Checked electronic voting

In recent days, there were three posts on Habré, dedicated to e-voting:
FIDO / FTN distributed voting system
Pro electronic secret voting
Open electronic voting (proof by contradiction) ,
but a complete solution providing secret e-voting, the results of which every voter could verify, was not found.
I think there is such a solution.
')
Task
Electronic voting must meet the following conditions:
- Anonymity - no one should be able to relate a specific vote to a specific voter.
- Openness - voting results should be available to everyone.
- Verifiability - every voter should be able to check his vote. Anyone should be able to calculate the final results and check for the absence of “stuffing”.
The key technology for solving the task is a blind signature - a way to sign the body of an encrypted message without decrypting it.
Voting procedure
- The voter generates a pair of keys and registers his public key with the CEC. As a result of registration, a list of voter addresses is laid out in public. Something like this:
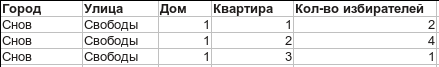
Already at this stage, everyone can check that he is on the lists, another 146 people were not registered in his apartment, and a new microdistrict did not grow up next night. - The voter generates his own bulletin of the form:
Then he encrypts the ballot (the key can be any), signs it with his private key and sends it to the CEC - CEC verifies the signature. Making sure that this signature is on the list of voters, signs the ballot with a blind signature and sends it to the voter. After that, the CEC in the public voter list increments the count of voters:
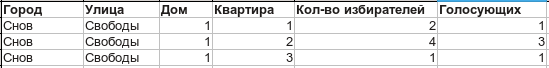
Here the voter can make sure that he is counted. - The voter decrypts the ballot, verifies the CEC’s signature and sends the decoded, signed by the CEC ballot back to the CEC.
- The CEC receives the bulletin, checks the validity of its signature, encrypts it, and immediately puts in a shared pair (random number of the bulletin (from point 2), encrypted bulletin). The ballot is encrypted by the CEC, the encryption key is kept secret until the end of the vote.
- After the voting is completed, the key to the cipher of the ballots is published.
What do we have as a result?
In general, there are:
- The list of voter addresses from paragraph 3. Everyone can check the number of voters, make sure there are no “stuffing”.
- The list of ballots from paragraph 5. Each voter can find his vote by a random number, which he generated at the stage of creating a ballot. Anyone can count the voting results and compare the number of ballots with the number of voters who have voted.
None of the stages of the CEC or anyone else can match the voter and his vote. In the voting process, you can track changes in public lists, identifying suspicious dynamics of changes. Each voter can check if his vote is correctly taken into account. Anyone can independently count the voting results. Alarms can be revealed.
What do you think will work?
Upd:
Thank you all for the feedback!
mihaild painted the points more clearly:
1. The voter sends to the CEC key IzbPub1 and its address.
2. A voter makes a bulletin (random number + voice), encrypts it with a key Izb2, signs it with a key IzvPriv1, sends it to the CEC.
3. The CEC verifies the signature using the key IzPub1, blindly signs the encrypted ballot with the KeyPriv1, sends the result back to the voter.
4. The CEC notes that it received a voice from the corresponding address.
5. A voter, using an encrypted signed bulletin and a key F2, receives an unencrypted ballot signed by CicPriv1.
6. The voter sends the signed unencrypted ballot back to the CEC.
7. The CEC verifies the signature with the CicPub1 key.
8. The CEC publishes a pair (number, ballot, encrypted CycPub2) and takes into account the voter's vote.
9. At the end of the election, the CEC publishes CECPriv2.
vics001 noted that the commutation capability of signature operations and the masking factor can lead to the creation of several fake ballots.
The way out - at the second stage, the hash of the previous part is added to the bulletin, which will make the selection of the masking factor unreal.
edhell correctly noted - in the first paragraph, I did not indicate that registration takes place offline with the presentation of a passport. This is a one-time procedure that allows you to vote in the future, and can be easily combined with obtaining a passport and changing registration.
Source: https://habr.com/ru/post/156423/
All Articles