Tagging EXE files without damaging the digital signature

Hello!
We want to tell about our experience in the study of digital signatures of Windows PE files and the possible use of their features for their own purposes. If you are interested in technical details or just reading about what seems to be well-known things, welcome to Cat.
User Account Control
Many of you know that with the advent of Windows Vista, there was such an interesting thing called UAC (User Account Control). This mechanism is designed to increase security, and its essence is to restrict application access to critical parts of the operating system. However, the opportunity to get to these parts still exists, and the user has control over this.
')
Any Windows application can contain a manifest - an XML file used by Windows when launching the application. In this manifest, the requirement to launch an application with elevated privileges can be described, and in this case, when the application is launched, the user will see the same UAC window asking whether to trust the application and allow it to start with maximum permissions?
In order to make the task easier for the user at this stage, and to allow developers to be confident in the integrity and originality of the transferred files, Microsoft offers the authors of legal and harmless software to use digital signatures. They certify the author, and, more importantly, the authenticity of the original file.

Seeing a launch request with information about a verified publisher, the user can be sure that the contents of the executable part of this file have not changed and can be run with a clear conscience (if he, of course, trusts this author). However, when requesting to launch an application from an unverified publisher, it is worth thinking about, analyzing possible causes and consequences.
Closer to the topic
But what if we (the authors of these applications) want to transfer to them any additional information that will be known only at the moment of downloading? After all, any change to the file automatically makes the digital signature invalid. What options do we have?
- Add the required data to the name of the file to be transferred, and redirect such requests to a single physical file via a regular server via regular expressions.
+ easy to implement;
+ the file internals remain intact and the signature is always correct;
- you can send only a small set of data (for example, several identifiers);
- at file renaming the information disappears. - Modify the data inside the file and re-sign it upon release.
+ you can transfer any amount of data;
+ when you rename nothing is lost;
- re - signing is a very long process if we are talking about the return of hundreds of large (100 MB +) distributions of games per second, as in our case. - Change the data inside the file and DO NOT re-sign it, while maintaining the correct digital signature.
+ you can transfer any amount of data;
+ when you rename nothing is lost;
+ no need to re-sign the file;
- this is impossible (or possible?).
Some theory
Below is the structure of a Windows PE file with information about which parts of it a digital signature is formed, and which blocks are skipped in this process.
Also shown is the digital signature block format ( PKCS # 7 structure) used by Microsoft.
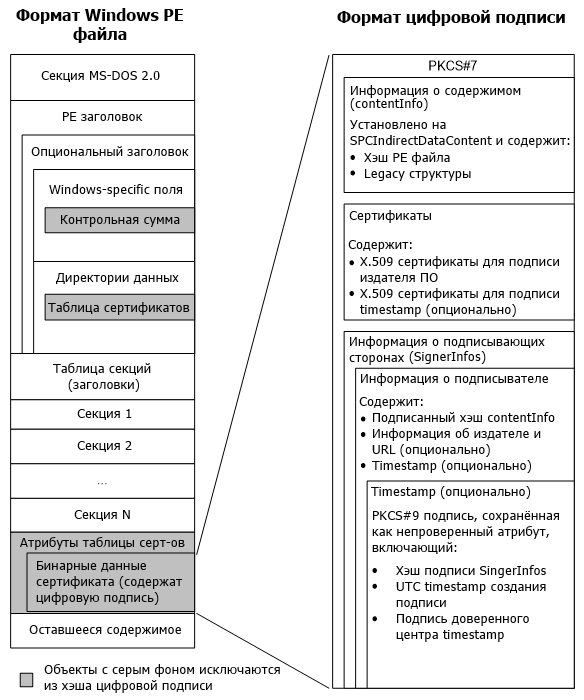
The key point in this scheme is the presence of blocks that are excluded when generating and verifying a digital signature. These blocks are described by the simplest C structures:
The “Certificate Table” in the “Data Directories” section is an IMAGE_DATA_DIRECTORY structure:
typedef struct _IMAGE_DATA_DIRECTORY { DWORD VirtualAddress; DWORD Size; } IMAGE_DATA_DIRECTORY, *PIMAGE_DATA_DIRECTORY; Where:
- VirtualAddress - a direct pointer to the attributes of the table of certificates in the PE file;
- Size - the size of this block in the PE file.
The “Certificate Table Attributes” is a WIN_CERTIFICATE structure:
typedef struct _WIN_CERTIFICATE { DWORD dwLength; WORD wRevision; WORD wCertificateType; BYTE bCertificate[ANYSIZE_ARRAY]; } WIN_CERTIFICATE, *LPWIN_CERTIFICATE; elements of which contain the following values:
- dwLength - the size of the binary data section of the certificate;
- wRevision - the used version of the WIN_CERTIFICATE structure;
- wCertificateType - set to 0x0002 for digital signatures of PE files. The value is defined in Wintrust.h as WIN_CERT_TYPE_PKCS_SIGNED_DATA;
- bCertificate is a dataset containing a digital signature in the format PKCS # 7.
When a PE file is signed, the attribute section of the certificate table is always placed at the end of the file (the “Remaining Content” block is absent). Knowing this feature, you can crank up a little trick with very attractive results.
Impossible is possible
The focus is this: the size of the section described in IMAGE_DATA_DIRECTORY may differ from the actual size of the WIN_CERTIFICATE structure , and when checking the digital signature, the entire section is excluded, the size of which is described in IMAGE_DATA_DIRECTORY. At the same time, manually added content to this section is no longer part of the digital signature and, in fact, can contain any data set. Thus, you can easily add any data to the contents of the “Certificate Table Attributes” block by first changing the section size in the IMAGE_DATA_DIRECTORY structure without damaging the file’s digital signature. Do not forget about file padding up to a size multiple of 8 bytes.
You should understand the possible consequences of using this method, keep in mind the type of data transferred, the volume, the possible processing of them, and the potential holes associated with it. It is in your interest to transfer there only such information that can be painlessly
“Of course, what about the checksum of the PE file?” You ask. I hasten to reassure you - it does not play any role when starting and running regular EXE files. The checksum is checked only on critical system files, for example, the System File Checker service (for diagnosing missing or damaged system files) is oriented towards it.
As a conclusion: who uses it and how?
This feature is used by Google when distributing its products through the automatic Google Omaha update. You may have noticed that when you download Google Chrome or Google Earth, you are prompted to make some settings before downloading, for example, install the Chrome browser with Earth. These settings are transmitted using the distribution tagging - the process of adding data to an EXE file, which Omaha subsequently processes on the user's local machine.
It is also convenient to use this opportunity in various partner networks - distribution of distributions with partner tracking - the need for different companies.
The mechanism for uploading files from a web server using this feature can be implemented using a self-written nginx plug-in, a virtual file system based on FUSE, or some other more exotic way (tell us in the comments if you’ve come up with your own version).
Information on digital signatures of PE files can be found in this document: Windows Authenticode Portable Executable Signature Format .
Source: https://habr.com/ru/post/155365/
All Articles