Apple Wi-Fi Features and Implications for Organization Networks
Without any introduction, I would say that Apple iOS devices in corporate networks are present in considerable numbers, and in the future they seem to be fewer (especially with the popularization of BYOD ideology). And it does not matter whether they are used as a business device directly or simply as personal gadgets of employees and bosses. Therefore, it is necessary to put up with them and somehow get along. In this article, the features of Wi-Fi operation in Apple iOS are collected under one roof and there are links to materials for further study. Let's take a look at what is and is not in iOS, and how to live with it.
In general, in the vision of Apple i-devices in corporate networks, there is heaven, peace and grace. The paper on the deployment of iOS in corporate WLAN is provided with as much as one illustration. Apparently, nothing more to know is not necessary.
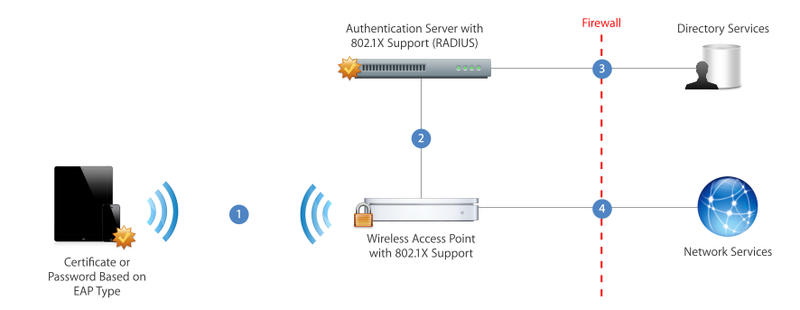
Let's go in reverse order.
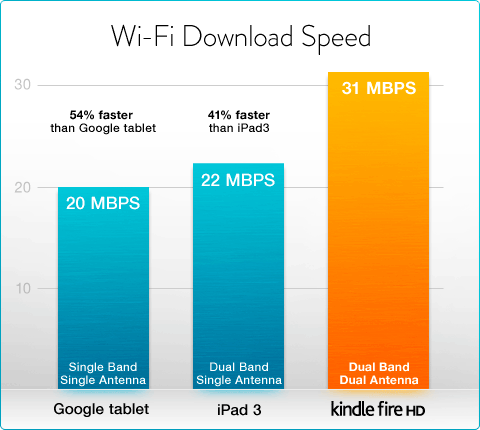
But, as the author of several popular financial pyramids likes to say, this was all a saying ...
An article on the Apple support site “recommendations for setting up WiFi for iOS devices” reveals interesting details.
An interesting note with a selection of Cisco TAC impressions of iOS support
Bonjour protocol (service announcement, AirPlay video transmission, etc.) is not routed. Those. devices must be in the same VLAN (which is normal at home). However, in a corporate environment, the chances of connecting a wired AppleTV and a wireless iPhone to the same VLAN are minimal (if you have the right network design).
Whether you consider iOS suitable for the corporate environment or do not consider - but somehow it is necessary to live with it. Let's summarize everything in the form of recommendations for iOS support in a corporate wireless network.
Ideally, we want to give people access to the Internet and nothing more. If you need mail and so on - it is much easier (from the Wi-Fi point of view) to force all these devices to enter the corporate network through a VPN, thanto wreak havoc and destruction to change something in a debugged Wi-Fi network.
If you plan to support corporate applications in the corporate network - you should think
Security is a great NSA document . I think they can be trusted ( if this is not a deliberate disinformation of a potential enemy ).
')
In conclusion, I note that Apple in terms of Wi-Fi has made a significant breakthrough. If the first firmware for the iPhone was so crooked that they cut the Cisco network tightly , now everything is much better. I still cannot call iOS-devices "corporate", but, in general, it is already possible to support iOS in the corporate network. If you are careful about your appetites and promises. (This is not related to fleet management and BYOD in general!)
Share opinions. Of particular interest is the experience of people supporting 50+ devices.
Good at first.
- All necessary (and unnecessary) encryption mechanisms are supported: WEP, TKIP, CCMP. At the same time, we remember that if we want 802.11n and high speeds on the network, then WEP and TKIP fall away, as Apple warns on the support site.
- All basic authentication mechanisms are supported: EAP-TLS, EAP-TTLS, EAP-SIM, PEAPv0 (MSCHAP-v2), PEAPv1 (GTC), and proprietary Cisco LEAP and EAP-FAST.
- PKCS # 1 (.cer, .crt, .der) and PKCS # 12 are supported from certificates.
- Very user-friendly 802.1x supplicant - no multi-level dialogs with obscure options - just enter the password, select / confirm the certificate and work.
- Thus, we have support for both WPA and WPA2 in the Personal and Enterprise versions and a wide range of options that the user can customize himself.
- The latest models support 802.11n and even 5 GHz.
- IOS6 has support for 802.11k and 802.11r, which allow the device when roaming to determine the optimal access point (APs transmit data about their load) and quickly move to it.
In general, in the vision of Apple i-devices in corporate networks, there is heaven, peace and grace. The paper on the deployment of iOS in corporate WLAN is provided with as much as one illustration. Apparently, nothing more to know is not necessary.

But it was not there.
Let's go in reverse order.
- 802.11k and 802.11r (according to the aforementioned paper) are supported only on iPhone 4S, iPhone / iTouch 5 and the new iPad - so they don’t have to count on them either.
- 5GHz is only supported on iPhone / Touch 5, iPad (1-4, mini) and Apple TV. However, there isn’t much enthusiasm for the iPhone 5, it’s not at all clear to iTouch 5 (you can take the Mini for almost the same money), and the iPhone 4 / 4S is still feeling quite good. Therefore, it is impossible to rely only on 5GHz for “total” support for i-gadgets - you will have to work at 2.4GHz with all the ensuing consequences (3 channels, interference, heaps of neighbors, etc.).
- Friendly 802.1X supplicant allows you to safely accept someone else's unverified certificate.
- It is very convenient for the lab and demonstrations, it is not very pleasant if someone gets on a dummy access point ( MSCHAP is quietly opened - then it is used by the vast majority due to the prevalence of Active Directory - and the user name / password is extracted).
- This feature is disabled via Configuration Manager, but for this you need to either hand over the phone to an IT person, or send the profile to the user remotely and make sure that he has applied it.
- For the company, let's add about “super speeds” 802.11n and MIMO in smartphones and tablets. No comments ( Amazon authorship )

But, as the author of several popular financial pyramids likes to say, this was all a saying ...
An article on the Apple support site “recommendations for setting up WiFi for iOS devices” reveals interesting details.
- iOS doesn't like hidden network names. My iTouch 4G on iOS5 works quite calmly with a hidden network, but I heard complaints from others.
- Wide channels (40MHz) are not supported.
- On the one hand, well and right, there is nothing to be mixed with wide channels in 2.4GHz. There are exactly one of them there, in most cases there is more interference than sense. But why aren't 40MHz in 5GHz supported? The answer to the picture above is 20MHz, and so enough for the eyes.
- And what about the rest of the devices in the corporate network where the wide channels are turned on (if you use, say, iPads on 5GHz, as some fashion retailers do)? The only answer is to suffer. Parallel to HT Protection, in 802.11n there is a 40MHz compatibility mode with 20MHz, which also reduces network performance in similar ways (pre-frames, etc.). How much - depends on many parameters, mainly on how often the iPad will require air - can not be accurately predicted.
- When you connect to a Wi-Fi network, your device checks for an Internet connection by trying to connect to the Apple server and pull a specific web page from there. If this page is not available, it is assumed that we are sitting on a hotspot and pops up a browser window asking for a login, while the system no longer tries to climb into the network. Conveniently. As shown by the recent incident with IOS6, in the absence of access to this page - there is no access to the network.
An interesting note with a selection of Cisco TAC impressions of iOS support
- OKC support doesn’t really bother anyone if you don’t use softphones or you have iOS6 devices (802.11r will successfully replace OKC).
- If you do not have access to the Internet for more than 20 minutes, the device tries to reconnect or find another network (maybe it’s lucky there).
- TAC adds another brushstroke to a picture with hidden SSIDs - if there are two or more SSIDs, the device will always connect to open networks, even if you intentionally select a profile with hidden SSIDs.
- Devices (especially the iPad) have significant transmission power, but worse reception sensitivity (due to home specifics).
- A variety of shoals are possible when the speed is turned off 11Mbps (which requires, in fact, the inclusion of 802.11b support). I did not observe such problems on my device with IOS4 / 5, most likely - these are remnants of older versions. However, some Motorola partners have confirmed that they have encountered such a problem with customers.
- The article is dated July 2012, possibly with the release of iOS6 some of the problems are gone. Unfortunately, Apple is not very generous with details.
Bonjour protocol (service announcement, AirPlay video transmission, etc.) is not routed. Those. devices must be in the same VLAN (which is normal at home). However, in a corporate environment, the chances of connecting a wired AppleTV and a wireless iPhone to the same VLAN are minimal (if you have the right network design).
- However, the popularity of AppleTV has led to the fact that many vendors have introduced so-called. Bonjour Gateway is essentially an analogue of DHCP Relay, but for Bonjour, and now they even measure its performance, showing diametrically opposite (these are two different links) results :). This feature is supported by Cisco, Aruba, Aerohive. Motorola does not support Bonjour Gateway in a “pure” form - other options for forwarding L2 to L3 are offered - from the proprietary MiNT to L2TPv2 / 3 and PBR.
- There are still trifles (only 1 WEP key is supported, etc., devices do not connect to networks with WMM disabled ), but they shouldn’t really bother anyone. no such configurations should be used in corporate networks.
Total
Whether you consider iOS suitable for the corporate environment or do not consider - but somehow it is necessary to live with it. Let's summarize everything in the form of recommendations for iOS support in a corporate wireless network.
Ideally, we want to give people access to the Internet and nothing more. If you need mail and so on - it is much easier (from the Wi-Fi point of view) to force all these devices to enter the corporate network through a VPN, than
- In this case, it is enough to create a guest network, get on it https hotspot with RADIUS authorization, tied to the corporate user base (AD or other). I already wrote about the reasons for mandatory authentication on hotspots here .
- It is enough to deploy the network in 2.4GHz in the mode of total guest access for the whole row: support b / g / n-speeds (of course, if possible, disable low speeds 1,2,5,5Mbps), channels 20MHz, non-hidden SSID, etc. .
- A prerequisite for enabling i-device access is to use a security profile that blocks the ability to accept someone else's certificates (protection against phishing and disclosure of corporate credentials).
If you plan to support corporate applications in the corporate network - you should think
- Do we transmit synchronous traffic (voice, video)? Many schools in the US are now using iPads to transfer educational videos, for example.
- If not, we follow the recommendations of the previous paragraph, but instead of hotspot, we configure 802.1X, blessing, options for the sea. Since the average user is frightened by the word "RADIUS" - it is much easier to convince him to apply the security profile by giving it along with the network settings ("click here and everything will be configured by itself").
- You may have to play around with the speed settings on the network (if you have optimized) and include some rates.
- Make sure that the website www.apple.com/library/test/success.html has access from your network, or set up a redirect to your web server that will convince iPhones that everything is in order. :)
- If voice and video transmission is planned, everything becomes more complicated.
- Traditionally, such networks are built in 5GHz, since to provide QoS in "contaminated" 2.4 is very problematic. The best way out is to state directly that the work of streaming applications for iPhone4S and below is not guaranteed and is not supported, and then transfer iPads and other new devices to 5GHz.
- At the same time, wide channels should be considered if they are used in 5GHz. Testing will help assess the performance drop caused by the appearance of iPads on such a network.
- For fast roaming (if required), it makes sense to upgrade users to iOS6 (there is a suspicion that 802.11k / r is a chip of the OS, not chipsets, though) and configure them in your wireless infrastructure. Otherwise, at least enable PMK Caching.
- If Bonjour is planned to be used, we analyze traffic flows and do L2 forwarding over L3 (or enable and configure Bonjour Gateway). Very well, if you can do a selective forvarding on ACL, so as not to send all traffic, but it depends on the capabilities of the existing network equipment.
- We thoroughly test the behavior of devices of different generations and different firmware at different speeds. Typically, high-performance WLANs disable 18Mbps and below. In this case, you will have to test which speeds can be disabled - and which ones to leave. Perhaps, together with special requirements for signal strength, this will entail changes in radio planning, which you need to be prepared for.
Security is a great NSA document . I think they can be trusted ( if this is not a deliberate disinformation of a potential enemy ).
')
In conclusion, I note that Apple in terms of Wi-Fi has made a significant breakthrough. If the first firmware for the iPhone was so crooked that they cut the Cisco network tightly , now everything is much better. I still cannot call iOS-devices "corporate", but, in general, it is already possible to support iOS in the corporate network. If you are careful about your appetites and promises. (This is not related to fleet management and BYOD in general!)
Share opinions. Of particular interest is the experience of people supporting 50+ devices.
Source: https://habr.com/ru/post/157233/
All Articles