SCADA security in numbers
 Nuclear and hydroelectric power stations, oil and gas pipelines, factories, transport networks (subways and high-speed trains), as well as many other vital systems for humanity are controlled using various computer technologies.
Nuclear and hydroelectric power stations, oil and gas pipelines, factories, transport networks (subways and high-speed trains), as well as many other vital systems for humanity are controlled using various computer technologies.A wide interest in the protection of industrial systems arose after a series of incidents with the Flame and Stuxnet viruses, which were the first signs of the cyberwar era. In Russia, there is another reason to pay attention to the security of such systems - new requirements of regulators aimed at improving the security of the automated process control system (ICS / SCADA / PLC).
In order to choose adequate security measures, it is necessary to understand what capabilities a cybercriminal has and what attack vectors he can use. To answer these questions, Positive Technologies experts conducted an ICS / SCADA safety study. Results under the cut.
')
The object of the study were vulnerabilities discovered from 2005 to October 1, 2012. Briefly, several facts can be noted from the analysis:
- For several months of 2012, more vulnerabilities have been found in the process control system than in the entire previous year: a rapid increase in their number is occurring.
- Problems, as always, are found in the most popular products, and about 65% of vulnerabilities are serious or critical.
- The United States and Europe are leading in the number of automated process control systems accessible from the Internet, while 40% of all external SCADA systems are vulnerable and can be hacked.
- Most of the security problems of the automated process control systems accessible from the Internet are related to configuration errors (such as standard passwords) and the lack of updates.
But about everything in order.
Demand for automated process control systems in Russia
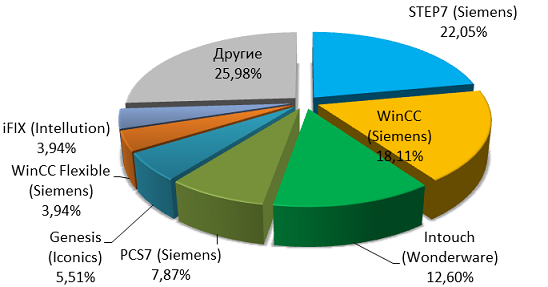
Approximately, the shares of different manufacturers in the market of automated process control systems can be represented by assessing the demand for specialists with experience with a particular system, protocol, technology or program. As a basis for the analysis was taken statistics hh.ru vacancy database. The most popular were specialists with experience in working with Siemens solutions. Four of the six most common products belong to the Siemens SIMATIC family:
- Step 7 - development of automation systems based on PLC (about 22.05%),
- WinCC and WinCC Flexible - creating a human-machine interface (18.11% and 3.94% respectively),
- PCS 7 - building complex automation systems (7.87%).
The top five also includes Wonderware's InTouch HMI (12.6%) and the Iconics Genesis software package (5.51%).
If we consider the technology of data transmission, the most popular of them are Modbus (RTU and TCP / IP) and Profibus / Profinet, occupying approximately 33% each. Next comes OPC (25%).
Among all operating systems used with the automated process control system, Microsoft Windows leads the way, with experience in most advertisements in this area. Knowledge of QNX and FreeRTOS are indicated only in a small number of vacancies.
In the segment of programmable logic controllers (PLC, PLC) most often looking for experts on Siemens solutions (approximately 31%). This is followed by the products of Schneider Electric (11%), ABB (9%), Allen-Bradley (7%) and Emerson (5%).
Vulnerability Analysis
Vulnerabilities are often published without coordination with the developers, so for our research we used data from various sources, such as the vulnerability database and vendor notifications, exploit packs, specialized events reports, publications on thematic sites and blogs .
It is interesting to note that in the period from 2005 to early 2010, only 9 vulnerabilities were discovered in the automated process control systems, and after the appearance of the Stuxnet worm and the ensuing hype in 2011, 64 vulnerabilities were already found. In the first eight months of 2012, 98 new vulnerabilities became known: this is more than in all previous years.
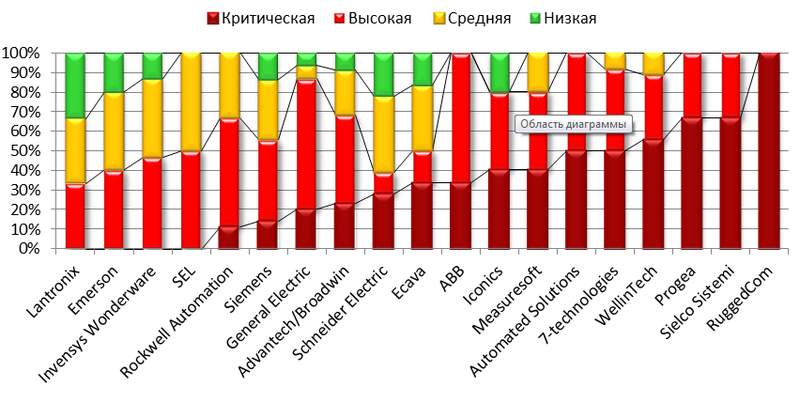
The greatest number of vulnerabilities (42) for the reporting period was found in the components of the industrial control system manufactured by Siemens. In second place is the Broadwin / Advantech system (22). The third is Schneider Electric (18). A similar picture in the case of automated process control systems, as well as in information technologies in general, is explained by the fact that the greatest number of vulnerabilities is found in the most common solutions. In addition, a number of manufacturers have only recently begun to actively search for and fix vulnerabilities in their products (an example is Siemens ProductCERT ).
Vulnerabilities by type of hardware and software components for industrial process control systems
Of greatest interest to attackers are components of the automated process control system, such as SCADA and human-machine interface (HMI), in which 87 and 49 vulnerabilities are found, respectively. In the programmable logic controllers of different manufacturers during the reporting period, 20 vulnerabilities were found.
Types of vulnerabilities
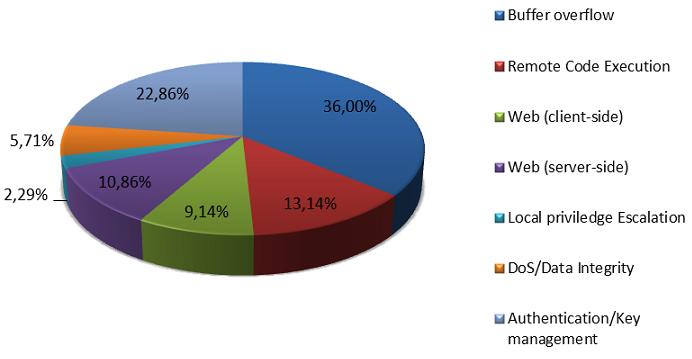
Almost a third of the vulnerabilities (36%) are related to buffer overflow (Buffer Overflow). This security problem allows an attacker to not only cause a program crash or hang the program, which leads to a denial of service, but also to execute arbitrary code on the target system. If you add up all types of vulnerabilities, the exploitation of which allows a hacker to launch code execution (for example, buffer overflow, remote code execution), you will get about 40% of all vulnerabilities. It is worth noting a large number of problems with authentication and key management (Authentication / Key Management) - almost 23%.
The proportion of eliminated vulnerabilities ACS TP
Most security flaws (81%) were promptly eliminated by manufacturers — even before they became widely known, or within 30 days after uncoordinated disclosure of information. However, approximately every fifth vulnerability was “closed” with a serious delay, and in some cases was not eliminated.
A visual representation of how seriously the various vendors of the automated process control system take information security issues gives a fraction of “closed” vulnerabilities. For example, Siemens has fixed and released updates for 98% of vulnerabilities, while Schneider Electric has eliminated just over half (56%) of the problems found.
Availability of information or attack software
The availability in the public domain of a ready means for exploiting a vulnerability or information about it significantly increases the likelihood of a successful attack. Currently, for 35% of all vulnerabilities represented in the APCS, exploits exist that are distributed as separate utilities, are included in software packages for pentests, or are described in vulnerability notifications. The same indicator for other IT systems is several times smaller.
As a rule, the number of published vulnerabilities correlates with the number of published exploits. In the period from the beginning of 2011 to September 2012, 50 exploits were published - six times more than in six years from 2005 to 2010.
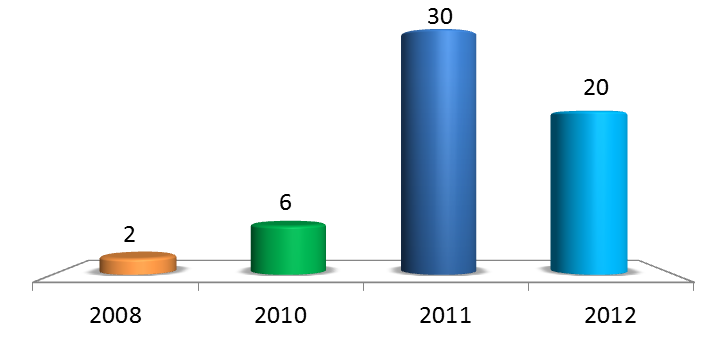
The relatively small number of exploits that appeared in 2012 is due to two factors:
- streamlining the relationship between manufacturers of industrial control systems and researchers, the policy of responsible disclosure;
- traditional delay between the publication of a vulnerability and the release of an exploit (its development requires additional costs).
The degree of risk of detected vulnerabilities
Almost 65% of all vulnerabilities are classified as high (CVSS v. 2 Base Score> 6.5) or critical risk (an exploit is available).
However, the lack of a known method for implementing an attack reduces the likelihood of an attack, but does not completely exclude it, since cyber attacks on industrial facilities are carried out with the assistance of experienced high-level specialists who often simply do not need "exploit packs" and other popular tools.
Unresolved vulnerabilities of process control systems
Vulnerabilities that already have an exploit, but have not yet released a fix, pose the greatest danger, since an attacker does not need in-depth knowledge and lengthy preparation to penetrate the system. Any student who decides to cheat may cause enormous damage. The worst situation here is for products of the Schneider Electris automated process control system: 6 open vulnerabilities have been discovered. General Electric is in second place (three vulnerabilities), Advantech / Broadwin and Rockwell Automation share third place - they each have one open vulnerability.
Prevalence of ICS systems on the Internet
In order to understand the extent to which all these vulnerabilities could be exploited by an attacker, an Internet study was conducted to determine the presence of vulnerable process control systems. Search and verification of system versions was carried out using passive analysis methods using search engines (Google, Yahoo, Bing) and specialized knowledge bases, such as ShodanHQ, Every Routable IP Project. The information obtained was analyzed in terms of the presence of vulnerabilities related to configuration management and the installation of updates.
Almost a third of the automated process control systems, which have access to the elements from the Internet, are located in the USA (31.3%). The second place with a large margin is Italy (6.8%), South Korea closes the top three (6.2%). Russia ranks 12th with 2.3%, while in the PRC there are only 1.1% of all visible from the global network of automated process control systems.
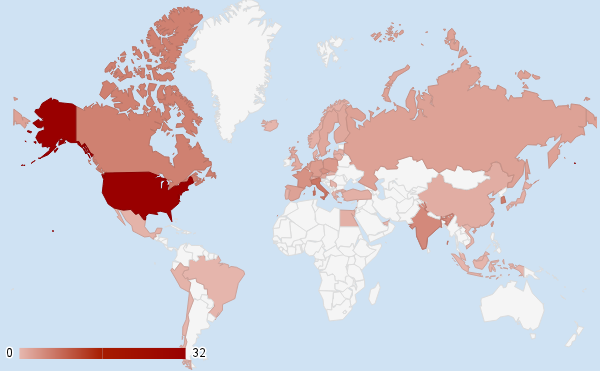
The results are expected, since the number of available systems directly depends on the degree of automation of the infrastructure.
Types of automated process control systems
Most often, the global network contains various components of SCADA systems (including HMI). They account for 70% of all detected objects. Another 27% of the available components of the process control system are programmable logic controllers. In 3% of cases, various network devices used in the ACS TP (Hardware) networks were detected.
Types of vulnerabilities
The most common security flaws (detected in 36% of cases) are associated with configuration errors. This includes incorrect password policies (for example, the use of standard engineering passwords), access to critical information, erroneous separation of powers. A quarter of the vulnerabilities are due to the lack of the required security updates.
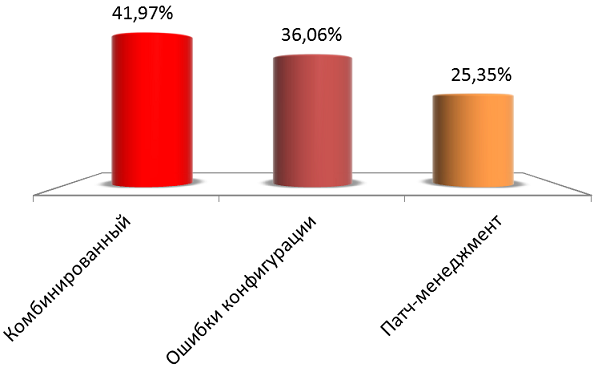
Proportion of vulnerable process control systems in various countries and regions
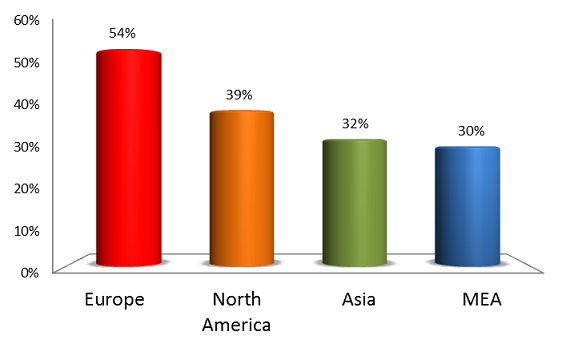
The most vulnerable systems for process control systems that are “visible” from the Internet are in Switzerland (100%). Next comes the Czech Republic (86%), in third place is Sweden (67%). In Russia, exactly half of the automated process control systems accessible from outside are vulnerable.
The security systems in Europe are least concerned about security in Europe: 54% of industrial automation systems are vulnerable in this region. North America is in second place (39%), then Asia (32%), where unsafe objects in Taiwan and South Korea play a significant role.
Source: https://habr.com/ru/post/157589/
All Articles