The advantages of Check Point centralized security over network competitors
To write this article I pushed the discussion in the comments Installation and initial configuration of Check Point R75 . What does Check Point's multifunctional security gateway outperform its famous competitors Cisco, Juniper, PaloAlto, and others?
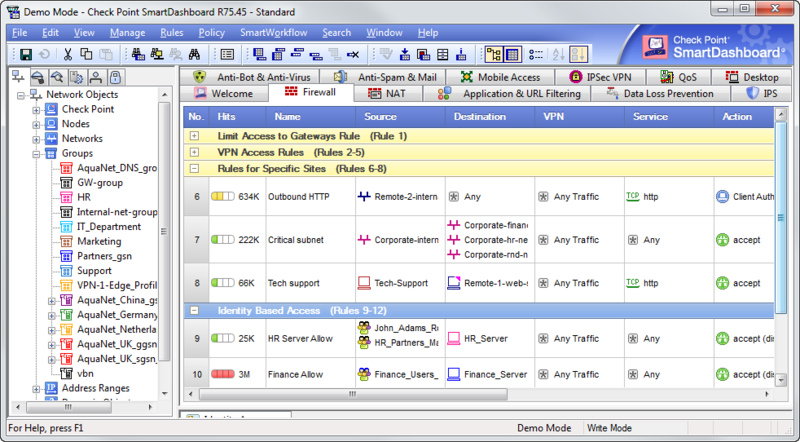
The strengths of this solution are many, the main of which, in my opinion, is the system of centralized management of IT security policy from a single administrator console:
')
Historically, this is the first firewall to use Stateful Inpection technology (session state tracking). Check Point offered software for installation on x86-compatible servers / Sparc-servers / Nokia-platform (actually, this is reflected in the name of Check Point Software Technologies), and since 2007, hardware gateways with a pre-installed OS and security software have appeared in the line. . The same fate befell the SmartCenter control system - it is available both in software and in the form of hardware Smart-1 devices.
Since April 2012, Gaia has been the operating system on all platforms, the result of combining the capabilities of SPLAT (Secure PLATform Check Point, RHEL-based) and the takeover of Nokia business with its IPSO operating system and IP appliance with hardware.
Equipment for small offices / branches UTM-1 Edge and Safe @ Office uses a different, simplified, firmware and specialized hardware.
All Check Point functionality is licensed for Security Blades and Management Blades , security signature blades (IPS, antivirus, antispam, URL-filtering, application control, DLP) require an annual subscription renewal. There is also a separate Endpoint Security branch (Full Disk Encryption, Port Protection and media encryption, FW + AV + etc), but not about that now.
Regardless of the size of the customer’s network and the number of branch offices, all security gateways are managed from a single point - the SmartCenter server, part of the interface above. The three-tier management system: the administrator with the SmartConsole installed connects to the SmartCenter, and the SmartCenter distributes policy to the gateways and collects logs.
And here is the killer feature: the administrator prescribes a security policy without binding to specific security gateways!
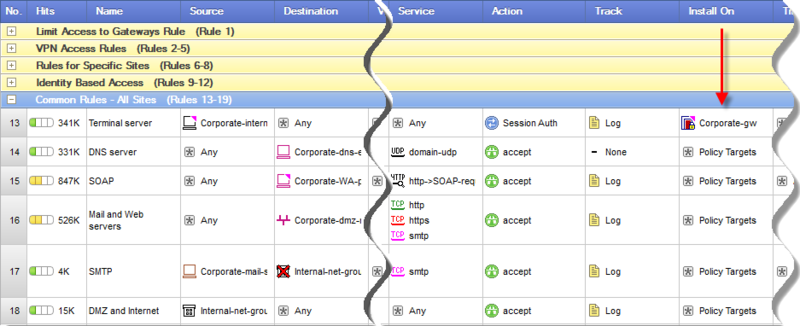
This is achieved due to the fact that SmartCenter automatically generates and sends policies (Policy Package) to security gateways based on the data on the interfaces and network topology behind each security gateway. And the topology is defined by the administrator in the properties of the security gateway:
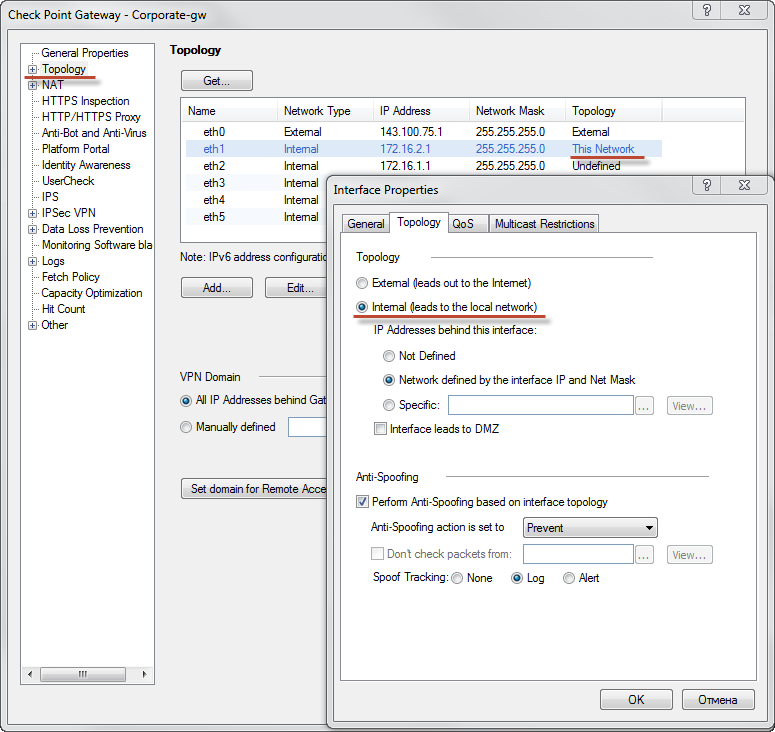
Having a single database of enterprise network objects (networks, nodes, groups of objects, users from the LDAP directory) and a single holistic security policy increases the readability of the policy, reduces errors caused by human factors. Management from the graphical interface without the need to configure settings in the command line on each of the interfaces reduces the amount of routine work by an order of magnitude.
In the case of expanding the number of branches, new security gateways must be connected to the SmartCenter management server (create network objects and establish secure internal communication with them SIC). Then you can install the policy as usual - the server will generate the Policy Package for them.
Configuring VPN between branches also occurs centrally and with a few clicks:
Thanks to such a convenient VPN configuration (as well as the SmartProvisioning toolkit for managing multiple, same-pattern-based gateways), Check Point solutions are used to protect large branch networks and ATM traffic in particular. So, in Ukraine, one of the banks successfully operates 3,000 ATMs according to the above centralized management scheme.
The presence of centralized management has another advantage - all security events (logs) are collected and processed centrally. Administrator has access to 3 logging tools:
Check Point was and remains a vendor, 100% focused on IT security. Currently, all 500 Fortune 500 companies are using its products.
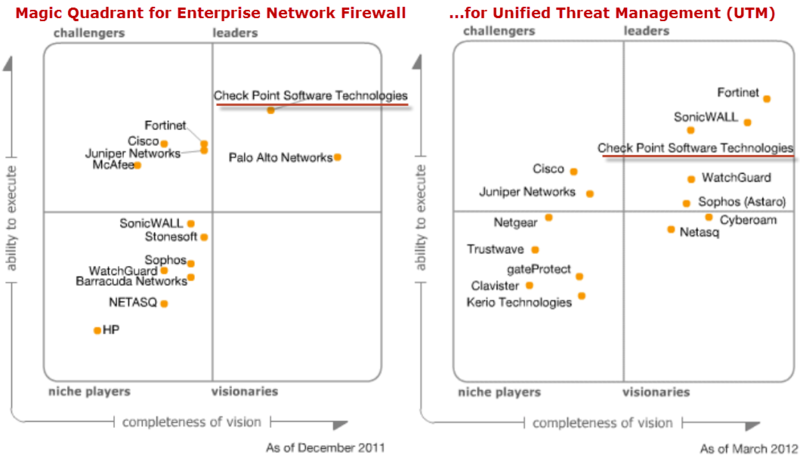
Gartner Quadrant's annual analytical reviews also confirm the leading position in the market for Enterprise Network Firewall (December 2011) and Unified Threat Management (March 2012):
Of course, the ideal approach to IT security does not exist. This article does not aim to start a holivar “who is better”; its goal is to indicate the strengths of Check Point solutions; perhaps for some people they will be decisive when choosing a gateway for perimeter network protection.
PS Screenshots of the control system interface are made on the basis of demo data (network objects, rules, logs). You can get acquainted yourself - for this you need to download a full-fledged SmartConsole management console ( mirror , of.sayt ), install it and run in the "demo" mode.
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
The strengths of this solution are many, the main of which, in my opinion, is the system of centralized management of IT security policy from a single administrator console:

')
For a start, a quick tour of Check Point.
Historically, this is the first firewall to use Stateful Inpection technology (session state tracking). Check Point offered software for installation on x86-compatible servers / Sparc-servers / Nokia-platform (actually, this is reflected in the name of Check Point Software Technologies), and since 2007, hardware gateways with a pre-installed OS and security software have appeared in the line. . The same fate befell the SmartCenter control system - it is available both in software and in the form of hardware Smart-1 devices.
Since April 2012, Gaia has been the operating system on all platforms, the result of combining the capabilities of SPLAT (Secure PLATform Check Point, RHEL-based) and the takeover of Nokia business with its IPSO operating system and IP appliance with hardware.
Equipment for small offices / branches UTM-1 Edge and Safe @ Office uses a different, simplified, firmware and specialized hardware.
All Check Point functionality is licensed for Security Blades and Management Blades , security signature blades (IPS, antivirus, antispam, URL-filtering, application control, DLP) require an annual subscription renewal. There is also a separate Endpoint Security branch (Full Disk Encryption, Port Protection and media encryption, FW + AV + etc), but not about that now.
Centralized management and scalability
Regardless of the size of the customer’s network and the number of branch offices, all security gateways are managed from a single point - the SmartCenter server, part of the interface above. The three-tier management system: the administrator with the SmartConsole installed connects to the SmartCenter, and the SmartCenter distributes policy to the gateways and collects logs.
And here is the killer feature: the administrator prescribes a security policy without binding to specific security gateways!

This is achieved due to the fact that SmartCenter automatically generates and sends policies (Policy Package) to security gateways based on the data on the interfaces and network topology behind each security gateway. And the topology is defined by the administrator in the properties of the security gateway:

Having a single database of enterprise network objects (networks, nodes, groups of objects, users from the LDAP directory) and a single holistic security policy increases the readability of the policy, reduces errors caused by human factors. Management from the graphical interface without the need to configure settings in the command line on each of the interfaces reduces the amount of routine work by an order of magnitude.
In the case of expanding the number of branches, new security gateways must be connected to the SmartCenter management server (create network objects and establish secure internal communication with them SIC). Then you can install the policy as usual - the server will generate the Policy Package for them.
Configuring site-to-site VPN branch office tunnels
Configuring VPN between branches also occurs centrally and with a few clicks:
- Create a new VPN community with a specific topology (star or fully connected), specify which gateways are participating in this “VPN community”:
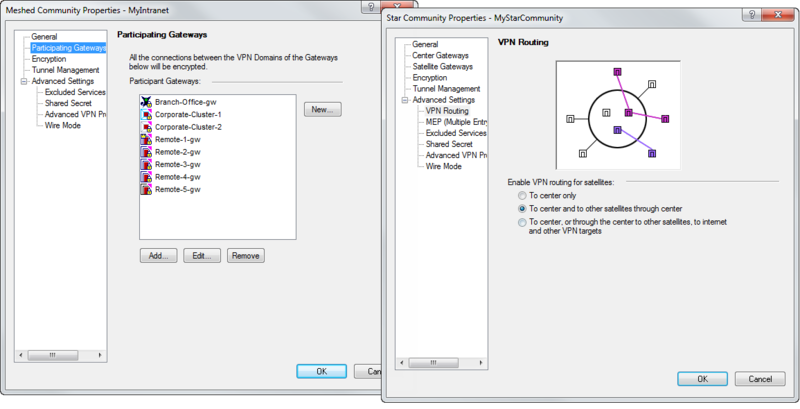
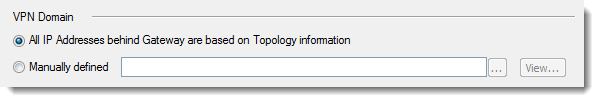
- Identify each of the gateways in the properties of their “VPN Domain”, i.e. networks whose traffic should be automatically encrypted. By default, these are all networks behind the gateway based on its Topology information, but you can also specify them manually:
- Refine in the firewall rule (“from-to-kind of traffic-action”) the type of traffic by a specific VPN community:

- Install policy. That's it, we set up Site-to-Site VPN!
Thanks to such a convenient VPN configuration (as well as the SmartProvisioning toolkit for managing multiple, same-pattern-based gateways), Check Point solutions are used to protect large branch networks and ATM traffic in particular. So, in Ukraine, one of the banks successfully operates 3,000 ATMs according to the above centralized management scheme.
Security event correlation (SmartEvent integrated SIEM system) and viewing logs
The presence of centralized management has another advantage - all security events (logs) are collected and processed centrally. Administrator has access to 3 logging tools:
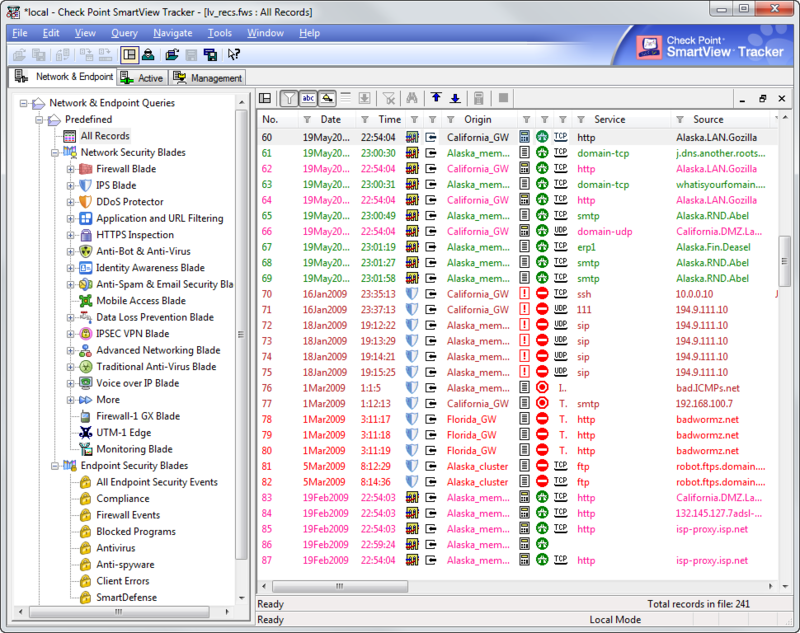
- SmartView Tracker for a classic display of all events in the form of a table, as well as on the filter of the source blade that generated the log (be it before the firewall, antivirus or IPS-reflection of the attack).
- SmartLog for quick sampling of filters of interest, using the advantages of indexing the database of logs - the results are output almost instantly.

- SmartEvent to correlate (group) security events from all blades on a single time scale. This tool allows you to track complex attacks and trends, can rightly be considered the dispatching point of a security officer - you can immediately see the danger (the degree of importance of events) and the intensity (number of alarms) of current violations. The drill down mechanism is also convenient - the administrator moves from general information (for example, 5 security events) to private information (3 IPS events, 1 DLP event and 1 antivirus event), and then to the detailed one - according to which IPS signature triggered what is the signature and attack mechanism.
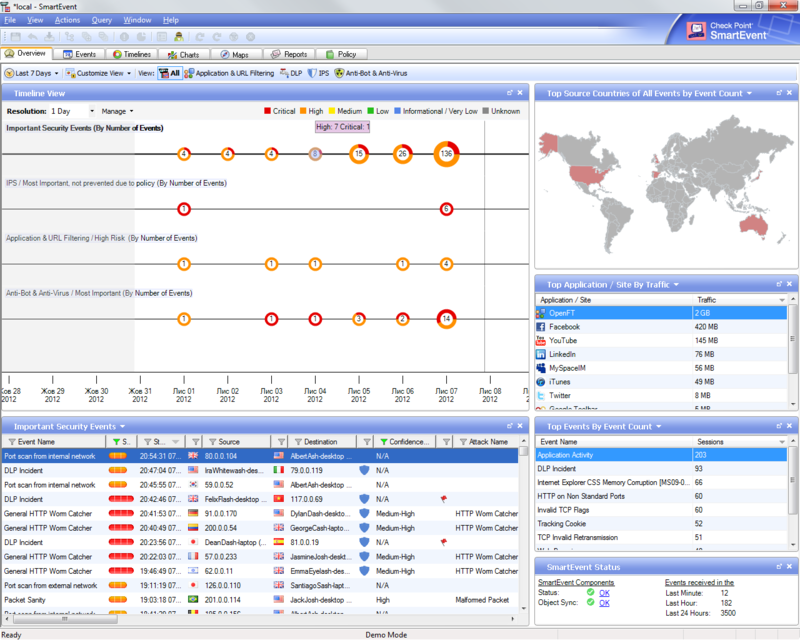
And with a double click on a group of 8 events in the top row we get a detailed description: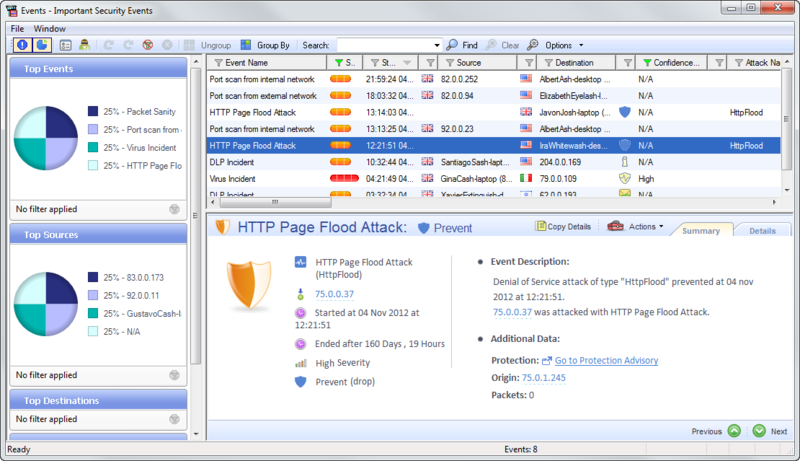
Marketing arguments
Check Point was and remains a vendor, 100% focused on IT security. Currently, all 500 Fortune 500 companies are using its products.
Gartner Quadrant's annual analytical reviews also confirm the leading position in the market for Enterprise Network Firewall (December 2011) and Unified Threat Management (March 2012):

As a conclusion
Of course, the ideal approach to IT security does not exist. This article does not aim to start a holivar “who is better”; its goal is to indicate the strengths of Check Point solutions; perhaps for some people they will be decisive when choosing a gateway for perimeter network protection.
PS Screenshots of the control system interface are made on the basis of demo data (network objects, rules, logs). You can get acquainted yourself - for this you need to download a full-fledged SmartConsole management console ( mirror , of.sayt ), install it and run in the "demo" mode.
MUK-Service - all types of IT repair: warranty, non-warranty repair, sale of spare parts, contract service
Source: https://habr.com/ru/post/157385/
All Articles