Such a dangerous Internet Explorer ...
 We have not started a real fall of the leaves, and zero-day vulnerabilities fell like autumn leaves. How much time elapsed since identifying the last 0-day vulnerability (in Java SE 7) - less than three weeks? And now a new, and no less interesting vulnerability - remote execution of arbitrary code in all versions of Microsoft Internet Explorer (from 6 to 9) on all versions of Windows OS - from 98 to 7.
We have not started a real fall of the leaves, and zero-day vulnerabilities fell like autumn leaves. How much time elapsed since identifying the last 0-day vulnerability (in Java SE 7) - less than three weeks? And now a new, and no less interesting vulnerability - remote execution of arbitrary code in all versions of Microsoft Internet Explorer (from 6 to 9) on all versions of Windows OS - from 98 to 7.In general, it has already been described in this post. I will tell you more about how the exploit works, what its sources are, and I will share my opinion on what to do with all this ...
A new vulnerability was “unearthed” by studying the work of the C & C servers that launched the attack on the Java SE 7 vulnerability. the theft of intellectual values - formulas, descriptions of chemical processes, etc. In the future, he participated in other attacks. Several infected servers used by the Nitro group were also in the spotlight. September 14 at one of them, located in Italy, a new folder with the following contents:
')
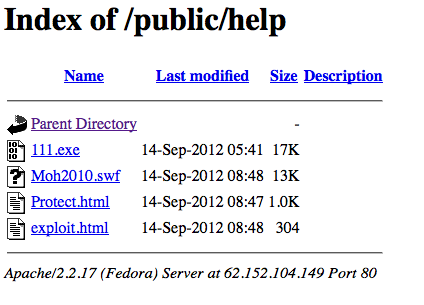
These files were tested by us on a fully updated Microsoft Windows XP Pro SP3 server with the latest version of Adobe Flash (11,4,402,265). As a surprise, additional files were added to the test computer. Scanning the studied files on the VirusTotal resource yielded zero results - none of the antiviruses recognized the malicious code in them.
The analysis showed that the exploit consists of 4 main components:
1. File "Exploit.html" - the starting point and preliminary preparation of the exploit. After creating the necessary conditions for the exploitation of the vulnerability, it launches the flash file “Moh2010.swf”.
Symantec detects this process as Bloodhound.Exploit.474
2. "Moh2010.swf" is responsible for the hidden download of executable code. After downloading the malicious code, it launches the vulnerability file "Protect.html" in the iFrame window.
Symantec detects this process as Trojan.Swifi.
3. The “Protect.html” file is the opening trigger for this vulnerability, which is responsible for executing the malicious code loaded with “Moh2010.swf”.
Symantec also detects this process as Bloodhound.Exploit.474.
4. The downloaded malicious code pumps up additional malicious programs and runs them on the compromised system.
Symantec detects these malicious programs like Trojan.Dropper and Backdoor.Darkmoon.
Thus, it turned out that Microsoft Internet Explorer contains a vulnerability that allows remote execution of arbitrary code on a user's computer in the context of user rights, which has already been confirmed by the manufacturer, Microsoft.
And now what i can do? Get into a panic, and how the German government to stop using IE? Then pay attention to the fact that one 0-day vulnerability was born after another, and in the hands of the same criminal group. And not the fact that will not appear anything else. And not necessarily for Internet browsers. I think that excluding one software product after another, we will not come to a secure computing environment, unless we go to the accounts.
On the contrary, I propose to be reasonable people and rely on the best practices:
• use a special account for working with the Internet with the minimum necessary rights;
• Be sure to install released software updates and
• always keep protective equipment up to date.
Good luck on the Internet!
Andrey Zerenkov, Symantec Russia
Source: https://habr.com/ru/post/151816/
All Articles