Protecting Microsoft Hyper-V Server from Unauthorized Network Access
 Currently, virtualization is widespread and is used everywhere to solve a wide variety of tasks.
Currently, virtualization is widespread and is used everywhere to solve a wide variety of tasks.We decided to find out whether modern virtualization platforms need additional information protection tools and whether Security Code products can be useful for enhancing their level of security and for meeting the requirements of regulators when processing personal data and state secret information on such platforms.
Microsoft Hyper-V Security
Referring to the widely used Microsoft Hyper-V virtualization platform. Microsoft's materials on this product emphasize that the platform was designed and developed to meet security requirements (for example, Hyper-V security is covered in a Microsoft report at the RSA 2008 conference). Hyper-V hypervisor uses micronuclear architecture. Access checks are implemented at all levels, starting from hypercalls from virtual machines and access to physical memory and resources, and ending with the possibilities of organizing role-based access to virtual machines and combining them into groups. Each virtual machine gets its own unique SID, which is used when setting access rights to physical files that store machine images and data — this eliminates the possibility of accessing data from one machine to another.
In addition, recommendations have been published to strengthen security settings when deploying the Hyper-V platform. They, in particular, pay attention to the network security of the Hyper-V server itself. For example, to increase the network security level of the server, it is recommended to install at least two network adapters: one should be allocated for the administration channel, and the rest should be set up for organizing network access of virtual machines to external networks. In doing so, Microsoft recommends isolating the administration network from all other networks. This is necessary in order to exclude the possibility of network access to Hyper-V administration tools from virtual machines and external networks. The most reliable method of isolation is physical: changing the network topology, installing and configuring the necessary network equipment, and highlighting a special administration network that is separated from the general network.
')
Alternatives to physical network isolation
In some cases, the physical isolation of networks is impossible or highly undesirable. Then logical isolation is applied, the impossibility of network exchange is not achieved by physical separation of networks, but by using special software tools that specify the necessary access rules. In the case of Hyper-V, the IPSec suite of protocols can be used as such a tool, which allows you to lay “virtual” access channels on top of a conventional network. IPSec support is built into the OS, but different options are available in different versions of Windows. Support for user authentication (and not computer) appeared only in the new OS, IPSec configuration is performed differently depending on the version of Windows.
In the Security Code product line, there is a product that helps organize the logical isolation of networks by using the protocols of the IPSec family (AH and ESP) in transport mode. This is a TrustAccess distributed firewall (ME class 2), which supports almost all versions of Windows, is easy to deploy and configure, has official compatibility status with the platform running Hyper-V, “Works with Server 2008 R2” and Compatibility of users with “Compatible with Windows 7”.
An important feature of this product is the ability to distinguish network access not only by network addresses and protocols, but also by subjects of access - users and computers that initiated access to the protected resource.
At the same time, TrustAccess implements its own network authentication and access control mechanisms, which allows creating an independent secure logical perimeter on top of the existing local network without changing its topology. The product has been certified by FSTEC and can be used to protect confidential information up to class 1G inclusive, all classes of personal data information systems (ISPDn classes K1, K2, K3), as well as to protect state secrets in automated systems up to class 1B inclusive.
Using TrustAccess for Logic Hyper-V Management Network Isolation
Consider a Hyper-V server with two network adapters configured according to Microsoft recommendations:
- Network adapter 1 — dedicated only for administrative access to the server;
- Network Adapter 2 - designed for use by virtual machines.
In the Hyper-V settings, you need to create a new virtual network associated with adapter 2 (External type). The option “Allow management operating system to share this network adapter” should be disabled.
The local network establishes the TrustAccess management server and creates user accounts for Hyper-V administrators. The TrustAccess agent is installed on the Hyper-V server, as well as on all the computers from which the server will be administered. This configuration is shown in Figure 1 :
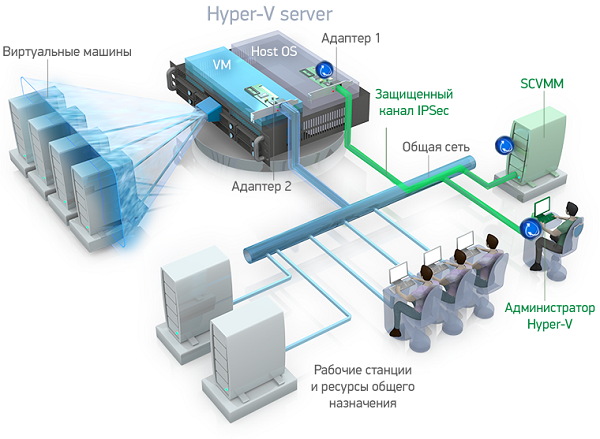
Using the TrustAccess management console for the Hyper-V server, rules are configured that allow network access only to specific users and groups (Hyper-V administrators) for network adapter 1.
How is logical isolation achieved
- The Hyper-V administrator at his workplace points out his TrustAccess account information and authenticates with the management server.
- After successful authentication, a network connection to the Hyper-V server is created to administer an ISAKMP security session for its administration, a session key is generated, and all network traffic addressed to the Hyper-V server is automatically signed by the TrustAccess agent (IPSec, AH in transport mode). From the user's point of view, all channel security mechanisms work transparently, i.e. do not require any intervention from him.
- The TrustAccess agent on the Hyper-V server passes network traffic addressed to the server itself, in accordance with the access rules and current security sessions; The user is identified by the IPSec / AH IP packet header that contains the session ID. If the IP packet signature is missing or does not match the data, the packet will be dropped. Checks are also performed on the packet sequence number in the IPSec AH header to protect against replay attacks.
- The response network traffic of the server is also signed by the session key and passes similar checks by the agent on the user's computer.
Thus, only Hyper-V administrators authenticated with TrustAccess can create network connections and exchange information. In this case, all attempts to access the server, including unauthorized, will be recorded. Registered events can be centrally processed with the ability to generate reports.
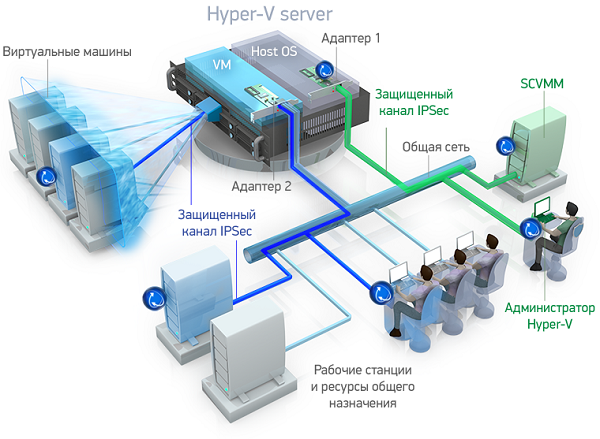
With TrustAccess, you can protect the virtual machines themselves, as well as other corporate network resources (servers and workstations). You can allocate new secure network segments ( Figure 2 ) or granularly configure user access rights to network services of protected resources. At the same time, the availability of FSTEC certificates will assist in the certification of information systems processing personal data and data constituting state secrets.
Conclusion
As we can see, third-party products can help meet security requirements and recommendations when building secure infrastructures based on the Hyper-V virtualization platform. From the point of view of network protection of the server against unauthorized access, the TrustAccess firewall has made it possible to isolate the administration network in a convenient way without the need to change the topology of the local network and install additional equipment.
Source: https://habr.com/ru/post/154309/
All Articles