Is the CIA model useful for protecting a process control system?
I was prompted to write this post by a recent article and the subsequent discussion on the Tofino Security website on the priority of security properties (confidentiality, integrity and availability) of information in the process control system.
Is this question correctly posed in relation to the process control system?
The CIA model (confidentiality, integrity, availability) has passed the test of time and to question it is a thankless task. But due to the specifics of the process control system, I think it is worth reviewing the applicability of this model. It is necessary to understand how adequately it describes the information security of an automated process control system, and whether any changes are required.
Take a look at confidentiality, integrity and availability in terms of management decisions. We need information to make informed decisions and their further implementation in order to achieve our goals.
')
If confidentiality is violated, our decisions become known to our opponents, which causes their response and does not allow us to achieve our goals. The result of all activities is negative, the goal is not achieved.
If integrity is violated, our decisions become erroneous, as they are based on distorted information. The situation is complicated by the fact that it is unknown when we find out that the information was distorted. The result of the same.
If accessibility is impaired, we cannot make a decision at all. The good news here is that we know that there is no information, and if we have extra time, we still have a chance to get it. The result of the same.
The above was a very general approach. To protect the process control system, such an approach is not required. It can be narrowed down by the specifics and specifics of the process control system. Namely:
Based on the first paragraph, privacy protection becomes unnecessary. Here it is necessary to give additional comments, since a number of studies are known dedicated to determining the type of technological process (control object) as a result of analysis of captured network traffic. But still, in this case, the knowledge obtained in this way cannot affect the achievement of the goal of controlling an automated process control system, but it can help an attacker to develop an attack on an automated process control system. Then this knowledge should be attributed to the type of information “About the PCS”, and not to the technological information processed within the PCS. And then it is necessary to protect the confidentiality of information "About ASUTP". This type of information includes: design and operational documentation and other information that allows you to identify and describe the process control system (something like personal data, only about the process control system).
In conditions of limited time (fourth point), availability and integrity in an automated process control system become equivalent, since the consequences of the lack of a solution (due to a violation of accessibility) or an erroneous decision (a consequence of a violation of integrity) for the process are the same. In the given time frame, only the correct solution is acceptable.
Thus, the entire information security of an automated process control system degenerates into the protection of one: integrity-accessibility or accessibility-integrity. Somehow unexpected! Is such a model useful?
Thus, it’s pointless to argue about the priority of confidentiality, integrity and availability. We received an answer to the question at the beginning of the post and asked a new one.
Let's leave our theoretical studies and move on closer to the practice. But in practice we need to find technical means and organizational measures to ensure the information security of the automated process control system, namely, to protect against unauthorized access threats for the integrity of the information security of the automated process control system . How many people will understand what to do with such a formulation of the problem? And most importantly, will dispatchers and operators of an automated process control system feel the importance and adequacy of such “protection of an automated process control system” that is simply necessary for information security in an automated process control system? In my opinion, the answers to these questions are negative.
Therefore, I would suggest the protection of the process control system from unauthorized access based on the following model based on the CIA, but more adequate in the process control system:
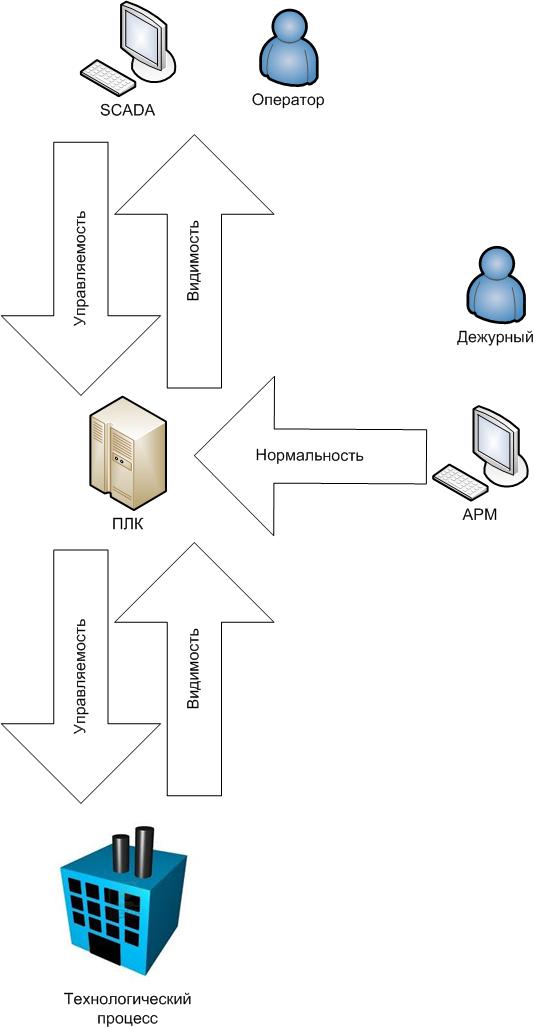
How this model is adequate and practically useful to judge you, the readers of Habrahabr.
Is this question correctly posed in relation to the process control system?
The CIA model (confidentiality, integrity, availability) has passed the test of time and to question it is a thankless task. But due to the specifics of the process control system, I think it is worth reviewing the applicability of this model. It is necessary to understand how adequately it describes the information security of an automated process control system, and whether any changes are required.
Take a look at confidentiality, integrity and availability in terms of management decisions. We need information to make informed decisions and their further implementation in order to achieve our goals.
')
If confidentiality is violated, our decisions become known to our opponents, which causes their response and does not allow us to achieve our goals. The result of all activities is negative, the goal is not achieved.
If integrity is violated, our decisions become erroneous, as they are based on distorted information. The situation is complicated by the fact that it is unknown when we find out that the information was distorted. The result of the same.
If accessibility is impaired, we cannot make a decision at all. The good news here is that we know that there is no information, and if we have extra time, we still have a chance to get it. The result of the same.
The above was a very general approach. To protect the process control system, such an approach is not required. It can be narrowed down by the specifics and specifics of the process control system. Namely:
- Technological information (emerging events, input data and output commands) is typical, operational and local, that is, it is typical for such systems, loses its relevance very quickly and makes sense within the same system, respectively.
- Decisions are made by dispatchers and control system operators, as well as computing devices (for example: programmable logic controllers) according to a given algorithm (software), based on arising events and / or input data (information gathering).
- Decisions (teams) are performed by duty or operational personnel, as well as executive mechanisms.
- The time for the adoption and execution of the decision is strictly limited.
- Process control can be either automated (with human participation) or automatic (without human participation).
- The process control loop (contour) consists of the acquisition phase, the decision phase (automatic processing or calculations) and the command phase.
- The subject of information security of an automated process control system is protection against unauthorized access (other problems related to information are not new for an automated process control system and it can solve them, for example, with the help of industrial safety).
- The PCS can process and store information of interest to criminals (for example, terrorists). For example, information on the accounting process resources may be of interest to criminals seeking to gain illegal benefits and hide the traces of their crimes.
Based on the first paragraph, privacy protection becomes unnecessary. Here it is necessary to give additional comments, since a number of studies are known dedicated to determining the type of technological process (control object) as a result of analysis of captured network traffic. But still, in this case, the knowledge obtained in this way cannot affect the achievement of the goal of controlling an automated process control system, but it can help an attacker to develop an attack on an automated process control system. Then this knowledge should be attributed to the type of information “About the PCS”, and not to the technological information processed within the PCS. And then it is necessary to protect the confidentiality of information "About ASUTP". This type of information includes: design and operational documentation and other information that allows you to identify and describe the process control system (something like personal data, only about the process control system).
In conditions of limited time (fourth point), availability and integrity in an automated process control system become equivalent, since the consequences of the lack of a solution (due to a violation of accessibility) or an erroneous decision (a consequence of a violation of integrity) for the process are the same. In the given time frame, only the correct solution is acceptable.
Thus, the entire information security of an automated process control system degenerates into the protection of one: integrity-accessibility or accessibility-integrity. Somehow unexpected! Is such a model useful?
Thus, it’s pointless to argue about the priority of confidentiality, integrity and availability. We received an answer to the question at the beginning of the post and asked a new one.
Let's leave our theoretical studies and move on closer to the practice. But in practice we need to find technical means and organizational measures to ensure the information security of the automated process control system, namely, to protect against unauthorized access threats for the integrity of the information security of the automated process control system . How many people will understand what to do with such a formulation of the problem? And most importantly, will dispatchers and operators of an automated process control system feel the importance and adequacy of such “protection of an automated process control system” that is simply necessary for information security in an automated process control system? In my opinion, the answers to these questions are negative.
Therefore, I would suggest the protection of the process control system from unauthorized access based on the following model based on the CIA, but more adequate in the process control system:
- The closure of the process control is the protection of the integrity and availability of technological information, as well as the integrity of the parameters and software of the entire control cycle.
- - Visibility of the technological process - protection of the integrity and availability of technological information, as well as the integrity of the parameters and software of the control information acquisition phase.
- - Process controllability - protection of the integrity and availability of technological information, as well as the integrity of the parameters and software of the control cycle command phase.
- - Process normality - protecting the integrity of the parameters and software of the automatic control cycle processing phase
- Continuity of process control - protection against accident, shutdown or critical delays
- Aloof here is the prevention and detection of economic and criminal offenses (integrity, provability).

How this model is adequate and practically useful to judge you, the readers of Habrahabr.
Source: https://habr.com/ru/post/158255/
All Articles