50_48247500.html
http://screenshot.ru/html/11.13.12_23:10:36_64dafe3f.html
If such letters came to you - a reason to be wary!
The only way to protect yourself at the moment is to register a new, unknown e-mail address and change the main e-mail account to a new one via Skype .
Attention! It is impossible to change the main e-mail through skype itself! Only through the site!
Over the last week, 10 people from my contact list were hacked using this vulnerability.
I want to warn everyone to protect themselves as quickly as possible, since so far Microsoft has not taken any action, take care of your own security.
UPD
There was a way (PoC) how to use the vulnerability:
http://forum.xeksec.com/f13/t68922/#post98725
UPD2
Official comment from a Skype representative:
We have received Skype security vulnerability reports. For the security of our users, we have temporarily disabled the password reset function, and we continue to investigate this issue further. We apologize for the inconvenience, the safety of our users is our top priority.
Source: https://habr.com/ru/post/158545/
All Articles