Mikrotik + IPSec + Cisco = Peace, Friendship, Gum
Technical task: to organize ipip-tunnel between offices, with ipsec encryption, using Mikrotik RB450G and Cisco 2821.
Nuance
- the latest version of the software on the microta (5.20)
- IPIP tsiska type
- Transform type “transport” instead of “tunnel”
Initial data
- Cisco 2821 (OS v12.4)
- 2. Mikrotik RB450G
- 3. Real external IP on both devices
- 4. Address tsiski: 77.77.77.226. Subnet from a tsiska: 10.192.0.0/22
- 5. Mikrotik address: 88.88.88.2. Subnet from the side of microtic: 192.168.88.0/24
Prehistory
Faced with the need to replace the servers in our branches, for something more reliable, hardware.
We communicate with the central office through tunnels with ipsec encryption. In the central office we have, in fact, everything is built on felines, and in most of the branches there are regular servers running FreeBSD that cling to the tunnels using racoon.
There was a problem, due to obsolescence, the failure of the servers themselves, to start installing simple, inexpensive hardware solutions.
Brothers in mind, colleagues and forums pushed me to the products Mikrotik, and immediately I sent a letter to them as follows:
. , , : nat-, ipsec- 28, 100, ospf. , "POE" . The answer came unexpectedly, very quickly, within one day:
, Mikrotik. , - RB/MRTG (miniROUTERG) 4531 - RB1100AHx2 16915 : http://routerboard.com/RB450G http://routerboard.com/RB1100AHx2 http://wiki.mikrotik.com/wiki/IPSec_VPN_with_Dynamic_Routing_/_Mikrotik_and_Cisco I immediately chose the “RB450G”. Ordered, brought.
At once I will say, it was not possible to set up the link above. The data there is outdated, some parameters in version 5.20 are simply missing.
Rummaged through the forums, read articles about this content:
betep.wpl.ru/2009/02/wiki-mikrotik.html
netandyou.ru/17 is interesting by the way, but an example of ipsec in the gre-tunnel is considered, and in my case the type of tunnel ipip and the mode of operation of crypto ipsec transform-set on the tsiska are not “Tunnel”, but “Transport”. But also did not work.
I also rummaged through a bunch of materials on the forums, got the connection to pass, encryption was enabled, but nothing worked, the packets refused to run through the tunnel, as I did not try to force them to do so.
Two lost days and prompted me to write on Habr, perhaps these lines will help someone in work.
In the end, everything turned out to be banal and very simple.
I focused my attention on the settings of the IPSec policies in Mikrotik , and it looked like it was a mistake :)
After a thoughtful study of the material, which really helped me:
wiki.mikrotik.com/wiki/Manual : IP / IPsec # Transport_mode_2 - from here and below on a couple of pages
and
wiki.mikrotik.com/wiki/Manual : Interface / IPIP - it's just the basics, but just in case.
')
I just removed all the policies (by the way - they were correctly configured, judging by the dynamic ones that were created later), and just ticked the autogeneration policy. What successfully and did a tsiska with a microtic after connection.
All settings (console and similar graphics) are listed below.
Cisco:
! - 5 3des (pre-share) crypto isakmp policy 20 encr 3des hash md5 authentication pre-share ! group2 , dh-group=modp1024 group 2 ! crypto isakmp key MyPassWord address 88.88.88.2 no-xauth crypto isakmp keepalive 30 ! . ! transport, tunnel crypto ipsec transform-set transform-2 esp-3des esp-md5-hmac mode transport crypto dynamic-map dynmap 10 set transform-set transform-2 reverse-route crypto map vpnmap client configuration address respond crypto map vpnmap 5 ipsec-isakmp dynamic dynmap crypto map vpnmap 10 ipsec-isakmp ! crypto map vpnmap 93 ipsec-isakmp description Mikrotik_Local ! ip set peer 88.88.88.2 set security-association lifetime seconds 86400 set transform-set transform-2 ! pfs group2 , dh-group=modp1024 set pfs group2 ! access-, match address 137 ! interface Tunnel93 description tunnel_Mikrotik ip unnumbered GigabitEthernet0/1 ! tunnel source 77.77.77.226 ! tunnel destination 88.88.88.2 ! ipip tunnel mode ipip ! interface GigabitEthernet0/1 description Internet ip address 77.77.77.226 255.255.255.224 no ip redirects no ip unreachables no ip proxy-arp ip wccp web-cache redirect out ip virtual-reassembly ip route-cache policy no ip mroute-cache duplex auto speed auto no mop enabled ! crypto map vpnmap ! , ip route 192.168.88.0 255.255.255.0 Tunnel93 ! access-list 137 permit ip host 77.77.77.226 host 88.88.88.2 Mikrotik:
/interface ipip add disabled=no dscp=0 local-address=88.88.88.2 mtu=1260 name=ipip1 \ remote-address=77.77.77.226 add address=192.168.88.1/24 comment="default configuration" disabled=no \ interface=ether2-master-local network=192.168.88.0 add address=88.88.88.2/30 disabled=no interface=ether1-gateway network=\ 62.5.248.248 add add-default-route=yes comment="default configuration" \ default-route-distance=1 disabled=no interface=ether1-gateway \ use-peer-dns=yes use-peer-ntp=yes /ip ipsec peer add address=77.77.77.226/32 auth-method=pre-shared-key dh-group=modp1024 \ disabled=no dpd-interval=2m dpd-maximum-failures=5 enc-algorithm=3des \ exchange-mode=main generate-policy=yes hash-algorithm=md5 lifebytes=0 \ lifetime=1d my-id-user-fqdn="" nat-traversal=no port=500 proposal-check=\ obey secret=MyPassWord send-initial-contact=yes /ip route add comment="Default routing" disabled=no distance=1 dst-address=0.0.0.0/0 \ gateway=88.88.88.1 scope=30 target-scope=10 add disabled=no distance=1 dst-address=10.192.0.0/22 gateway=ipip1 scope=30 \ target-scope=10 /ip firewall filter add action=accept chain=input comment="default configuration" disabled=no add action=accept chain=output disabled=no /system logging add action=memory disabled=no prefix="" topics=ipsec If someone configures through Winco Mikrotikovsky GUI, a similar setting:
1. Interfaces-IP Tunnel . Add:
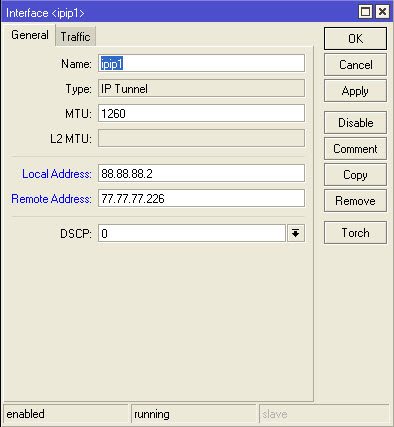
2. In the IP-IPSec-Proposals section in the default rule, it is MANDATORY to change SHA1 to MD5!
3. IP-IPSec-Peers . Add:
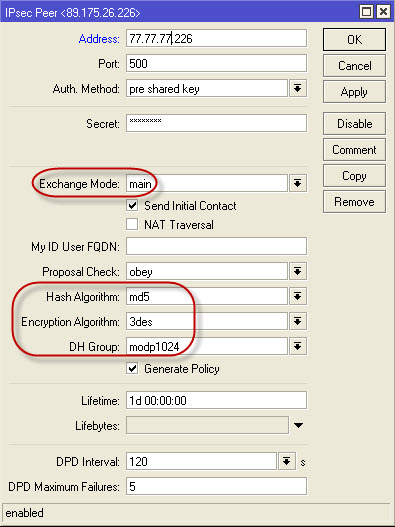
After that, if the tsiska is already configured, then the session should rise:

And automatically generated policies:
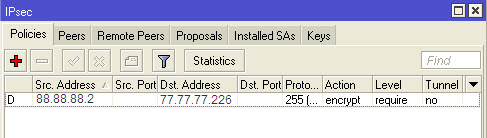
4. IP-Routes . Add:
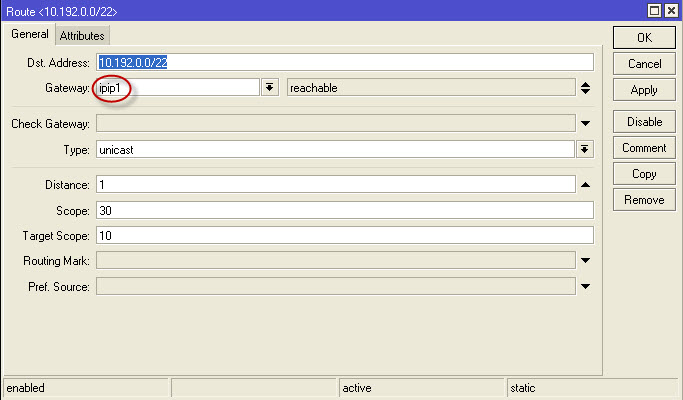
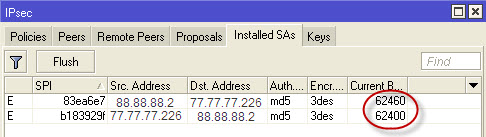
After that, you can look back at IP-IPSec, the tab of Instaled SAs, and you should see that Baitics run through the tunnel in both directions:
I hope this material will save someone time and nerves.
Source: https://habr.com/ru/post/151951/
All Articles