Interception of HTTPS traffic between an Android device and an external server
Sometimes it is curious to see that various Android applications are being sent back and forth via HTTP and HTTPS protocols. Sometimes, even when developing your own software, it is convenient to see all traffic in real time. To accomplish these tasks, many good programs have long been invented, such as, for example, Charles or Fiddler2 . In fact, there are many more of them, only the two above give the opportunity to view not only HTTP, but also HTTPS.
Difficulties begin when it comes to intercepting traffic between an Android device and an external server. In the case of unencrypted (HTTP-protocol) traffic, everything is very trivial (here is the instruction ) - we allow Fiddler2 external connections, in Android we set the proxy server address of our machine with Fiddler2 - and voila, everything works. But it took me a little longer to set up HTTPS traffic interception.
Theory
So what is the difficulty? The fact that when using the HTTPS protocol, the client by default checks whether the server to which it is connected is really necessary. For this purpose certificates are used. And now, at the real server, this certificate, of course, is also real and corresponds to the open URL, but our proxy does not. To solve this problem in desktop operating systems in such cases it is possible to generate a fake certificate into Fiddler2, import it into trusted ones - and now the client will always believe that the connection with Fiddler2 is completely safe. Unfortunately, with a mobile device such a light earmuffs did not pass.
First, there is no possibility to import an external certificate in Android versions younger than 4.0. There are some non-trustworthy options with rutted devices - but this is not our way.
Secondly, even Android version 4.0 cannot import the Fiddler2 certificate. The fact is that the certificate generated by default does not meet any kind of Android security criteria and is not installed. It needs to be generated in a special way.
Thirdly, it’s not even the fact that all programs in a row will immediately trust a fake certificate. There are nuances.
')
Practice
- We take the device with Android version 4.0 or higher. No, a device with 2.3 will not work. Yes, emulator version 4.0 will work.
- Install the latest version of Fiddler2 on your computer.
- We install special libraries generating Android-compatible security certificate from here .
- We export the security certificate from Fiddler2 (“Tools-> Fiddler Options-> HTTPS-> Export root certificate to Desktop”). We put on the flash drive, in the root (well, or on the emulator, if you use it).
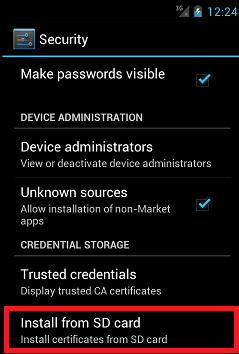
- On Android, we add a security certificate to the trusted ones (“Settings> Security> Install from SD card”)
- We start Fiddler2, we allow external connections in settings
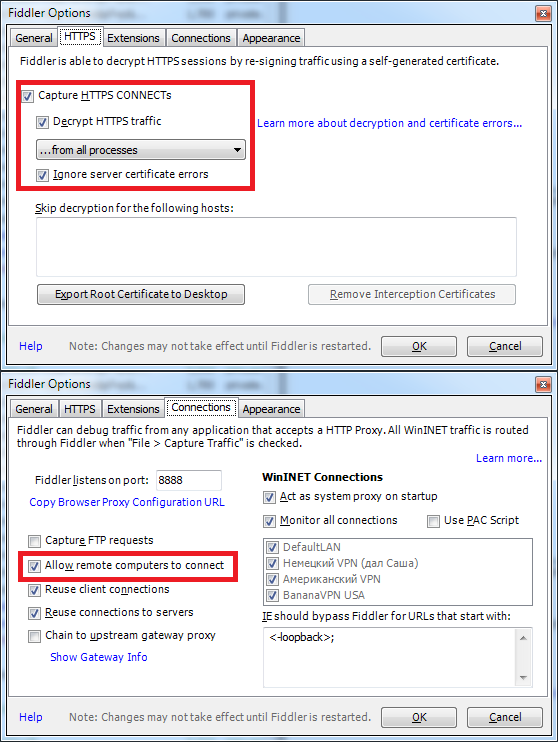 .
. - On Android, in the settings of the network, we register the address of our desktop machine with Fiddler2 as a proxy.

- On Android, open the browser, enter google.com - and see the request with the answer in the Fiddler2 window.
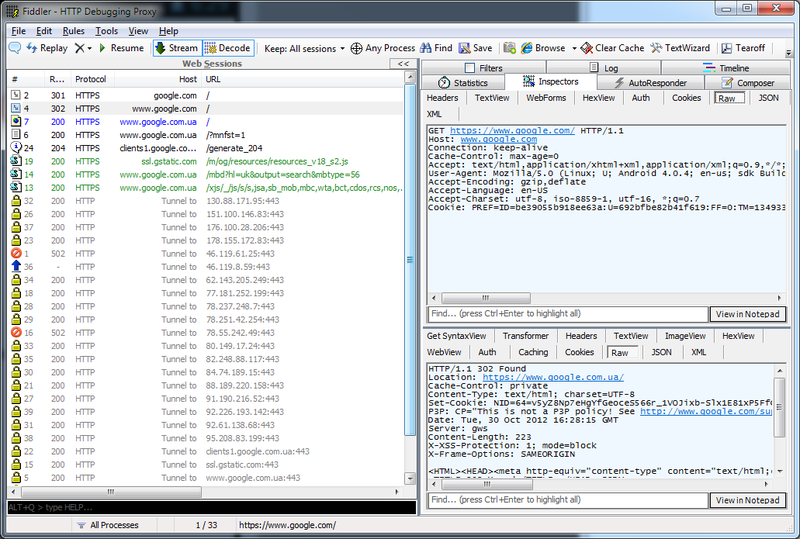
So, with the browser turned out. Unfortunately, not all programs are as trusting as the browser. For example, in my own software, where I use the Apache HTTP Client , the method did not work - the Apache client spat on trusted OS certificates. In this case, I had to disable this check manually, in this way:
Protocol.registerProtocol("https", new Protocol("https", new EasySSLProtocolSocketFactory(), 443)); where EasySSLProtocolSocketFactory is taken from here and allows trust to any certificates.
Not safe, just for debugging!
After that, the traffic of my program was also successfully displayed in Fiddler2.
Source: https://habr.com/ru/post/156711/
All Articles