Granular restoration of virtualized application objects
An important function of modern backup products is the possibility of granular recovery of files, emails, documents in workflow systems and other objects of various applications without having to perform a full rollback of the entire system to a certain control point in the past, when these objects still existed. When such a complete rollback is performed, it is forced to “drop” all users of the system “into the past”, which creates a lot of business problems associated with “data loss over a period of time”.
There are two ways of such a granular recovery, when the system is not completely rolled back: “ universal ” (independent of a specific application, carried out through restoring the entire system to a test lab or sandbox) and “ specialized ” (developed for a specific application, allowing you to extract objects application-specific data directly from the application data file (s) without the need to launch the application (with all dependent components) in the sandbox).
Further, the essence of these approaches will be shown on the example of Veeam Backup & Replication, which has the functionality to use both approaches, depending on what is best for the user in a particular case.
')
Veeam Universal Application Item Recovery
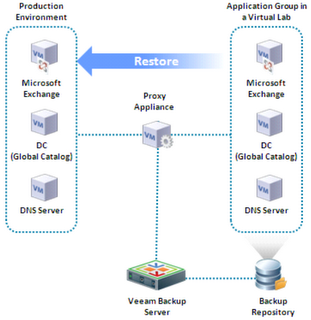
The universal recovery mechanism is built on running a set of interdependent virtual machines in the sandbox (environment isolated from the production network) directly from the backup repository, without having to unpack the disks of the selected virtual machine into a temporary location.
If we talk in terms of usage scenarios, then the work process is schematically as follows:
Veeam Explorer for Microsoft Exchange
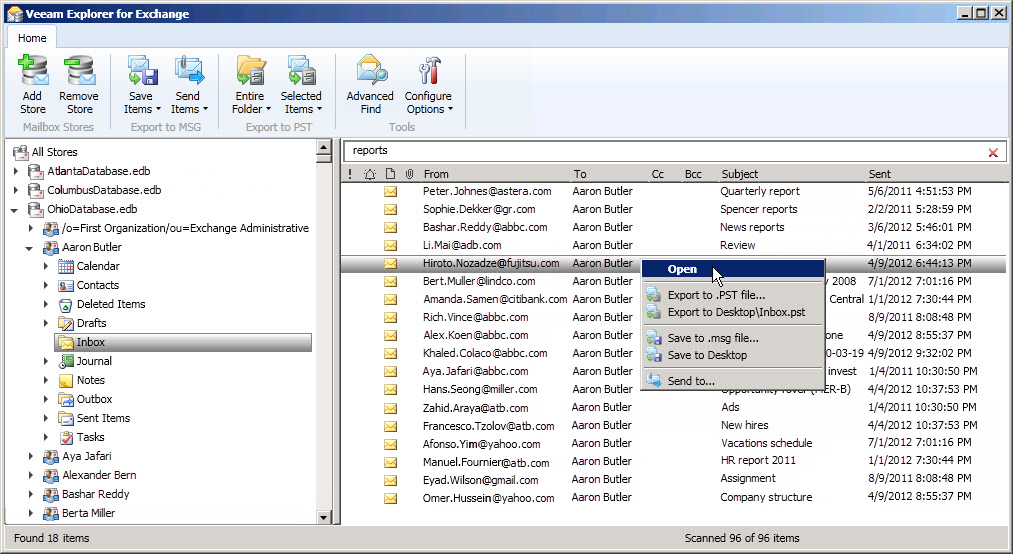
The product recovers deleted Microsoft Exchange Server emails using existing backups of the virtual machine on which it is installed. Any type of backup (full, incremental, compressed, and / or deduplicated) can be used for recovery. Veeam Explorer for Microsoft Exchange allows you to open the Exchange information base of the server directly from the virtual machine disk and perform typical operations that are usually performed by the administrator when recovering emails: you can view the contents of Exchange mailboxes, search by user-defined criteria, and restore the message in msg format or letters in the form of a PST file. The product uses a simple explorer-like interface.
This recovery method does not start any “farms” of interdependent virtual machines in the sandbox, since the Exchange server is not launched in principle - instead, the virtual machine disk containing the Exchange information storage file is mounted directly from the backup repository. server, after which it is performed at a low level using a parser of the appropriate format.
In addition to the actual recovery operations of individual letters, Veeam Explorer for Microsoft Exchange allows you to perform a compliance search (search in accordance with the requirements of the law) using various search criteria and the ability to export the result to a PST file.
Universal recovery can be applied in almost any case, but it may require launching a large number of virtual machines with dependent services in the sandbox. For example, recovery of an Exchange server may require (at a minimum) recovery of a virtual machine with a domain controller and (possibly a separately installed) DNS server. In the process of launching such a “farm”, network delays may occur waiting for virtual machines and services to start, on which the functionality of the restored application server depends. This entire process of starting the server farm sequentially may require significantly more time than specialized recovery requires that the application server does not start (only the operating system is required to start with the application information file). However, it should be noted that specialized recovery is usually available for a limited list of the most popular application servers, determined by the number of specially developed or publicly available parsers - so it may not always be applicable.
It is advisable to use products for "specialized recovery" :
It is advisable to use universal recovery tools:
There are two ways of such a granular recovery, when the system is not completely rolled back: “ universal ” (independent of a specific application, carried out through restoring the entire system to a test lab or sandbox) and “ specialized ” (developed for a specific application, allowing you to extract objects application-specific data directly from the application data file (s) without the need to launch the application (with all dependent components) in the sandbox).
Further, the essence of these approaches will be shown on the example of Veeam Backup & Replication, which has the functionality to use both approaches, depending on what is best for the user in a particular case.
')
Universal Recovery Technology
Veeam Universal Application Item Recovery
The universal recovery mechanism is built on running a set of interdependent virtual machines in the sandbox (environment isolated from the production network) directly from the backup repository, without having to unpack the disks of the selected virtual machine into a temporary location.

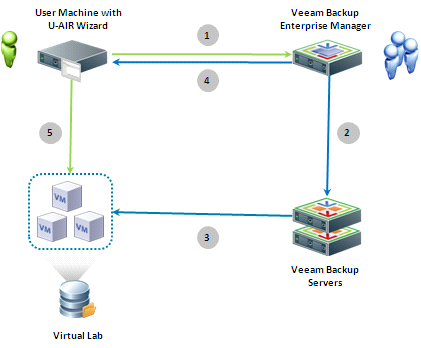
If we talk in terms of usage scenarios, then the work process is schematically as follows:

- A user who needs to restore an application object (for example, a mistakenly deleted Exchange server letter) launches the Universal U-AIR Recovery Wizard and sends a request to restore the objects of interest to it.
- The Backup Enterprise Manager administrator receives an email notification of the registration of a new recovery request.
- User’s rights to data requested for recovery are checked
- The user is informed of the result of checking his access rights, and, in the case of rights, the Administrator starts the task of restoring virtual machines using the SureBackup backup automated testing technology. This technology allows you to run virtual machines directly from the backup repository, without requiring you to decompress its disks into a temporary location.
- As soon as the virtual machine set is restored and launched in the sandbox, the user receives a notification with a link to the prepared virtual machine with the application of interest.
- Using the resulting link, the user can independently restore the application objects that interest him.
- Upon completion of the recovery procedure, virtual machines are shut down automatically or manually (by the administrator).
Technology Specialized Granular Recovery
Veeam Explorer for Microsoft Exchange
The product recovers deleted Microsoft Exchange Server emails using existing backups of the virtual machine on which it is installed. Any type of backup (full, incremental, compressed, and / or deduplicated) can be used for recovery. Veeam Explorer for Microsoft Exchange allows you to open the Exchange information base of the server directly from the virtual machine disk and perform typical operations that are usually performed by the administrator when recovering emails: you can view the contents of Exchange mailboxes, search by user-defined criteria, and restore the message in msg format or letters in the form of a PST file. The product uses a simple explorer-like interface.

This recovery method does not start any “farms” of interdependent virtual machines in the sandbox, since the Exchange server is not launched in principle - instead, the virtual machine disk containing the Exchange information storage file is mounted directly from the backup repository. server, after which it is performed at a low level using a parser of the appropriate format.
In addition to the actual recovery operations of individual letters, Veeam Explorer for Microsoft Exchange allows you to perform a compliance search (search in accordance with the requirements of the law) using various search criteria and the ability to export the result to a PST file.
Which way to choose?
Universal recovery can be applied in almost any case, but it may require launching a large number of virtual machines with dependent services in the sandbox. For example, recovery of an Exchange server may require (at a minimum) recovery of a virtual machine with a domain controller and (possibly a separately installed) DNS server. In the process of launching such a “farm”, network delays may occur waiting for virtual machines and services to start, on which the functionality of the restored application server depends. This entire process of starting the server farm sequentially may require significantly more time than specialized recovery requires that the application server does not start (only the operating system is required to start with the application information file). However, it should be noted that specialized recovery is usually available for a limited list of the most popular application servers, determined by the number of specially developed or publicly available parsers - so it may not always be applicable.
Thus, the following recommendations can be made:
It is advisable to use products for "specialized recovery" :
- if there is a complex configuration of the application server being restored , consisting of a set of interconnected virtual servers (for example, a distributed Exchange organization) - for reasons of speed of the recovery operation;
- if necessary, perform specialized operations that are usually not available in universal recovery products, for example, “search in accordance with the requirements of the laws”;
- if it is possible to delegate the recovery of a user document to an administrator . That is, if the user is ready to give the administrator a (potential) right to become familiar with the restoration of the document with all its contents. Example of a request for restoration: " Please restore the mistakenly deleted letter with the financial report for the 2nd quarter of the current year ." It is clear that in carrying out such a request, the administrator will have to look through all deleted letters for the period, even if they have been preselected by keyword.
It is advisable to use universal recovery tools:
- if the user has to restore the letter independently , because he does not want to give the administrator the right to familiarize himself with the contents of the document being restored;
- if the application server is not very large in terms of complexity of configuration and size , since universal recovery will not take much time;
- (Obviously) If there is no specialized recovery tool for the required application server.
Source: https://habr.com/ru/post/154323/
All Articles