Windows 8 - changes to the network file permissions model
Good afternoon, habrovchane. During testing of Windows 8 RP in a corporate environment, I was surprised to find that Microsoft had significantly reworked the model of network access to file resources. This is one of the most conservative subsystems of Microsoft operating systems. Distribution of accesses through security groups has not changed since at least Win 2000 Server, and now ... As one character used to say, “I feel a confusion close to concern ...” Well. Armed with a magnifying glass and go explore the details.
Folder sharing itself contains minimal changes in the interface and does not cause problems. The only thing I want to draw attention to is that in previous versions of Windows, when you tried to rename the shared folder, you were strongly warned that in this case the network access would be covered with a copper basin. Eight, like an obedient harem wife, will rename you a folder without a single objection ... but the network access will nevertheless be closed. Be careful.
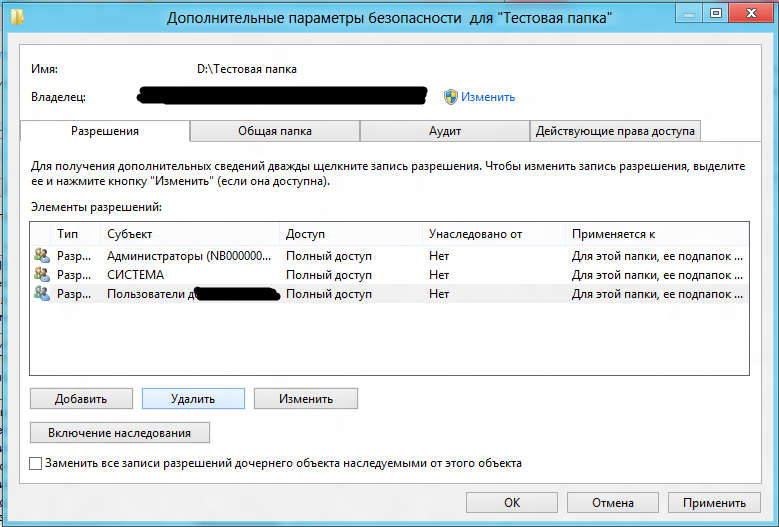
Go to the folder properties: Security - Advanced.
')
Changes that immediately catch the eye: now in the access rights model there are different subjects and objects. Subjects include users, security groups, computers, and embedded security subjects. Objects are the actual places of the application of access rights.
The tick of inheritance is replaced by a large “Enable / Disable Inheritance” button. The meaning of this substitution is unclear.
The owner of the folder now does not have a separate tab and is set by clicking on "Edit" in the upper part of the window.
The “Shared Folder” was added to the list of tabs. On it you can see the permissions on the network access, without interrupting the process. This is a plus - previously, for this, you had to completely exit the Security dialog or open another property window.
The “Audit” tab has no particular changes, unless it immediately warns that you can enable auditing only if you have the appropriate rights.
Well, the last tab, "Valid access rights." As the name implies, this is a testing ground for checking final access permissions. Specify access parameters and look at the result. Subjectively, the new window is much more convenient than analogs in previous versions of Windows.
Now we will add a new user and see what is being offered to us:

Click "Select a subject" and standardly specify the desired domain user or group. Permissions and prohibitions can no longer be specified in one window, they are set alternately by selecting the corresponding item in the menu. This, in my opinion, is uncomfortable. There is enough space in the window, and it was possible to freely implement both in one field.

The list of permissions does not bring anything unexpected, so go to the most delicious. In addition to these standard clauses, Microsoft has introduced a policy trigger system. And here is where to turn. At the bottom of the permissions window there is a conditions zone. Add a new condition and see the following structure:
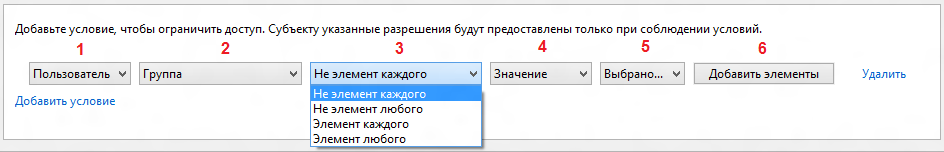
Consider the function fields:
1. Determines for which subject the rule is being formed. Accepts values:
User - user account or security group;
The device is the computer from which the input is made.
2. Group - does not matter. Apparently, reserved for the future.
3. Elements - provides powerful functionality, but is very crookedly translated. Although I admit that there is no adequate translation in Russian. This field describes the logical operation that will be performed on the selected values. According to the meaning corresponds to the following:
4. Value is reserved.
5. Selected - this field indicates the elements on which the operation is performed.
6. Button for adding element values.
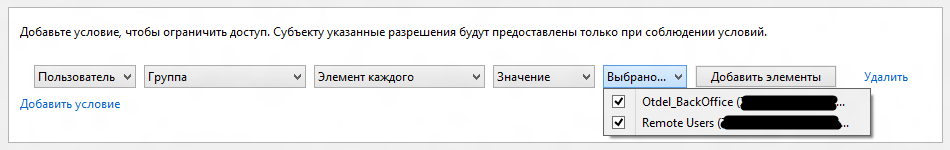
This mechanism allows you to grant or deny access based on cross-membership in several groups, or, conversely, the lack of them. So, for example, the following condition will skip only members of the test group who are employees of the back office and are members of the Remote Users:
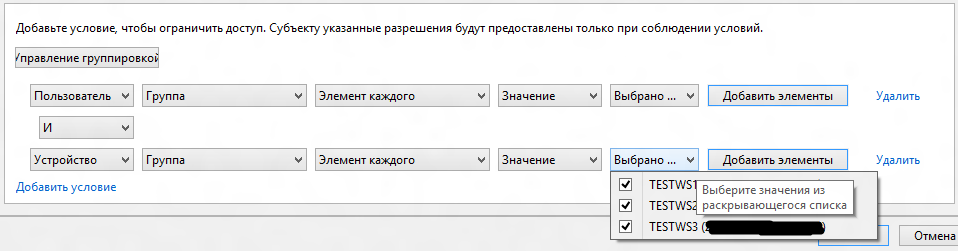
Add another condition, this time for the device. As can be seen from the screenshot, individual conditions are also associated with logical operations. Having included several computers in the list of values, we will get a more sophisticated structure - now, access to the files will be received only by the back-office employees, who are in the Remote Users, and will only come from those machines that we have listed. Even with a password leak, access to data from a foreign machine will fail.
And simply replacing the logical operation between the conditions from AND to OR, we get a scheme in which trusted employees can come in from anywhere, while the rest, not so trusted, can be obtained only from special computerswith a machine gun . Possible uses are limited only by your imagination.
I want to note that if there are more than two conditions, then logical operations between them are performed sequentially, although the scheme becomes hard to read and slips into chaos. Another innovation comes to the rescue - the ability to group conditions, and thus set the sequence for performing logical operations. Once you have created the second condition, the "Manage Grouping" button appears. By clicking on it, we’ll see checkboxes next to each grouping rule that allow you to select and link two conditions:

Now permission to access can take a completely furious form:

True, again, not without a spoonful of tar. If you apply the created rule, and then go back to look at it, then you may or may not see the grouping levels. The system shows / does not show them completely arbitrarily, for some internal reasons. Moreover, the grouping levels themselves do not disappear anywhere, but it is easier to pull down all the conditions and draw again than to remember how they should relate there.
Summing up, I believe that the new model of access rights was a success. It was not without drawbacks and controversial decisions, but it provides complete functionality with wide and interesting features. The three levels of nesting operations (inside conditions, between conditions and between groups of conditions) are clearly redundant, and, hand on heart, I cannot think of a plausible situation in which I would need all three. We assume that this is a growth stock for the future. The access model was described using the example of Windows 8, but I think that in Windows Server 2012 we will see the same mechanisms, only aggravated by the file server role - quotas, the system for classifying files and access categories. Building file resources becomes even more interesting.
Folder sharing itself contains minimal changes in the interface and does not cause problems. The only thing I want to draw attention to is that in previous versions of Windows, when you tried to rename the shared folder, you were strongly warned that in this case the network access would be covered with a copper basin. Eight, like an obedient harem wife, will rename you a folder without a single objection ... but the network access will nevertheless be closed. Be careful.
Go to the folder properties: Security - Advanced.

')
Changes that immediately catch the eye: now in the access rights model there are different subjects and objects. Subjects include users, security groups, computers, and embedded security subjects. Objects are the actual places of the application of access rights.
The tick of inheritance is replaced by a large “Enable / Disable Inheritance” button. The meaning of this substitution is unclear.
The owner of the folder now does not have a separate tab and is set by clicking on "Edit" in the upper part of the window.
The “Shared Folder” was added to the list of tabs. On it you can see the permissions on the network access, without interrupting the process. This is a plus - previously, for this, you had to completely exit the Security dialog or open another property window.
The “Audit” tab has no particular changes, unless it immediately warns that you can enable auditing only if you have the appropriate rights.
Well, the last tab, "Valid access rights." As the name implies, this is a testing ground for checking final access permissions. Specify access parameters and look at the result. Subjectively, the new window is much more convenient than analogs in previous versions of Windows.
Now we will add a new user and see what is being offered to us:

Click "Select a subject" and standardly specify the desired domain user or group. Permissions and prohibitions can no longer be specified in one window, they are set alternately by selecting the corresponding item in the menu. This, in my opinion, is uncomfortable. There is enough space in the window, and it was possible to freely implement both in one field.

The list of permissions does not bring anything unexpected, so go to the most delicious. In addition to these standard clauses, Microsoft has introduced a policy trigger system. And here is where to turn. At the bottom of the permissions window there is a conditions zone. Add a new condition and see the following structure:

Consider the function fields:
1. Determines for which subject the rule is being formed. Accepts values:
User - user account or security group;
The device is the computer from which the input is made.
2. Group - does not matter. Apparently, reserved for the future.
3. Elements - provides powerful functionality, but is very crookedly translated. Although I admit that there is no adequate translation in Russian. This field describes the logical operation that will be performed on the selected values. According to the meaning corresponds to the following:
- Not an element of each: AND-NOT operand, the subject should not be included in all selected elements at once, but can be included in one of the elements;
- Not an element of any: operand OR NOT, the subject should not be included in any of the selected elements;
- Element of each: operand AND, the subject must be included in all selected elements;
- Element of any: operand OR, the subject must be included in at least one of the selected elements;
4. Value is reserved.
5. Selected - this field indicates the elements on which the operation is performed.
6. Button for adding element values.
This mechanism allows you to grant or deny access based on cross-membership in several groups, or, conversely, the lack of them. So, for example, the following condition will skip only members of the test group who are employees of the back office and are members of the Remote Users:

Add another condition, this time for the device. As can be seen from the screenshot, individual conditions are also associated with logical operations. Having included several computers in the list of values, we will get a more sophisticated structure - now, access to the files will be received only by the back-office employees, who are in the Remote Users, and will only come from those machines that we have listed. Even with a password leak, access to data from a foreign machine will fail.

And simply replacing the logical operation between the conditions from AND to OR, we get a scheme in which trusted employees can come in from anywhere, while the rest, not so trusted, can be obtained only from special computers
I want to note that if there are more than two conditions, then logical operations between them are performed sequentially, although the scheme becomes hard to read and slips into chaos. Another innovation comes to the rescue - the ability to group conditions, and thus set the sequence for performing logical operations. Once you have created the second condition, the "Manage Grouping" button appears. By clicking on it, we’ll see checkboxes next to each grouping rule that allow you to select and link two conditions:

Now permission to access can take a completely furious form:

True, again, not without a spoonful of tar. If you apply the created rule, and then go back to look at it, then you may or may not see the grouping levels. The system shows / does not show them completely arbitrarily, for some internal reasons. Moreover, the grouping levels themselves do not disappear anywhere, but it is easier to pull down all the conditions and draw again than to remember how they should relate there.
Summing up, I believe that the new model of access rights was a success. It was not without drawbacks and controversial decisions, but it provides complete functionality with wide and interesting features. The three levels of nesting operations (inside conditions, between conditions and between groups of conditions) are clearly redundant, and, hand on heart, I cannot think of a plausible situation in which I would need all three. We assume that this is a growth stock for the future. The access model was described using the example of Windows 8, but I think that in Windows Server 2012 we will see the same mechanisms, only aggravated by the file server role - quotas, the system for classifying files and access categories. Building file resources becomes even more interesting.
Source: https://habr.com/ru/post/155281/
All Articles