IS audit methodology
How to determine the degree of system security (information object)?
Today, there are two most common types of IS audit: the first is the assessment of compliance with the requirements of standards (compliance) and the second is threat modeling and risk assessment.
Both types have drawbacks, which may result in incorrect assessment. In the first case, we check the compliance of our system with the requirements for a wide range of systems. These requirements cannot take into account the specifics of a particular system, and therefore there is a possibility that there are unnecessary requirements or a lack of necessary ones. In the second case, the result depends only on the qualifications and awareness of the auditor.
Under the katom described methodology for the audit of information security, minimizing these disadvantages.
The proposed method is based on the construction of failure trees and causes (from graph theory). Below are the actions of the auditor in stages.
1. Preparatory events
2. Building Failure Trees
3. Building a tree of causes
4. Assessment of compliance
An illustration of stages 2 and 3 is presented in the figures below.
')
Example of building fault trees:
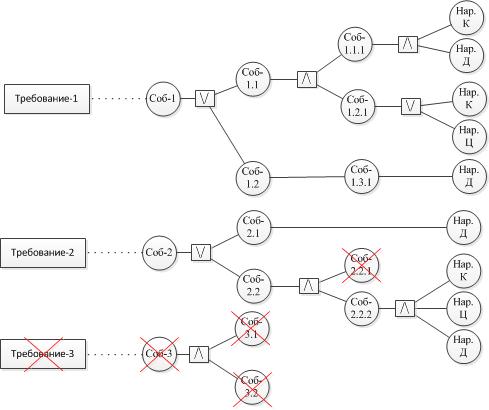
An example of building a tree of reasons:

Today, there are two most common types of IS audit: the first is the assessment of compliance with the requirements of standards (compliance) and the second is threat modeling and risk assessment.
Both types have drawbacks, which may result in incorrect assessment. In the first case, we check the compliance of our system with the requirements for a wide range of systems. These requirements cannot take into account the specifics of a particular system, and therefore there is a possibility that there are unnecessary requirements or a lack of necessary ones. In the second case, the result depends only on the qualifications and awareness of the auditor.
Under the katom described methodology for the audit of information security, minimizing these disadvantages.
The proposed method is based on the construction of failure trees and causes (from graph theory). Below are the actions of the auditor in stages.
1. Preparatory events
- we choose the IB standard (Russian, international, branch);
- write down the requirements of the selected standard for our system;
- for each requirement we compose a violation (the event as a result of which the requirement will not be fulfilled).
2. Building Failure Trees
- for each violation made at the preparatory stage, we build a failure tree (thus, we describe the events that follow the violation);
- We identify events that do not lead to violations of information security properties, and remove them from further consideration.
3. Building a tree of causes
- for all nodes of fault trees that are not leaves or roots (in our case, leaves are events that directly lead to violations of information security properties, roots are initial violations), we build trees of causes (thus we describe events that can lead to a specific violation);
- while in building the causes of trees, violations appeared that are absent in the failure trees, then for such violations we build requirements leading to their elimination.
4. Assessment of compliance
- we carry out an assessment of the fulfillment of requirements (requirements of the standard minus the requirements removed on the construction of failure trees plus the requirements built during the construction of the tree of causes).
An illustration of stages 2 and 3 is presented in the figures below.
')
Example of building fault trees:

An example of building a tree of reasons:

Source: https://habr.com/ru/post/151669/
All Articles