Examples and recommendations of convenient instructions
Hello again, dear habralud!
In continuation of my post I decided to write how best to create instructions for users and administrators.
Anyone who is interested, I ask under the habrakat.
')
The principle of Keep It Simple Stupid is well-known in programming, but for some reason it is rarely used for writing instructions and guidance documents, preferring to spread the mind along the tree. In 70% of situations, this documentation is necessary only to dismiss our cheerful regulators, but at the same time they forget that they will have to work with this documentation, and not always technically savvy and knowledgeable people in the field of information security.
To begin, I will write a few rules that will help create a working and convenient document:
1. Try to separate instructions for users from instructions for administrators and security officers. and the first should not contain references to the second (they may contain references to each other).
2. Do step-by-step instructions, like "picked up and done." That is, the instructions should describe the algorithm of actions of the person to whom it is directed.
3. Describe each item as a separate action with the obligatory indication of the person in charge and contacts, if necessary.
4. For greater clarity, you can additionally draw in the instruction block diagram of actions. This will help the user to clearly understand and evaluate the actions, as well as you can explain the algorithm when learning.
5. Psychological moment - the instruction will be poorly executed and work if the algorithm on the fingers and examples is clear and accessible to users. Therefore - DO NOT FORGET ABOUT TRAINING!
Below is an example of instructions for setting up a user account in a corporate network.

The specificity of Russian organizations working from Soviet times and of the same experienced employees is such that, as a rule, their table is littered with papers. The computer sometimes does not turn off and does not block, even when they go home. Recently, I personally saw, passing late in the evening past one municipal enterprise, as if behind open blinds in a locked building a monitor was burning with a Vordov document open on it.
Users sometimes do not realize possible unintended leaks of information. Let her not confidential, perhaps it is only for internal use. But it gives an understanding that in this organization they do not care about their security and can do so with confidentiality. And it is also possible there will be information that has not yet been classified as closed, but already existing in the internal circulation of the organization.
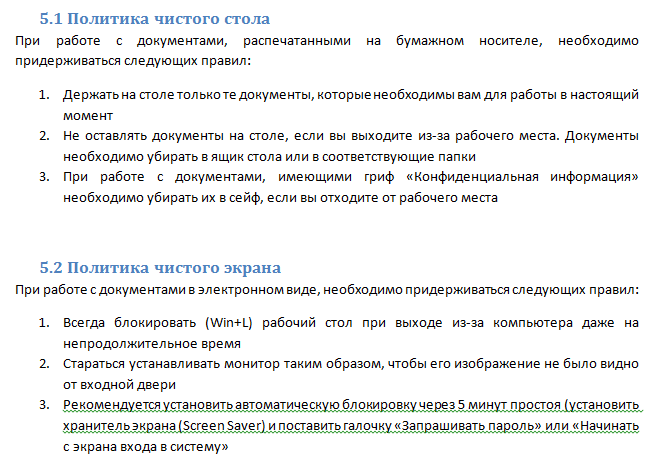
A good example of the best practices here is the policy of a clean table and a blank screen. They can be described in the same way as I gave an example earlier, but it will look a little silly, since the actions there are simple. Better to just make a set of rules:
This concludes the examples and recommendations. A series of similar posts, I will continue, if there is interest.
PS In the post there are screenshots of actually implemented and working instructions and policies. All matches with existing organizations are random. All department and bureau names are changed.
In continuation of my post I decided to write how best to create instructions for users and administrators.
Anyone who is interested, I ask under the habrakat.
')
Kiss
The principle of Keep It Simple Stupid is well-known in programming, but for some reason it is rarely used for writing instructions and guidance documents, preferring to spread the mind along the tree. In 70% of situations, this documentation is necessary only to dismiss our cheerful regulators, but at the same time they forget that they will have to work with this documentation, and not always technically savvy and knowledgeable people in the field of information security.
To begin, I will write a few rules that will help create a working and convenient document:
1. Try to separate instructions for users from instructions for administrators and security officers. and the first should not contain references to the second (they may contain references to each other).
2. Do step-by-step instructions, like "picked up and done." That is, the instructions should describe the algorithm of actions of the person to whom it is directed.
3. Describe each item as a separate action with the obligatory indication of the person in charge and contacts, if necessary.
4. For greater clarity, you can additionally draw in the instruction block diagram of actions. This will help the user to clearly understand and evaluate the actions, as well as you can explain the algorithm when learning.
5. Psychological moment - the instruction will be poorly executed and work if the algorithm on the fingers and examples is clear and accessible to users. Therefore - DO NOT FORGET ABOUT TRAINING!
Sample user instructions
Below is an example of instructions for setting up a user account in a corporate network.

Clear screen / clear desk
The specificity of Russian organizations working from Soviet times and of the same experienced employees is such that, as a rule, their table is littered with papers. The computer sometimes does not turn off and does not block, even when they go home. Recently, I personally saw, passing late in the evening past one municipal enterprise, as if behind open blinds in a locked building a monitor was burning with a Vordov document open on it.
Users sometimes do not realize possible unintended leaks of information. Let her not confidential, perhaps it is only for internal use. But it gives an understanding that in this organization they do not care about their security and can do so with confidentiality. And it is also possible there will be information that has not yet been classified as closed, but already existing in the internal circulation of the organization.
A good example of the best practices here is the policy of a clean table and a blank screen. They can be described in the same way as I gave an example earlier, but it will look a little silly, since the actions there are simple. Better to just make a set of rules:

This concludes the examples and recommendations. A series of similar posts, I will continue, if there is interest.
PS In the post there are screenshots of actually implemented and working instructions and policies. All matches with existing organizations are random. All department and bureau names are changed.
Source: https://habr.com/ru/post/153973/
All Articles