Reverse-engineering of a single virus for Android
I am a Java programmer and not so long ago began to learn Java for Android. Today, my tablet got a very curious notification “I need to update the Flash Player”, if not for the professional interest in the Android platform, then most likely I would have missed it and continued to relax, but today is a cold Sunday evening and I decided to see what the virus “under the hood.
By the way, the guys were good at the moment of release of their “FlashPlayer”: just an hour before that I updated the normal FlashPlayer from Adobe on the hospital.
If it is interesting to you - I ask under kat. Under the cut there are a few screenshots.
So, I downloaded the APK on the tablet, Lockout immediately cursed that it was a Trojan and suggested immediately removing the file from harm's way. Refusing to delete, I transferred the apk-shnik to the hospital via FTP Server for further investigation.
The first thing to do was unpack the archive using apktool (all links to the used programs at the end of the article).
')
First of all, I drew attention to the Android Manifest.
There was a whole (or almost all) set of functions of the device. In addition to standard (for virus programs) permissions like:
There were such things:
Fuck him access to the alarm clock, I did not understand.
By tracking this event, from immediately performs itself after immediately after loading.
Also, the virus tracks:
And registers the service:
If you install the application on the device, the installation looks like this:

After the manifesto, I looked at the resources: there was nothing interesting: the standard flash player icon is 72 by 70 in size for all densities and strings.xml with the value:
The most interesting thing was in the assets folder.

In the files folder there were 6 photos of guys, 4 photos of girls, a file tabor.css (with some styles) and obviously not a text file a.txt (the unix-new utility file didn’t really help determine what it was,
In the folders css, images and js were auxiliary things for drawing html-pages.
The white.html page looks like this:

Apparently, the authors made a calculation on completely stupid users (the flash player icon, and offer to ship Opera Mini 6.5 (very often distributed through AdMob in applications).
At the press of a button, the script JS is activated, which redirects to payed.html
Even in white.html there is a hidden div: with a hard-coded link:
On the payed.html page the link is different:
The sendcontacts.html page simply redirects to payed.html
The most interesting page is test.html .
JS c jQuery is actively used there.
The algorithm is as follows:
offerta.html contains an agreement between the service flashplayer-ru.net and the Subscriber.
The full text can be read on infomobiles.net/oferta.php
I will give the most remarkable moments:
And after all these rules there is a button further, clicking on which will transfer the victim to payed.html, where it is waiting for a link to filesesa.net
By whois, we learn that the flashplayer-ru.net domain was created on 22.06.2012, and filesesa.net - on September 4. The rest is all the same
Then I went to the registrar's site (bs - this is the Bahamas) and talked to the tech-support girl, who advised me to send a message to abuse by emailing abuse@internet.bs.
Having written in abuse, I continued to dig. In the unpacked archive there were also smali files. But while I was on the subject of reversing from .smali to .java, I decided to return to the original APK archive. Having unpacked apk-shku with a simple 7-zip, I found classes.dex there.
Next came dex2jar
And then the JD-GUI, which gave me the code:
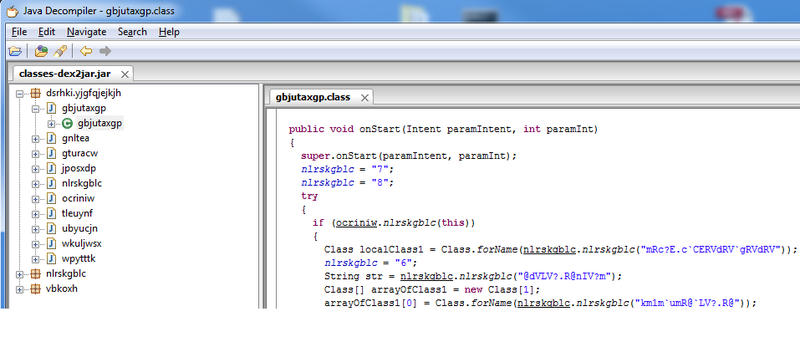
It seems that the code is heavily obfuscated. I haven’t fully figured out how exactly the web pages are called, but by running a virus on the emulator, I can say that it starts right after reboot and immediately crashes.
I posted the resulting code on our laboratory website: virtalabs.net/apkHack/flash-player.src.zip
The APK itself can be found there: virtalabs.net/apkHack/flash_player_installer.apk
And the unzipped folder is here: virtalabs.net/apkHack/FlashPlayer
Now I am waiting for the reaction from the registrar. Since the sites are made in Russian for the CIS audience (as seen by the user agreement, at a minimum), is it worth it to send reversing results to department K?
I hope this article will cause interest in the android-community and will save someone from installing this type of viruses.
And as I promised links to the used programs:
APKtool - code.google.com/p/android-apktool
Dex2Jar - code.google.com/p/dex2jar
JD-Gui - java.decompiler.free.fr/?q=jdgui
JD-Gui has a version under Eclipse IDE (http://java.decompiler.free.fr/?q=jdeclipse) - but I could not install it because of problems with the JD site.
I was also greatly benefited by the article by Ken Kinder: kkinder.com/2011/11/27/so-you-want-to-reverse-engineer-an-android-app-apk
By the way, the guys were good at the moment of release of their “FlashPlayer”: just an hour before that I updated the normal FlashPlayer from Adobe on the hospital.
If it is interesting to you - I ask under kat. Under the cut there are a few screenshots.
So, I downloaded the APK on the tablet, Lockout immediately cursed that it was a Trojan and suggested immediately removing the file from harm's way. Refusing to delete, I transferred the apk-shnik to the hospital via FTP Server for further investigation.
The first thing to do was unpack the archive using apktool (all links to the used programs at the end of the article).
')

First of all, I drew attention to the Android Manifest.
There was a whole (or almost all) set of functions of the device. In addition to standard (for virus programs) permissions like:
<uses-permission android:name="android.permission.READ_SMS" />
<uses-permission android:name="android.permission.SEND_SMS" />
<uses-permission android:name="android.permission.RECEIVE_SMS" />
<uses-permission android:name="android.permission.READ_CONTACTS" />
<uses-permission android:name="android.permission.UPDATE_DEVICE_STATS" />
<uses-permission android:name="android.permission.CHANGE_WIFI_STATE" />
<uses-permission android:name="android.permission.WRITE_SETTINGS" />
There were such things:
<uses-permission android:name="com.android.alarm.permission.SET_ALARM" />Fuck him access to the alarm clock, I did not understand.
<uses-permission android:name="android.permission.RECEIVE_BOOT_COMPLETED" />By tracking this event, from immediately performs itself after immediately after loading.
Also, the virus tracks:
- Connect / disconnect from the network:
<intent-filter>
<action android:name="android.net.conn.CONNECTIVITY_CHANGE" /> - Sent SMS'ki
<intent-filter android:priority="999">
<action android:name="android.provider.Telephony.SMS_RECEIVED" />
And registers the service:
<service android:name="dsrhki.yjgfqjejkjh.gbjutaxgp">
<intent-filter>
<action android:name="dsrhki.yjgfqjejkjh.gbjutaxgpStart76" />
If you install the application on the device, the installation looks like this:

After the manifesto, I looked at the resources: there was nothing interesting: the standard flash player icon is 72 by 70 in size for all densities and strings.xml with the value:
Loading
The most interesting thing was in the assets folder.

In the files folder there were 6 photos of guys, 4 photos of girls, a file tabor.css (with some styles) and obviously not a text file a.txt (the unix-new utility file didn’t really help determine what it was,
a.txt: dataIn the folders css, images and js were auxiliary things for drawing html-pages.
The white.html page looks like this:

Apparently, the authors made a calculation on completely stupid users (the flash player icon, and offer to ship Opera Mini 6.5 (very often distributed through AdMob in applications).
At the press of a button, the script JS is activated, which redirects to payed.html
Even in white.html there is a hidden div: with a hard-coded link:
:
yerc1.net/?u=64504 .On the payed.html page the link is different:
:
filesesa.net/?u=90-656jc5y9ny1yc2fb0d .The sendcontacts.html page simply redirects to payed.html
The most interesting page is test.html .
JS c jQuery is actively used there.
The algorithm is as follows:
- At first, the icon and the inscription: “Wait, the installation is in progress.”
- Further with the help of JS random timeout is calculated
timeout = Math.floor((Math.random()*100)+1) + Math.floor((Math.random()*100)+1);
This shows fake progressbar to the user. - At the end of the waiting condition is calculated:
(androidInfo.match(/operator3/) == 'operator3' || androidInfo.match(/operator13/) == 'operator13' )
If operator13, then the message is displayed:$('#paymentinfo').html(' , 29900. ');
A good price for a free app ...
If operator = 3, then the message is: "The service is paid, not more than 354p including VAT."
If not, then not another, then a link to offerta.html is shown.
offerta.html contains an agreement between the service flashplayer-ru.net and the Subscriber.
The full text can be read on infomobiles.net/oferta.php
I will give the most remarkable moments:
- The software product is an installation module (“application”) that provides access to the services of the Internet resource flashplayer-ru.net
- In the process of registration ... up to three telecommunication messages are sent to digital identifiers that have premium billing
- You give information about the technical parameters of the subscriber station you are using to further provide compatible applications or links to compatible applications.
- The cost is 1062 rubles
- ... you must contact the Subscriber Support Service by mail: me.s.mobile@gmail.com.
And after all these rules there is a button further, clicking on which will transfer the victim to payed.html, where it is waiting for a link to filesesa.net
By whois, we learn that the flashplayer-ru.net domain was created on 22.06.2012, and filesesa.net - on September 4. The rest is all the same
Domain Name: FILESESA.NET
Registrar: INTERNET.BS CORP.
Whois Server: whois.internet.bs
Referral URL: www.internet.bs
Name Server: NS3.SUPERIDNS.NET
Name Server: NS4.SUPERIDNS.NET
Status: ok
Updated Date: 04-sep-2012
Creation Date: 04-sep-2012
Expiration Date: 04-sep-2013
Then I went to the registrar's site (bs - this is the Bahamas) and talked to the tech-support girl, who advised me to send a message to abuse by emailing abuse@internet.bs.
Having written in abuse, I continued to dig. In the unpacked archive there were also smali files. But while I was on the subject of reversing from .smali to .java, I decided to return to the original APK archive. Having unpacked apk-shku with a simple 7-zip, I found classes.dex there.
Next came dex2jar

And then the JD-GUI, which gave me the code:

It seems that the code is heavily obfuscated. I haven’t fully figured out how exactly the web pages are called, but by running a virus on the emulator, I can say that it starts right after reboot and immediately crashes.
I posted the resulting code on our laboratory website: virtalabs.net/apkHack/flash-player.src.zip
The APK itself can be found there: virtalabs.net/apkHack/flash_player_installer.apk
And the unzipped folder is here: virtalabs.net/apkHack/FlashPlayer
Now I am waiting for the reaction from the registrar. Since the sites are made in Russian for the CIS audience (as seen by the user agreement, at a minimum), is it worth it to send reversing results to department K?
I hope this article will cause interest in the android-community and will save someone from installing this type of viruses.
And as I promised links to the used programs:
APKtool - code.google.com/p/android-apktool
Dex2Jar - code.google.com/p/dex2jar
JD-Gui - java.decompiler.free.fr/?q=jdgui
JD-Gui has a version under Eclipse IDE (http://java.decompiler.free.fr/?q=jdeclipse) - but I could not install it because of problems with the JD site.
I was also greatly benefited by the article by Ken Kinder: kkinder.com/2011/11/27/so-you-want-to-reverse-engineer-an-android-app-apk
Source: https://habr.com/ru/post/151608/
All Articles