Mikrotik + IPSec + Cisco. Part 2. Tunnel on the "gray" IP
In continuation of the post .
Last time I looked at the connection, when from the tsisk and mikrota side there were real IPs.
Here I will consider an example of a “gray realist”, that is, a gray IP, which the provider masks as external with unconditional redirection (binat).
external IP on the tsiska, and gray on the microtic, which is masked by the provider as external, with unconditional redirection (calls to this external user from the Internet will be redirected to the interface gray IP).
Scheme:

')
When connecting a new branch, I found out that the provider (the only local one) instead of the external IP gave me a “gray”.
To my legitimate indignation that the contract should be given to us by an external address - the provider replied that the external for us was made by nat'a, and all calls from the Internet to this external user will be redirected to our “gray” ip, and otherwise they will not do anything can
At this point, our conversation ended, and I began to set up the tunnel. The tunnel did not start :)
The situation is ambiguous. On the one hand, it looks like an external person, who actually looks “gray”, but there is no sense in using NAT-T
For about an hour, I was torturing a cicus mikrotik, and as a result I got a strange, but workable design (by the way I tried to repeat it on racoon under freebsd - it didn’t take off).
I created a tunnel on the tsiska, in which I indicated the gray ip microtic in the destination.
All settings (console and similar graphics) are listed below.
The same config, through the eyes of WinBox:
1. Interfaces-IP Tunnel . Add:

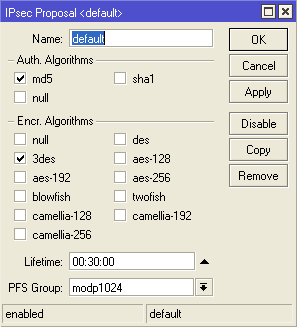
2. In the IP-IPSec-Proposals section in the default rule, it is MANDATORY to change SHA1 to MD5, because in this example MD5 is used.
3. IP-IPSec-Peers . Add:

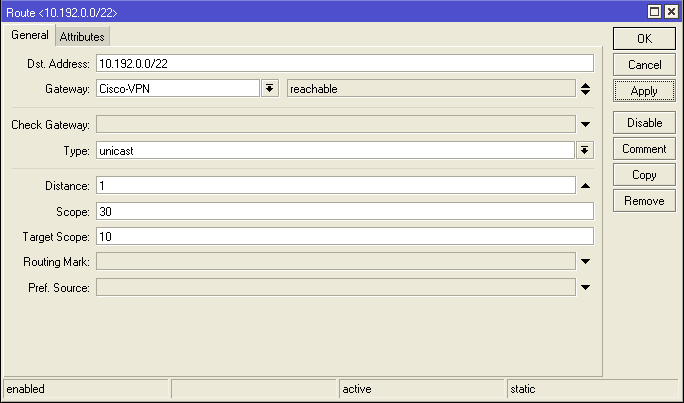
4. IP-Routes . Add:
Hope the material was helpful.
Last time I looked at the connection, when from the tsisk and mikrota side there were real IPs.
Here I will consider an example of a “gray realist”, that is, a gray IP, which the provider masks as external with unconditional redirection (binat).
Technical task: to organize ipip-tunnel between offices, with ipsec encryption, using Mikrotik RB450G and Cisco 2821.
Nuance
external IP on the tsiska, and gray on the microtic, which is masked by the provider as external, with unconditional redirection (calls to this external user from the Internet will be redirected to the interface gray IP).
Scheme:

Initial data
- Cisco 2821 (OS v12.4)
- 2. Mikrotik RB450G
- 3. Real external IP on both devices
- 4. Address tsiski: 77.77.77.226. Subnet from a tsiska: 10.192.0.0/22
- 5. Address microtic: 99.99.99.2. Subnet from the side of microtic: 192.168.100.0/24
- 6. Gray address microtic on the external interface: 172.16.99.2.
')
Prehistory
When connecting a new branch, I found out that the provider (the only local one) instead of the external IP gave me a “gray”.
To my legitimate indignation that the contract should be given to us by an external address - the provider replied that the external for us was made by nat'a, and all calls from the Internet to this external user will be redirected to our “gray” ip, and otherwise they will not do anything can
At this point, our conversation ended, and I began to set up the tunnel. The tunnel did not start :)
The situation is ambiguous. On the one hand, it looks like an external person, who actually looks “gray”, but there is no sense in using NAT-T
For about an hour, I was torturing a cicus mikrotik, and as a result I got a strange, but workable design (by the way I tried to repeat it on racoon under freebsd - it didn’t take off).
What happened in the end
I created a tunnel on the tsiska, in which I indicated the gray ip microtic in the destination.
All settings (console and similar graphics) are listed below.
Cisco:
! - 5 3des (pre-share) crypto isakmp policy 20 encr 3des hash md5 authentication pre-share ! group2 , dh-group=modp1024 group 2 ! crypto isakmp key MyPassWord address 99.99.99.2 no-xauth crypto isakmp keepalive 30 ! . ! transport, tunnel crypto ipsec transform-set transform-2 esp-3des esp-md5-hmac mode transport crypto dynamic-map dynmap 10 set transform-set transform-2 reverse-route crypto map vpnmap client configuration address respond crypto map vpnmap 5 ipsec-isakmp dynamic dynmap crypto map vpnmap 10 ipsec-isakmp ! crypto map vpnmap 95 ipsec-isakmp description polyanka ! ip set peer 99.99.99.2 set security-association lifetime seconds 86400 set transform-set transform-2 ! pfs group2 , dh-group=modp1024 set pfs group2 ! access-, match address 136 ! interface Tunnel95 description tunnel_NewMikrotik ip unnumbered GigabitEthernet0/1 ! tunnel source 77.77.77.226 ! . ! - . - ... ! , . tunnel destination 172.16.99.2 tunnel mode ipip interface GigabitEthernet0/1 description Internet ip address 77.77.77.226 255.255.255.224 no ip redirects no ip unreachables no ip proxy-arp ip wccp web-cache redirect out ip virtual-reassembly ip route-cache policy no ip mroute-cache duplex auto speed auto no mop enabled ! crypto map vpnmap ! , ip route 192.168.100.0 255.255.255.0 Tunnel95 ! access-list 136 permit ip host 77.77.77.226 host 99.99.99.2 access-list 136 permit ip host 77.77.77.226 host 172.16.99.2 Mikrotik:
/interface ipip add comment="Office tunnel" disabled=no dscp=0 local-address=172.16.99.2 \ mtu=1260 name=Cisco-VPN remote-address=77.77.77.226 /ip ipsec proposal set [ find default=yes ] auth-algorithms=md5 disabled=no enc-algorithms=3des \ lifetime=30m name=default pfs-group=modp1024 /ip ipsec peer add address=77.77.77.226/32 auth-method=pre-shared-key dh-group=modp1024 \ disabled=no dpd-interval=2m dpd-maximum-failures=5 enc-algorithm=3des \ exchange-mode=main generate-policy=yes hash-algorithm=md5 lifebytes=0 \ lifetime=1d my-id-user-fqdn="" nat-traversal=no port=500 proposal-check=\ obey secret=MyPassWord send-initial-contact=yes /ip route add disabled=no distance=1 dst-address=10.192.0.0/22 gateway=Cisco-VPN scope=30 \ target-scope=10 /ip firewall filter add action=accept chain=input comment="default configuration" disabled=no add action=accept chain=output disabled=no The same config, through the eyes of WinBox:
1. Interfaces-IP Tunnel . Add:

2. In the IP-IPSec-Proposals section in the default rule, it is MANDATORY to change SHA1 to MD5, because in this example MD5 is used.

3. IP-IPSec-Peers . Add:

4. IP-Routes . Add:

Hope the material was helpful.
Source: https://habr.com/ru/post/154829/
All Articles