Electronic fingerprinting using Internet browser
The reason for writing this post was this question , alas, accounting has the status of read-on => it is impossible to leave comments. And the subject slightly outgrew the question itself.
The question of user identification is solved by the banal htpasswd, if users are counted on the fingers of their hands; before the form of the login means of the resource, if this very resource of the thumb and fingers is not enough; authorization of access to sections of a resource is solved again by means of the resource itself.
Authentication of the host (and its subsequent authorization in access), provided it is impossible to bind to a static IP address, as noted in the comments of the question, is resolved by certificates.
But the head does not give hands to rest: it is necessary to find an alternative way.
Googling, quickly found such a project and this document (pdf 500Kb) . My frail English cannot adequately translate it completely, and the volume discourages the desire.
The Electronic Frontier Foundation conducted, in my opinion, a vast experiment, asking how uniquely to identify the browser.
')
So what can be found in the document itself
It is impossible to define uniqueness for any one parameter due to various limitations of the browsers themselves, designed so as to maximize the security and privacy of the user.
In fingerprinting, the uniqueness of a print is determined by the search for patterns and their location to each other. I will not give a hand to cut off that it is infa 100, this is my idea. The link to the wiki , by the way, the article in English will be updated.
Similarly, in the panopticlick project, all visitors were identified by several datapoints. Merging these lines creates a complete imprint.

It should be noted that disabled javaskript and cookies are also indicators that determine the “papillary” pattern.
The experiment took place from January 27th to February 15th, 2010.
The audience was attracted from various resources, both thematic and news partners, and social networks.
For each visitor of the site that passed the “test me” link, the following data was recorded on the methodology (fingerprint), IP address, and a 3-month cookie was also left.
An exception was made for intermittent imprint-ip pairs, and the cookies left were different.
That is, the triplet fingerprint1-aypi1-cookie1 and fingerprint1-aypi1-cookie2 were considered unique and were considered as identical systems for one firewall. (two android one for example)
As a result, out of 1,043,426 tested, 470,161 unique fingerprints were identified.
Were also considered cases when ip addresses changed. Of the 321 155 browsers that allowed Oreo to be recorded, 14,849 (4.6%) were identified. They are taken as a marginal statistical error.
Total 83.6% of unique prints, 8.1% which cannot be unambiguously attributed to the first and 8.2% which occurred 2 to 9 times.
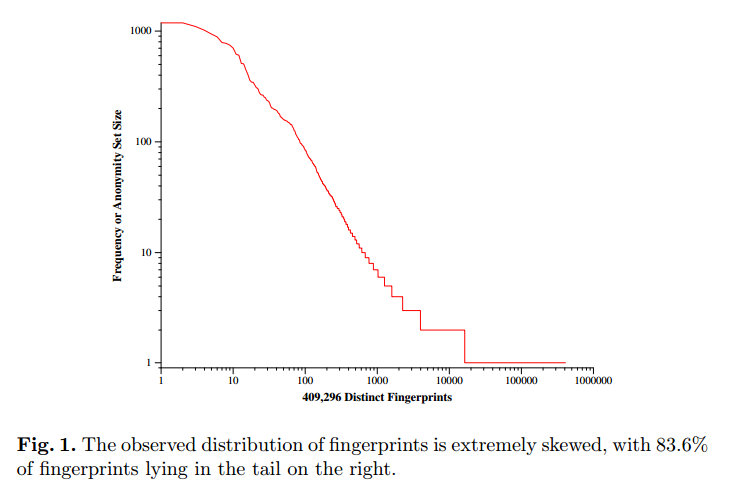
In addition, the article has distribution charts for different browsers from mobile to desktop. And among desktop prints are usually more unique than among mobile
On a global scale, EFF did not conduct extrapolation, one of the reasons was the fact that the respondents were mostly technically savvy and were more responsible for safety issues.
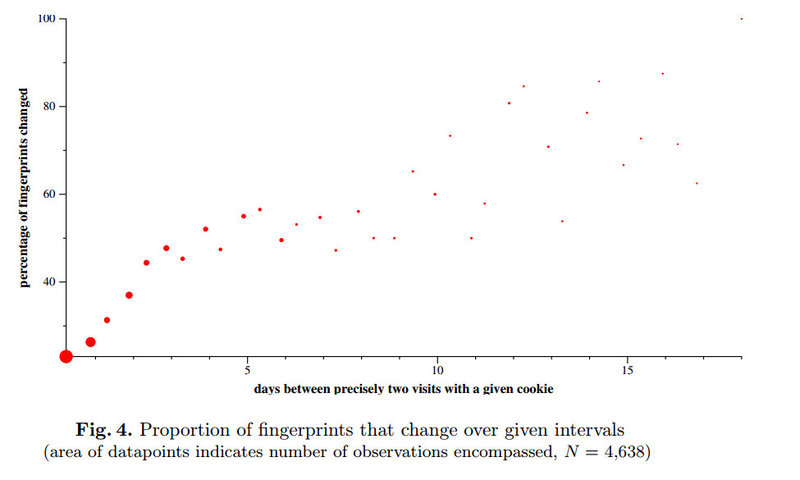
This aspect was tracked by the same oreo. The factors affecting the evolution of fingerprints are many: upgrading the browser version, changing the settings of cookies and jay es, installing fonts, locking flash. The authors warn that their data are probably somewhat exaggerated, because during the experiment, they encouraged participants to experiment (forgive the tautology) with these parameters in order to provide data on the traceability of these changes.
Actually graph obtained data:
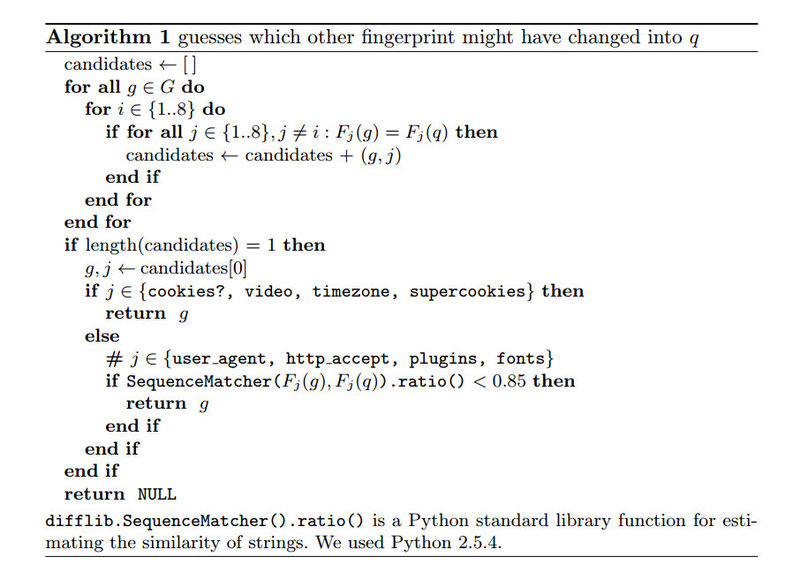
And the algorithm of guessing changes of a print developed by them:
 P
P
Interestingly, “tightening the screws”, to a certain extent, has the opposite effect. since in such a statistical way you will stand out more from the main mass. those. Your print is more unique. This paradox will be valid until this very mass starts to apply them.
What we have in the dry residue?
Browser fingerprinting turned out to be a very effective technique, although not the most stable. But as the data points increase, reliability increases.
And if used in a complex with oreo, ip and super cookies (flash, web sequel and lokol storazh), a very good user traceability tool is obtained.
And again considerations privacy of users. It is also noted that the use of Tor, gives a kind of gloves.
And calling browser developers on the possibility of collecting data points through various APIs
PS As you may have guessed, the translation is very free and not complete. C rather even squeeze. For what I apologize in advance.
The question of user identification is solved by the banal htpasswd, if users are counted on the fingers of their hands; before the form of the login means of the resource, if this very resource of the thumb and fingers is not enough; authorization of access to sections of a resource is solved again by means of the resource itself.
Authentication of the host (and its subsequent authorization in access), provided it is impossible to bind to a static IP address, as noted in the comments of the question, is resolved by certificates.
But the head does not give hands to rest: it is necessary to find an alternative way.
Googling, quickly found such a project and this document (pdf 500Kb) . My frail English cannot adequately translate it completely, and the volume discourages the desire.
The Electronic Frontier Foundation conducted, in my opinion, a vast experiment, asking how uniquely to identify the browser.
')
So what can be found in the document itself
- As the real good guys, the EFF assigned a separate chapter to the privacy and ethics of such tools on the Internet (which we will successfully omit here).
- Methodology
- Mathematical component (due to their incompetence in this matter, study independently
- Actually the process of collecting information and its processing
- results
- How such a fingerprint is suitable as a global identifier (again, mathematics)
- Consistency and reliability of the print
- Countermeasures
- Conclusion
Methodology
It is impossible to define uniqueness for any one parameter due to various limitations of the browsers themselves, designed so as to maximize the security and privacy of the user.
- It is impossible to get a unique MAC address, by the way, if desired, and it is spoof
- the user-agent itself is not unique and is also easily replaced.
- cpuid do not call etc. hardware data
In fingerprinting, the uniqueness of a print is determined by the search for patterns and their location to each other. I will not give a hand to cut off that it is infa 100, this is my idea. The link to the wiki , by the way, the article in English will be updated.
Similarly, in the panopticlick project, all visitors were identified by several datapoints. Merging these lines creates a complete imprint.

It should be noted that disabled javaskript and cookies are also indicators that determine the “papillary” pattern.
Data collection and processing
The experiment took place from January 27th to February 15th, 2010.
The audience was attracted from various resources, both thematic and news partners, and social networks.
For each visitor of the site that passed the “test me” link, the following data was recorded on the methodology (fingerprint), IP address, and a 3-month cookie was also left.
An exception was made for intermittent imprint-ip pairs, and the cookies left were different.
That is, the triplet fingerprint1-aypi1-cookie1 and fingerprint1-aypi1-cookie2 were considered unique and were considered as identical systems for one firewall. (two android one for example)
As a result, out of 1,043,426 tested, 470,161 unique fingerprints were identified.
Were also considered cases when ip addresses changed. Of the 321 155 browsers that allowed Oreo to be recorded, 14,849 (4.6%) were identified. They are taken as a marginal statistical error.
results
Total 83.6% of unique prints, 8.1% which cannot be unambiguously attributed to the first and 8.2% which occurred 2 to 9 times.

In addition, the article has distribution charts for different browsers from mobile to desktop. And among desktop prints are usually more unique than among mobile
Global ID
On a global scale, EFF did not conduct extrapolation, one of the reasons was the fact that the respondents were mostly technically savvy and were more responsible for safety issues.
Consistency and reliability of the print
This aspect was tracked by the same oreo. The factors affecting the evolution of fingerprints are many: upgrading the browser version, changing the settings of cookies and jay es, installing fonts, locking flash. The authors warn that their data are probably somewhat exaggerated, because during the experiment, they encouraged participants to experiment (forgive the tautology) with these parameters in order to provide data on the traceability of these changes.
Actually graph obtained data:

And the algorithm of guessing changes of a print developed by them:
 P
PCountermeasures
Interestingly, “tightening the screws”, to a certain extent, has the opposite effect. since in such a statistical way you will stand out more from the main mass. those. Your print is more unique. This paradox will be valid until this very mass starts to apply them.
Conclusion
What we have in the dry residue?
Browser fingerprinting turned out to be a very effective technique, although not the most stable. But as the data points increase, reliability increases.
And if used in a complex with oreo, ip and super cookies (flash, web sequel and lokol storazh), a very good user traceability tool is obtained.
And again considerations privacy of users. It is also noted that the use of Tor, gives a kind of gloves.
And calling browser developers on the possibility of collecting data points through various APIs
PS As you may have guessed, the translation is very free and not complete. C rather even squeeze. For what I apologize in advance.
Source: https://habr.com/ru/post/156909/
All Articles