Using cryptographic functions implemented on a hardware token in web applications
For a long time, I was not bothered by the problem of using cryptographic functions in a web application (hash, esp, encryption, etc.) without using various additional software on the client site. All the solutions that I met, in one way or another, required the installation of various plug-ins, crypto-providers and other related software.
I want to express my view on the solution of the issue of using cryptographic transformations in web applications.
In sufficient detail, this issue is analyzed in articles on Habré: " EDS in the browser: problems, solutions, personal experience " and " Interesting solutions for electronic signature in the browser ."
A hardware token is a device that performs all the necessary crypto-transformations inside it. In the system, it also appears as removable media, working as a regular mass storage device.
')
The idea is that the token connected to the host usb port is a local web server available at 127.0.0.1 : port. To access the cryptographic functions of the token, you must implement the appropriate service.
As an example, to demonstrate this concept, a tinyweb web server was started that runs from a removable token media and a service that implements a hashing function was written in the form of a cgi script. This script uses the token API, including its functionality for determining the progress of a cryptographic operation.
The process is shown schematically in the figure:

Technically it looks like this. The user enters a web browser on a page formed according to certain rules. For example, I created a page (using my favorite Sencha ExtJS - wcrdemo.16mb.com )
When you click on the “Calculate hash” button, the local server is sent a request of the form
127.0.0.1 : 5151 / wTokenZ.cgi? Actionparam = EnumDevices. EnumDevices is a parameter that determines the function call, which returns a list of identifiers and serial numbers of connected tokens. For ease of processing, the script returns the data in json-format.
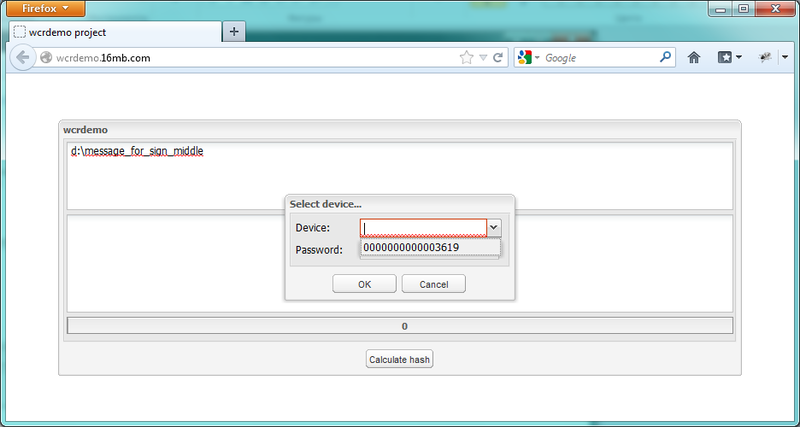
I want to note a significant point. This technology involves cross-domain requests. For implementation, I used the data.Store component of the Sencha ExtJS library and data.ScriptTagProxy as its proxy property.
The calculation of the hash is similar. The local server is sent a request with the following parameters for the script wTokenZ.cgi actionparam = HashData & deviceSerial = serial-token-number & devicePwd = password-activation-token & dataparam = text-or-name-for-hash file.
To monitor the hash calculation process, the following mechanism was implemented. Hashing functions can be passed from the token API. callback function, which is called during the execution of a long operation. This function writes its status to the file - in this case the number of bytes processed by the original message. I have implemented all this economy in a separate thread of the wTokenZ.cgi script. On the client side, at the moment the hash calculation request is sent, a periodic task is launched, which in 1 second sends a request of the form to the local server: 127.0.0.1 : 5151 / wTokenZ.cgi? Actionparam = GetIndicator. GetIndicator is a parameter that defines a function call, reads the number of bytes processed (from a file) and knowing the total size of the original message, which returns the percentage of the operation completed. To create, start and stop the monitoring process, the TaskMgr component was used (technically, the task was built on the data.Store component with data.ScriptTagProxy as its proxy property), and the Sencha ExtJS library component ProgressBar was used to indicate the process.
The result of performing a hash test file recorded on the token is shown in the figure:

So, summing up, we can highlight the following points:
- The principal point is the use of a token that implements cryptographic algorithms and works as a removable medium;
- to perform cryptographic operations there is no need to install any third-party software, even when using the scheme implemented in the above example, you only need to have a token available;
- for full cross-platform, it is desirable to implement such a service directly on the token.
I want to express my view on the solution of the issue of using cryptographic transformations in web applications.
In sufficient detail, this issue is analyzed in articles on Habré: " EDS in the browser: problems, solutions, personal experience " and " Interesting solutions for electronic signature in the browser ."
A hardware token is a device that performs all the necessary crypto-transformations inside it. In the system, it also appears as removable media, working as a regular mass storage device.
')
The idea is that the token connected to the host usb port is a local web server available at 127.0.0.1 : port. To access the cryptographic functions of the token, you must implement the appropriate service.
As an example, to demonstrate this concept, a tinyweb web server was started that runs from a removable token media and a service that implements a hashing function was written in the form of a cgi script. This script uses the token API, including its functionality for determining the progress of a cryptographic operation.
The process is shown schematically in the figure:

Technically it looks like this. The user enters a web browser on a page formed according to certain rules. For example, I created a page (using my favorite Sencha ExtJS - wcrdemo.16mb.com )
When you click on the “Calculate hash” button, the local server is sent a request of the form
127.0.0.1 : 5151 / wTokenZ.cgi? Actionparam = EnumDevices. EnumDevices is a parameter that determines the function call, which returns a list of identifiers and serial numbers of connected tokens. For ease of processing, the script returns the data in json-format.

I want to note a significant point. This technology involves cross-domain requests. For implementation, I used the data.Store component of the Sencha ExtJS library and data.ScriptTagProxy as its proxy property.
The calculation of the hash is similar. The local server is sent a request with the following parameters for the script wTokenZ.cgi actionparam = HashData & deviceSerial = serial-token-number & devicePwd = password-activation-token & dataparam = text-or-name-for-hash file.
To monitor the hash calculation process, the following mechanism was implemented. Hashing functions can be passed from the token API. callback function, which is called during the execution of a long operation. This function writes its status to the file - in this case the number of bytes processed by the original message. I have implemented all this economy in a separate thread of the wTokenZ.cgi script. On the client side, at the moment the hash calculation request is sent, a periodic task is launched, which in 1 second sends a request of the form to the local server: 127.0.0.1 : 5151 / wTokenZ.cgi? Actionparam = GetIndicator. GetIndicator is a parameter that defines a function call, reads the number of bytes processed (from a file) and knowing the total size of the original message, which returns the percentage of the operation completed. To create, start and stop the monitoring process, the TaskMgr component was used (technically, the task was built on the data.Store component with data.ScriptTagProxy as its proxy property), and the Sencha ExtJS library component ProgressBar was used to indicate the process.
The result of performing a hash test file recorded on the token is shown in the figure:

So, summing up, we can highlight the following points:
- The principal point is the use of a token that implements cryptographic algorithms and works as a removable medium;
- to perform cryptographic operations there is no need to install any third-party software, even when using the scheme implemented in the above example, you only need to have a token available;
- for full cross-platform, it is desirable to implement such a service directly on the token.
Source: https://habr.com/ru/post/152535/
All Articles