Warm and lamp VPN

Nothing foreshadowed trouble, when suddenly at 2 am the phone rang.
- Hello, dear! My youtube is not working!
- Fine, go to sleep!
- Nuuu! There is a new series!
- I'll do everything tomorrow!
- Well Zayaya, well!
- Okay! Okay! Now.
...
From this post you will find out the answers to the following questions:
How to save your darling from stress at 2 am? How to return access to youtube.com, if your provider has blocked it? How to quickly raise the VPN and configure client devices (Android, Windows, Debian, dd-wrt) to work with it? How to safely surf the Internet at open access points? How to earn karma in the eyes of your beloved? If it is interesting to you, welcome under kat!
')
Start
First of all, I asked to do a trace and sozolvit youtube.com with a DNS provider and Google Public DNS
tracert youtube.com
nslookup youtube.com
nslookup youtube.com 8.8.8.8, . , , . , , , . .
, , , , VPN , — . .
vServer VQ 7 — Hetzner , 7.90 /, .. VPN , .
, , , . VISA.
, vServer VQ 7,
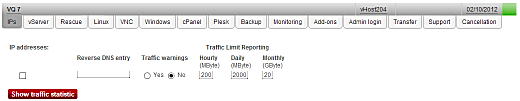
debian ( ). Linux, Debian 6.0 minimal, 32bit, Activate.
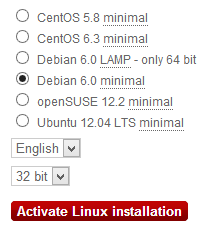
, .. , vServer, SSH.
. root , SSH .
#
passwd root
# mc ( , )
apt-get update
apt-get install mc
# openvpn
apt-get install openvpn
cd /usr/share/doc/openvpn/examples/easy-rsa/2.0/
#
nano ./vars
#
export KEY_SIZE=1024 #
export KEY_EXPIRE=3650 #
# -
export KEY_COUNTRY="RU"
export KEY_PROVINCE="RU"
export KEY_CITY="Moscow"
export KEY_ORG="http://habrahabr.ru"
export KEY_EMAIL="org@example.com"
#
# keys
. ./vars
. ./clean-all
./build-ca #
./build-key-server server #
./build-dh #
# tls-auth, vpn , DoS , :
openvpn --genkey --secret ./keys/ta.key
# tls-auth? ta.key , .
#
cp ./keys/ca.crt /etc/openvpn
cp ./keys/server.crt /etc/openvpn
cp ./keys/server.key /etc/openvpn
cp ./keys/dh1024.pem /etc/openvpn
# tls-auth, :
cp ./keys/ta.key /etc/openvpn
# , ( , -, Enter. (Enter export password), , )
./build-key-pkcs12 vpn.android
./build-key-pkcs12 vpn.windows
./build-key-pkcs12 vpn.debian
./build-key-pkcs12 vpn.ddwrt
./build-key-pkcs12 vpn.home
# /usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/ vpn.android.*, vpn.windows.* .
# , SSH, :
# cd /usr/share/doc/openvpn/examples/easy-rsa/2.0/
# . ./vars
# ./build-key-pkcs12 vpn.newuser1
# ./build-key-pkcs12 vpn.newuser2
#
zcat /usr/share/doc/openvpn/examples/sample-config-files/server.conf.gz > /etc/openvpn/server.conf
nano /etc/openvpn/server.conf
# - , , :
local IP___
push "redirect-gateway def1 bypass-dhcp"
push "dhcp-option DNS 8.8.8.8"
push "dhcp-option DNS 8.8.4.4"
client-to-client # , VPN
# tls-auth, ( #)
# tls-auth ta.key 0
# , , . .
port 1194
#
# rc.local, , .
nano /etc/rc.local
# exit 0
iptables -A FORWARD -s 10.8.0.0/24 -j ACCEPT
iptables -A FORWARD -m state --state RELATED,ESTABLISHED -j ACCEPT
iptables -t nat -A POSTROUTING -s 10.8.0.0/24 -o eth0 -j MASQUERADE
#
nano /etc/sysctl.conf
#
net.ipv4.ip_forward=1
# ,
reboot, . . , :
/usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/android (root )
1. OpenVPN for Android
2. p12,
/usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/vpn.android.p123. OpenVPN for Android
4. VPN Profiles > Add, . :
- Basic > Server Address: IP VPN ,
- Type: PKCS12 File
- Select: *.p12
- PKCS12 Password: , .
- upd: , remote-cert-tls server -. ,
- tls-auth , tls-auth ta.key
5. . , ( VPN, , . , ).
Windows
1. : 32bit | 64bit
2. myvpnconfig.ovpn ( ):
remote IP__ 1194
client
dev tun
ping 10
comp-lzo
proto udp
tls-client
remote-cert-tls server
pkcs12 vpn.windows.p12
verb 3
pull# tls-auth , :
tls-auth ta.key 13. batch (start_my_vpn.cmd) VPN :
cd C:\some\path\openvpn\
"C:\Program Files\OpenVPN\bin\openvpn.exe" --config C:\some\path\openvpn\myvpnconfig.ovpn4. , vpn.windows.p12 ,
/usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/vpn.windows.p125. , , , «» .
, :
, p12 ca.crt, vpn.windows.key vpn.windows.crt, ,
pkcs12 vpn.windows.p12ca ca.crt
cert vpn.windows.crt
key vpn.windows.key/usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/Linux
debian 6.0
# openvpn
apt-get install openvpn
# , VPN
mkdir /opt/openvpn
#
echo 'cd /opt/openvpn
/usr/sbin/openvpn --config /opt/openvpn/myvpnconfig.ovpn
' > /opt/openvpn/start_vpn.run
#
echo 'remote IP__ 1194
client
dev tun
ping 10
comp-lzo
proto udp
tls-client
remote-cert-tls server
pkcs12 vpn.debian.p12
verb 3
pull' > /opt/openvpn/myvpnconfig.ovpn
# tls-auth , :
# tls-auth ta.key 1
# vpn.debian.p12 /usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/
# , p12 ca.crt, vpn.debian.key vpn.debian.crt, windows, VPN, VPN.
chmod +x /opt/openvpn/start_vpn.run. vpn.debian.p12 ca.crt, vpn.debian.key vpn.debian.crt .
VPN, :
/opt/openvpn/start_vpn.rundd-wrt (Big Mega)
, VPN, , , NAT' IP. , VPN.
1. router_ip/Diagnostics.asp (.->)
2. « », , , . « » « »
3. :
#### CERT ####
CA_CRT='-----BEGIN CERTIFICATE-----
C4dczC6ZeWIgri7krQzPIrX5hNYAc676PNv6iomNWVJNkugr
-----END CERTIFICATE-----'
CLIENT_CRT='-----BEGIN CERTIFICATE-----
C4dczC6ZeWIgri7krQzPIrX5hNYAc676PNv6iomNWVJNkugr
-----END CERTIFICATE-----'
CLIENT_KEY='-----BEGIN RSA PRIVATE KEY-----
C4dczC6ZeWIgri7krQzPIrX5hNYAc676PNv6iomNWVJNkugr
-----END RSA PRIVATE KEY-----'
#### CERT ####
#### OPEN VPN ####
OPVPNENABLE=`nvram get openvpncl_enable | awk '$1 == "0" {print $1}'`
if [ "$OPVPNENABLE" != 0 ]
then
nvram set openvpncl_enable=0
nvram commit
fi
sleep 30
mkdir /tmp/openvpn; cd /tmp/openvpn
echo "$CA_CRT" > ca.crt
echo "$CLIENT_CRT" > client.crt
echo "$CLIENT_KEY" > client.key
chmod 644 ca.crt client.crt
chmod 600 client.key
sleep 30
echo 'remote IP__ 1194
client
dev tun
ping 10
comp-lzo
proto udp
tls-client
remote-cert-tls server
ca ca.crt
cert client.crt
key client.key
verb 3
pull' > openvpn.conf
# tls-auth , :
# tls-auth ta.key 1
killall openvpn
openvpn --config /tmp/openvpn/openvpn.conf&
### MASQUERADE
iptables -I FORWARD -i br0 -o tun0 -j ACCEPT
iptables -I FORWARD -i tun0 -o br0 -j ACCEPT
iptables -I INPUT -i tun0 -j ACCEPT
iptables -t nat -A POSTROUTING -o tun0 -j MASQUERADE
###
4. CA_CRT, CLIENT_CRT CLIENT_KEY, ca.crt, vpn.ddwrt.crt vpn.ddwrt.key , , vpn.ddwrt.crt , .
/usr/share/doc/openvpn/examples/easy-rsa/2.0/keys/5. IP__ « ».
6. , VPN. VPN IP ifconfig.
fin
OpenVPN , , 2ip.ru, IP , Hetzner, .

VPN Wi-Fi.
, wi-fi ( , . ).
, , NAT , . client-to-client .
:
1. www.opennet.ru/base/sec/openvpn_server.txt.html
2. wiki.hidemyass.com/DD-WRT_OpenVPN_Setup
3. www.hetzner.de
p.s.: youtube.com.
p.p.s.: android One X SGS II.
p.p.p.s.: , .
Source: https://habr.com/ru/post/153855/
All Articles