Stealthphone Software - cryptographic information protection in mobile phones
Each of us uses a mobile phone or tablet, which, having ceased to be elements of luxury, have become indispensable tools in everyday life and production activities. Currently, there are about 6 billion mobile devices in the world, while only 1.5 billion are computers.
The use of mobile phones and tablets involves the transfer of various kinds of information in voice, text and graphic form. This may be data containing personal and even intimate details. But in modern conditions when using a mobile phone or tablet, there is no clear distinction between the scope of their use, which, in turn, leads to the accumulation in the device’s memory not only private information, but also information used in the work. One of the consequences of this in 60% of cases, according to the Ponemon Institute , is the removal of important corporate information by hackers when a mobile device is lost by a negligent employee, as a result of which the employer company loses its competitive advantage.
We live in the information space, the boundaries of which are endless and are not legally restricted by anyone. The developing situation is taken into account by specialists all over the world when determining the approach to solving information security (cyber security) issues.
')
It is not for nothing that US President Barack Obama, at one of his speeches in August 2012, made a statement that “cyber threat is one of the most serious economic and national security problems,” he determined that “America’s economic prosperity in the 21st century will depend on cyber security ". Therefore, now all US government agencies of federal subordination are engaged in the development and implementation of a unified information security strategy for energy companies, commercial and non-profit organizations working in strategic sectors of the country's economy.
Information security technologies were also an important sector of the largest international exhibitions held in 2012 devoted to information and telecommunication technologies. Of particular interest at these exhibitions was the section on ensuring the information security of mobile devices.
Taking into account that by 2014, 80% of all calls to the Internet will occur through mobile phones and tablets, foreign companies are actively developing various information security systems for mobile devices. In most cases, a fully software solution is used which is installed on a mobile phone or tablet to reduce the cost and provide convenience to the user.
As a result, the "miser pays twice": modern hackers, using sophisticated virus programs, as well as various attacks via BlueTooth, Wi-Fi and, easily bypass such protection. It should also be understood that the technical means used by them for this purpose are comparable in their characteristics with those used by the special services. For example, for the purpose of cyber theft, computers are used that can collect a few trillion passwords per second. Given that this article is aimed at the mass user, we will not stop to consider “protected” technologies, as for President Obama, whose development costs tens of millions and costs tens of thousands of dollars. In our case, this is unacceptable.
The solution to the problem described above was the creation of conditions for the protection of information outside mobile devices. ROHDE & SCHWARZ company took this path, but the device developed by it can only encrypt voice.
The “Stealthphone Software” solution, created by the specialists of the Ankort company, is a software that can be supplemented by hardware to provide the necessary level of protection of the information array.
Stealthphone Software is a software application for a mobile phone or tablet running on iOS, Android, Symbian and BlackBarry operating systems.
The considered application is designed to protect the information of your mobile phone or tablet during data transfer by voice, SMS, MMS and e-mail. This application installed on your mobile phone or tablet that supports the Internet connection function will ensure the confidentiality of any information transmitted via 3G, 3.5G, EDGE, Wi-Fi, WiMAX communication networks. “Stealthphone Software” works through the Ankort's IP servers, which pass the information transmitted through them in a secure manner, which prevents access to the data by the operators of such a server and reduces the cost of communication services for subscribers. The quality of voice transmission is comparable to that provided by the newest program for IP-telephony Viber, which is widespread in the West, having 70,000,000 users and is the main competitor of Skype. The user capabilities of Viber (SIP client, SMS), being provided for use, in the software application “Stealthphone Software” are supplemented by the possibilities of sending SMS, MMS, e-mail and secure chat in an encrypted form.
A number of competitive software solutions are presented on the information security market, which, according to the developers, guarantee the protection of information when working in IP networks.
In particular, experts from Ankort conducted a preliminary analysis of the capabilities of the Stealthphone Software application and the SilentCircle solution. As a result, it was concluded that when comparing the two specified software products, the advantages of “Stealthphone Software” are:
More detailed comparative information is also presented in the table below:
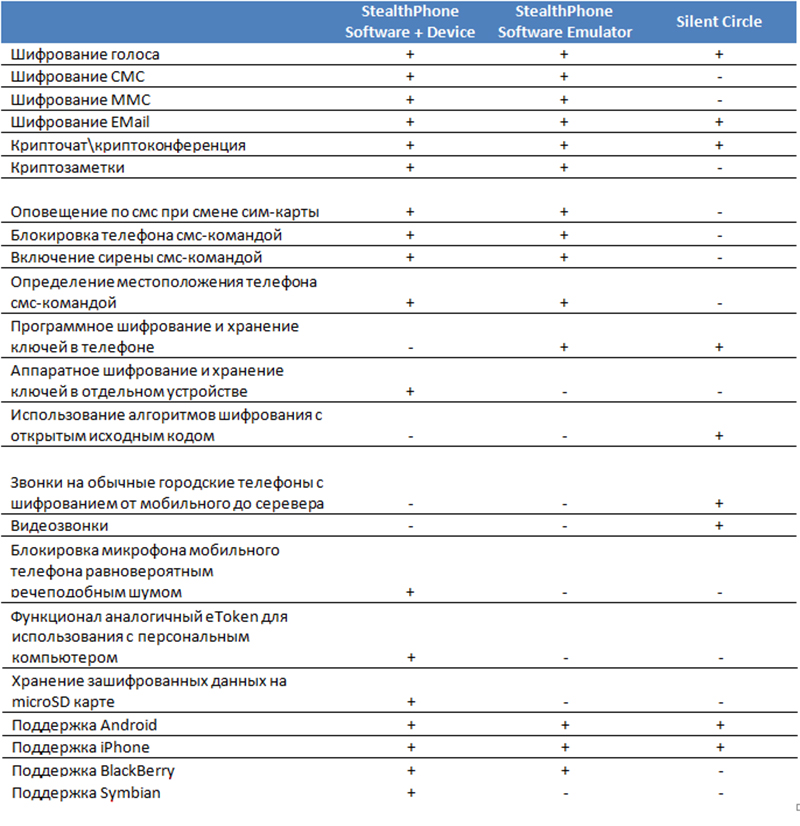
Thus, the Stealthphone Software application corresponding to the current state of development of information resources and infrastructure is designed for the widest range of consumers, but first of all it should interest representatives of those professional communities (politicians, bankers and brokers, journalists, lawyers, commercial managers). companies, etc.) that deal with strictly confidential information.
With the demo version of "Stealthphone Software", you can share on Google Play
The use of mobile phones and tablets involves the transfer of various kinds of information in voice, text and graphic form. This may be data containing personal and even intimate details. But in modern conditions when using a mobile phone or tablet, there is no clear distinction between the scope of their use, which, in turn, leads to the accumulation in the device’s memory not only private information, but also information used in the work. One of the consequences of this in 60% of cases, according to the Ponemon Institute , is the removal of important corporate information by hackers when a mobile device is lost by a negligent employee, as a result of which the employer company loses its competitive advantage.
We live in the information space, the boundaries of which are endless and are not legally restricted by anyone. The developing situation is taken into account by specialists all over the world when determining the approach to solving information security (cyber security) issues.
')
It is not for nothing that US President Barack Obama, at one of his speeches in August 2012, made a statement that “cyber threat is one of the most serious economic and national security problems,” he determined that “America’s economic prosperity in the 21st century will depend on cyber security ". Therefore, now all US government agencies of federal subordination are engaged in the development and implementation of a unified information security strategy for energy companies, commercial and non-profit organizations working in strategic sectors of the country's economy.
Information security technologies were also an important sector of the largest international exhibitions held in 2012 devoted to information and telecommunication technologies. Of particular interest at these exhibitions was the section on ensuring the information security of mobile devices.
Taking into account that by 2014, 80% of all calls to the Internet will occur through mobile phones and tablets, foreign companies are actively developing various information security systems for mobile devices. In most cases, a fully software solution is used which is installed on a mobile phone or tablet to reduce the cost and provide convenience to the user.
As a result, the "miser pays twice": modern hackers, using sophisticated virus programs, as well as various attacks via BlueTooth, Wi-Fi and, easily bypass such protection. It should also be understood that the technical means used by them for this purpose are comparable in their characteristics with those used by the special services. For example, for the purpose of cyber theft, computers are used that can collect a few trillion passwords per second. Given that this article is aimed at the mass user, we will not stop to consider “protected” technologies, as for President Obama, whose development costs tens of millions and costs tens of thousands of dollars. In our case, this is unacceptable.
The solution to the problem described above was the creation of conditions for the protection of information outside mobile devices. ROHDE & SCHWARZ company took this path, but the device developed by it can only encrypt voice.
The “Stealthphone Software” solution, created by the specialists of the Ankort company, is a software that can be supplemented by hardware to provide the necessary level of protection of the information array.
Stealthphone Software is a software application for a mobile phone or tablet running on iOS, Android, Symbian and BlackBarry operating systems.
The considered application is designed to protect the information of your mobile phone or tablet during data transfer by voice, SMS, MMS and e-mail. This application installed on your mobile phone or tablet that supports the Internet connection function will ensure the confidentiality of any information transmitted via 3G, 3.5G, EDGE, Wi-Fi, WiMAX communication networks. “Stealthphone Software” works through the Ankort's IP servers, which pass the information transmitted through them in a secure manner, which prevents access to the data by the operators of such a server and reduces the cost of communication services for subscribers. The quality of voice transmission is comparable to that provided by the newest program for IP-telephony Viber, which is widespread in the West, having 70,000,000 users and is the main competitor of Skype. The user capabilities of Viber (SIP client, SMS), being provided for use, in the software application “Stealthphone Software” are supplemented by the possibilities of sending SMS, MMS, e-mail and secure chat in an encrypted form.
A number of competitive software solutions are presented on the information security market, which, according to the developers, guarantee the protection of information when working in IP networks.
In particular, experts from Ankort conducted a preliminary analysis of the capabilities of the Stealthphone Software application and the SilentCircle solution. As a result, it was concluded that when comparing the two specified software products, the advantages of “Stealthphone Software” are:
- high quality voice;
- transfer of information in a protected form via 3G, 3.5G, EDGE, Wi-Fi, WiMAX communication channels;
- the guarantee of preserving the confidentiality of data when a mobile device is lost;
- support for the work of "Stealthphone Software" with low-speed mobile Internet connections;
- use of its own developed encryption algorithm, certified by the governments of Sweden and South Africa;
- the ability to generate user encryption keys;
- the ability to supplement the software application "Stealthphone Software" hardware encoder "Stealthphone Touch", which increases the security of transmitted information.
More detailed comparative information is also presented in the table below:

Thus, the Stealthphone Software application corresponding to the current state of development of information resources and infrastructure is designed for the widest range of consumers, but first of all it should interest representatives of those professional communities (politicians, bankers and brokers, journalists, lawyers, commercial managers). companies, etc.) that deal with strictly confidential information.
With the demo version of "Stealthphone Software", you can share on Google Play
Source: https://habr.com/ru/post/158321/
All Articles